by Scott Muniz | Aug 21, 2020 | Uncategorized
This article is contributed. See the original author and article here.
We announced the general availability of workload isolation for Azure Synapse Analytics which allows data engineers to configure and manage resources across their workloads to meet their business and performance objectives. This experience is not only available using familiar T-SQL syntax but we have also introduced the public preview of a graphical user interface in the Azure portal to provide a guided experience to the entire workload management process.
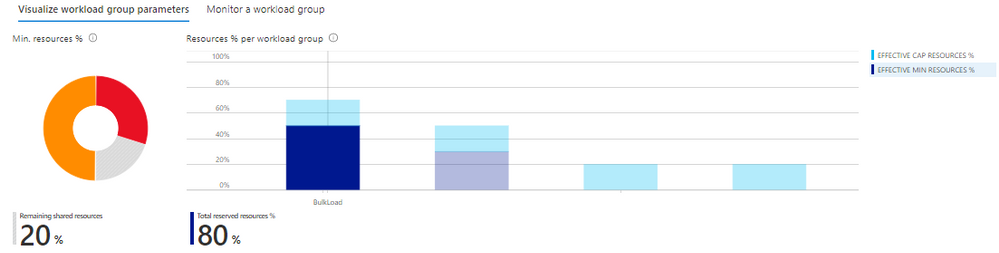
The Azure portal workload management experience comes with built-in commonly used views and charts which dynamically update allowing you to:
- Immediately identify how much shared resources are available that have not been allocated and reserved to a particular workload group across the entire SQL pool. You can also quickly understand the distribution of resources across your workload groups.

- Leverage built-in charts to monitor resource allocation, query timeouts, active and queued queries per workload group.
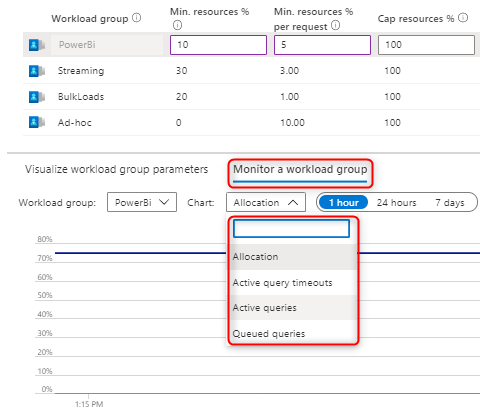
- Pinpoint changes in the Effective Values of your workload group based on your service level objective and shared resources.
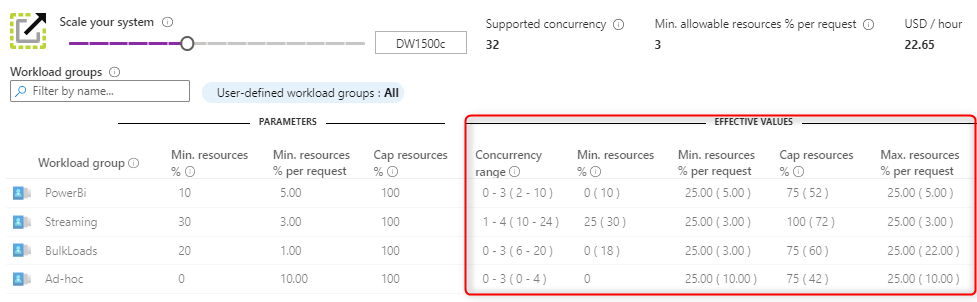
Using these views and charts, you can balance resource demands of various workloads under concurrency and ensure your workload groups are not underutilized or overloaded. This can be done easily by creating, updating, or even deleting workload groups and classifiers both in T-SQL and directly in the portal:
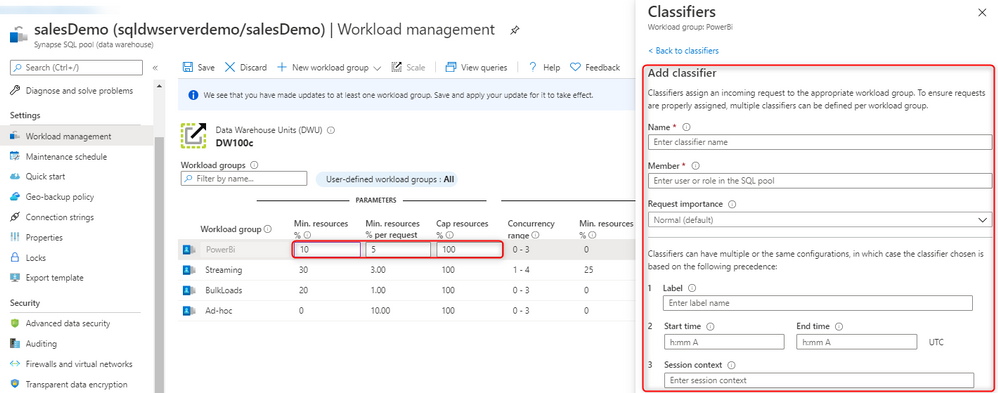
The process of employing effective workload management practices has never been easier with the code-free experience in the Azure portal.
Try it out today! If you have feedback on the preview of this experience, reach out to the following distribution list: SynapseSQLStudioFeedback@service.microsoft.com.
For more information on workload management, see the following documentation:

by Scott Muniz | Aug 21, 2020 | Uncategorized
This article is contributed. See the original author and article here.

Microservices communication: Rabbitmq and Asp.net core
Damien Doumer is a software developer and Microsoft MVP in development technologies, who from Cameroon and currently based in France. He plays most often with ASP.Net Core and Xamarin, and builds mobile apps and back-ends. He often blogs, and he likes sharing content on his blog at https://doumer.me. Though he’s had to deal with other programming languages and several frameworks, he prefers developing in C# with the .Net framework. Damien’s credo is “Learn, Build, Share and Innovate”. Follow him on Twitter @Damien_Doumer.

ASP.NET MVC: Load Page with Data on Bootstrap Modal
Asma Khalid is an Entrepreneur, ISV, Product Manager, Full Stack .Net Expert, Community Speaker, Contributor, and Aspiring YouTuber. Asma counts more than 7 years of hands-on experience in Leading, Developing & Managing IT-related projects and products as an IT industry professional. Asma is the first woman from Pakistan to receive the MVP award three times, and the first to receive C-sharp corner online developer community MVP award four times. See her blog here.

Install and Configure Power BI Report Server Step by Step
Mohamed El-Qassas is a Microsoft MVP, SharePoint StackExchange (StackOverflow) Moderator, C# Corner MVP, Microsoft TechNet Wiki Judge, Blogger, and Senior Technical Consultant with +10 years of experience in SharePoint, Project Server, and BI. In SharePoint StackExchange, he has been elected as the 1st Moderator in the GCC, Middle East, and Africa, and ranked as the 2nd top contributor of all the time. Check out his blog here.

Microsoft Teams provisioning with Power Automate and Graph API
Vesku Nopanen is a Principal Consultant in Office 365 and Modern Work and passionate about Microsoft Teams. He helps and coaches customers to find benefits and value when adopting new tools, methods, ways or working and practices into daily work-life equation. He focuses especially on Microsoft Teams and how it can change organizations’ work. He lives in Turku, Finland. Follow him on Twitter: @Vesanopanen

SharePoint online Highlighted Content Web Part
John Naguib is an Office Servers and Services MVP. He’s also a Solution Architect and Senior Consultant, with a deep knowledge of SharePoint. In addition, he has a strong .net application development background and is knowledgable in Office 365, Azure and several Microsoft products. John is a recognized expert within the IT industry, as he’s published several gold award articles on Microsoft TechNet blogs and spoken at several events. He is based in Egypt. Follow him on Twitter @johnnaguib.
by Scott Muniz | Aug 21, 2020 | Uncategorized
This article is contributed. See the original author and article here.
An updated version of SQL Server Management Pack is ready. It has many new features which are mostly based on your feedback.
Please download at:
Microsoft System Center Management Pack for SQL Server
What’s New
-
Added a new “Securables Configuration Status” monitor targeted to SQL Server databases
-
Updated the “Product Version Compliance” monitor with the most recent versions of public updates for SQL Server
-
Updated the “Securables Configuration Status” monitor targeted to the DB Engine when a SQL Server instance participates in Availability Groups
-
Removed the “Securables Configuration Status” monitor targeted to the Availability Replica as non-useful
-
Updated the “SQL Server Database Engines” discovery; the “Netbios Computer Name” property is now uppercased.
- Added reports from version-specific management packs for SQL Server
- Updated monitor “Job Duration” to add current job run’s duration to its alert description
- Updated Web Console version of SQL MP Dashboards to support SCOM 2019 UR1
- Updated alert description of monitor “Securables Configuration Status”
- Added “CheckStartupType” property to SSIS Health Status monitor
- Revised columns of SQL Agent and SQL Agent Jobs state views
- Updated display strings
Issues Fixed
- Fixed error “Unsupported path format” in workflows targeting Filegroups
- Fixed discovery error on non-readable availability replicas
- Fixed wrong Run As profile in SSIS Seed Discovery
- Fixed issue that caused rule “Disable Discovery of Selected DB Engines” to fail
- Fixed discovery issue for databases in recovering state
- Fixed issue in monitor “Securables Configuration Status” when it went critical on Shared-Memory-only SQL Servers
-
Fixed the Alerting Rules data source to avoid an alert storm after exiting maintenance mode
-
Fixed the SQL Log Reader data source to support changing of the SQL Authentication method
-
Fixed the Performance Reader data source to support changing of the SQL Authentication method
We are looking forward to hearing your feedback.
by Scott Muniz | Aug 21, 2020 | Azure, Microsoft, Technology, Uncategorized
This article is contributed. See the original author and article here.
It is practical to enable access to the developer portal for users from multiple Azure Active Directories. The following instructions show you how to manage the external groups of multiple tenants.
Prerequisites
NoteThis feature is available in the Premium, Standard and Developer tiers of API Management.
Instructions
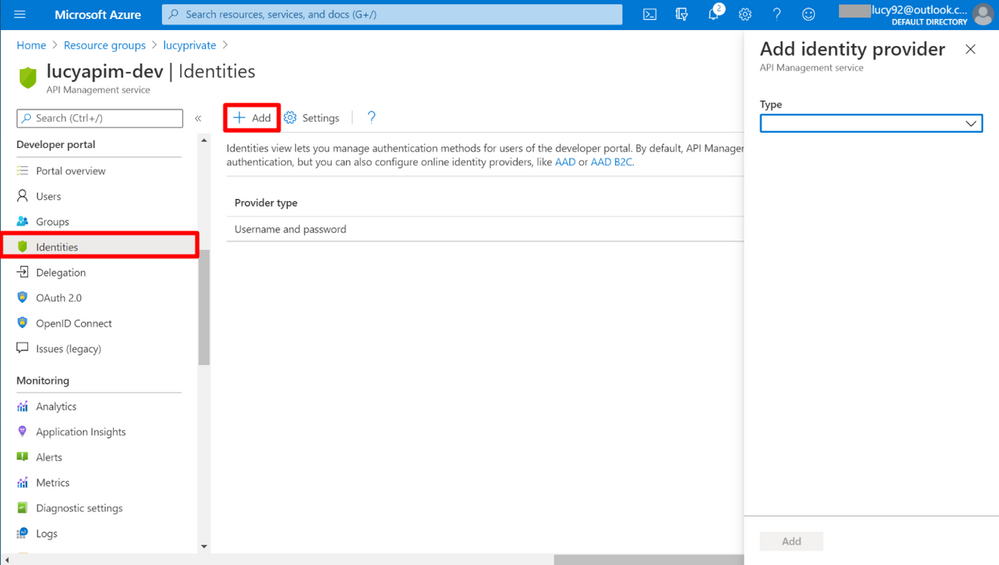
1. Go to the APIM instance. Select Identities on the portal. Click the button + Add on the top, then you will see the Add identity provider pane appears on the right.
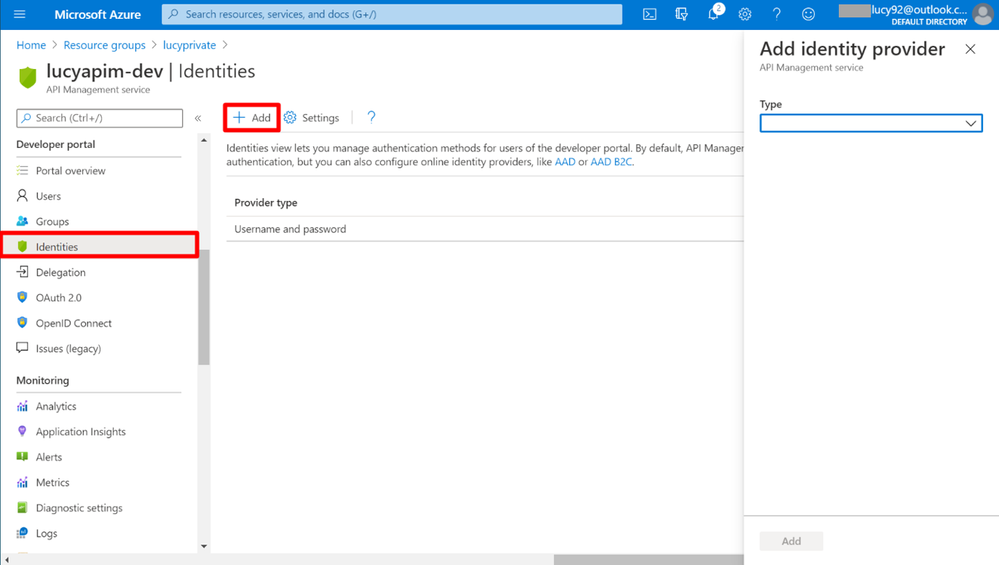
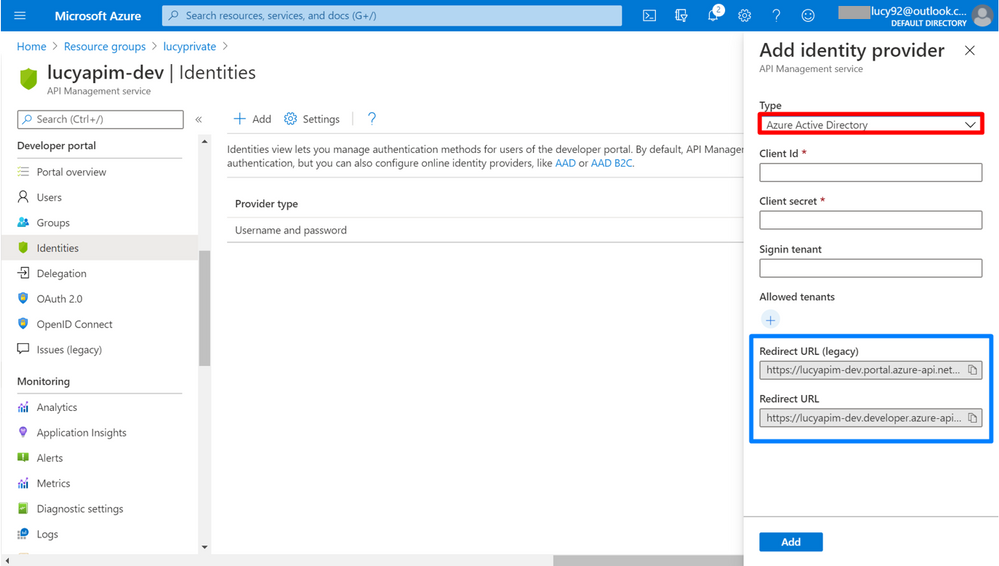
2. Select Azure Active Directory on the pane. The Request URL (legacy) is used for the Developer Portal (legacy), while the Request URL is used for the Developer Portal. In this article, we will use the Developer Portal as a sample.
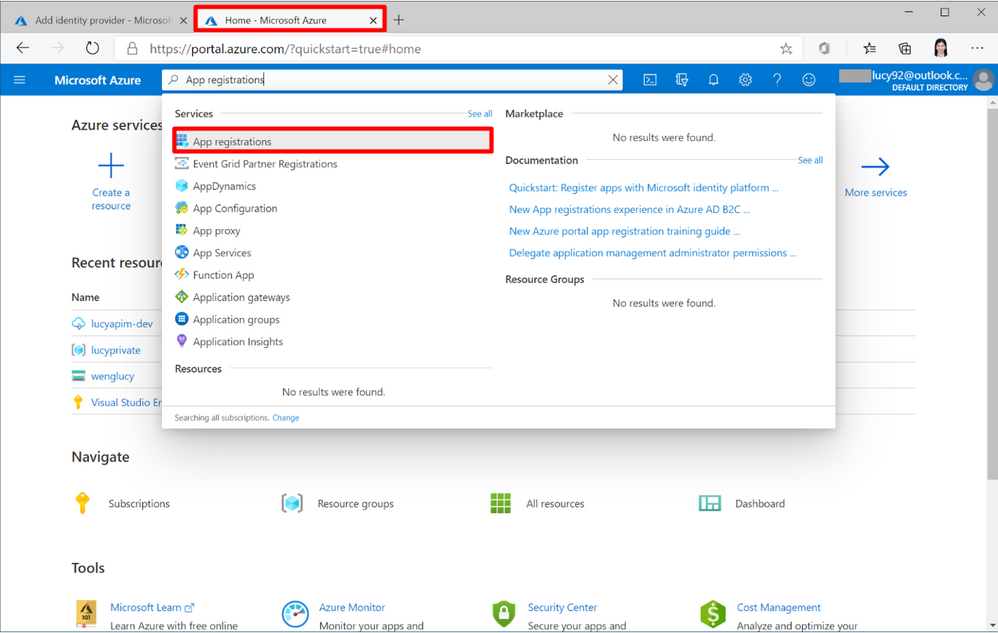
3. Open a new Tab on the browser. Select the service App registrations.
4. Click the button + New Registration.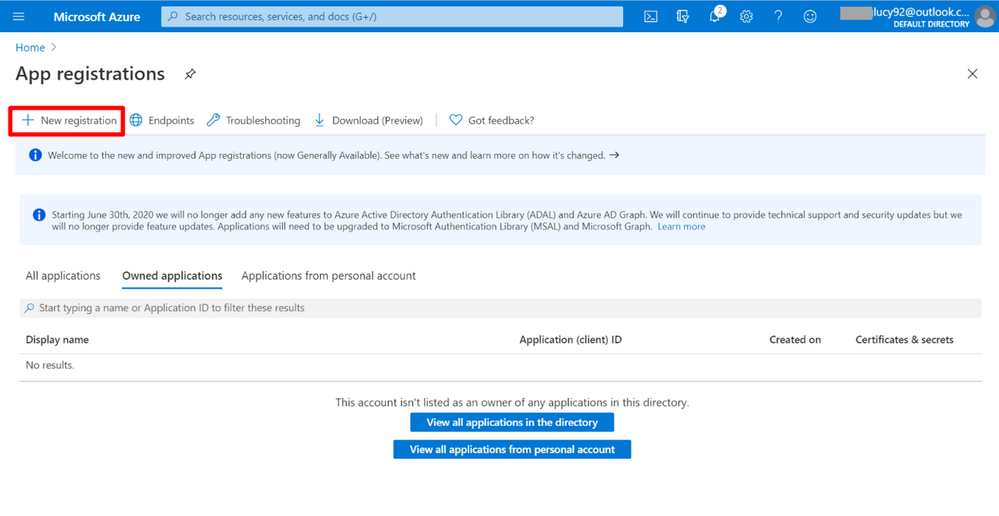
5. Give the new registration a meaningful name. Set Supported account types to Accounts in any organizational directory (Any Azure AD directory – Multitenant). Set Redirect URI to the value you got from step 2. Choose Register.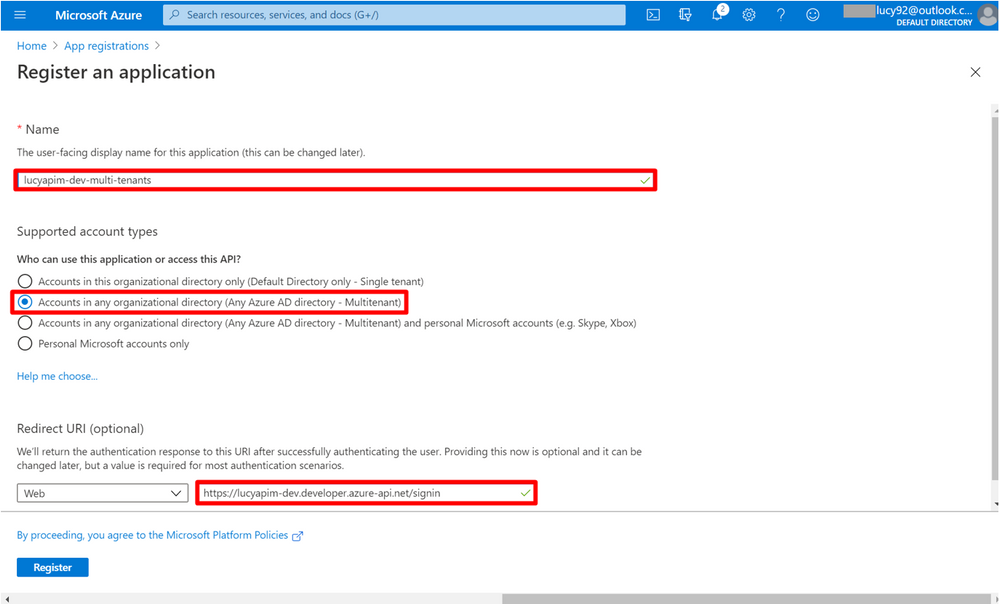
6. On the App registrations portal, copy the Application (client) ID and the Directory (tenant) ID.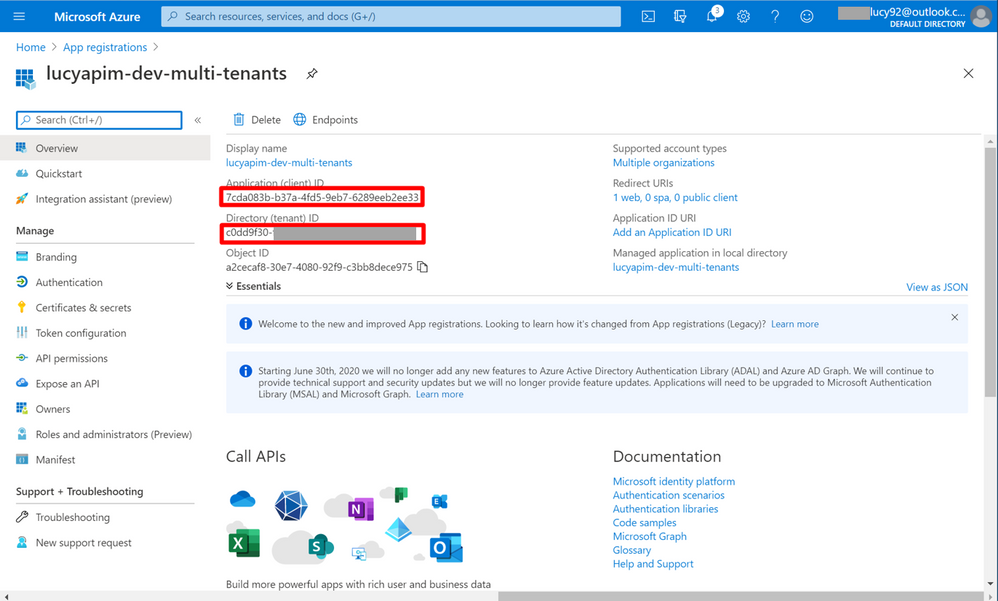
7. Go back to the API Management portal. Paste Application (client) ID into Client Id and paste Directory (tenant) ID into Signin tenant.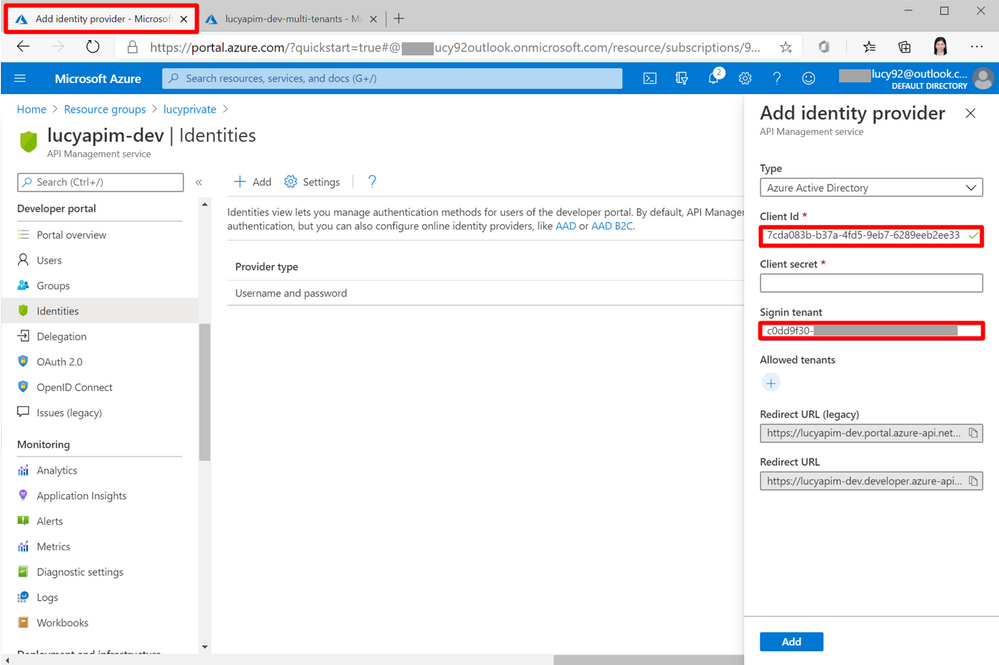
8. Go to the App registration portal. Select Certificates & secrets. Select the button + New client secret. To add a new client secret, give it a meaningful name and select the button Add.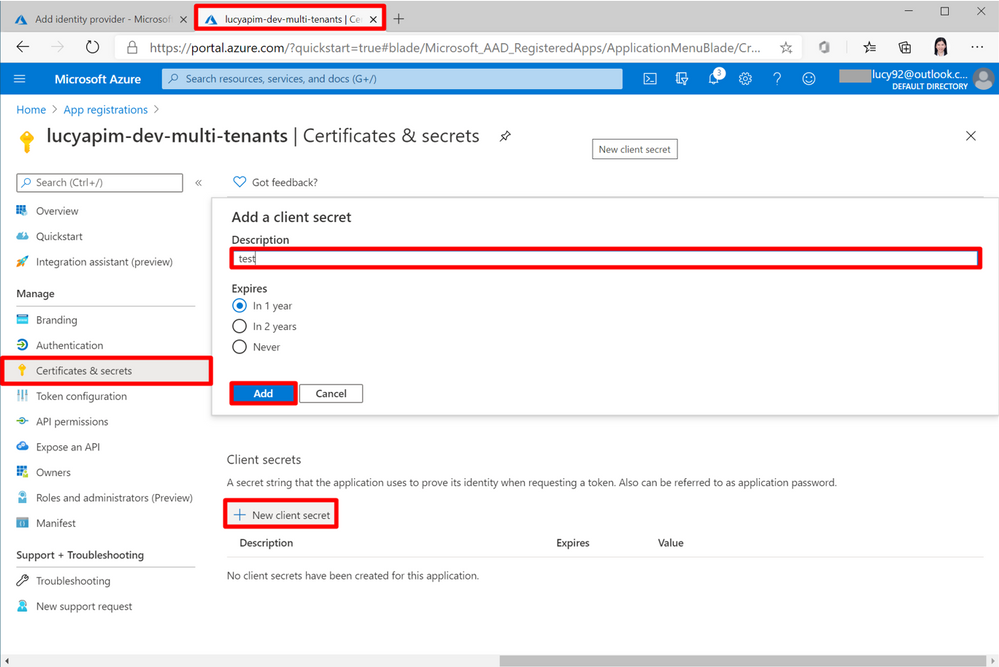
9. Copy the secret value immediately, because when you leave the page, you can never see the secret again.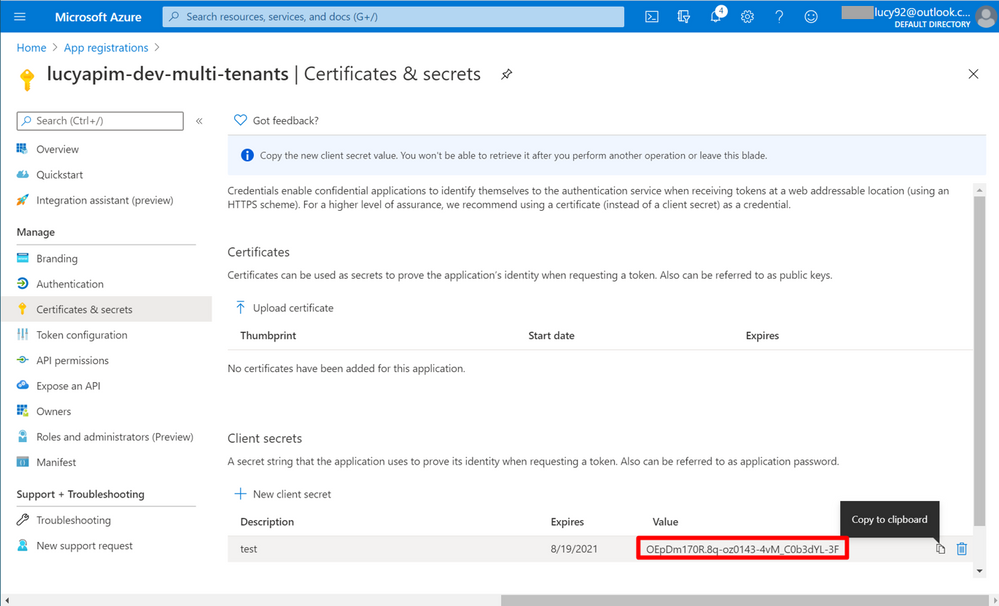
10. Go back to the APIM portal. Paste the secret into Client secret and select Add.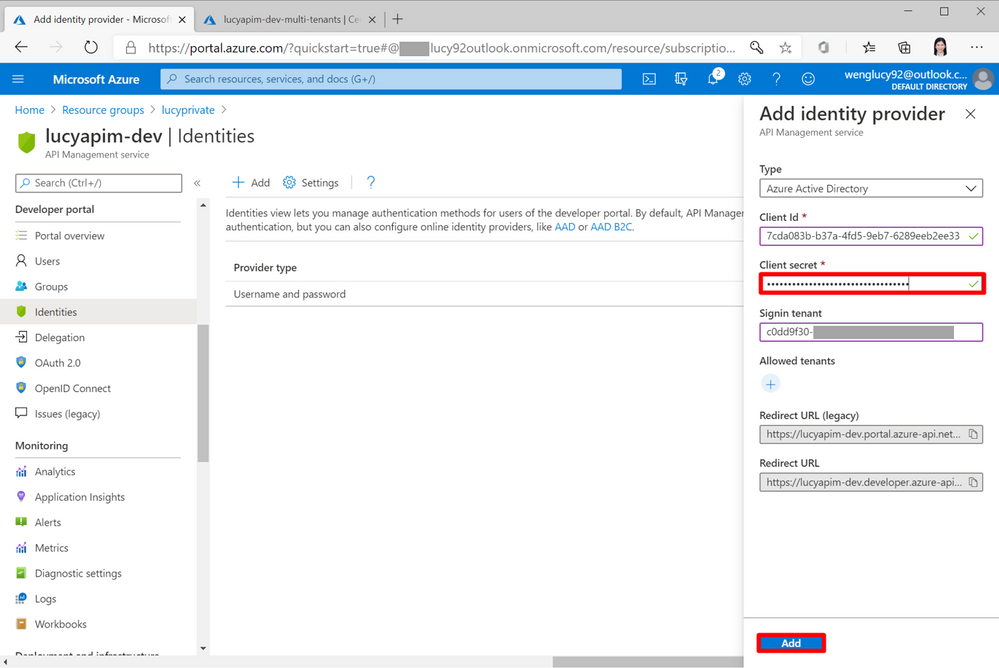
11. Select Group on the right pane. Then you will see that a new button + Add Azure AD group displays on the portal now.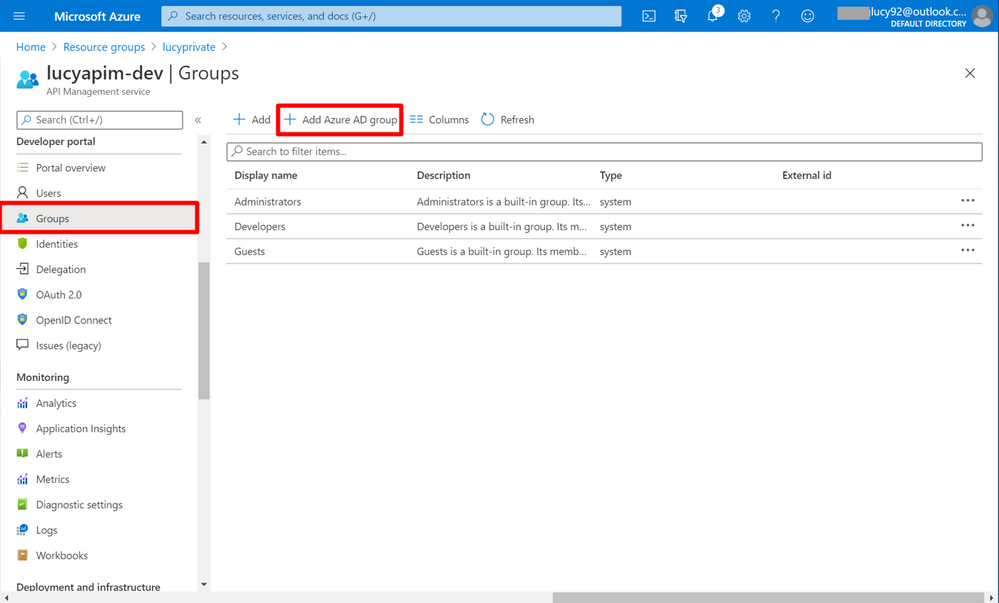
12. Then go to the App registration portal. Select Authentication. Choose ID token. Click the button Save.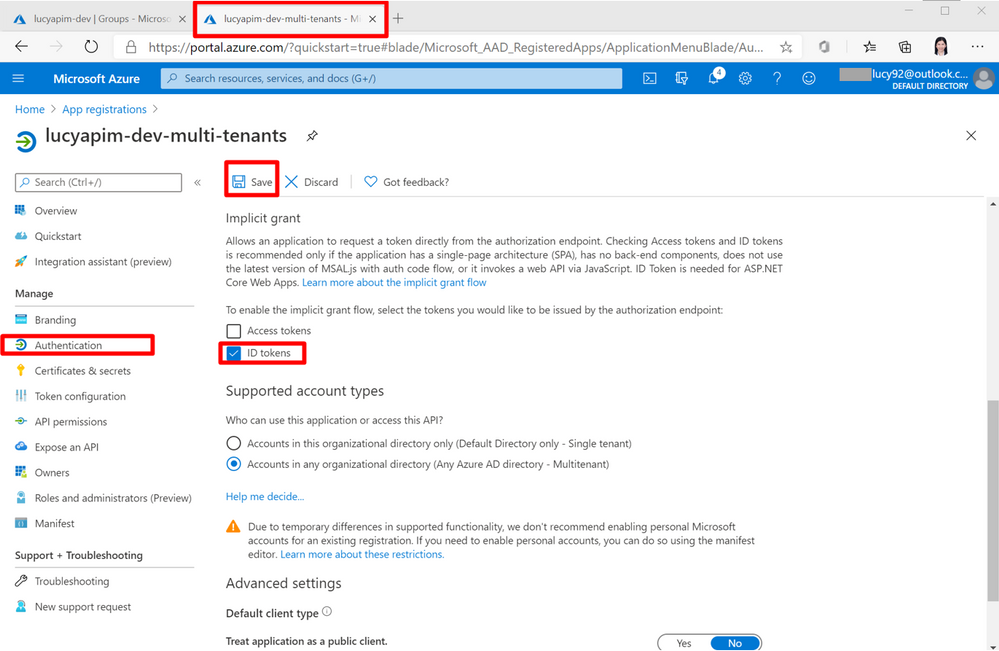
13. Select API permission on the right pane. Click the button + Add a permission.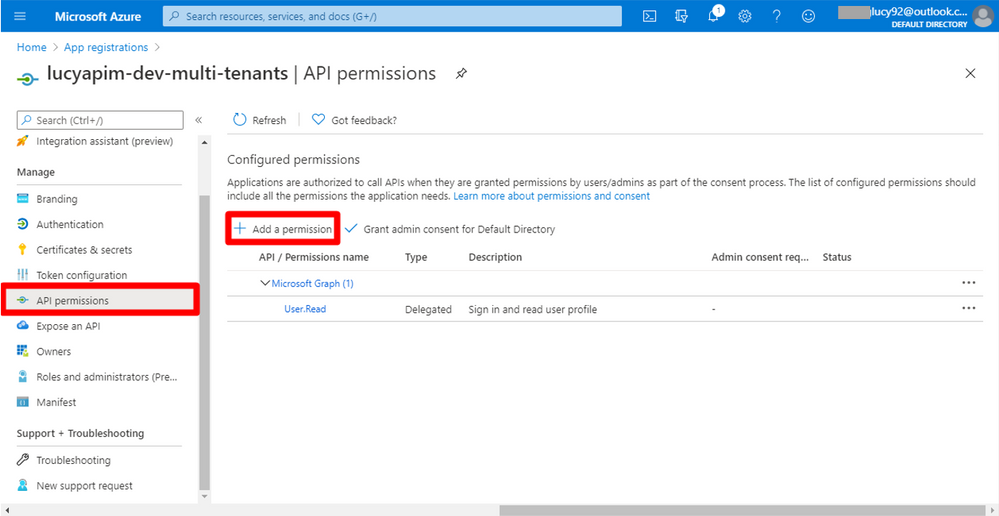
14. Select Azure Active Directory Graph under the Supported legacy APIs.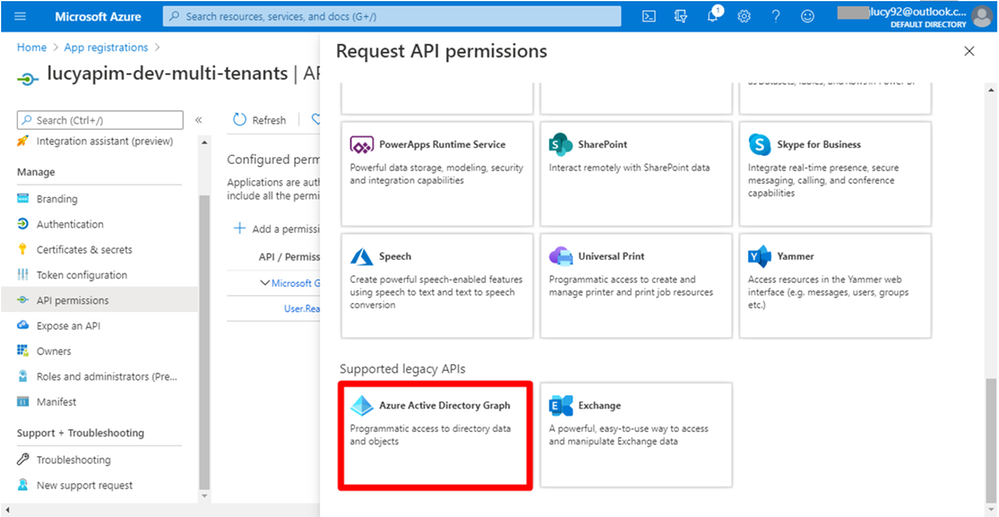
15. Select Application permissions. Choose the permission Directory.Read.All. Then Click the button Add permission.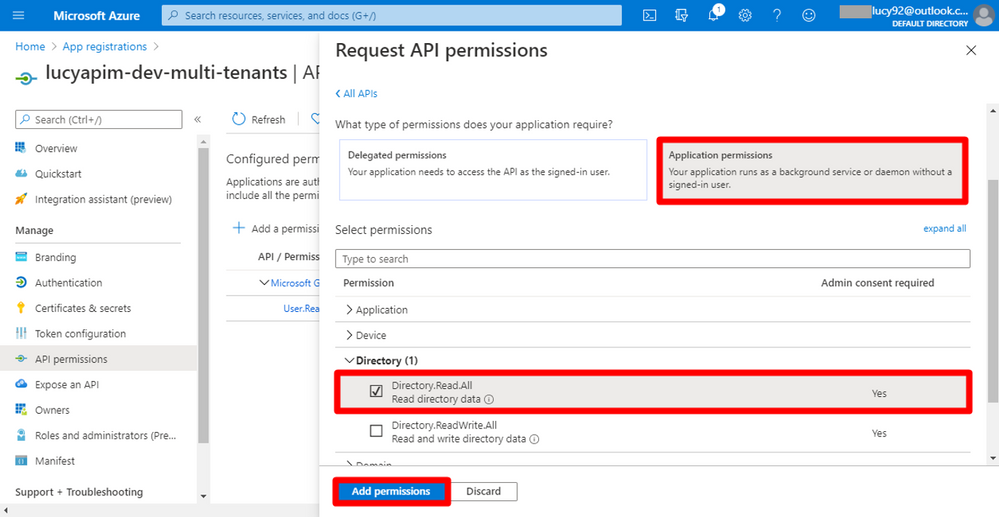
16. Click the button Grant admin consent for Default Directory to eliminate the warning Not granted for Default Directory.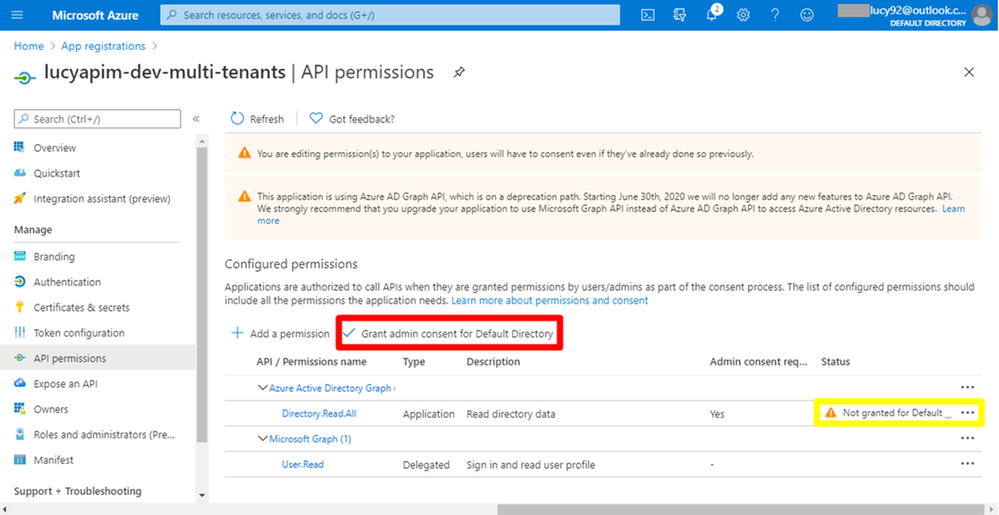
17. Go back to the API Management Portal. Select Group on the right pane. Click the button + Add Azure AD group.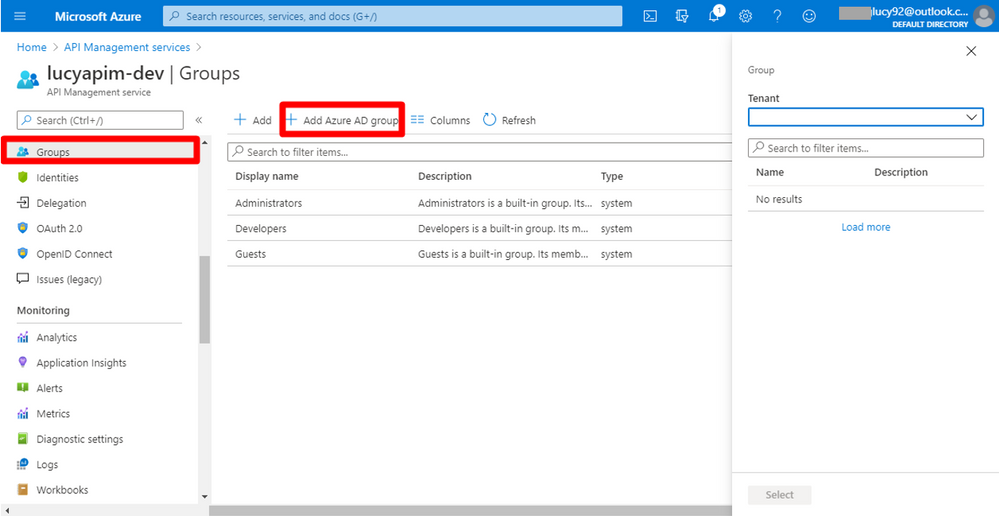
18. Select your default tenant in the drop-list of Tenant. Then choose the AD group you want to add. Until now, we have completed all the steps to authorize developer accounts by Azure AD in the default tenant. Next, we need to learn how to add the AD group from the external tenants.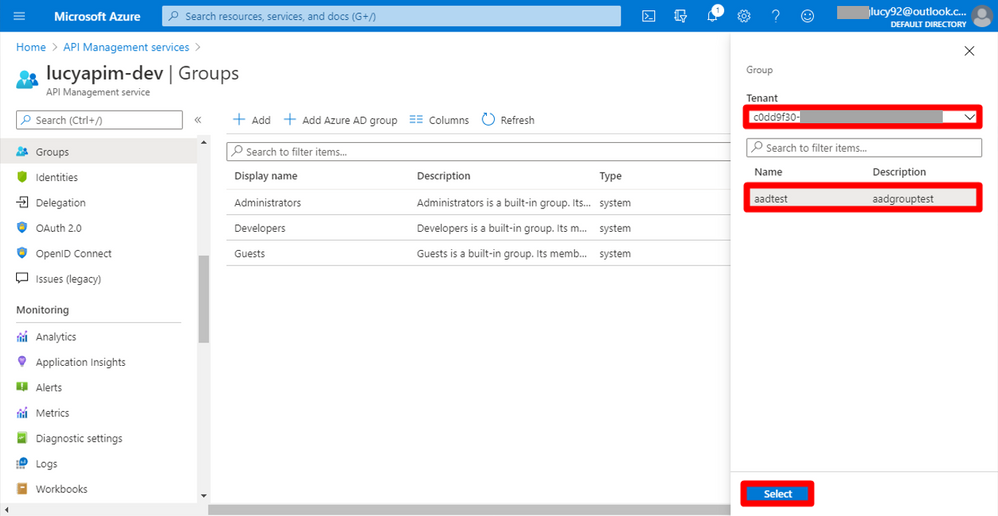
19. Go to Identities. Select the provider type Azure Active Directory we just created. Change the Signin tenant to the external tenant Id. Add the external tenant Id into Allowed tenants as well. Then click the button Update.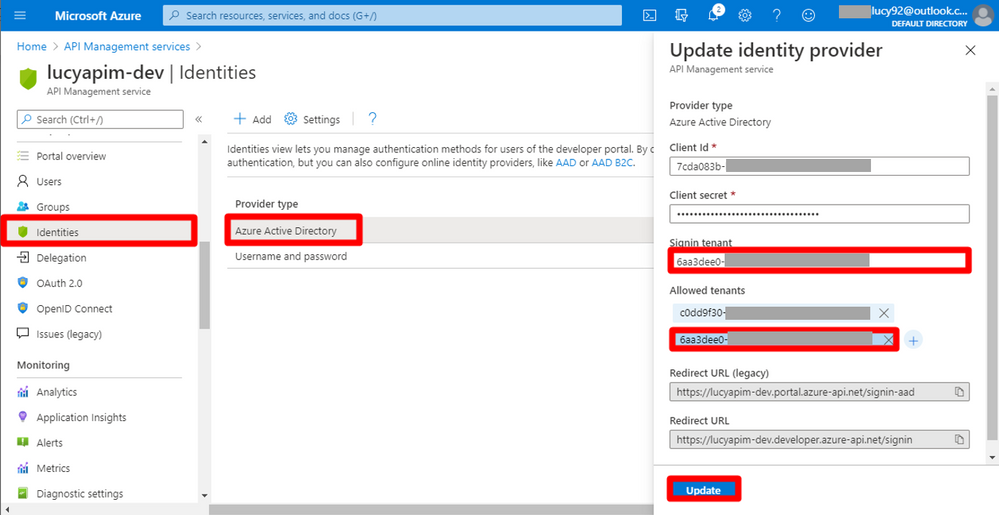
20. Before adding the external AD group into the APIM, we must get the admin consent for the external tenant. There are two ways to grant admin consent for the external directory.
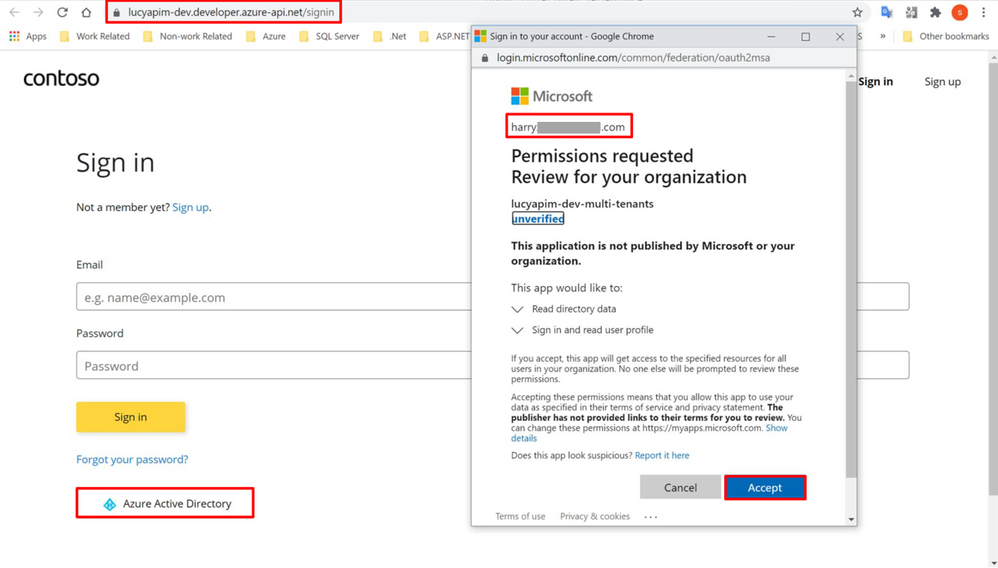
- Ask the admin of the external directory sign in the developer portal with Azure Active Directory. During signing in, the window Permissions requests will pop up. Select the button Accept, then the permission will be approved.
- Ask the admin of the external directory open the service Enterprise application on Azure Portal. Select the app with the same name of the app registration you created earlier. Click the button Grant admin consent for Default Directory.
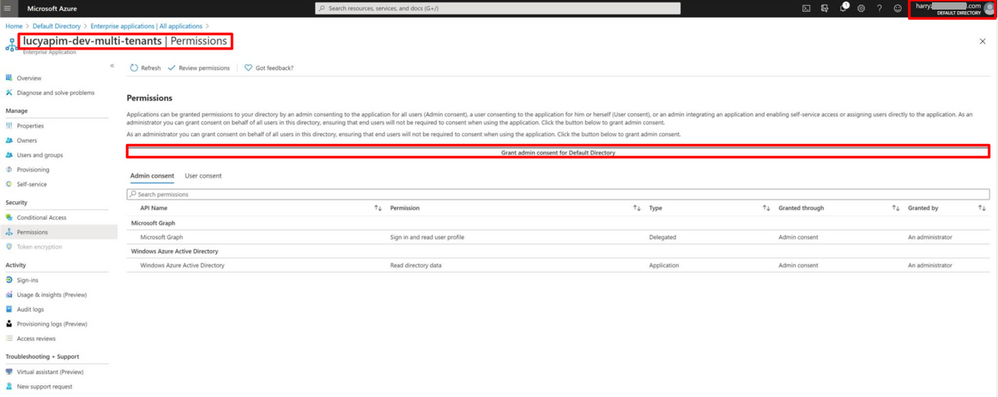
Please note when adding the external tenant as the allowed tenant in step 19, a new enterprise application with the same name of the app registration should be created into the external tenant. The two methods are equivalent and able to grant the admin consent for the external tenant by the AD admin.
21. Go back to the tenant containing the APIM service. On the APIM portal, select Group in the right pane. Select + Add Azure AD group. Now we can add the AD group from the external tenant.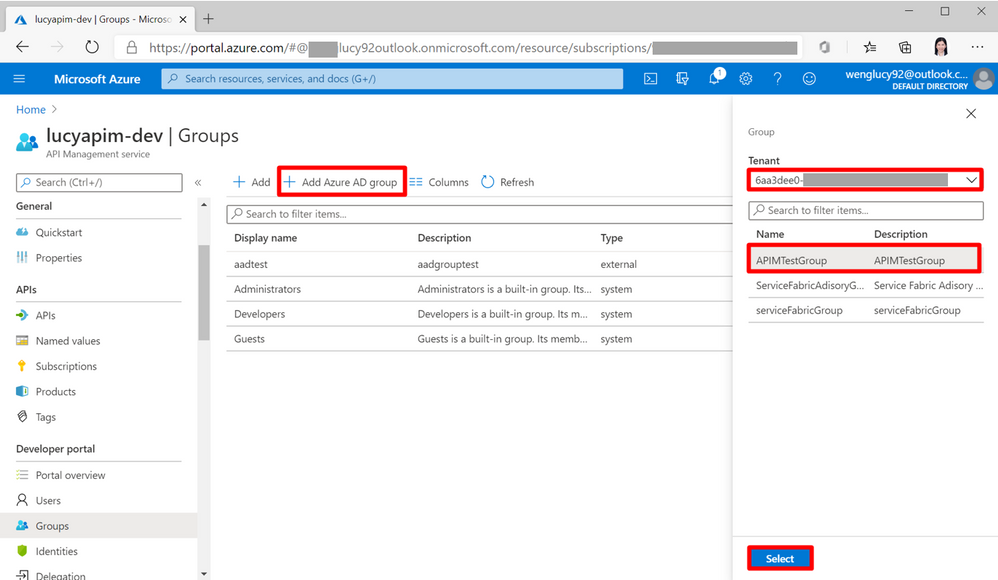
by Scott Muniz | Aug 21, 2020 | Uncategorized
This article is contributed. See the original author and article here.
I recently worked on some tenant user scenarios, as a part of POCs, with customers on Azure Synapse Analytics (preview). These are more ‘what if’ kind scenarios scoped for Synapse studio (preview). It is important to understand the kind of access to be given to users so that they can work on Synapse studio.
Background
Before we start, please note https://web.azuresynapse.net works on AAD authentication. I have five AAD users (user1 to user4) and two AAD groups ‘pocsqladmin’ and ‘pocsynapsereader; in office365 tenant. User5 is in my Org tenant.
I am owner of workspace and have created SQL Pool – ‘synapsesqlpool’ and Spark Pool –‘pocsparkpool’.
AAD group – Pocsqladmin is contributor in workspace and active directory admin of SQL Pool. It is being added as workspace, sql and spark admin from synapse studio. Also, this group has RBAC role in storage account. Additionally, I have added pocsqladmin as user in SQL Pool under security.
CREATE USER [pocsqladmin] FROM EXTERNAL PROVIDER
GO
GRANT CONTROL ON DATABASE::synapsesqlpool TO [pocsqladmin];
Scenarios
- User Senario1 –> User with contributor role is subscription
If user’s role in subscription = contributor then it gets inherited to synapse workspace as contributor. Following errors will be seen in synapse studio if no other permission is given.
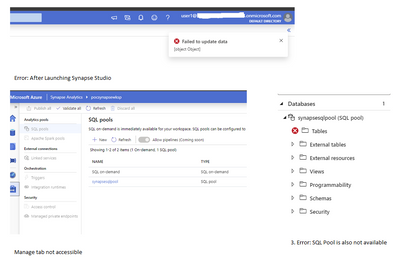
Mitigation:
- Add user as workspace admin/SQL pool admin etc.
- Or add user to pocsqladmin AAD group.
With a and b, you can create pipeline, notebook, can use mange tab etc. But this will only give select permission on objects of SQL pool. You will receive following error, if you issue ‘Create’ command
Failed to execute query.
Error: The specified schema name “user1@org.onmicrosoft.com” either does not exist or you do not have permission to use it.
Add user explicitly to the SQL Pool under security with appropriate grant permission.
CREATE USER [user1@org.onmicrosoft.com] FROM EXTERNAL PROVIDER
GO
GRANT CONTROL ON DATABASE::synapsesqlpool TO [user1@org.onmicrosoft.com];
Please refer Database Engine Permissions poster for a list of all the permissions
- User Scenario2 –> user with reader role in subscription and member of AAD group ‘pocsqladmin’
If user’s role in subscription = reader then it gets inherited to workspace as reader but as it is member of AAD group, he/she can to access entire workspace including manage tab, spark pool etc. Add user to SQL pool, similar to user1.
- User Scenario3 –> user with reader role in subscription and added as
pocsynapsereader from synapse studio.
If user’s role in subscription = reader then it gets inherited to workspace as reader. User3 is part of reader group, it gets following error while browsing synapse studio.
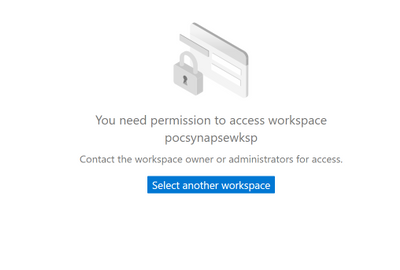
- User Scenario4 –> user with reader role in subscription and added as spark pool admin
If user’s role in subscription = reader then it gets inherited to workspace as reader
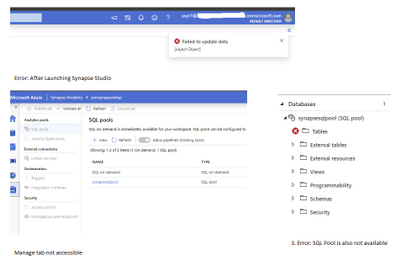
Spark pool admin – with this access user will not be able to browse SQL Pool and also get following error while running notebook or browsing storage.
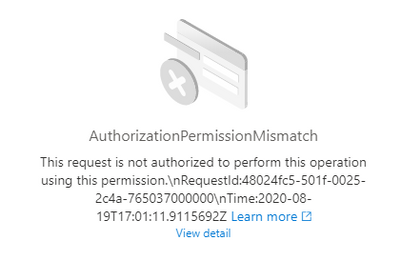
e.g. %%pyspark
data_path = spark.read.load(‘abfss://pocsynapsefs@pocsynapsesa.dfs.core.windows.net/Test/TestEmpInsertFromTxt.txt’, format=’text’)
data_path.show(100)
Error:
Py4JJavaError : An error occurred while calling o127.load. : Operation failed: “This request is not authorized to perform this operation using this permission.”, 403, HEAD, https://storageaccount.dfs.core.windows.net/filesystem/Test/TestEmpInsertFromTxt.txt?upn=false&action=getStatus&timeout=90 at org.apache.hadoop.fs.azurebfs.services.AbfsRestOperation.execute(AbfsRestOperation.java:166)
Mitigation: Make user as storage blob data contributor to run notebooks and browse ADLS
- User Scenario5 –> User from different tenant and subscription
Synapse analytics workspace is created in Office 365 tenant and user is expecting to be able to add other users from his organization tenant.
User will not able to see users(different tenant/subscription) in drop down list of manage tab in Synapse Studio.
Run following command and check if user is added in workspace subscription.
Get-AzRoleAssignment -SignInName <email_or_userprincipalname>
Also, make sure to populate email field with UPN(User Principal Name), so workspace admin can identify correct account to assign rights to SQL pools.






Recent Comments