by Scott Muniz | Jun 25, 2020 | Uncategorized
This article is contributed. See the original author and article here.
To collect events in Azure Sentinel from VMs and servers, we use the Microsoft Monitoring Agent. The MMA supports both Windows and Linux operating systems independently of where they run: on-premise, Azure or other clouds. The agent may be installed on Windows or Linux VMs by using one of the following methods:
- Manual installation: following a wizard or using an existing software distribution tool.
- Azure Automation Desired State Configuration (DSC): you can include the MMA agent as part of your desired state configuration.
- Scripting or Automation: either using PowerShell, Bash or other automation tools such as Ansible, Puppet, Chef, etc.
- VM extension: the Log Analytics agent virtual machine installs the Log Analytics agent on Azure virtual machines, and enrolls virtual machines into an existing Log Analytics workspace.
There is a very convenient and fast approach for making sure all of your Azure VMs are onboarded into Azure Sentinel, using an Azure Policy that can audit settings inside the machine and then using the VM extensions installation as a remediation task if the agent is not present. However, it was only available for Azure VMs ; for non-Azure deployments, we had to do a manual installation, what if we could have a similar experience for those servers as well?
Azure Arc for servers allows us to extend Azure Policies and extensions outside the boundaries of Azure, this makes non-Azure VMs first class citizens in Azure management plane. On this article we will focus on how you can not only automate the MMA installation using extensions but also leveraging Azure Policies to warrantee all servers are reporting events to Azure Sentinel.
Azure Arc agent on boarding
To apply policies to non-Azure VMs you must first deploy the Azure Arc agent, so it is registered into ARM. Having this agent and using Azure as the management control plane will also come with a set of new benefits:
- Have a full inventory of your resources
- Organize them into Resource Groups and Subscriptions to follow your cloud native practices
- Apply tagging, RBAC and locks
- Each Azure Arc connected machine will get a resource ID in ARM, so you will be able to scope your Log Analytics queries
- Deploy extensions at scale including Microsoft monitoring Agent, Desired State Configuration and Custom Script extension.
You could deploy this agent manually or automate the installation with tools like:
- Windows Admin Center
- Azure automation service
- System Center Configuration Manager (SCCM)
- System Center Virtual Machine Manager (SCVMM)
- Other automation tools: Ansible, Puppet, Chef, etc.
Azure Policies with Azure Arc
Now that external resources are connected to Azure, you can start managing them in a similar way you’d do in Azure. A very common way to make sure all of your VMs are reporting events to Sentinel would be to set up an Azure Policy at subscription or Resource Group level so, why not do the same for non-Azure Linux and Windows systems?
This article, shows the steps needed to set up a policy that will act as built-in control to make sure all your servers are reporting to you Azure Sentinel Log Analytics Workspace.
We will set up an initiative at resource group level to make sure that all Azure Arc enabled servers are reporting to Azure Sentinel, including on-prem and other cloud servers. Since we can install extensions on Azure Arc enabled VMs, we can use deployIfNotExist policies to automatically remediate non-compliant resources and install the MMA as an extension.
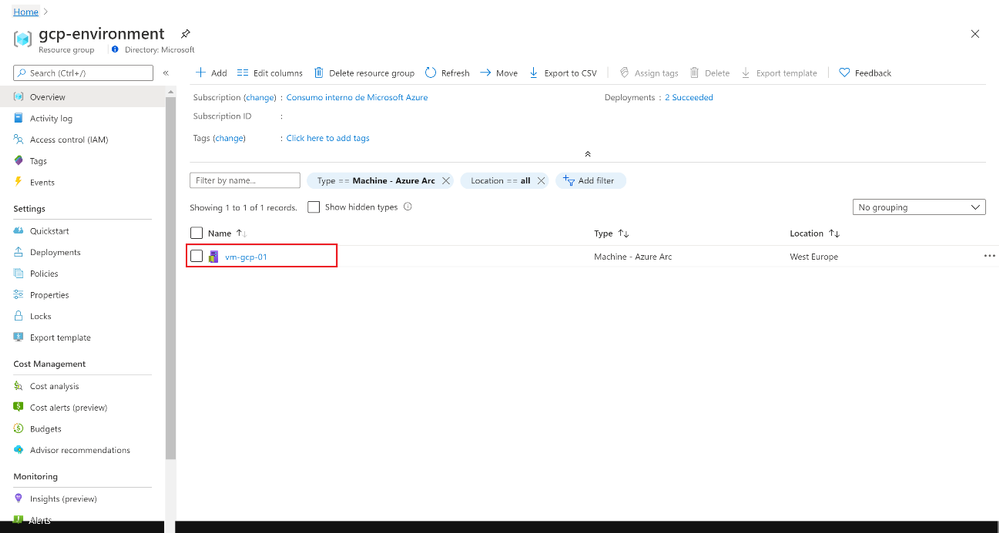
First, I created a Linux Virtual machine in Google Cloud Platform and installed the Azure Arc agent. As a result, you will be able to see this GCP VM on Azure as an Azure Arc connected VM that is now mapped to a Resource Group, Subscription and Region.
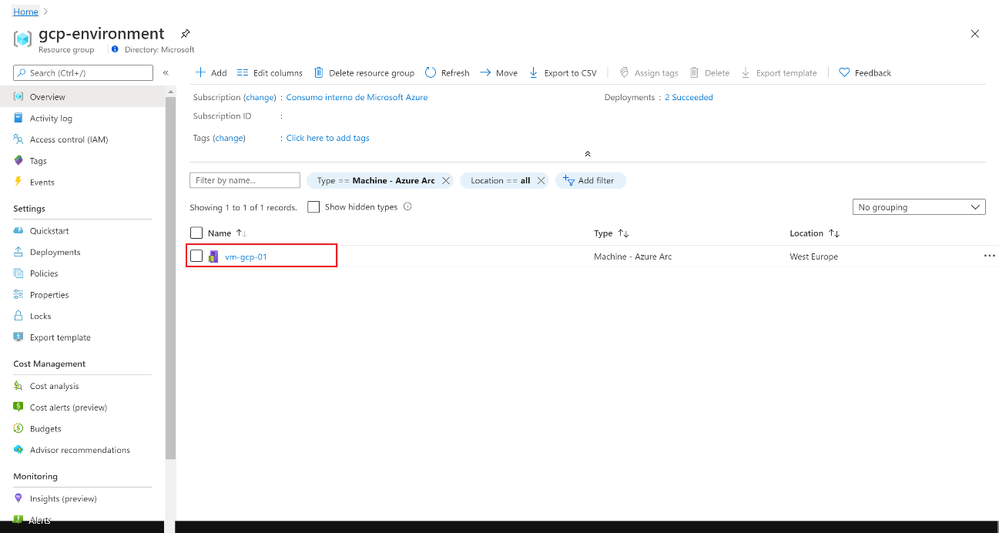
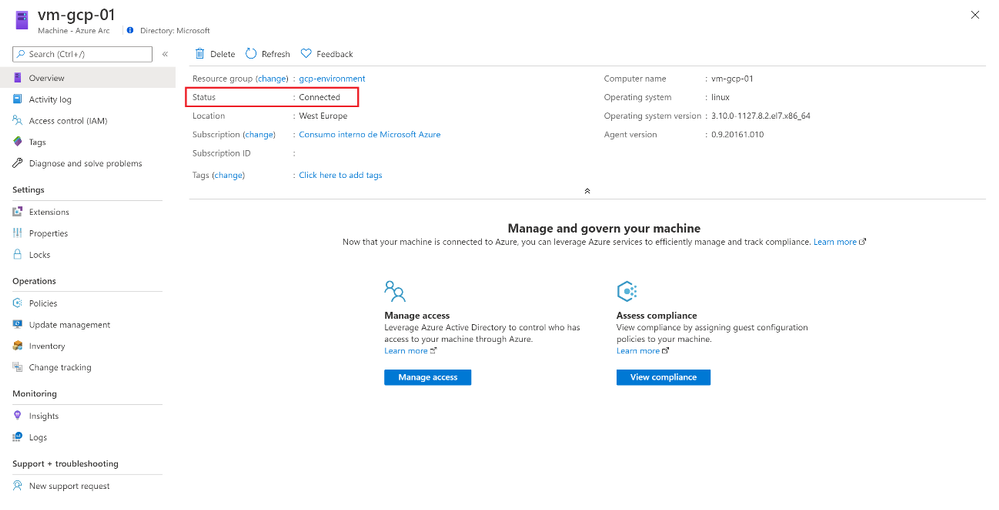
Now we can set up an Initiative to the Resource Group, In this case we will set up the initiative called “Enable Azure Monitor” and the scope will be the Resource Group (you could also apply it to the entire subscription).
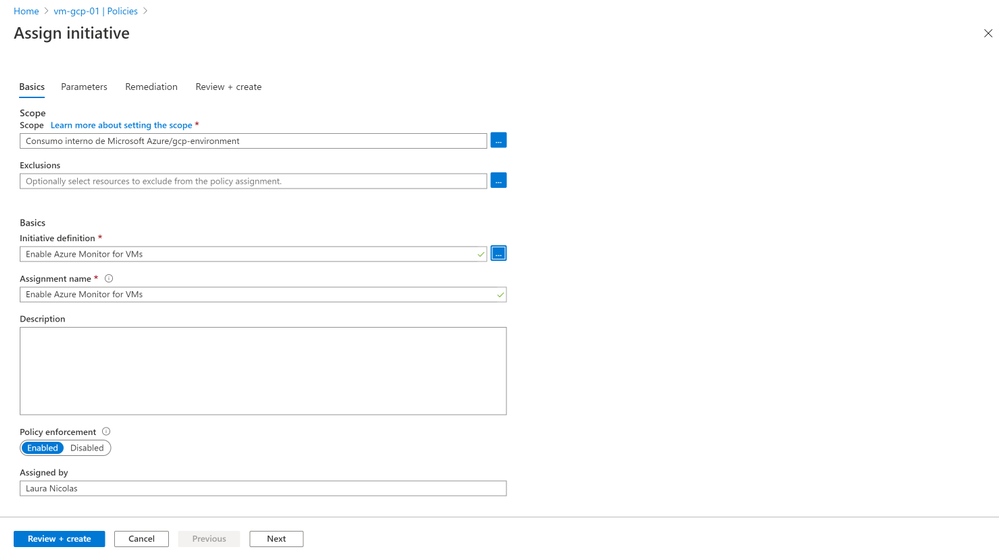
As part of the initiative, we need to provide the Log Analytics workspace we want to use to configure the agent to connect to. In this case, we will provide the information of the Log Analytics workspace where we have enabled Azure Sentinel.
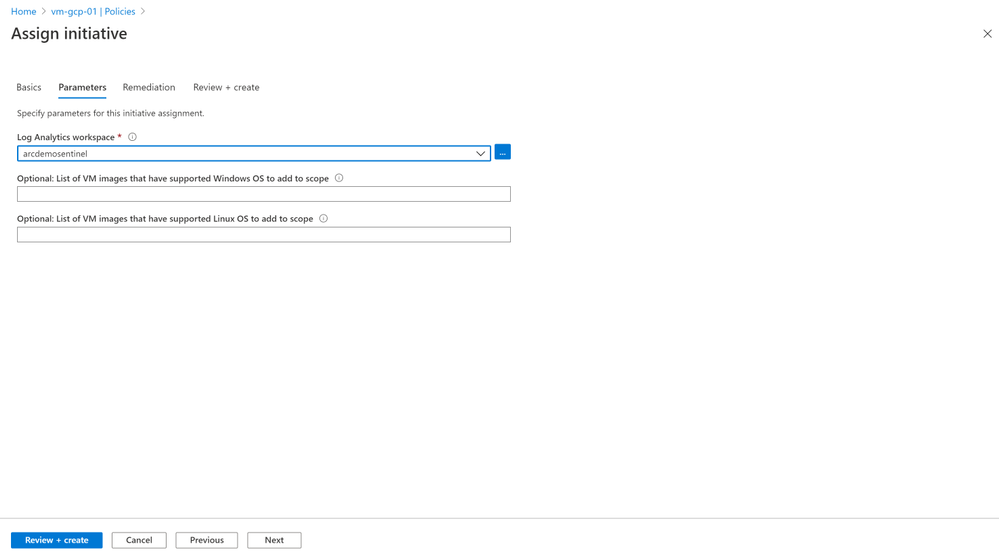
Then we also have the option to define how the policy should act in case it finds resources that are non-compliant, using a remediation task. The initiative we are using is of the type deployIfNotExists, therefore it has the option to modify the not compliant resource so it can be put into a compliant state. The remediation task we will use is “Deploy Log Analytics agent to Linux Arc machines”, the task will leverage the Azure Arc agent to deploy MMA as an extension.
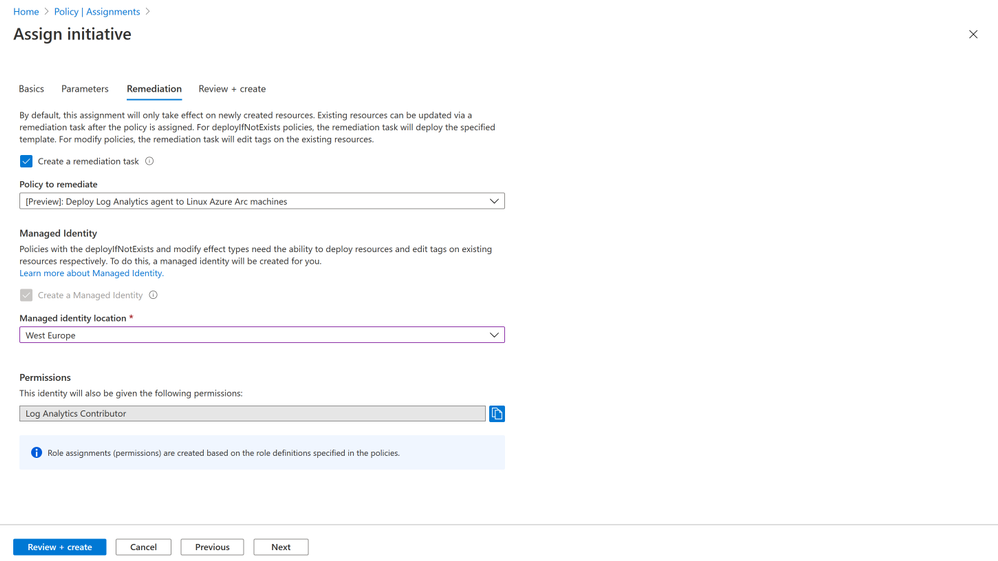
Once you have assigned the initiative, you will see that it will be evaluated (it may take 30 minutes to run the scan) and show that the server on GCP is not compliant.
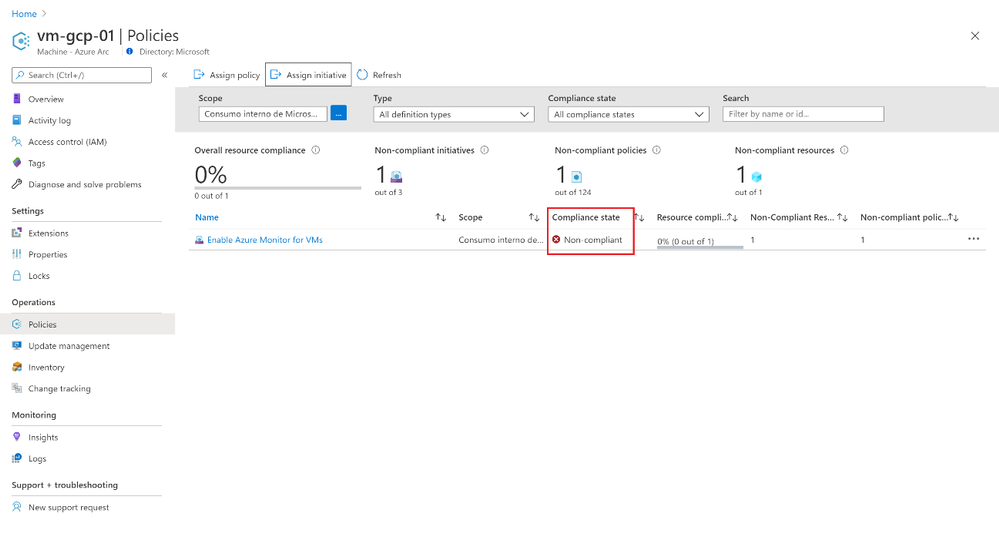
After we run the remediation task, we will see that the extension is deployed to the VM and we have a compliant Azure Policy report, with a Linux VM reporting to our Sentinel Log Analytics workspace.
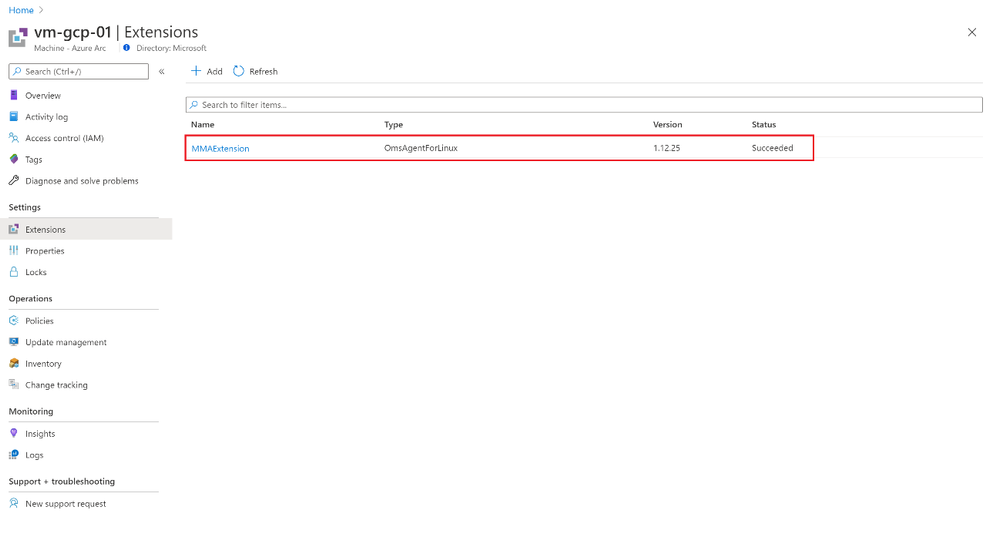
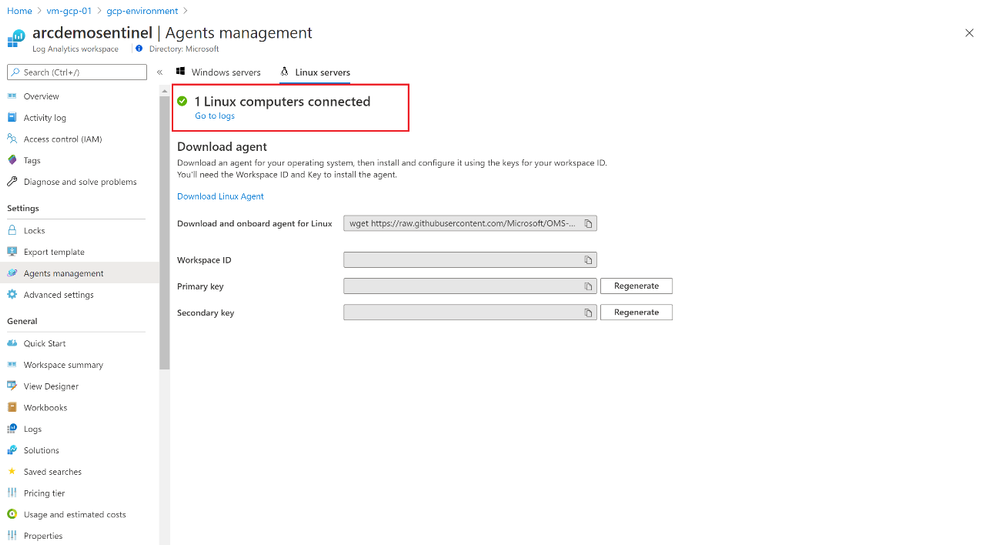
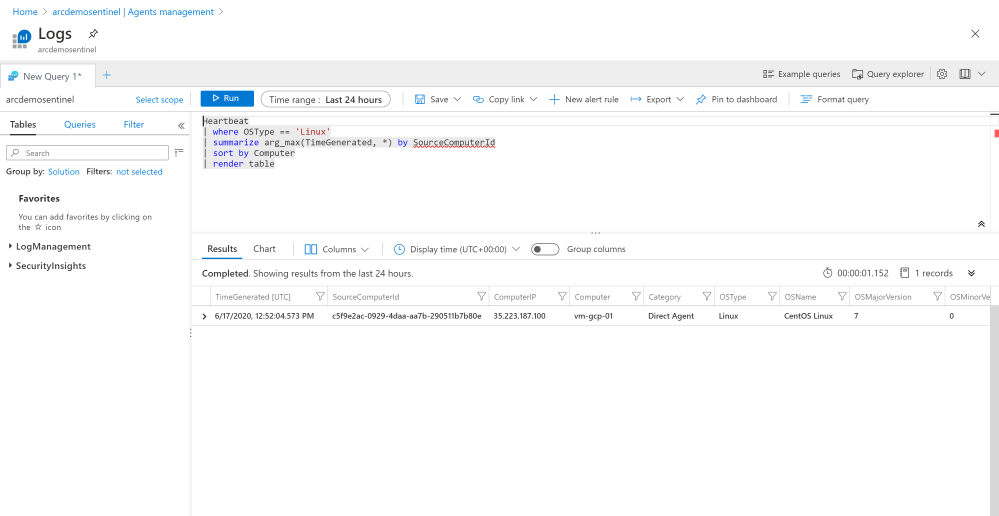
We can also verify that we are collecting hearbeats and security events from the VM.
Additional Resources:
by Scott Muniz | Jun 25, 2020 | Uncategorized
This article is contributed. See the original author and article here.
With all the changes in Azure, it is sometimes hard to keep track, that’s why I thought I would give you a quick update on a couple of exciting things I learned this week. In this update, I want to share a couple of things around updates on how Azure.com runs on Azure, Azure Migrate supports multiple credentials for discovery, updates for Azure IoT Hub message routing, simplified declarative deployments in Azure, and more! Also, tune in for our live stream later today.
Azure.com operates on Azure
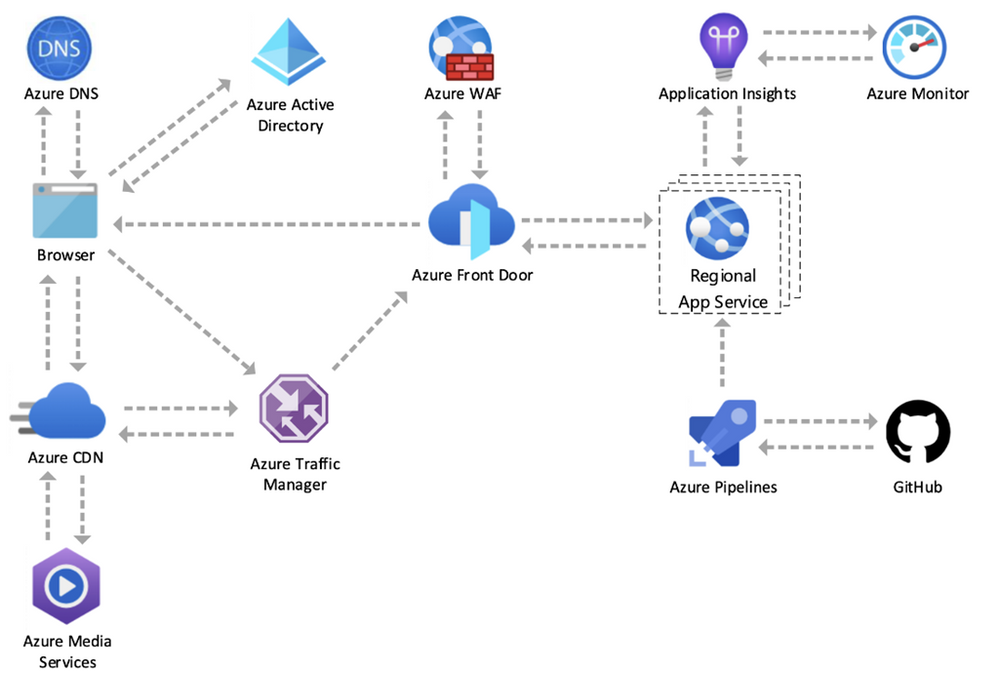
This week the team which runs Azure.com shared two very interesting blogs about the history of Azure.com and how they design and run Azure.com efficiently and with the right uptime. You will get a peek behind the Azure.com web page to show you how the Azure.com team thinks about running a major brand website on a global scale. The team also shares its design approach and best practices for security, resiliency, scalability, availability, environmental sustainability, and cost-effective operations—on a global scale.
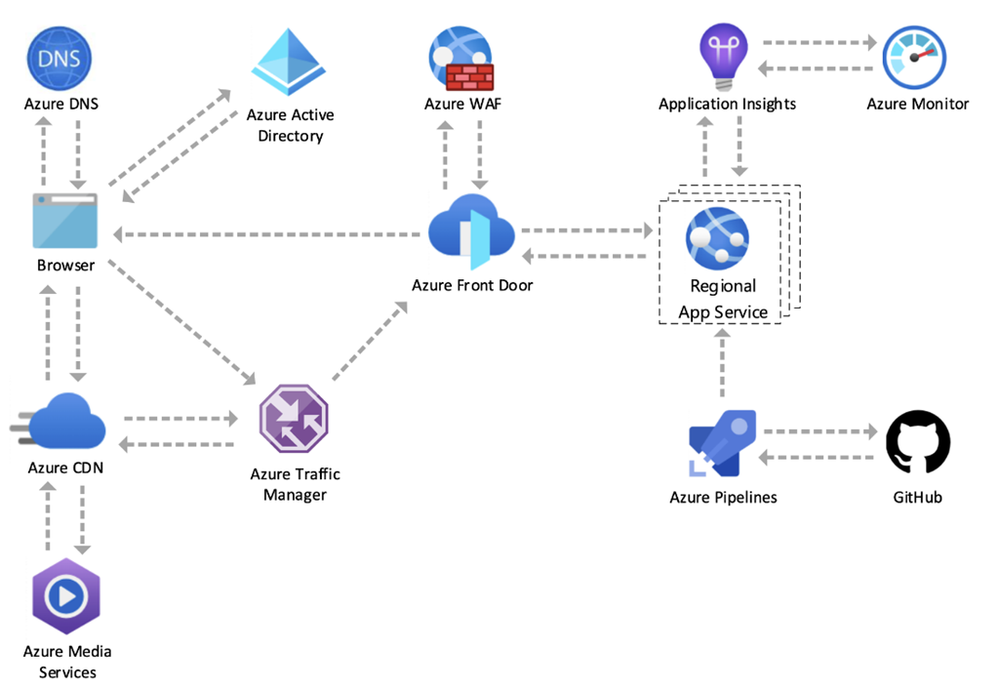 Azure.com operates on Azure
Azure.com operates on Azure
Check out the two blog posts here:
The AZ-104 Azure Administrator Exam is out of beta
This week the AZ-104 Azure Administrator Exam came out of beta.
Candidates for this exam should have subject matter expertise implementing, managing, and monitoring an organization’s Microsoft Azure environment.
Responsibilities for an Azure Administrator include implementing, managing, and monitoring identity, governance, storage, compute, and virtual networks in a cloud environment, plus provision, size, monitor, and adjust resources, when needed.
An Azure Administrator often serves as part of a larger team dedicated to implementing your organization’s cloud infrastructure.
If you took the exam while in beta, you are getting an email shortly about your results. If you are looking to study and learn for this exam, check out my AZ-104 Azure Administrator Exam Study Guide.
Azure Migrate now supports multiple credentials for discovery of physical server
Azure Migrate now supports adding multiple credentials for the discovery and assessment of physical servers (in preview). In addition, the number of servers that can be discovered per appliance has been increased from 250 to 1,000.
For more details, read the documentation.
Updates for monitoring and troubleshooting Azure IoT Hub message routing
Azure IoT Hub got several updates to message routing help reduce the learning curve and accelerate monitoring and troubleshooting, like Multidimensional, per-endpoint monitoring metrics are now available in Azure Monitor to help you identify metrics for each endpoint and gain more details to diagnose issues faster.
You can find the full list for Updates for monitoring and troubleshooting Azure IoT Hub message routing here.
Simplifying declarative deployments in Azure!
Early this week, Mark Russinovich (CTO of Microsoft Azure) shared new updates on how the team renewed the focus in Azure Resource Manager (ARM) template deployments with a focus on addressing some of the key challenges shared by our customers. The new updates include:
- Simplified authoring experience with Visual Studio Code
- What-if: Pre-deployment impact analysis
- Deployment scripts: completing the ‘last mile’ scenarios
- Management group and subscription provisioning at scale
- Continued focus on quality and reliability
But there is also more to come. Check out the full blog post here on Azure.com.
MS Learn Module of the Week

Cloud Concepts – Principles of cloud computing
Explore the core concepts of cloud computing and how it can help your business.
In this module, you will:
- Explore common cloud computing services
- Explore the benefits of cloud computing
- Decide which cloud deployment model is best for you.
Livestream
Tune in for our live stream later today.
Conclusion
I wish you a good weekend, and I hope this short blog post provided you with some news from this week. I know there is much more than just the things I listed here. I recommend that you follow the Azure announcements blog. If you have any questions, feel free to leave a comment.
Also, check out last week’s Az Update here.
by Scott Muniz | Jun 25, 2020 | Uncategorized
This article is contributed. See the original author and article here.
A few weeks ago, I was asked to talk about Azure Security Center in a virtual full-day security workshop. After my session, I got some great feedback from attendees, and from this feedback, I realized that I had touched a topic during my talk which made attendees think and which seems to be more or less unknown or unclear to many of our customers. This is why I decided to write this article to shine some light on Azure Secure Score and Azure governance.
Azure Security Center is a Cloud Security Posture Management (CSPM) and Cloud Workload Protection Platform (CWPP) solution, with Secure Score being one of the main features in the CSPM stack. The idea behind Secure Score is to give customers a comprehensive and unified overview of their cloud environments’ current security postures.
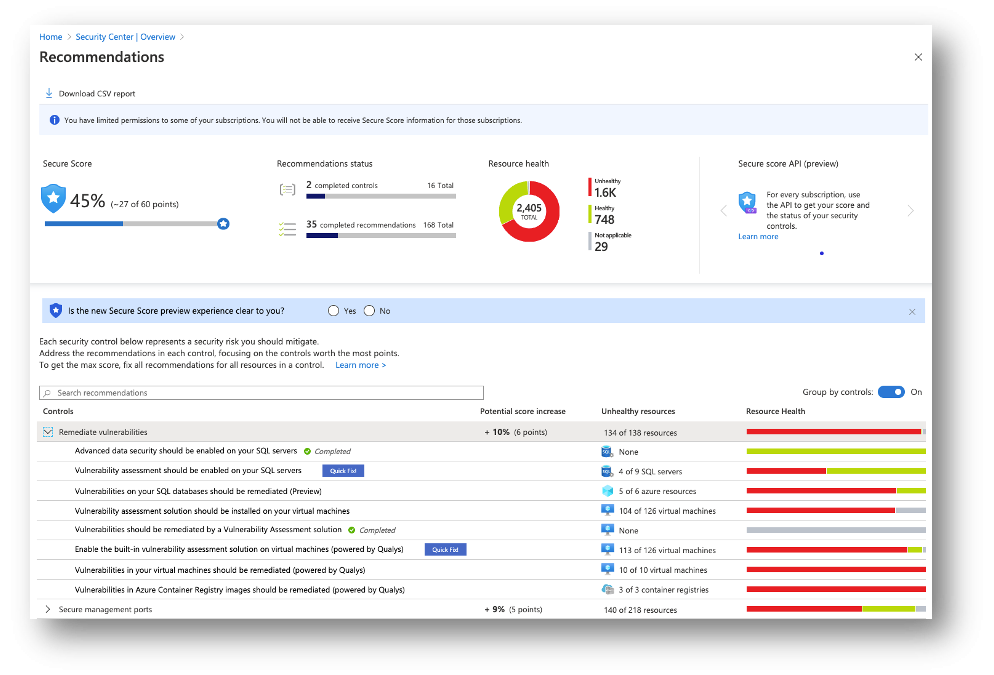
 Figure 1 – Secure Score, recommendations, and security controls
Figure 1 – Secure Score, recommendations, and security controls
Secure Score is based on recommendations which reflect industry standard and Microsoft security best-practices, such as the recommendations to enable MFA or to secure management ports. Recommendations are logically grouped in security controls. For more information about how Secure Score works, read Enhanced secure score in Azure Security Center.
The overall Secure Score in the example shown in Figure 1 is 45%. The first security control Remediate vulnerabilities contains several recommendations, some of which already have been completed for all resources in the given scope. In order to increase the Secure Score, not one recommendation needs to be completed for all resources, but all recommendations need to be completed for all flagged resources.. If all recommendations under the security control are remediated, your Secure Score increases by the value that is shown in the respective security control. This is because we want Secure Score to give customers valid and useful information without claiming security improvements which are not really secure. For example, if you would complete our recommendation to install an endpoint protection solution on a VM but then would not resolve health issues with this solution (which is a second recommendation), increasing the Secure Score would lead to a misassumption regarding the actual security posture of that workload.
How does secure score influence your governance?
Now that you understand Secure Score calculations from a high-level perspective, let’s take a look at what can influence Secure Scores over time. Of course, the goal is to increase your Secure Score because that means that your security posture has enhanced alongside. At the same time, the higher the Secure Score gets, the fewer recommendations will be left, making it easier to plan for remediation. The diagram shown in Figure 2 has an example of a secure score that is improving over time.
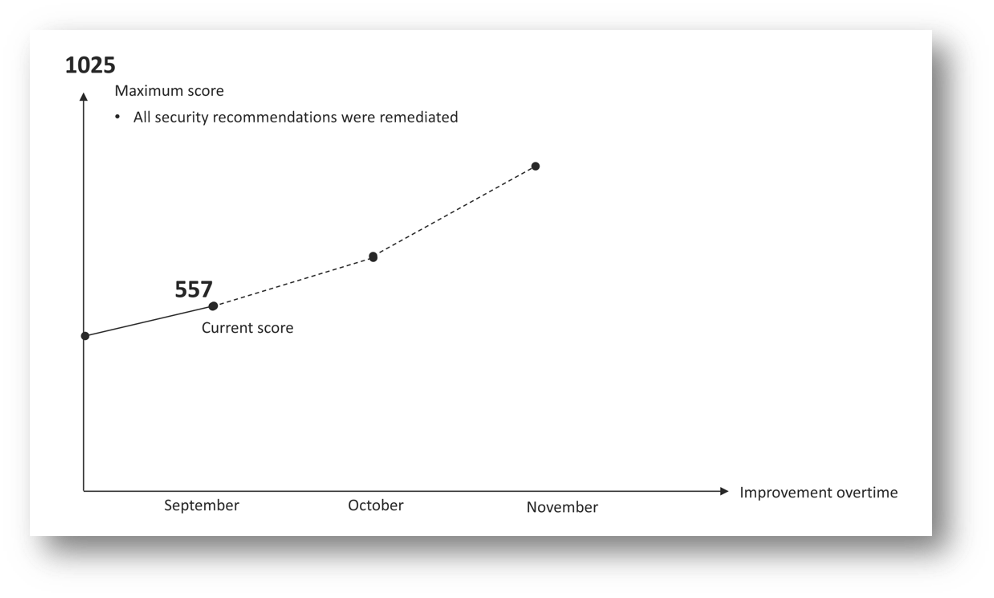 Figure 2 – Secure Score improvement over time
Figure 2 – Secure Score improvement over time
There are many strategies to continue driving the secure score up, I recommend you to read the Secure Score Survival Guide in order to understand some of these strategies.
Once you have invested time and effort in increasing your Secure Score, you want to make sure that it will not decrease by a serious percentage, again. The problem is that the remediation is always done for existing resources, not for new ones. For example, if you grant an Azure AD account write access to an Azure subscription without enabling it for MFA, or if you create new Azure VMs without making sure that their management ports are protected, or if you create new storage accounts without enabling secure transfer; your Secure Score will drop once you provision new resources which are not secure by default.
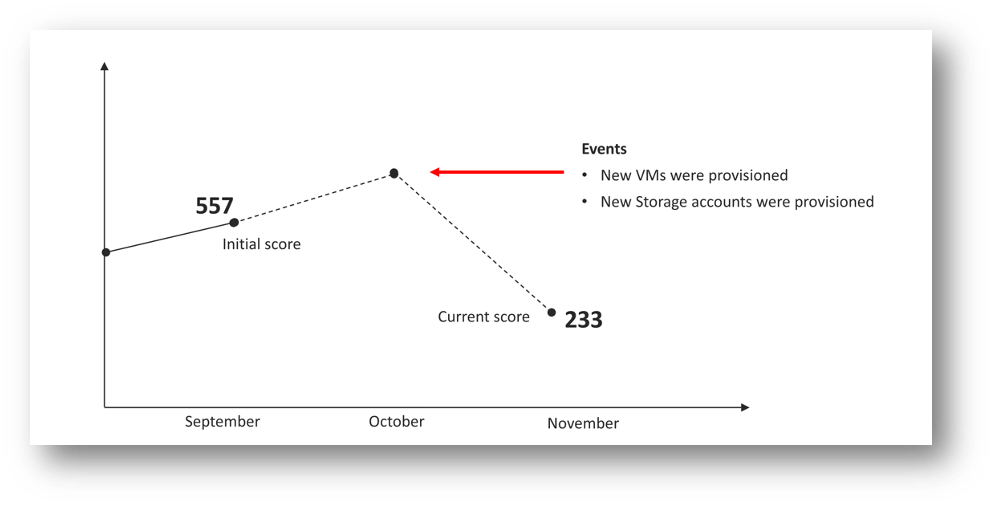 Figure 3 – Secure Score drops after resource creation
Figure 3 – Secure Score drops after resource creation
This is when Azure Governance comes into play. With Azure Policy you can make sure that only resources that adhere to your security principles and recommendations can be deployed, and with Azure Blueprints, you have a great tool to enable quick and repeatable creation of fully governed Azure environments. Furthermore, Blueprints enable you to ensure compliance and empower DevOps.
That said, every time you remediate a particular security recommendation or the entire security control, you need to make sure that this remediation also reflects in your deployment scenarios. Whatever recommendation you remediate, make sure to change your ARM templates and PowerShell deployment scripts accordingly. This way, you make sure that you will only deploy resources which are secure by default.
In large environments, remediation at scale is one of the most important aspects when it comes to leveraging Azure Security Center. No one wants to manually take care of 20,000 storage accounts and 2,300 VMs across 1,500 subscriptions. Azure Policy definitions, Logic App Playbooks, and PowerShell scripts are some immensely powerful tools within this context. With DINE (deploy-if-not-exist) policies, you can make sure that all resources in the affected scope will automatically be remediated (depending on the recommendation). When new resources are deployed, the respective policy will automatically make sure that the security recommendations will be met just after deployment. With PowerShell scripts, you can remediate existing resources, and with Logic App Playbooks, you can react on triggers, such as recurrence, or events, or you can directly run them from the recommendation in Azure Security Center. In our GitHub community, we have published a number of remediation scripts and templates which you can leverage for your environments.
Secure Score over time
Today, Secure Score reflects your current security posture at a given point in time. We have recently released the Secure Score API in public preview, which enables you to export and store your Secure Score at any time. As an example, we have published a LogicApp playbook on our Azure Security Center GitHub community, which will pull your Secure Score, controls, and assessments into an EventHub every 24 hours. This information can then be used for example to create custom PowerBI dashboards or be integrated into your own dashboards to show a Secure Score trend over time. You can also read this great post that shows how to operationalize the Secure Score API to send weekly briefings via email.
Takeaways
As you see, Azure Governance is an important part of security and should always be part of your strategy to enhance your security posture. We recommend our customers to leverage Secure Score as a great tool to determine their current security state and to use the Secure Score API to build a trending view that helps them understand where they came from and what they have already achieved on their journey to security. We also encourage you to join our GitHub community, and use the tools and scripts we have published. If you miss something, let us know, or create some artifacts by yourself which then can be added to the repository.
Thanks for reading and best regards,
Tom Janetscheck,
Senior Program Manager – CxE ASC Team
This post was reviewed by @Yuri Diogenes, Senior Program Manager – CxE ASC Team
by Scott Muniz | Jun 25, 2020 | Uncategorized
This article is contributed. See the original author and article here.
The Problem
When using the new Safari 13.1 browser with Intelligent Tracking Prevention (ITP), 3rd party cookies are not allowed by default to remove the ability for websites to track you using cookies.
When an iframe is hosted in a page, it’s cookies, even if they are for the origin in the frame are considered 3rd party if it is hosted in a page that is a different origin. This causes the cookies set for the SharePoint add-in webpart model to not be sent on subsequent requests, including the authentication cookie (fedauth).
The Solution
There is a solution to this by adding some code to request access to these cookies via a storage access API that has been implemented in Safari, and Firefox, as well as browsers based on their respective projects (webkit and mozilla) and has experimental/future support in Chrome and Edge (chromium) as well.
This script code will allow you to request access to the 3rd party cookies-
//check if the function ‘hasStorageAccess()’ exists on the document object
//this lets you know that the storage access API is there
if(undefined !== document.hasStorageAccess){
var promise = document.hasStorageAccess();
promise.then(
function (hasAccess) {
// Boolean hasAccess says whether the document has access or not.
document.requestStorageAccess()
},
function (reason) {
// Promise was rejected for some reason.
Console.log(“Storage request failed: “ + reason);
}
);
}
If you have a SharePoint add-in that is running in an iframe in a SharePoint page, then you would add the above code to your provider hosted page.
If you run into problems with cookies, or authentication that only seem to affect the Safari browser, you can confirm that ITP is causing the issue by disabling the feature that is blocking third party cookies called Intelligent Tracking Protection (ITP).
To disable this setting, navigate to:
Preferences -> Privacy
Then uncheck the Prevent cross-site tracking option.
Disabling the feature for normal use is not recommended, as it is a security measure that is designed to block malicious scripts.
Future development testing
If you are developing a new SharePoint provider hosted add-in or an SPFx add-in that uses content in an iframe or calls to a 3rd party site (with another domain) then you can test the script above by turning on the Storage Access API feature in the experimental features.
In the MS Edge (chromium) browser use this URL-
edge://flags/
In Chrome, use this URL-
chrome://flags/
Find and enable the ‘Storage Access API’ feature to enable the method used by the script.
There will likely be some updates here to clarify behavior.
by Scott Muniz | Jun 25, 2020 | Uncategorized
This article is contributed. See the original author and article here.
Update 2006 for the Technical Preview Branch of Microsoft Endpoint Configuration Manager has been released. Now the Company Portal can be your cross-platform experience in Microsoft Endpoint Manager. You can now use a preview version of the Company Portal on co-managed devices. By configuring co-managed devices to also use the Company Portal, you can provide a consistent user experience on all devices.
This preview version of the Company Portal supports the following actions:
- Launch the Company Portal app on co-managed devices and sign in with Azure Active Directory (Azure AD) single sign-on (SSO).
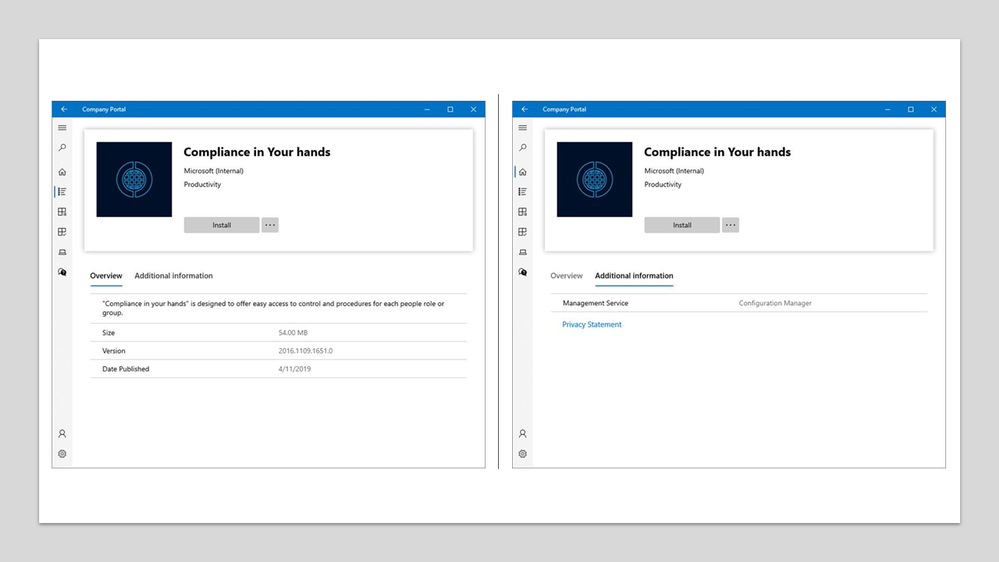
- View available and installed Configuration Manager apps in the Company Portal alongside Intune apps.
- Install available Configuration Manager apps from the Company Portal and receive installation status information.
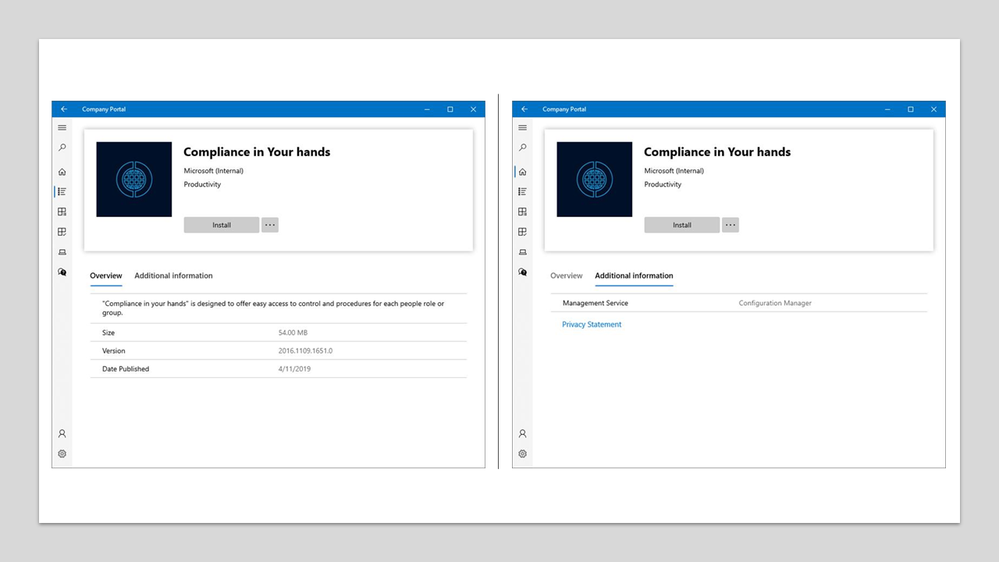 ConfigMgr apps in Company Portal
ConfigMgr apps in Company Portal
Learn more about Using the Company Portal app on co-managed devices.
This preview release also includes:
Improvements to available apps via CMG – An internet-based, domain-joined device that isn’t joined to Azure Active Directory (Azure AD) and communicates via a cloud management gateway (CMG) can now get apps deployed as available. The Active Directory domain user of the device needs a matching Azure AD identity. When the user starts Software Center, Windows prompts them to enter their Azure AD credentials. They can then see any available apps.
Intranet clients can use a CMG software update point – Intranet clients can now access a CMG software update point when it’s assigned to the boundary group. Admins can allow intranet devices to scan against a CMG software update point in the following scenarios:
- When an internet machine connects to the VPN, it will continue scanning against the CMG software update point over the internet.
- If the only software update point for the boundary group is the CMG software update point, then all intranet and internet devices will scan against it.
Improvements to task sequences via CMG – This release includes the following improvements to deploy task sequences to devices that communicate via a cloud management gateway (CMG):
- Support for OS deployment: With a task sequence that uses a boot image to deploy an OS, you can deploy it to a device that communicates via CMG. The user needs to start the task sequence from Software Center.
- This release fixes the two known issues from Configuration Manager current branch version 2002.
Management insights to optimize for remote workers – This release adds a new group of management insights, Optimize for remote workers. These insights help you create better experiences for remote workers and reduce load on your infrastructure. The insights in this release primarily focus on VPN.
Improvements to VPN boundary type – This release improves upon the new VPN boundary type first introduced in technical preview version 2005. You can now create more than one VPN boundary, and can detect the connection by the VPN name or description.
Tenant Attach: Improvements to Configuration Manager actions in Microsoft Endpoint Manager admin center – This release introduces a number of improvements to the administration of Configuration Manager devices in Microsoft Endpoint Manager admin center. Improvements include:
- Configuration errors now include links to documentation to help you troubleshoot.
- You can re-evaluate applications.
- User available applications now appear in the Applications node for a ConfigMgr device
CMG support for endpoint protection policies – While the cloud management gateway (CMG) has supported endpoint protection policies, devices required access to on-premises domain controllers. Starting in this release, clients that communicate via a CMG can immediately apply endpoint protection policies without an active connection to Active Directory.
Import previously created Azure AD application during tenant attach onboarding – During a new onboarding, an administrator can specify a previously created application during onboarding to tenant attach.
Improvements to client upgrade on a metered connection – Starting in Configuration Manager technical preview version 2005, you could install and upgrade the client when you allowed client communication on a metered connection. You can now also configure the client setting Client communication on metered internet connections to Limit. This option reduces the client communication on a metered network, but now still allows the client to stay current.
Improvements to managing device restarts – Configuration Manager provides many options to manage device restart notifications. Based on your UserVoice feedback, you can now configure client settings to prevent devices from automatically restarting when a deployment requires it. By default, Configuration Manager can still force devices to restart.
Improved support for Windows Virtual Desktop – The Windows 10 Enterprise multi-session platform is available in the list of supported OS versions on objects with requirement rules or applicability lists.
Direct links to Configuration Manager Community hub items – You can now easily navigate to and reference items in the Configuration Manager console Community hub node with a direct link. The intention for this feature is for easier collaboration and being able to share links to Community hub items with your colleagues. Currently, you’ll see these links shared by the Configuration Manager team and in the documentation.
Update 2006 for Technical Preview Branch is available in the Microsoft Endpoint Configuration Manager Technical Preview console. For new installations, the 2002 baseline version of Microsoft Endpoint Configuration Manager Technical Preview Branch is available on the Microsoft Evaluation Center. Technical Preview Branch releases give you an opportunity to try out new Configuration Manager features in a test environment before they are made generally available.
We would love to hear your thoughts about the latest Technical Preview! Send us Feedback about product issues directly from the console and our UserVoice page for ideas about new features.
Thanks,
The Configuration Manager team
Configuration Manager Resources:
Documentation for Configuration Manager Technical Previews
Try the Configuration Manager Technical Preview Branch
Documentation for Configuration Manager
Microsoft Endpoint Manager announcement
Microsoft Endpoint Manager vision statement
Configuration Manager Forums
Configuration Manager Support







Recent Comments