by Scott Muniz | Aug 28, 2020 | Uncategorized
This article is contributed. See the original author and article here.
Join the Microsoft Advertising team to learn about exciting new features coming soon to the developer and API roadmap. We’ll explore features that are currently available as well as several that we’ll be piloting and releasing soon. Please click here to register for the webcast on 17th September 2020 at 11:00 a.m. U.S. Pacific Time.
This webcast will provide you with a clear understanding of upcoming features and the value they can bring to your Microsoft Advertising campaigns. Along with a view of the API features coming soon and those recently updated, we’ll also provide an estimated timeline as to when features will become available, so you’ll have the building blocks needed to develop the solution that works best for you.
In this webcast we will cover:
- Microsoft Audience Network (MSAN)
- Google Import: API & UI
- Digital Merchant Center (DMC)
- Smart Shopping
- Feed Driven Experiences:
- Automotive Inventory Ads
- Dynamic Data Sitelink Extension
- Automated Bidding
- Updates to Image Extensions
- Update on Deprecation for Average Position
- Azure Active Directory (AAD) & Multi-Factor Authentication (MFA)
If you can’t make the live webcast, register to watch it on demand when it’s most convenient for you. The on-demand version is usually available 24 hours after the live event.
Looking forward to meeting you soon,
Bing Ads API team
Microsoft Advertising

by Scott Muniz | Aug 28, 2020 | Uncategorized
This article is contributed. See the original author and article here.
We are pleased to announce the enterprise-ready release of the security baseline for Microsoft Edge version 85!
We have reviewed the settings in Microsoft Edge version 85 and updated our guidance with the addition of one setting that we will explain below. A new Microsoft Edge security baseline package was just released to the Microsoft Download Center. You can download the version 85 package from the Security Compliance Toolkit.
SHA-1
A new (but, ironically, deprecated) setting has been added to version 85: Allow certificates signed using SHA-1 when issued by local trust anchors. While it might seem odd that we are adding a deprecated setting to the baseline, this one is important. Microsoft Edge forbids certificates signed using SHA-1 by default, and the security baseline is enforcing this to ensure Enterprises recognize that allowing SHA-1 chains is not a secure configuration. Should you need to use a SHA-1 chain for compatibility with existing applications that depend on it, moving away from that configuration as soon as possible is critical to the security of your organization. In version 92 of Microsoft Edge (mid-2021) this setting will be removed, and there will be no supported mechanism to allow SHA-1, even for certificates issued by your non-public Certificate Authorities, after that.
App protocol prompts
While they may not seem directly related to security, app protocols are something you should be mindful of, as they provide a mechanism for escaping the browser sandbox. New policies to help manage these might therefore be useful in your organization as you strive to balance security and productivity.
To make managing app protocols easier, we first added a flag in version 82, exposed a user-facing option in version 84, and have added a policy for the IT Pro to manage them in version 85: Define a list of protocols that can launch an external application from listed origins without prompting the user. For a detail discussion on the topic, we recommend reading Eric Lawrence’s blog here.
Commonly seen with applications like Microsoft 365 Apps, Microsoft Teams, Skype, the user is by default prompted to allow the external application to launch as depicted in the below examples.

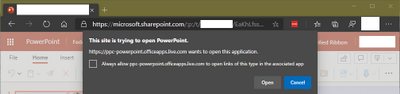
Leveraging this setting will suppress that prompt and reduce noise to the end user by approving the content at the enterprise level. Reducing end user prompts both improves user productivity and helps them make better decisions when an unexpected request appears by reducing prompt fatigue!
While you are at Eric’s blog, be sure to check out his other posts.
Baseline Package Refresh
Since a new setting has been added we have updated the security baseline package which will include the usual artifacts, as well as a list of new settings from version 84 to 85 and version 80 to 85. This way, those that have been keeping up with the blog have a smaller set of settings to review, and those only looking at the actual released package can see all the changes.
As a friendly reminder, all available settings for Microsoft Edge are documented here, and all available settings for Microsoft Edge Update are documented here.
Please continue to give us feedback through the Security Baselines Discussion site and via this post!
by Scott Muniz | Aug 28, 2020 | Uncategorized
This article is contributed. See the original author and article here.
News this week includes:
Internet of Things announced a new series called Ask the IoT Expert. Each month, from September onwards, engineers and specialists will briefly introduce an IoT topic in the Learn IoT discussion section on TC and open it up to users to ask any questions or thoughts relating to that topic.
Transcribe in Word was announced. Transcribe individually separates different speakers so it’s clear which part was said by a teacher versus a student. After the conversation, parts of the recording can be played back by clicking on timestamped audio and the transcript can be edited.
@eguif is our Member of the Week, and a great contributor in the Microsoft Edge Insider community.
View the Weekly Roundup for August 24-28 in Sway and attached PDF document.
by Scott Muniz | Aug 28, 2020 | Uncategorized
This article is contributed. See the original author and article here.
This case started as an issue on SQL on-demand while reading a parquet file. The error was conversion overflows.
Error: Conversion overflows.
So my objective on this post is to describe a possible workaround to read this file in the Spark as also to give some ideas on how to troubleshoot this with the notebook.
Basically I loaded the file on Spark using Scala and it completed successfully:
val sqlContext = new org.apache.spark.sql.SQLContext(sc)
// Create a DataFrame
val df = sqlContext.read.parquet("abfss://<storage>.dfs.core.windows.net/folder/file.parquet")
Display (df.limit(10))
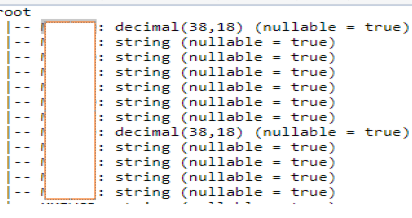
No big deal here. After that, I wanted to check the metadata:
// Print the schema in a tree format
df.printSchema()
You should have a result like the following:
More information you can find here:
https://spark.apache.org/docs/preview/sql-programming-guide.html
Once I found the metadata I used the column name information to run the query against SQL on-demand. With this information, I found the issue was related to a decimal column.
Here some SQL On-demand query tips for conversion issues:
1) You can use schema inferring while querying and by using it you can convert the column datatype. For example, I will convert the decimal column named as column_dec_converted to varchar.
SELECT *
FROM OPENROWSET(
BULK 'https://<storage>.dfs.core.windows.net/folder/file.parquet',
FORMAT='PARQUET' ) WITH ( column_dec_converted varchar(100) ) as rows
2) You can actually apply the convert on the Select Clause as you would do on standard SQL Server:
SELECT cast (column_dec_converted as varchar(100))
FROM OPENROWSET(
BULK https://<storage>.dfs.core.windows.net/folder/file.parquet',
FORMAT='PARQUET' ) as Result
SQL On Demand does not support DML but it fully Supports Select syntax.
That is it!
Liliam C Leme
UK Engineer
by Scott Muniz | Aug 28, 2020 | Uncategorized
This article is contributed. See the original author and article here.
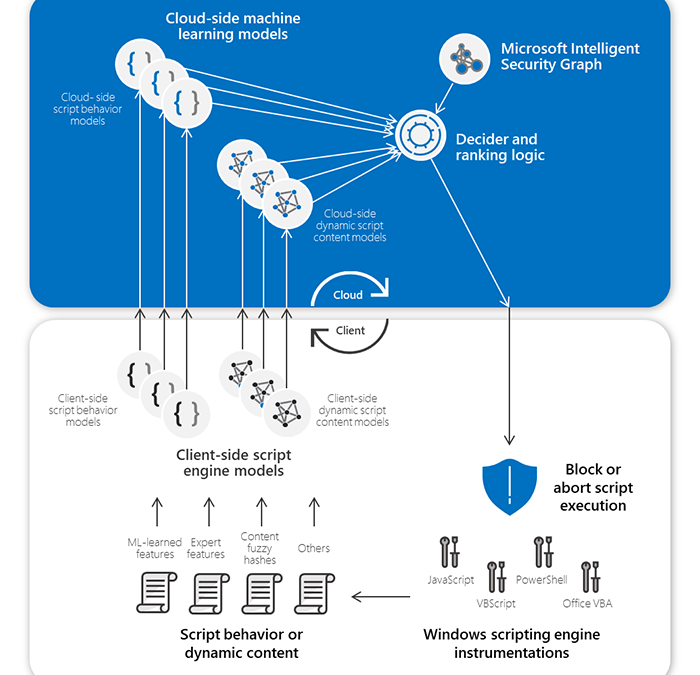
Behavioral blocking and containment capabilities in Microsoft Defender Advanced Threat Protection (ATP) use protection engines that specialize in detecting and stopping threats by analyzing behavior. One of these engines leverages insights from Antimalware Scan Interface (AMSI), which has visibility into script content and behavior, and pairs of machine learning models on the client and in the cloud working together to detect and stop malicious scripts post-execution.
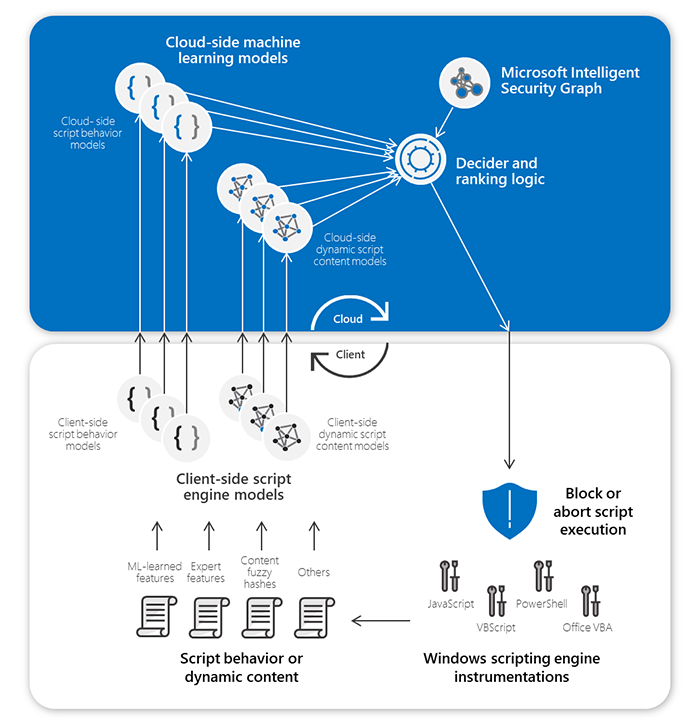
These pairs of AMSI-powered machine learning classifiers, one pair for each scripting engine, allow Microsoft Defender ATP to detect malicious behavior and stop post-exploitation techniques and other script-based attacks, such as BloodHound and Kerberoasting attacks.
To learn more, read our latest blog post: Stopping Active Directory attacks and other post-exploitation behavior with AMSI and machine learning.





Recent Comments