Experiencing Alerting failure for alerts and action rules – 08/29 – Investigating
This article is contributed. See the original author and article here.
- Work Around: None
- Next Update: Before 08/29 16:00 UTC
-Subhash
This article is contributed. See the original author and article here.
-Subhash
This article is contributed. See the original author and article here.
This post was written by Sagar Chandra Reddy Lankalain in collaboration with Ji Eun Kwon. Sagar and Ji Eun currently serve as the Program Managers for VS and .NETat Microsoft.
Azure Lab Services is a managed cloud service that enables educators and IT to easily roll out cost-efficient labs with customizable virtual machines, without having to master the complexities of setting up cloud infrastructure.
Azure Lab Services helps to quickly create virtual lab environments and enables to easily run a class, set up a training lab, or host a hackathon in the cloud so that users can access lab resources from anywhere, anytime.
Azure Lab Services provides the following key capabilities:
Azure Lab Services has recently rolled out new cost control features that will proactively prevent waste of virtual machine usage hours inside the labs! The combination of these three automatic shutdown and disconnect features will now catch most of the cases where users accidentally leave their virtual machines running:
These settings can be configured at both the lab account level and the lab level. If the settings are enabled at the lab account level, they will be applied to all labs within the lab account. Any changes to the settings made at the lab level will override the lab account level configuration. For all new lab accounts, these settings will be turned on by default.
Let’s look at what each setting does in detail.
This is a setting that is only available for Windows virtual machines. When the setting is turned on, any machines in the lab, including the template virtual machine, will automatically disconnect the user when the Windows OS deems the session to be idle. Windows OS’s definition of idle uses two criteria:
Users will see a message like this inside the virtual machines before they are disconnected:
Please note that the virtual machine is still running when the user is disconnected. If the user reconnects to the virtual machine by signing in, windows or files that were open or unsaved work previous to the disconnect will still be there. In this state, because the virtual machine is running, it still counts as active and accrues cost.
To automatically shut down the idle Windows virtual machines that are disconnected, use the combination of “Disconnect users when virtual machines are idle” and “Shut down virtual machines when users disconnect” settings.
For example, if you configure the settings as follows:
The Windows virtual machines will automatically shutdown 20 minutes after the user stops using them.
This setting now supports both Windows and Linux virtual machines. When this setting is on, automatic shutdown will occur when:
This feature utilizes the Linux Diagnostic Extension and is available for only the specific distributions and versions of Linux that the Linux Diagnostic Extension supports.
You can specify how long the virtual machines should wait for the user to reconnect before automatically shutting down.
Inside a lab, a user might start a virtual machine but never connect to it. For example:
The “Shut down virtual machines when users do not connect” setting will catch these cases and automatically shut down the virtual machines.
—-
Please enable these settings to minimize waste in your labs and check out Azure Lab Services Blog for such important features and updates.
This article is contributed. See the original author and article here.
The way you work is complex and the streams of information keep increasing, constantly demanding your attention. Your projects, your team’s projects, and the information you need to do your work are stored across multiple applications, forcing you to constantly switch between them and then re-focus and regain context. That constant switching and the inevitable distractions add up quickly – and your productivity plummets.
Keeping things organized is one step to being productive. Having everything in one place will save you time and being able to quickly find what you need will make you more effective. Imagine a dresser, with unlimited drawers, and each drawer with unlimited organizers in them.
To help you achieve that, we are introducing Project Moca in Outlook on the Web. With Project Moca, you can simplify your workflow so you can focus on what matters. Add tasks, goals, notes, files from OneDrive and other cloud storage providers, links, contacts, and even emails and events, all into one dynamic space. Each space has a flexible canvas so you can customize and view your content your way.
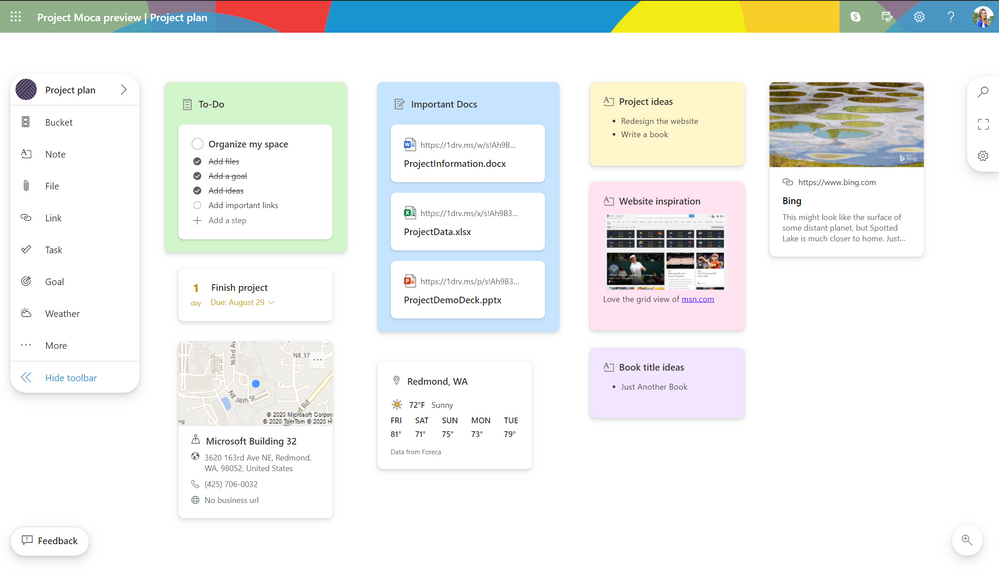
Find Project Moca in the module switcher in Outlook on the web. If you can’t see it, click on the overflow “…” menu.
Access Project Moca from the module switcher
You can start a space from scratch or you can use one of the templates provided; either way you can organize, customize, and move things around to meet your way of working.
Create a new space from scratch or from a template
Once in there, click on “Bucket” to create one of those “drawer organizers” and then start adding content to it.
Create a bucket
Keep track of specific goals or set due dates on any kind of content in your space to get reminded about the things that matter. Your goals will also show up on your Outlook calendar.
Create a goal
View your goals on your calendar
Create tasks to track your progress and they will sync automatically across Microsoft 365. See and manage them in Outlook, Microsoft To Do, or Teams.
View your tasks in Microsoft To Do
Need to keep track of several documents? No problem. Bring in all your PowerPoint decks, Word documents, and Excel spreadsheets from OneDrive.
Add files from OneDrive
Write a quick note and see it sync as a Sticky Note.
Notes in Project Moca are saved as Sticky Notes
Add emails to a space directly from your Inbox in Outlook.
.
Add an email to a space via the ellipsis menu
Add the email you added from your Inbox into your space
You can also add emails and events within Project Moca via the Activity Pane.
Add emails and events from the Activity Pane
Planning a trip? Add location and weather cards to your space.
With Project Moca, you can keep things organized, simplify your workflow, and find what you need quickly without worrying about details scattered across multiple apps – so you can stay focused on what matters.
Project Moca is available for Microsoft 365 consumer subscribers, EDU customers, and select commercial customers and is shipped off-by-default. Admins can enable it through PowerShell with the Set-OwaMailboxPolicy OwaMailboxPolicy-Default -ProjectMocaEnabled $true parameter. You can learn more about PowerShell cmdlets at: https://docs.microsoft.com/powershell/module/exchange/set-owamailboxpolicy.
We hope you try it and share your thoughts with us. Please send us feedback through the feedback button in each space to let us know how we can improve!
Give feedback via the feedback button in the bottom left corner
Thanks,
Lydia and the Project Moca team
This article is contributed. See the original author and article here.
We’ve confirmed that all systems are back to normal with no customer impact as of 8/28, 21:30 UTC. Our logs show the incident started on 8/28, 17:30 UTC and that during the 4 hours that it took to resolve the issue, customers in the West US Region could have experience delayed or lost Diagnostic Logs. Customers using App Services Logs in Public Preview could have also experienced missed or delayed logs in all US and Canada Regions.
We understand that customers rely on Azure Monitor as a critical service and apologize for any impact this incident caused.
-Eric Singleton
This article is contributed. See the original author and article here.
This article was written by Azure and AI MVP Stefano Tempesta as part of the Humans of IT Guest Blogger series. Stefano shares about the critical work in helping humans around the world regain and own their own digital identities in the modern, digital world.
Did you know?
Over 1 billion people worldwide are unable to prove their identity through any recognized means. As such, they are without the protection of law, are unable to access basic services, education, employment, participate as a citizen, or transact in the modern economy. Most of those affected are children, and many are refugees, forcibly displaced, or stateless persons. Today, Microsoft is actively involved in building a digital ID network to help provide legal identification to billions of people worldwide with no official documents, as part of the ID 2020 Alliance initiative.
Identity is vital for political, economic, and social opportunity. But systems of identification are archaic, insecure, lack adequate privacy protection, and for over a billion people, inaccessible. Not only does the lack of legal documentation strip one in seven people from having global access to critical services, it also puts those trapped in the “identity gap” at risk for larger issues including displacement and child trafficking.
To close this gap, as individuals, we must have control over our own identity, including how personal data is collected, used, and shared. For a start, you should restrict how others see your profile and network information. Most social network platforms, including LinkedIn in the screenshot below, have proper settings for that.
But the problem goes beyond access to personal information. Where the data resides, who retains your data, what use third parties do with it, with whom do they share it – these are all current challenges that centralized identity, i.e identity accounts owned by an identity provider grapples with today, yet there is no simple solution for this.
In today’s world, many of the transactions that require identification are being conducted digitally. From e-passports to digital wallets, online banking to social media accounts, these new forms of digital ID allow us to travel, conduct business, access financial and health records, stay connected, and much more.
Digital identity, as mentioned, carries significant risk, if not thoughtfully designed and carefully implemented. Large-scale data breaches affecting millions of people have been the consequence of the use of archaic and insecure tools, along with the lack of appropriate privacy protection.
Proper technical design can mitigate some of these risks, and cryptographically secure, decentralized systems could provide greater privacy protection for users, while also allowing for portability and verifiability. However, widespread agreement on principles, design patterns, and interoperability standards is needed for decentralized digital identities to be trusted and recognized.
One thing is clear – Doing digital ID right means protecting civil liberties and putting control over personal data back where it belongs: in the hands of the individual.
A new form of identity is needed, one that weaves together technologies and standards to deliver key identity attributes, such as self-ownership and censorship resistance, that are difficult to achieve with existing systems. To deliver on these promises, we need to understand how self-sovereign identity compares to current identity systems. Email addresses and social network IDs were created as human-friendly aliases for collaboration but are now overloaded to serve as the control points for data access across many scenarios beyond collaboration. This poses a potential problem, given that access to these IDs can be revoked at any time by the email provider, social network provider, or other external parties, like governments.
Decentralized Identifiers (DIDs) are different. DIDs are user-generated, self-owned, globally unique identifiers rooted in decentralized systems. They possess unique characteristics, like greater assurance of immutability, censorship resistance, and tamper evasiveness. These are critical attributes for any ID system that is intended to provide self-ownership and user control.
Over the last few months, I’ve invested in developing a set of ideas and concepts for using blockchain and other distributed technologies to create new types of digital identities – identities designed from the ground up to enhance personal privacy, security and control. With specific application to the Education space, students would now be able to own their digital identity and studies across multiple educational institutes, creating a single, immutable, and verifiable curriculum. Certificates of attendance, completion of exams, and diplomas can be issued and be digitally signed. No more fake certifications, no more degree mills, no more “photoshopped” papers. For example, students applying for further education, a job, or immigration to another country often have to prove their level of study or fluency in languages. Recruiters, employers, governments and universities can now easily verify the student’s credentials in just minutes, without unnecessary intermediaries and can now avoid having to rely on central authorities that may take weeks or even months to respond due to backlogs.
Locally, this is the work that I’m conducting at the Department of Industry in Australia as part of the definition of the National Blockchain Roadmap. This definition of a self-owned identity for students essentially enables everyone the opportunity to access education as a basic right anywhere you go in the world because their identities are now easily and securely verifiable:
We’ve made progress, but we can do so much more than this. This is why I’m volunteering my time at the Decentralized Identity Foundation (DIF) to help define and build a digital ID network that can help provide legal identification to billions of people worldwide with no official documents.
The DIF initiative is part of a larger set of activities that sees Microsoft actively involved, including the ID 2020 Alliance, and the W3C Credentials Community Group. The purpose of these working groups is to establish a unified, interoperable ecosystem that developers and businesses can rely on to build a new wave of products, applications, and services that put users in control. As an open platform, you can also get involved as an active member and contribute by helping define the technology for billions of people to have access to reliable ID, empowering them to finally realize their dream for better education, services, business and overall quality of life.
Here are some key resources for you to get involved:
Closing the identity gap is an enormous challenge. It will take tremendous work of many committed tech professionals, volunteers and organizations coming together across different geographies, sectors and technologies. That said, it’s exciting to imagine a world where safe and secure digital identities are possible, providing everyone with an essential building block to every right and opportunity they deserve.
YOU can help make this future possible – volunteer your skills and get involved today!
#HumansofIT
#TechforGood
Recent Comments