by Contributed | Sep 25, 2020 | Uncategorized
This article is contributed. See the original author and article here.
The Sidecar pattern enables the extension and enhancement – of an existing process or an application container -without affecting/modifying the original process or container – thus ensuring the single-responsibility of the existing process / container. The problem context, solution, considerations and use cases for this pattern are comprehensively documented here.
Exploring the usage and reviewing the implementation of this pattern, in a real-world project, is an effective way to gain a practical perspective as you start putting the pattern into practice.
I have chosen two open source projects that implement the sidecar pattern as part of their core architecture. The first one is – Dapr – Distributed Application Runtime and the other project we will look into is the Open Service Mesh .
Dapr
Dapr is an event driven, portable runtime for building microservices on cloud and edge.
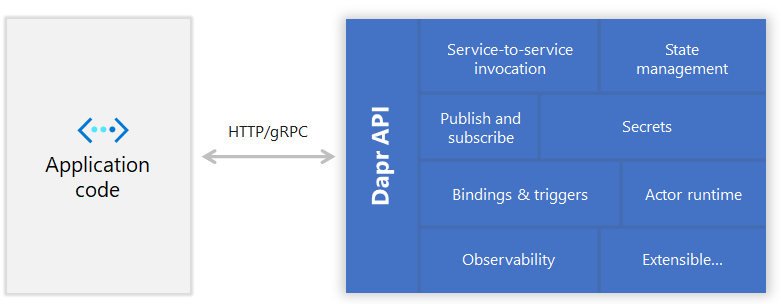
Dapr facilitates the development of microservices by providing independent building blocks like – State Management, Pub-Sub, Observability, Secrets and more – which are encapsulated as the Dapr API – in a platform-agnostic and language-agnostic manner. The independent nature of the building blocks lets you cherry-pick the set of features you want for your application and the platform-agnostic aspect gives you a wide spectrum of platforms to operate in ranging – from lean and resource-starved devices on the edge – to – power-packed , full fledged Azure Kubernetes Service clusters in the cloud.
Sidecar implementation in Dapr architecture
The key advantage of using Dapr is that the application utilizing it need not include any Dapr runtime code. This advantage is achieved by utilizing the – sidecar pattern.
The core Dapr API itself is exposed as a sidecar – either a sidecar process or a sidecar container.
If it is a sidecar process – the service code calls the Dapr API via HTTP/gRPC.
In the world of containers orchestrated by Kubernetes, the Dapr API is a side car container itself – which is utilized by the application container within the same pod.
Diagrams from the the Dapr project’s documentation as follows –
 Image 1 – Self hosted
Image 1 – Self hosted
 Image 2 – Kubernetes hosted
Image 2 – Kubernetes hosted
So, the use case in – Dapr’s case – is where a primary application uses a heterogeneous set of languages and frameworks and the component (Dapr API) located in a sidecar service /container can be consumed by applications written in different languages using different frameworks.
Open Service Mesh (OSM)
OSM is a lightweight and extensible cloud native service mesh that runs on Kubernetes. This was a project initiated by Microsoft that has been now donated to the Cloud Native Computing Foundation (CNCF) where it is a Sandbox project – at the time of this writing.
Sidecar implementation in OSM architecture
OSM onboards applications to the mesh by enabling the automatic sidecar injection of the Envoy proxy.
A look at the diagram below (source: OSM design doc) – shows the Envoy proxy already existing as sidecar container within the Kubernetes (k8s) pod.
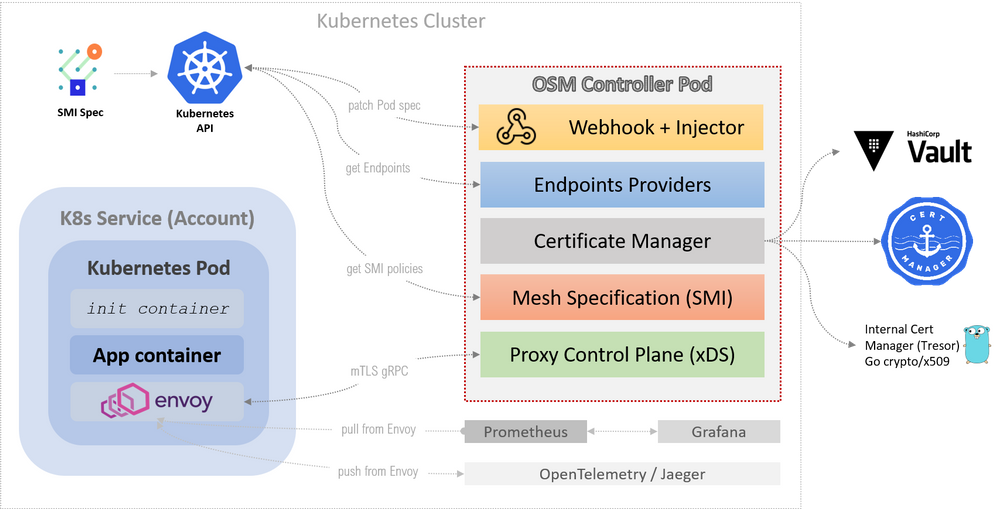 Image 3 – OSM Components
Image 3 – OSM Components
To elaborate on the automatic sidecar injection part – OSM utilizes a feature of Kubernetes called MutatingAdmissionWebhook admission controller to intercept the k8s API server request after the pod creation is initiated but before the actual persistence/creation of the pod – to augment the request to include a Envoy proxy sidecar. Now the created pod has the Envoy proxy sidecar automatically.
This means the powerful features of Envoy like – advanced load balancing, observability, rate limiting et.al. – are readily available to be utilized by each instance of the application and allowing the services in the mesh to communicate with each other.
The separation of concerns between application’s core functionality and Envoy’s functionality + the ability of Envoy features to still be in proximity of the application is achieved via the sidecar pattern in the case of Open Service Mesh.
I hope this has given you a bit more insight into the Sidecar pattern and has also piqued your interest in both the Dapr and Open Service Mesh projects!
References:
1. Sidecar pattern – https://docs.microsoft.com/en-us/azure/architecture/patterns/sidecar
2. Dapr – https://dapr.io/
3. Sidecar implementation in Dapr – https://github.com/dapr/docs/tree/master/overview#sidecar-architecture
4. Open Service Mesh(OSM) – https://openservicemesh.io/
5. OSM component and interactions – https://github.com/openservicemesh/osm/blob/main/DESIGN.md#osm-components–interactions
6. Kubernetes Admission Controllers – https://kubernetes.io/docs/reference/access-authn-authz/admission-controllers/
7. OSM MutatingWebhookConfiguration – https://github.com/openservicemesh/osm/blob/release-v0.3/charts/osm/templates/mutatingwebhook.yaml
Note – Images 1,2 and 3 in this article are from respective project documentations the links to which are referenced above.
by Contributed | Sep 25, 2020 | Uncategorized
This article is contributed. See the original author and article here.
We hope you loved our Microsoft Endpoint Manager sessions at Microsoft Ignite 2020, the digital edition, and have had time to check out the dozens of videos we put on the Video Hub on TechCommunity. We couldn’t possibly squeeze everything into 48 hours, especially when it came to connecting you, my fellow Microsoft Endpoint Manager enthusiasts, with my colleagues in engineering and on the product team. So, whether you’re new to Microsoft Endpoint Manager or a long-time fan looking to know more, I’m happy to announce that we are keeping the connection going through October and beyond—and already looking ahead to Microsoft Ignite in March 2021!
Free Microsoft Endpoint Manager post-day: September 29th
While there are many sessions from Microsoft Ignite 2020 now available on demand, we are kicking off a special post-conference experience and offering a 24-hour, around-the-world training marathon: Manage, Configure, and Secure Devices with Microsoft Endpoint Manager. Starting at 10:00 a.m. Brisbane time (AEST) on September 29, 2020, we’ll kick off our post-day with four hours of Windows content, specifically:
- Hour 1 – Get Your Windows Devices to Microsoft Endpoint Manager
- Hour 2 – Configure your Windows Devices
- Hour 3 – Secure your Windows Devices
- Hour 4 – Improve the End User Experience on Your Windows Devices
We’ll then proceed to a four-hour block of mobile device management training:
- Hour 1 – Get Your Mobile Devices to Microsoft Endpoint Manager
- Hour 2 – Secure Your Mobile Devices with Microsoft Endpoint Manager
- Hour 3 – Manage You MacOS with Microsoft Endpoint Manager
- Hour 4 – Manage Shared Devices for Firstline Workers
We’ll then repeat both sets of sessions twice, wrapping up at 6:00 p.m. Seattle time (PST). Each four-hour block will contain the same content so attend whichever session times work best for you. You can do them in any order and jump between the repeats. Depending where you are in the world, some sessions may start Monday, September 28th or continue to Wednesday, September 30th.
How do I sign up for the post-day?
Simply register at https://aka.ms/MEMPostDay and you’ll have access to calendar invitations for the times that work best for you. And yes, we’ll record it all, but attending live means you get to ask questions in real time in our exclusive Q&A sessions on Teams Live Events!
|
Section
|
Start time – UTC
|
End time – UTC
|
|
Windows Q&A 1
|
Tuesday Sept 29
00:00
|
Tuesday Sept 29
04:00
|
|
Mobility Q&A 1
|
Tuesday Sept 29
04:30
|
Tuesday Sept 29
08:30
|
|
Windows Q&A 2
|
Tuesday Sept 29
07:30
|
Tuesday Sept 29
11:30
|
|
Mobility Q&A 2
|
Tuesday Sept 29
12:00
|
Tuesday Sept 29
16:00
|
|
Windows Q&A 3
|
Tuesday Sept 29
16:30
|
Tuesday Sept 29
20:30
|
|
Mobility Q&A 3
|
Tuesday Sept 29
21:00
|
Wednesday Sept 30
01:00
|
Additional Q&A opportunities
Ask the ConfigMgr Experts: Endpoint Manager ATE series
We had some fantastic Q&A during our Microsoft Ignite digital breakouts and Ask the Expert sessions, but we know you probably have more questions. We also know that the Q&A panel with the Microsoft Endpoint Configuration Manager team continues to be one of our most popular sessions at Microsoft Ignite, so we’re now bringing it to you digitally in Teams Live Events on Wednesday, September 30th. Click the desired time below to add them to your calendar.
Tuesdays with Microsoft Endpoint Manager: Ask the Experts
We’ll continue offering live Q&A through October with more Ask the Experts sessions on Tuesdays:
The Microsoft Endpoint Manager AMA series continues
We’ve been running Ask Microsoft Anything (AMA) events in the Microsoft Tech Community for a few months now, and we aren’t stopping! In fact, we’re pumping them up in October and November to help answer questions you may have from any of the announcements and new features or capabilities we announced at Microsoft Ignite.
To keep tabs on announcements about future AMA events, to attend an AMA, or to see recaps of previous AMAs, bookmark https://aka.ms/AMA/MEM.
Microsoft Endpoint Manager 1:1 consultations
We know not every question is suitable to be asked in a public environment. And, you can’t pull someone aside at a Microsoft Ignite booth this year to ask something privately. As a result, we are opening up some 1:1 consultations with Microsoft Endpoint Manager engineers so you can still dig in where you need to. You’ll be able to start signing up for half-hour slots beginning Monday, September 28th and appointments will be available on weekdays from Thursday, October 1st to Thursday October 8th at different times of the day around the world. Slots will be limited so check back on September 28th to reserve one. (Note, for now, this link points to the Microsoft Endpoint Manager community on Tech Community. It will be redirected to the 1:1 signup tool on September 28th.)
Request a meeting with the Microsoft Endpoint Management leadership team
If you need to have a strategic conversation, possibly including your leadership team, you can submit your request here. When filling out the request form, please provide us a few possible days/times to meet and tell us who else from your organization you’d like to attend. Please also describe what you want to talk about in as much detail as possible so we can find the member of our leadership team that will be the most appropriate for you to speak with.
Become an Endpoint Management Insider
I’d like to conclude this post by announcing our own Insider community for Endpoint Management. We’ll use this community to host special events that we’ll reserve for our truest fans. We’ll also include fun things like community-driven roundtables and games to help connect you with your peers in the field of endpoint management. Sign up to be an Endpoint Management Insider today and watch your email for an invitation to our Insider site.
by Contributed | Sep 25, 2020 | Uncategorized
This article is contributed. See the original author and article here.
Microsoft Ignite is officially wrapped, with big news coming from several products:
SharePoint Syntex,
the first product from Project Cortex, was announced.
Microsoft Teams announced several new capabilities to help people stay connected, collaborate and build solutions in Teams.
Endpoint Analytics is now generally available in Microsoft Endpoint Manager.
@alexandertuvstrom is our Member of the Week, and a great contributor across multiple communities like Windows 10.
View the Weekly Roundup for Sept 21-25th in Sway and attached PDF document.
by Contributed | Sep 25, 2020 | Azure, Technology, Uncategorized
This article is contributed. See the original author and article here.
The most read paths on LEARN has gotten an update. Check out the new paths here and some description on what each path contains:
Azure Fundamentals part 1: Describe core Azure concepts
- Understand the benefits of cloud computing in Azure and how it can save you time and money
- Explain cloud concepts such as high availability, scalability, elasticity, agility, and disaster recovery
- Describe core Azure architecture components such as subscriptions, management groups, resources and resource groups
- Summarize geographic distribution concepts such as Azure regions, region pairs, and availability zones
Azure Fundamentals part 2: Describe core Azure services
- Understand the breadth of services available in Azure including compute, network, storage, and database
- Identify virtualization services such as Azure Virtual Machines, Azure Container Instances, Azure Kubernetes Service, and Windows Virtual Desktop
- Compare Azure’s database services such as Azure Cosmos DB, Azure SQL, Azure Database for MySQL, Azure Database for PostgreSQL, and Azure’s big data and analysis services
- Examine Azure networking resources such as Virtual Networks, VPN Gateways, and Azure ExpressRoute
- Summarize Azure storage services such Azure Blob Storage, Azure Disk Storage, and Azure File Storage
Azure Fundamentals part 3: Describe core solutions and management tools on Azure
- Choose the correct Azure Artificial Intelligence service to address different kinds of business challenges.
- Choose the best software development process tools and services for a given business scenario.
- Choose the correct cloud monitoring service to address different kinds of business challenges.
- Choose the correct Azure management tool to address different kinds of technical needs and challenges.
- Choose the right serverless computing technology for your business scenario.
- Choose the best Azure IoT service for a given business scenario.
Azure Fundamentals part 4: Describe general security and network security features
-
Having a good security strategy is essential in today’s digital world. Every application and service, whether on-premises or in the cloud, needs to be designed with security in mind. Security needs to happen at the application level, at the data level, and at the network level.
Learn about the various Azure services you can use to help ensure that your cloud resources are safe, secure, and trusted.
Azure Fundamentals part 5: Describe identity, governance, privacy, and compliance features
-
With the rise of remote work, bring your own device (BYOD), mobile applications, and cloud applications, the primary security boundary has shifted from firewalls and physical access controls to identity.
Understanding who is using your systems and what they have permission to do are critical to keeping your data safe from attackers. To stay organized, manage costs, and meet your compliance goals, you need a good cloud governance strategy.
Learn how Azure can help you secure access to cloud resources, what it means to build a cloud governance strategy, and how Azure adheres to common regulatory and compliance standards.
Azure Fundamentals part 6: Describe Azure cost management and service level agreements
-
Migration to the cloud presents new ways to think about your IT expenses. The cloud also removes the burden of supporting IT infrastructure.
As you move to the cloud, you might ask:
- How much will it cost?
- What guarantees does Azure provide around uptime and connectivity?
- How do preview services impact my production applications?
Learn about the factors that influence cost, tools you can use to help estimate and manage your cloud spend, and how Azure’s service-level agreements (SLAs) can impact your application design decisions.
by Contributed | Sep 25, 2020 | Azure, Technology, Uncategorized
This article is contributed. See the original author and article here.
The most read paths on LEARN has gotten an update. Check out the new paths here and some description on what each path contains:
Azure Fundamentals part 1: Describe core Azure concepts
- Understand the benefits of cloud computing in Azure and how it can save you time and money
- Explain cloud concepts such as high availability, scalability, elasticity, agility, and disaster recovery
- Describe core Azure architecture components such as subscriptions, management groups, resources and resource groups
- Summarize geographic distribution concepts such as Azure regions, region pairs, and availability zones
Azure Fundamentals part 2: Describe core Azure services
- Understand the breadth of services available in Azure including compute, network, storage, and database
- Identify virtualization services such as Azure Virtual Machines, Azure Container Instances, Azure Kubernetes Service, and Windows Virtual Desktop
- Compare Azure’s database services such as Azure Cosmos DB, Azure SQL, Azure Database for MySQL, Azure Database for PostgreSQL, and Azure’s big data and analysis services
- Examine Azure networking resources such as Virtual Networks, VPN Gateways, and Azure ExpressRoute
- Summarize Azure storage services such Azure Blob Storage, Azure Disk Storage, and Azure File Storage
Azure Fundamentals part 3: Describe core solutions and management tools on Azure
- Choose the correct Azure Artificial Intelligence service to address different kinds of business challenges.
- Choose the best software development process tools and services for a given business scenario.
- Choose the correct cloud monitoring service to address different kinds of business challenges.
- Choose the correct Azure management tool to address different kinds of technical needs and challenges.
- Choose the right serverless computing technology for your business scenario.
- Choose the best Azure IoT service for a given business scenario.
Azure Fundamentals part 4: Describe general security and network security features
-
Having a good security strategy is essential in today’s digital world. Every application and service, whether on-premises or in the cloud, needs to be designed with security in mind. Security needs to happen at the application level, at the data level, and at the network level.
Learn about the various Azure services you can use to help ensure that your cloud resources are safe, secure, and trusted.
Azure Fundamentals part 5: Describe identity, governance, privacy, and compliance features
-
With the rise of remote work, bring your own device (BYOD), mobile applications, and cloud applications, the primary security boundary has shifted from firewalls and physical access controls to identity.
Understanding who is using your systems and what they have permission to do are critical to keeping your data safe from attackers. To stay organized, manage costs, and meet your compliance goals, you need a good cloud governance strategy.
Learn how Azure can help you secure access to cloud resources, what it means to build a cloud governance strategy, and how Azure adheres to common regulatory and compliance standards.
Azure Fundamentals part 6: Describe Azure cost management and service level agreements
-
Migration to the cloud presents new ways to think about your IT expenses. The cloud also removes the burden of supporting IT infrastructure.
As you move to the cloud, you might ask:
- How much will it cost?
- What guarantees does Azure provide around uptime and connectivity?
- How do preview services impact my production applications?
Learn about the factors that influence cost, tools you can use to help estimate and manage your cloud spend, and how Azure’s service-level agreements (SLAs) can impact your application design decisions.

Image 2 – Kubernetes hosted
Image 3 – OSM Components


Recent Comments