
by Contributed | Nov 26, 2020 | Azure, Microsoft, Technology
This article is contributed. See the original author and article here.
Purpose:
This article help you cancel ongoing import or export operation on Azure SQL Database.
Step by Step guidance:
- Open new PowerShell window, you may use cloud shell on Azure portal as well by clicking the cloud shell button

- Copy and paste the following PowerShell code and execute it – it will create a function for the current PowerShell session
-
function Cancel-AzSQLImportExportOperation
{
param
(
[parameter(Mandatory=$true)][string]$ResourceGroupName
,[parameter(Mandatory=$true)][string]$ServerName
,[parameter(Mandatory=$true)][string]$DatabaseName
)
$Operation = Get-AzSqlDatabaseActivity -ResourceGroupName $ResourceGroupName -ServerName $ServerName -DatabaseName $DatabaseName | Where-Object {($_.Operation -eq "ExportDatabase" -or $_.Operation -eq "ImportDatabase") -and $_.State -eq "InProgress"}
if(-not [string]::IsNullOrEmpty($Operation))
{
do
{
Write-Host -ForegroundColor Cyan ("Operation " + $Operation.Operation + " with OperationID: " + $Operation.OperationId + " is now " + $Operation.State)
$UserInput = Read-Host -Prompt "Should I cancel this operation? (Y/N)"
} while($UserInput -ne "Y" -and $UserInput -ne "N")
if($UserInput -eq "Y")
{
"Canceling operation"
Stop-AzSqlDatabaseActivity -ResourceGroupName $ResourceGroupName -ServerName $ServerName -DatabaseName $DatabaseName -OperationId $Operation.OperationId
}
else
{"Exiting without cenceling the operation"}
}
else
{
"No import or export operation is now running"
}
}
- use the function
Cancel-AzSQLImportExportOperation
to cancel an Import or Export operation
- you need to provide the Resource Group name, Server name and Database name where the operation is currently running.
I hope you find it useful.
Thank you Roshna Nazir for pointing out this functionality.
if you have any feedback please do not hesitate to share it with me at yocr@microsoft.com
Yochanan.
by Contributed | Nov 26, 2020 | Azure, Microsoft, Technology
This article is contributed. See the original author and article here.
Hi Everyone,
Zoheb here again with my colleague Tim Beasley. Today, we will be sharing some best practices to help ensure that your VMs (virtual machines) (including Domain Controllers) are secure in your Azure/Cloud environment.
I would like to start this blog with an African Proverb “If you want to go fast, go alone. If you want to go far go together.”
This proverb is one of the principals we refer to internally at Microsoft (#OneMicrosoft). It helps us utilize the synergy to build / leverage great ideas from other Microsoft employees across the globe.
This proverb sums it up perfectly of what occurred during the creation of this blog post. There were multiple contributors (Tristan Kington, Akhlesh Sharma, Pierre Audonnet and Shobhit Garg) who also helped provide details and additional information in hopes of benefiting our customers.
The Initial Problem I found myself facing – I forgot my Administrator Password!
While working in my lab environment in Azure, I sometimes forget what the Administrator password is (This rarely happens. Am I right? :p). Considering this is an important environment I needed to regain access to, I started thinking about different ways of retrieving my password.
Initially, I tried guessing what password was using a few random ones. However, this did not work (I have Azure AD Password Protection configured in my lab to help protect against known passwords :smiling_face_with_smiling_eyes:). I then tried the VM Password Reset option, but that only works for members of the local Administrators group.
Suddenly, I had an epiphany! I remembered the Extensions setting that is available for VMs running in Azure where you can execute scripts running under the System Context.
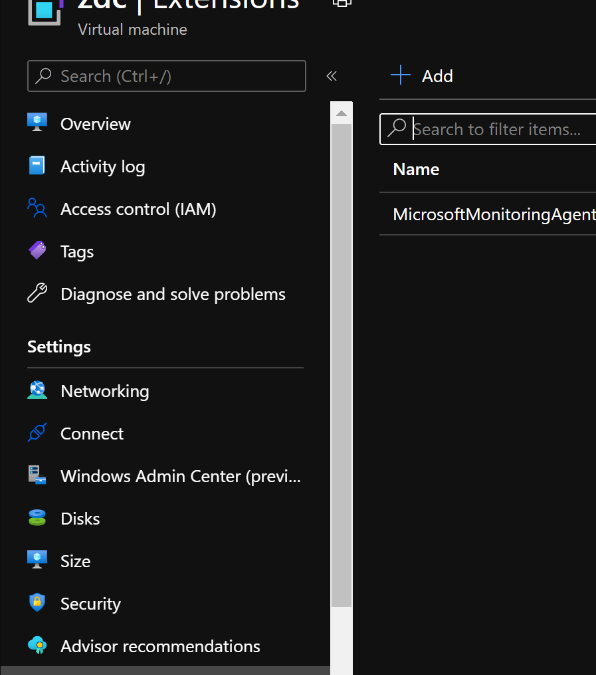
To achieve this, I located and selected the Azure Virtual Machine I was targeting and clicked on Extensions which is located under Settings. Here is where I will upload and execute a Custom Script Extension as shown below:
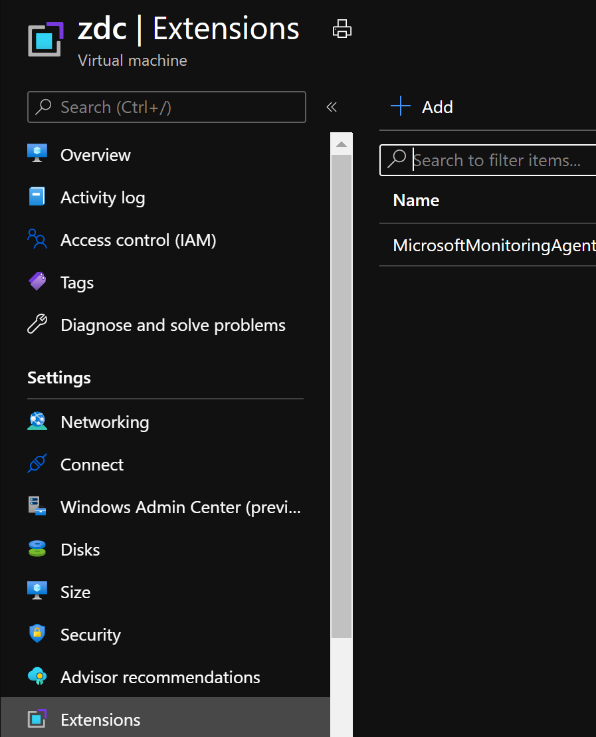
Figure 1. Click on Extensions.
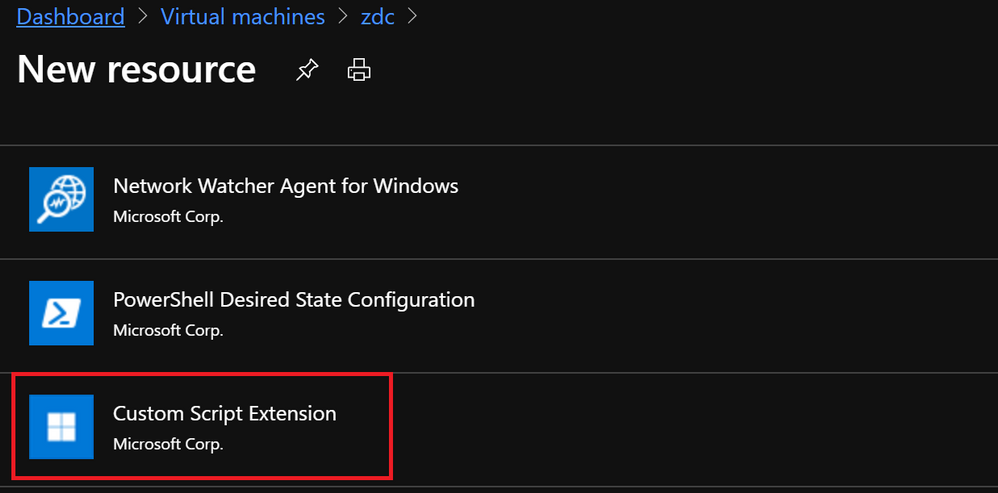
Figure 2. Select Custom Script Extension.
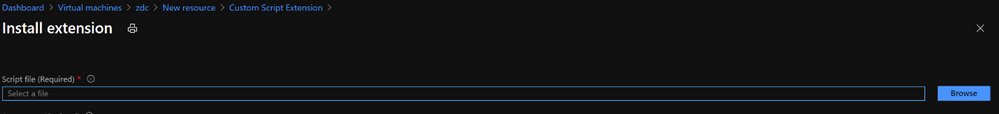
Figure 3. Browse for the custom PowerShell script you wish to upload.
Figure 4. Select Upload to upload your custom PowerShell script.
As you can see below, I uploaded the testreset.ps1 PowerShell script (to be added as a custom script extension) and ran it on the virtual machine in my lab environment. The PowerShell script uses the native Command Prompt utility Net.exe. In this example, we used Net User to reset the password for an Administrator account named zdcadm using DontKeepe@syPassw0rd$ as the password.
Net User zdcadm DontKeepe@syPassw0rd$
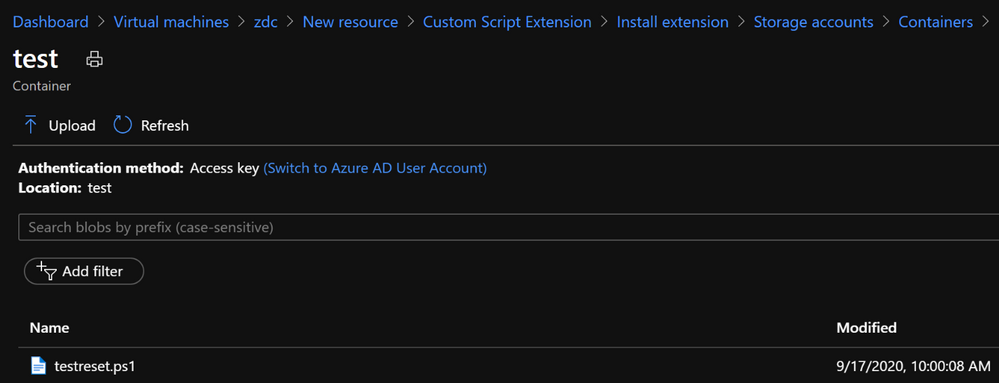
Figure 5. Custom PowerShell script was uploaded.
After the extension was applied and executed against the VM, it successfully reset the password for my Administrator account (zdcadm), which allowed me to regain access to that VM.
We managed to achieve this because Azure VM Agent is installed by default on any Windows VM deployed from an Azure Marketplace image. When you deploy an Azure Marketplace image from the portal, PowerShell, Command Line Interface, or an Azure Resource Manager template, the Azure VM Agent is also installed.
Though I was happy that this allowed me to log back into the VM, it also started to concern me. So, I started thinking about how this could potentially affect our customers and whether they are protecting their environment from such risks where Privilege escalation can be gained by Azure operators to domain admin (and by extension, domain admin on-prem).
We found similar concerns that were raised / discussed for our traditional infrastructure (Hypervisors) where we provide broad guidance on how to secure them. You can learn more about this by reading the Virtualizing Domain Controllers using Hyper-V Microsoft article.
Why should you be concerned?
You as an organization who have DC’s in Azure or cloud you should check who has access to them in Azure & is the access to Subscription controlled well.
Do you have any Azure Operators who could do Privilege Escalation to become a Domain Admin?
Remember when you let someone else administer a lower layer than your own, you are implicitly trusting that person equivalently to yourself.
The 10 Immutable Laws of Security are applicable everywhere.
Increasingly we see permissions being mis managed in many organization and Identity team is not always managing subscriptions, this can lead to some loose permissions on your resources if left unmonitored/checked.
How can you check who has access to your Domain Controllers or Azure Resources ?
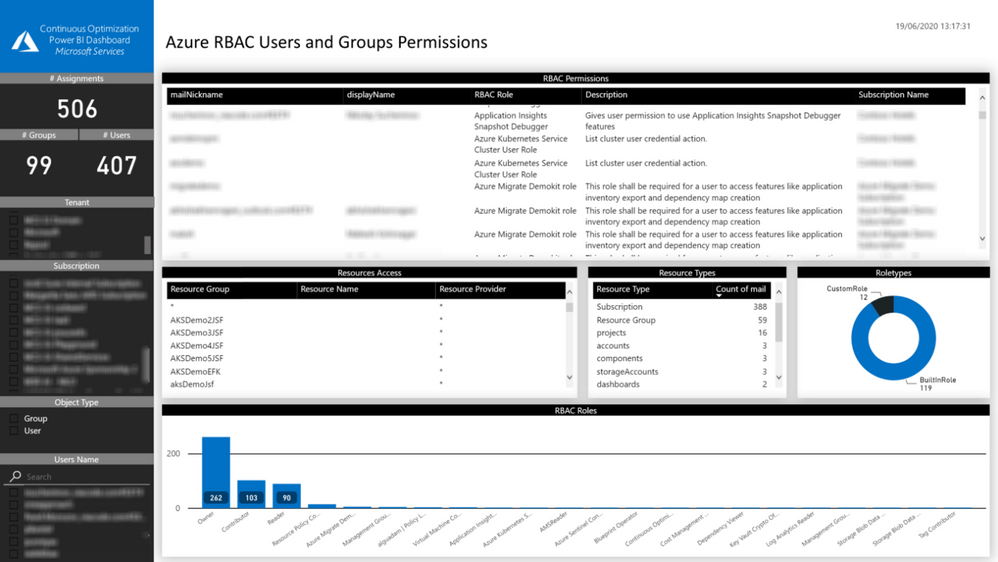
There are many ways you could see who has access to resources, I am listing one of the easier ways where you can get full information from a single dashboard.
Use the Azure Continuous Cloud Optimization dashboard, this can show the Azure RBAC (role-based access control) permissions from all the subscriptions a given Azure account has access to. You will be able to identify the roles applied to all Azure resources and if the subscriptions have custom roles. You can filter the information by:
- Tenant
- Subscription
- Object type
- User
The Solution to this little dilemma:
This made us think about the “Level of Protection” we should recommend to our customers that have important VMs (e.g. Domain Controllers) running in Azure. After several internal discussions along with reviewing publicly available Microsoft documentation, we decided that the following recommendations below will add an extra layer of protection to help secure your Azure IaaS VMs / environment (Not all, but heavy hitters)
- Force MFA (Azure Multi-Factor Authentication) for Admins with access to Domain Controllers (no matter where they are at – on-premises and cloud) whenever they are accessing Azure Portal.
- This will ensure that access to Azure Portal has at least two factor Authentication.
- Use this policy for all the users who have access to Azure Subscription where DC’s are hosted.
- Use Conditional access policies to define Admins location, Trusted machines to access Azure Portal for Domain Controller Subscriptions.
- You can further control the access to the Azure Portal/Subscription by using Conditional Access.
- You could define Trusted location, Trusted devices and many such parameters.
- This will help reduce the access to Domain Controllers.
- Limit Highly privileged users and use RBAC permissions to allow access to only specific people to DC’s.
- This is probably the most crucial point of all, you need to review who has permission to do such an activity and if they really need this.
- You could review this using CCO dashboard.
- Alternatively you could navigate to Azure Portal and look for “Access Control”
- Check for important Role Assignments like “Contributors, Owners etc.
- Review these users on a regular basis
- Where possible, use a Different Subscription for Domain Controllers or Tier 0 systems.
- Effective subscription design helps organizations establish a structure to organize and manage assets in Azure during cloud adoption.
- When possible use a dedicated subscription for all your Tier 0 assets
- PIM (Azure Active Directory Privileged Identity Management) for elevation to Domain Controller VM Access and follow just enough Administration (Least Privilege principal)
- Setup appropriate permissions to the “Azure Resource” through PIM.
- Define Eligible Assignments
- This will ensure that only users who are eligible get access to Domain Controllers in Azure
- Follow Just Enough Administration and least privilege model
- Use Azure ADDS (Active Directory Domain Services) when possible.
- When you create an Azure AD DS managed domain, you define a unique namespace.
- Two Windows Server domain controllers (DCs) are then deployed into your selected Azure region. This deployment of DCs is known as a replica set.
- You do not need to manage, configure, or update these DCs. The Azure platform handles the DCs as part of the managed domain, including backups.
- Since this is managed there is reduced risk also for this
- Using PAW(Privileged Access Workstations) to access Azure portal
- Secured, isolated workstations are critically important for the security of sensitive roles like administrators, developers, and critical service operators.
- Use highly secured user workstations and/or Azure Bastion for administrative tasks for Azure.
- The secured workstations can be centrally managed to enforce secured configuration, including strong authentication, software and hardware baselines, and restricted logical and network access.
- Using conditional access allow only approved machines to have access to Azure portal.
- Alternatively manage these machines through hardened GPO’s & Intune
Hope this helps,
Tim & Zoheb
by Scott Muniz | Nov 26, 2020 | Security, Technology, Tips and Tricks
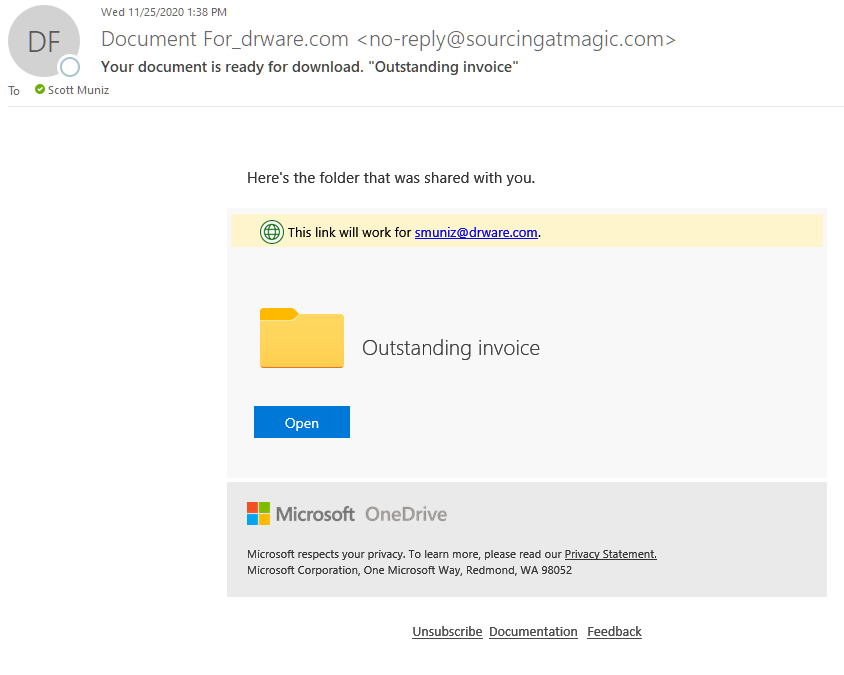
The OneDrive phishing scam is particularly dangerous because of how insidious it is. A seemingly innocuous email shows up in your Inbox with a subject something like this, “Document for [your name].” In the body of the email you see what looks like a familiar OneDrive notice about an available document that has been shared with you by someone you know. Upon clicking on the link or the folder you are forwarded to a familiar Microsoft 365 sign in box.
You enter your email, which is accepted, and then you enter your password, which fails on the first attempt but succeeds on the second. You may end up at office.com or OneDrive but you don’t have access or you don’t see the shared document. At this point you may become suspicious but it’s too late. They now have your Microsoft 365 email and password. They can get into your email, send spam in your name, see/edit/delete your OneDrive files. If you have administrative privileges they can wreak even more havoc. How can you avoid this scam?
How to Vet Your Email Messages
Every email that appears in your Inbox should be vetted no matter if it’s from a friend or foe (see image below).
- Are you expecting this email?
- Check the “sender,” not just the name, but also the email address.
- Hover over (don’t click) all links. A bubble will appear with the link destination.
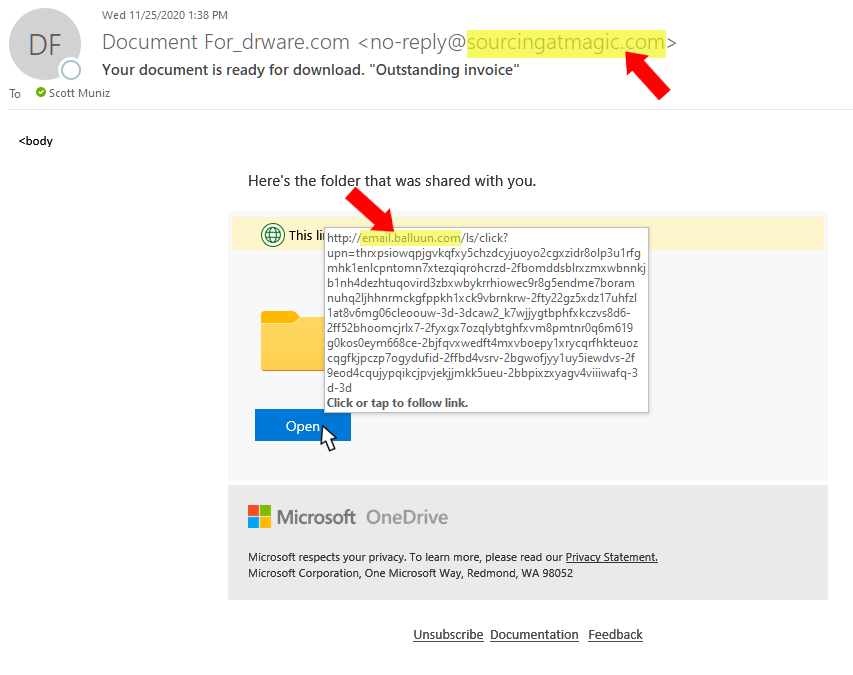
Now you’re equipped with all the information you need. If this is not an expected email then do not click on anything and contact the sender to see if they actually sent you this message. If it is expected or typical for the sender still do steps 2 and 3 above. If either do not match then do not click on anything. You may still want to alert the sender so they can check to see if their email has been hacked.
Additional Steps
Multifactor authentication would completely prevent this type of attack. When your Microsoft 365 administrator activates multifactor authentication then each time you log into Microsoft 365 you are asked for a verification code via text or call. You might even use the Microsoft Authenticator app. This extra step thwarts scammers. Even if someone were to fall for this scam, and the scammer had their Microsoft 365 email and password, when the scammer tries using their credentials a text, call, or email would go to the real user for verification and that would stop the scammer in their tracks. It would also alert the user that their account has been compromised allowing them to take steps to change their password. I strongly recommend multifactor authentication.
The other usual steps are:
- Always keep your Windows OS up-to-date by activating automatic Windows updates.
- Keep your antivirus up-to-date and run frequent virus checks.
- Never ever give anyone your Microsoft 365 password and change it regularly.
- Listen to your gut. If it looks fishy (phishy) then delete it and call or text the sender
Online scams are on a meteoric rise. Diligence will keep you safe. Please be careful!

by Contributed | Nov 26, 2020 | Business, Technology
This article is contributed. See the original author and article here.
Artificial Intelligence (AI) is driving innovative solutions across all industries, but with machine learning (ML) applying a paradigm change to how we approach building products, we are all exploring how to expand our skill sets and enhance our applications.
In this session we won’t be able to teach you how to become a data scientist. But in this on demand session you can spend 3 hours, showing you how to build on your current developer skills to integrate AI services into your business applications and also set you up on your journey to become certified in AI Fundamentals.
During the session we will show you interesting technology through the lens of real business scenarios and to do that we would like to introduce you to Tailwind Traders. Tailwind Traders is a retail company looking for support on how to benefit from applying AI across their business. In ‘Developers Guide to AI’ we will show how Tailwind Traders have solved business challenges and implemented AI technologies.
In this online learning series and associated Microsoft Learn learning paths you will see a wide range of examples: dealing with different types of data (text, audio, image, unstructured), sharing best practices around unstructured search and conversational AI or taking your next step in learning more about machine learning theory with low code solutions.
Session Content
| Introduction |
Introduction to the show and what we want people to achieve. |
| Introducing Computer Vision for Automation in Changing Times |
Cognitive Services: Computer Vision |
| Interview: Willem Mentis (Global AI Community, AI MVP) |
Working with Computer Vision technologies in the real world |
| Extracting Value from Text and Audio to Inform Business Strategy |
Cognitive Services: Text and Speech |
| Interview: James Mann (UK) AI MVP |
Working with Text data and extracting insights |
| Making Sense of your Unstructured Data with AI |
Azure Cognitive Search |
| Interview: Kokila Katyal (BP) / Adelina Balasa (Microsoft) |
Unstructured search in the real world |
| Improve Customer Engagement and Productivity with Conversational AI |
Microsoft Bot Framework Composer + LUIS + QNA Maker |
| Interview: Product Group – Senior PM Microsoft Bot Composer Team Gary Pretty |
Conversational AI, Bot Framework, and the future of this space |
| Start Building Machine Learning Models Faster than You Think |
Azure Machine Learning Designer |
| Interview: Marta Rodriguez Martinez lead data science coach at WhiteHat |
Getting started on your data science journey. |
| Q&A / Summary Session |
All guests back on for live Q&A |
| Close |
More details on MS Learn and Certification |
On Demand Session
Resources & Links from the session.
by Contributed | Nov 26, 2020 | Technology
This article is contributed. See the original author and article here.
With a diminishing boundary between work and life, it becomes more important to keep a track of things to do! Microsoft To Do helps you in managing all your work and personal tasks in one place, while ensuring proper syncing across all devices in an intelligent way.
As a part of our “six tips on To Do” series, in this article, we will focus on the exclusive To Do features available on Android. For six tips on To Do Windows click here.
Happy reading!
1. Reminders to plan your day
Forgot to set up My Day this morning? On Android, you can set a daily reminder to keep on top of your tasks. Find it in your settings!

2. Drag and drop between apps on Android
Quickly add a note or step in Android by dragging and dropping between any app and To Do in split screen view.
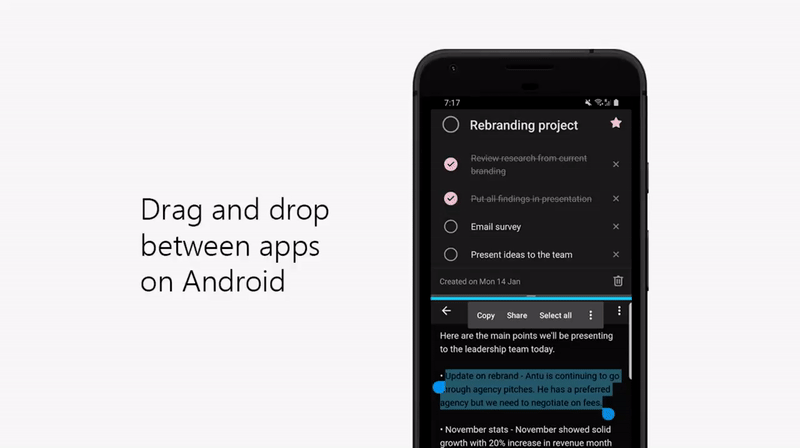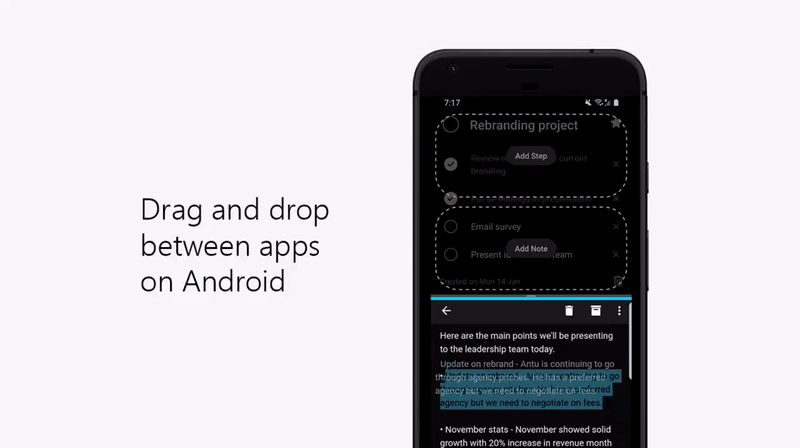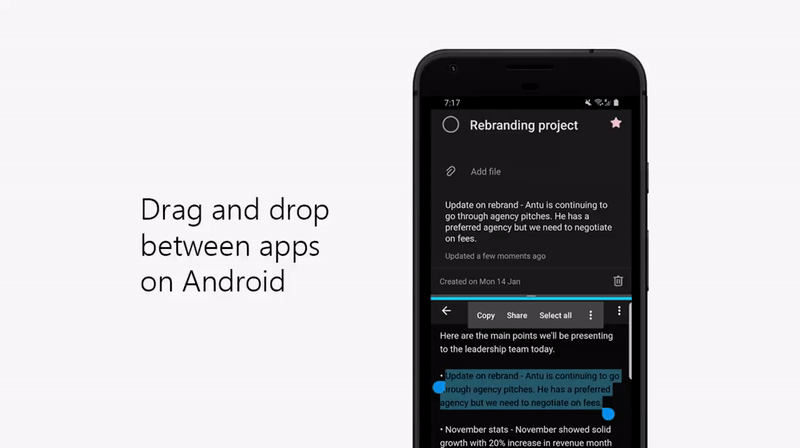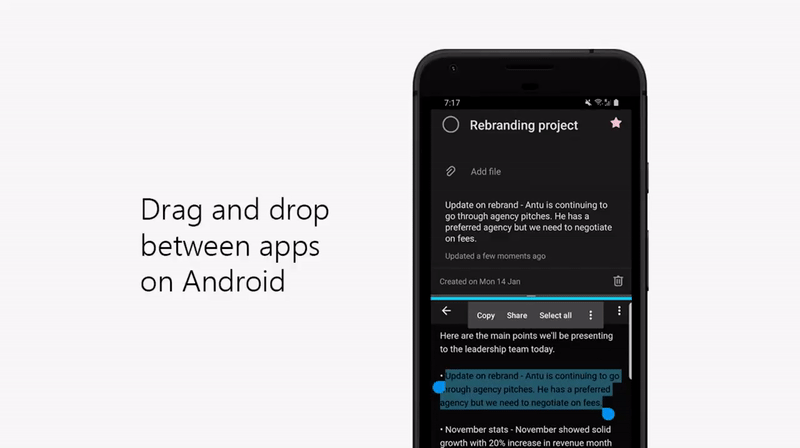
3. Home screen shortcut
Have a list you like to look at frequently? Add a shortcut to your home screen on Android to access it quickly.
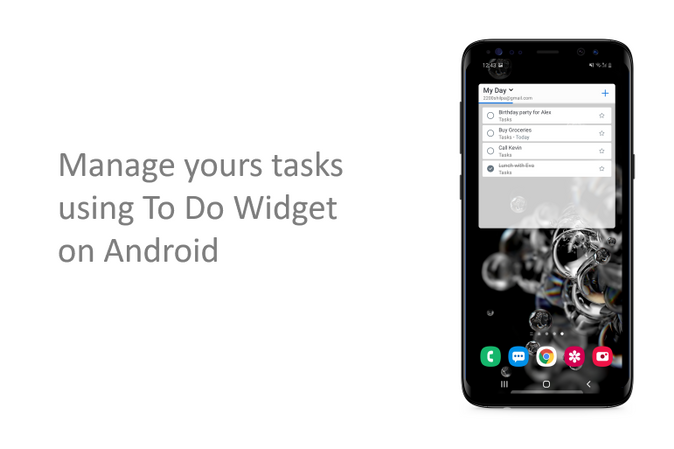
4. To Do widget on Android
To Do widget is available on Android! By using the To Do widget on your Android device you can quickly add and complete tasks without opening the app.
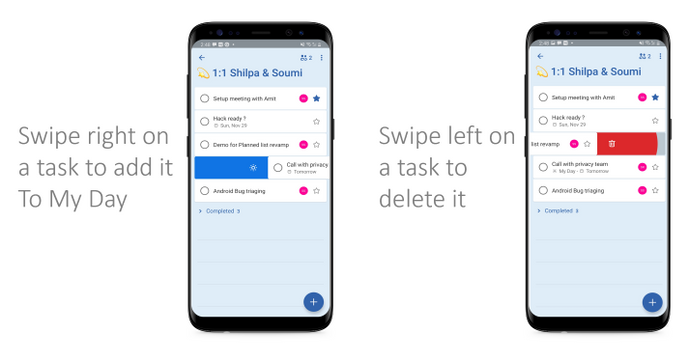
5. Swipe it!
Another quick action for you: just swipe left on any task to delete it, or swipe right to move it or add it to My Day.
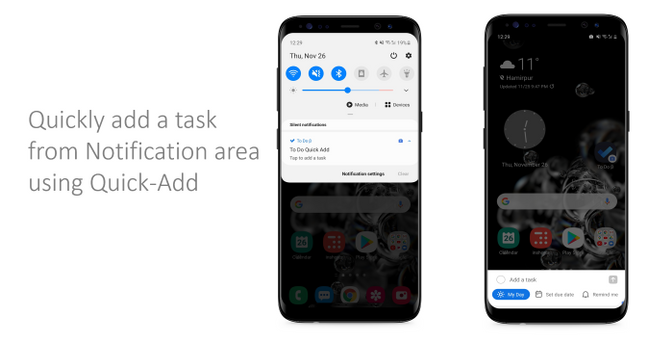
6. Quick add:
Exclusively available for Android To Do users, this persistent notification in your Android notifications area helps you add a task in To Do with just one tap. You can enable it from the notification setting area.
We hope that you enjoyed this article! let us know your feedback in the comments below or over on Twitter and Facebook. You can also write to us at todofeedback@microsoft.com.







Recent Comments