by Scott Muniz | Aug 28, 2020 | Uncategorized
This article is contributed. See the original author and article here.
Excel MVPs are Excel experts who passionately share their knowledge with the community. They’re deeply knowledgeable of Excel and use that knowledge to solve real world problems. They’re driven by their passion, community spirit and quest for knowledge, and always willing to help each other.
We want to start sharing with you some of the knowledge directly from our Excel MVPs:
Have You Got What It Text? Introducing ARRAYTOTEXT and VALUETOTEXT
Excel MVP Liam Bastick looks at what he has been able to glean about these welcome new additions to the Excel myriad of functions, features, and formulae.
11 Solid Reasons to Use Excel Tables
Excel MVP Ajay Anand explains 11 advantages of using Excel Tables. There are few bonus tips like the least known shortcut for creating Excel Table, Tables as source data for Dynamic Drop-Down List, shortcuts for Excel Tables, etc.
Bereichsvariable in der Funktion LET verwenden (Use Range Variable in the LET function)
Excel MVP Mourad Louha describes with an example how to use the new function LET and shows an interesting feature of this function.
Find this useful or want to know more about a specific Excel topic? Leave a comment below.

by Scott Muniz | Aug 28, 2020 | Azure, Microsoft, Technology, Uncategorized
This article is contributed. See the original author and article here.
Another Friday is upon us, so time to share some of the headlines that have happened this week in terms of Azure news. We have some new preview features in Azure as well as some going Generally Available (GA).
Revised end of service date for Windows 10, version 1803: May 11, 2021
Microsoft are delaying the scheduled end of service date for the Enterprise, Education and IoT Enterprise editions of Windows 10, version 1803. This means that if you are still running that version within your environment you will continued to receive security updates until May 11, 2021 instead of the previous November 2020 date.
 Azure Migrate
Azure Migrate
Support to assess physical, AWS, GCP servers now generally available within Azure Migrate
The ability to assess your physical, AWS, GCP servers with Azure Migrate has been around for a while now and it’s now generally available to use. So, it’s great for assessing those servers on another cloud provider you want to move to Azure or even those virtual machines that are hosted by a managed service provider and you can’t access the hypervisor layer on. I actually covered this off in a blog post and video recently, check it out if you want to see it in action.
 Cognitive Services
Cognitive Services
Public Preview: Cognitive Services Form Recognizer v2.1
Form Recognizer is a cognitive service that uses machine learning technology to identify and extract things like text from documents. In this latest public preview edition they team have introduced support for more languages, so as well as supporting English it now supports Chinese (Simplified), Dutch, French, German, Italian, Portuguese and Spanish. It also has a new pre-built model that will help extract information from a business card.
 Azure Storage Icon
Azure Storage Icon
AzCopy v10.6 released
A new version of AzCopy has been released, with some exciting features. If you aren’t familiar with AzCopy it is a great command line tool that helps you move data in and out of Azure Storage. One of the new features is the ability to query Blob Versioning, so you can download a specific version of a file or delete it.
MS Learn Module of the Week
 MS Learn Banner
MS Learn Banner
Improve incident response with alerting on Azure – responding to incidents and things that happen to your infrastructure in a timely manner is part of what makes and IT department successful. In this MS Learn module you’ll learn how alerting in Azure can help you monitor and response to things happening in your environment.
Let us know in the comments below if there are any news items you would like to see covered in next week show. Az Update streams live every Friday so be sure to catch the next episode and join us in the live chat.
by Scott Muniz | Aug 27, 2020 | Uncategorized
This article is contributed. See the original author and article here.
We recently released an update to Microsoft JDBC Driver for SQL Server, version 8.4.1. The update addresses a few issues that are important to our customers.
Fixed issues
- Fixed issue with SQLServerConnectionPoolProxy not being compatible with delayLoadingLobs #1403
- Fixed a potential NullPointerException issue with delayLoadingLobs #1403
- Fixed issue with decrypting column encryption keys using Windows Certificate Store
Getting the latest release
The latest bits are available to download from Microsoft, from the GitHub repository, and via Maven Central.
Add the JDBC 8.4 RTW driver to your Maven project by adding the following code to your POM file to include it as a dependency in your project (choose .jre8, .jre11, or .jre13 for your required Java version).
<dependency>
<groupId>com.microsoft.sqlserver</groupId>
<artifactId>mssql-jdbc</artifactId>
<version>8.4.1.jre11</version>
</dependency>
Help us improve the JDBC Driver by taking our survey, filing issues on GitHub or contributing to the project.
Please also check out our
tutorials to get started with developing apps in your programming language of choice and SQL Server.
David Engel
by Scott Muniz | Aug 27, 2020 | Uncategorized
This article is contributed. See the original author and article here.
This article is written by Jon Shectman and Brian Delaney, Microsoft.
Have you read about the elevation of privilege vulnerability that exists when an attacker establishes a vulnerable Netlogon secure channel connection to a domain controller? An attacker who successfully exploited the vulnerability could run a specially crafted application on a device on the network. If you haven’t, you can read about the vulnerability here a and learn how to manage the changes here. Those articles give an excellent overview of the issue, so I won’t repeat it in detail here. In short, we are addressing this vulnerability in a two-part rollout by modifying how Netlogon handles the usage of Netlogon secure channels.
Phase one, deployment, began on Aug 11. In this phase, secure Remote ProtoCol (RPC) is enforced for machine, trust and domain controller accounts. This phase also includes a new group policy object (GPO) and a registry key to manage configuration, and five new Event IDs.
These Event IDs are important for auditing and understanding of the issue. They are as follows:
Machine Events
5827 – Connection denied
5829 – Non-compliant (allowed during Deployment phase)
5830 – Allowed by policy
Trust Events
5828 – Connection denied
5831 – Allowed by policy
Phase two, enforcement, is slated to begin Feb 9, 2021. In phase two, non-compliant machine connections will be denied by default and an Event ID 5827 will be logged. It’s entirely possible to set the new GPO “Domain controller: Allow vulnerable Netlogon secure channel connections” and to simply allow the vulnerable connections. However, that is not recommended. Rather, you should use the new tab in the Insecure Protocols Workbook to detect and understand the five new Event IDs and take appropriate action to address the vulnerable Netlogon sessions prior to the enforcement phase. If you’re new to the Insecure Protocols Workbook, we recommend checking out the getting started guide and then come back here.
To populate the Workbook, take two steps:
1. On your domain controllers, apply the relevant update from CVE-2020-1472.
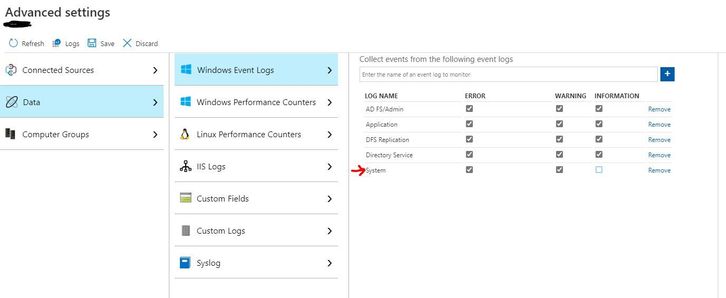
2. In Azure Sentinel, go to Settings, Workspace Settings, Advanced Settings, Data, Windows Event Logs, and add (or make sure you already have added) Errors and Warnings from the System Log.
Once you have data flowing, it’s time to start using the Insecure Protocols Workbook. The first addition you’ll notice is a new tab, Vulnerable Secure Channel.
The most efficient way to describe how to use this tab is to simply show it – as in the GIF below.
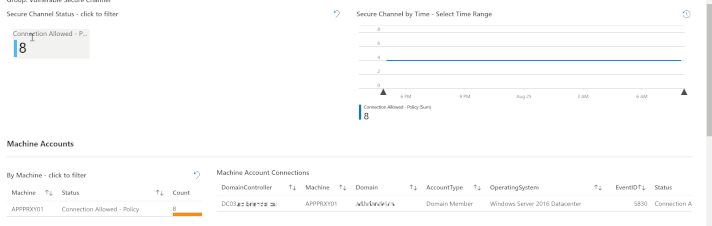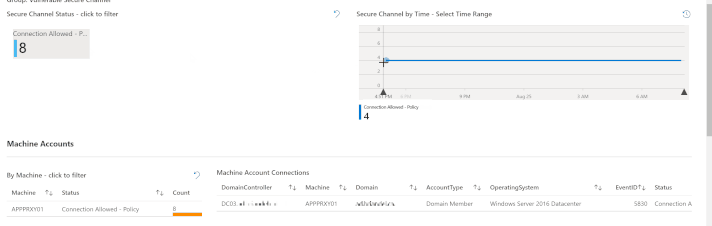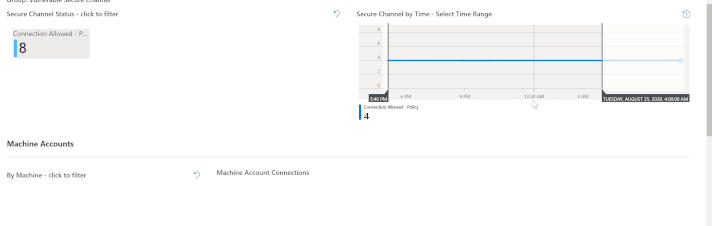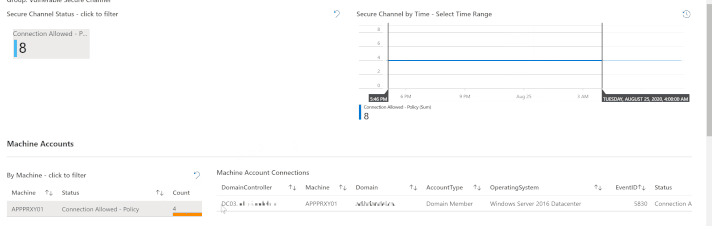
At the top of the tab is a counter (tile) for each of the five new Event IDs. In our lab, for example, we have eight instances of Event ID 5830. That’s the tile I clicked on to filter to that event ID. Next, I “painted” a timebrush slice to filter the queries below to a particular time; then I simply clicked on a Machine Account to show the Machine Account Connections. The result is a highly actionable data set, showing us exactly where we need to research vulnerable secure channel connections.
Once you know where to look, you’ll need to upgrade all Netlogon clients. However, there’s an additional point to consider. Though we expect it to be a rare finding, vulnerable secure channel connections can come from not only machines, but also from trusts (most likely Realm trusts). This configuration may result in significantly increased exposure (Event ID 5828) and may require more planning to remediate.
In this article, we briefly discussed the exposure in vulnerable secure channel connections, how they are logged during the first phase of CVE-2020-1472, and how to audit them with the Insecure Protocols Workbook.
A brief sidenote: If you ever feel your perspectives don’t matter or that your opinions aren’t good enough, we urge you to think again. This workbook enhancement came directly from a conversation on Twitter where multiple folks made the case for it. If you have concepts to add, functionality you’d like to see added, or ideas for improvement, please reach out on Twitter (@shectonsecurity), find us on LinkedIn, or use the comments section. We are all ears.
Thanks for reading and, as always, happy auditing. :)
by Scott Muniz | Aug 27, 2020 | Uncategorized
This article is contributed. See the original author and article here.
The security we have in place for managing MEM happens at several levels. A mantra here at Microsoft is that every security decision should be made under the assumption that all other security measures have failed to keep the “bad people” out. That means there are a lot of levels of security and thought. Being users of MEMCM and MEM Intune just like the rest of the customers out there we won’t try to cover all the product specific security implementations here. Those we will leave to the product documentation itself. Instead we will look at this from the administration process viewpoint.
Read-Only Access
Through normal daily activities we need to see various things in our services. Elevating or going through the steps necessary below to have read-only access granted becomes too complicated for these common access reasons. For that we maintain several different groups which provide access to various resources. Each of those is managed by an internal system where people can request to join a group and that group membership is either approved through a process or auto-approved, depending on what it is focused on. That membership, once granted, has a renewal timeline and will remove membership when someone leaves the group/company.
Multiple Accounts
A basis of what we do is to have two separate accounts. The idea is to have one account for normal operations (email, TEAMS meetings, etc). The other account is used ONLY for administrative activities. We refer to this as our “Alternative Account” or, “ALT account” for short. The ALT account is backed by a smart card and certificate login requirement making the compromise of the account a little more difficult. Both accounts require multi-factor authentication.
Secure Workstations
While much of our read only access can be done from our normal desktops and laptops, anything that requires an admin level of access is locked down to only allow access from Secure Access Workstations (SAW). These are special laptops which work on a basis of whitelisting what they are allowed to access and what apps they can run. We do not have admin rights on these machines like we do on our normal machines, we can’t go off to malicious websites, and we can’t get email on them. Their exposure to risk is more limited. The SAW run a separate VM which some people use for those “normal” activities, while others will remote back to other machines when that “normal” activity is needed.
Azure Portal
Our Microsoft Endpoint Manager Configuration Manager (SMS to you old school folks, SCCM to you “not as old, but not your first rodeo” folks) is Azure hosted, so protecting that Azure access is the first layer we need to keep secure. We do this using normal methods which allow our normal accounts a level of read access, but no standing administrative rights. Admin access requires Azure Privileged Identity Management (PIM). It will elevate our account, on a temporary basis, to have the needed admin permissions in Azure. This is audited, requires a second person approval, and is time limited to reduce the attack concerns.
Server Access
If we need to get into a server for looking at logs or other simple things we have some read-only share access setup for our team. Beyond that we have a system that is similar in concept to PIM that requires that we request the level of access we need and then grants that access for a limited time. We refer to it as “Just in Time” access, or JIT for short. Things like which server, is it OS level or SQL level or SCCM level, etc. are all separated to require different escalations, and it is all audited, of course. This allows us to request the minimal access necessary for the job at hand.
Intune Access
Admin access to Intune is, essentially, through the normal Azure portal like above. There is a separate PIM role for Intune administrative . This is also designed around the “nuclear launch” concept where a second person is required to agree and authorize the rights elevation. For those that need a lower level of rights, but still have the ability to read or interact with the environment in a limited capacity we make use of the RBAC roles within Intune and some self-cleaning security groups to grant that access. We also have a few different Intune environments (we are running beta versions of things) so we have some separation around those things as well.
Configuration Manager Access
Similar to server access we have JIT groups for accessing MEMCM itself. They tie back into the RBAC roles of the product so different people have different groups for different activities, but anything that can make any kind of change is controlled in this fashion. We have also enabled multi-factor authentication (MFA) in the product to help us ensure that people are coming in as securely as we can.
Summary
Anytime we have a new hire we always must go through an orientation of what to use when and how. But, once you do things a few times it gets to be second nature. A few things have some time delays that can be frustrating at times, but overall it seems to work well and we take the security of our operations very seriously. Does it add complexity and occasional frustration… yes. Is it worth it to keep our environment safe… totally.
Hopefully this gives you an idea of how we securely control access to our MEM environments. We have also done work within the features of the products to increase our security stance, such as removing the Network Access Account and using token authentication, getting rid of traditional service accounts where possible, and auditing activity. All that we will save for other blog posts.





Recent Comments