
by Contributed | Nov 25, 2020 | Technology
This article is contributed. See the original author and article here.

Hi IT Pros,
As you knew it, Ransomware is in aggravated assault mode at this time of year 2020, the joint cybersecurity advisory comes from the Cybersecurity Infrastructure and Security Agency (CISA), the Federal Bureau of Investigation (FBI), and the Department of Health and Human Services (HHS) have just given a serious warning about Ransomware Threat as shown in the following announcement:
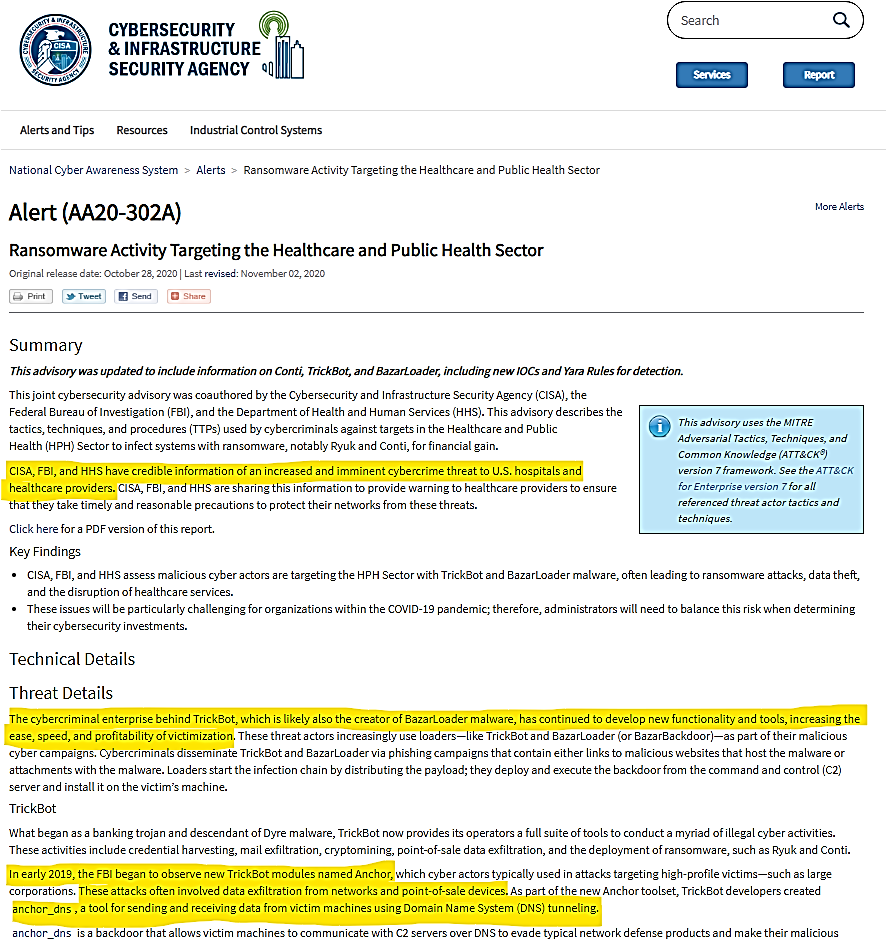
Debut in August of 2018, the Ransomware Ryuk gained shocking attention in 2019, Ryuk gangs demanded multi-million-dollar ransoms from victims, among them are companies, hospitals, and local governments. The actors be able to pocket over $61 million just in the US alone, according to FBI’s report.
Check Point, a security software vendor also noted that the gang was attacking on an average of 20 companies every week in the third quarter of 2020.
Sean Gallagher from Sophos Lab, gave us the story about a typical Ryuk and Conti Ransomeware attack.
- The attack began on the afternoon of Tuesday. September 22,2020 when multiple employees of the targeted company had received highly targeted phishing emails.
- The email was tagged with external sender warnings by the company’s mail software. The link, served up through the mail delivery service Sendgrid, redirected to a malicious document hosted on docs.google.com.
Multiple instances of the malicious attachment were detected and blocked. But there was one employee who clicked on the link in the email that afternoon, allowing the document to execute print_document.exe—a malicious executable identified as Buer Loader.
- The Buer Loader malware dropped qoipozincyusury.exe, a Cobalt Strike “beacon,” along with other malware files.
- Cobalt Strike’s beacon makes a covert connection to the command and control of hackers.
By Wednesday morning the actors had obtained administrative credentials and had connected to a domain controller, where they performed a data dump of Active Directory details.
Data dump to an Admin User directory was most likely accomplished using SharpHound, a Microsoft C#-based data “injestor” tool for BloodHound (an open-source Active Directory analysis tool used to identify attack paths in AD environments).
- Ransomware attack is now ready to remotely deploy to other servers using WMI, Powershell and Remote Desktop RDP
- Next, the SystemBC malicious proxy was deployed on the domain controller. SystemBC is a SOCKS5 proxy used to conceal malware traffic that shares code and forensic markers with other malware from the Trickbot family.
- The malware installed itself (as itvs.exe), and created a scheduled job for the malware, using the old Windows task scheduler format in a file named itvs.job—in order to maintain persistence.
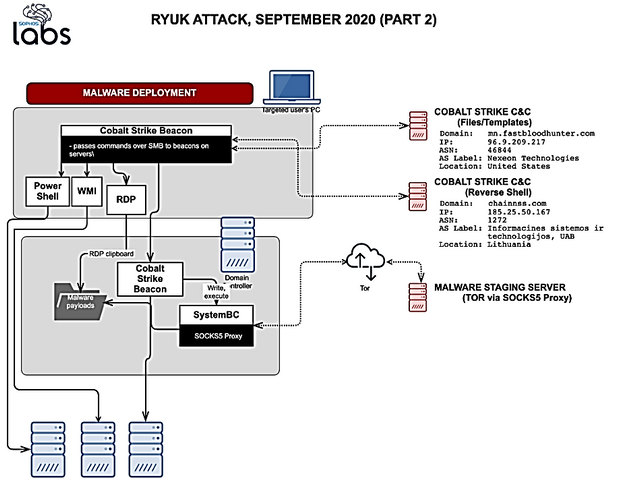
- The organizational backup server was among the first targeted. The attackers used the icacls command to modify access control, giving them full control of all the system folders on the server. GMER is frequently used by ransomware actors to find and shut down hidden processes, and to shut down antivirus software protecting the server.
Ryuk ransomware was redeployed and re-launched three more times in short order after each failed attempt, no files were encrypted.
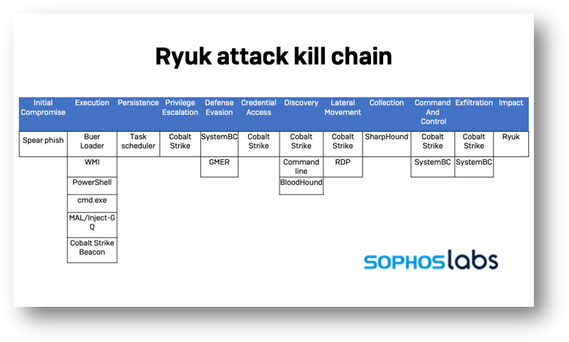
Lesson Learn
- The actor could repeat the attack multiple times with different variants of Ryuk, the attack period could be prolonged for days or weeks with multiple backdoors been used.
- Response time is critical to prevent damage from further steps down the path of attacking sequence, from reconnaissance, credential compromise to later movement, domain dominance and exfiltration, data encryption, data deletion.
- Team effort should be fully utilized during the attacking period.
- If more resources are needed, Security Team could consult with online security support experts ASAP to form an united front against hackers .
- We need to stop the attack at the Cobalt Strike Beacon level (step 2 in the above Chart) when compromised system starts connecting to outside command and control center of actor.
- The attack also shows that Remote Desktop Protocol can be dangerous even when it is inside the firewall.
- Proactive prevention with ASR rules for Office documents’ macros could be an important factor to avoid the ransomware attack right at step 0, by giving no attack opportunity . We should consider it as the best option. (see MD for Endpoint Mitigation Plan)
How good is Microsoft Defender for Endpoint and Identity against ransomware attack?
You may be worried and wonder how good the MD for Endpoint and MD for Identity could protect your systems from ransomware.
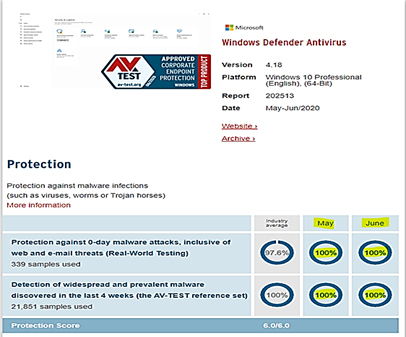
Well, let us bring MD to the test. The most trusted industry test could be AV-Test from the Independent IT-Security Institute, who has been known as the owner of the largest malware database in the world.
- For Windows Systems Antivirus Products. AV-Test conduct monthly tests against widespread and prevalent malware discovered in the last 4 weeks, for example, the test-set of August 2020 included 21,851 (virus) samples. AV-TEST creates identical and reproducible conditions for all the antivirus products from all big AV vendors who join the test program.
- MD for Endpoint continue getting AV-TEST top score monthly as shown in the following image, it scores 100% compared to the Industry at 97.6% protection level:
The test result table for all products based on protection, performance, usability scores is shown here, value of 6 is the highest score:
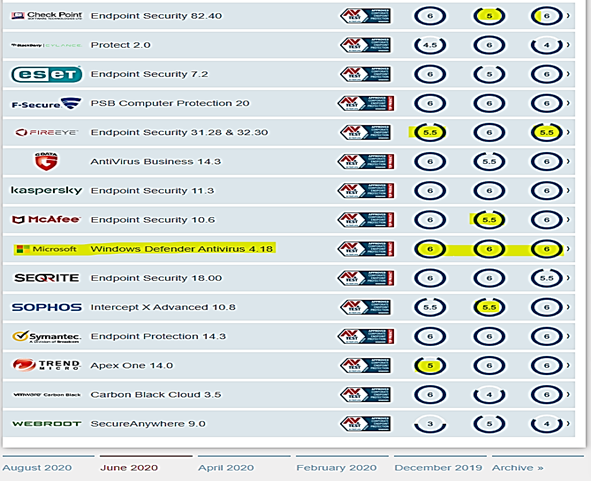
https://www.av-test.org/en/antivirus/business-windows-client/windows-10/june-2020/
Now, let us conduct our own test using the MD for Endpoint – Evaluation Lab feature:
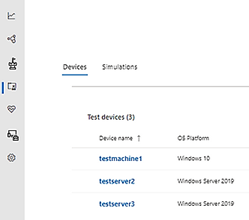
- we will create at least 3 test devices run windows 10 and windows server 2019 as shown here:
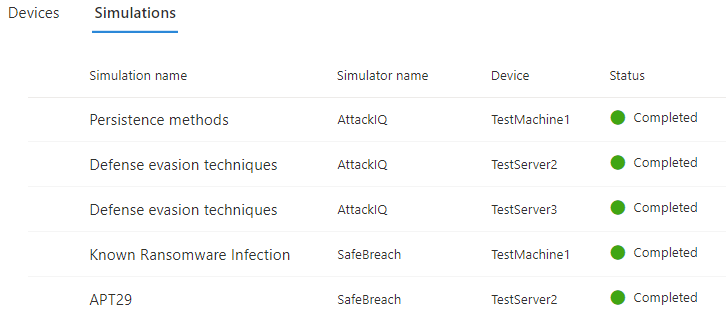
- We run the ” known ransomware infection” simulation by Safe breach for testmachine1
- You may also want to run different attack simulations provided by Safebreach and AttackIQ for different devices
with ” known ransomware infection” attack simulation , the following ransomware names are detected and alerted on test machine1:
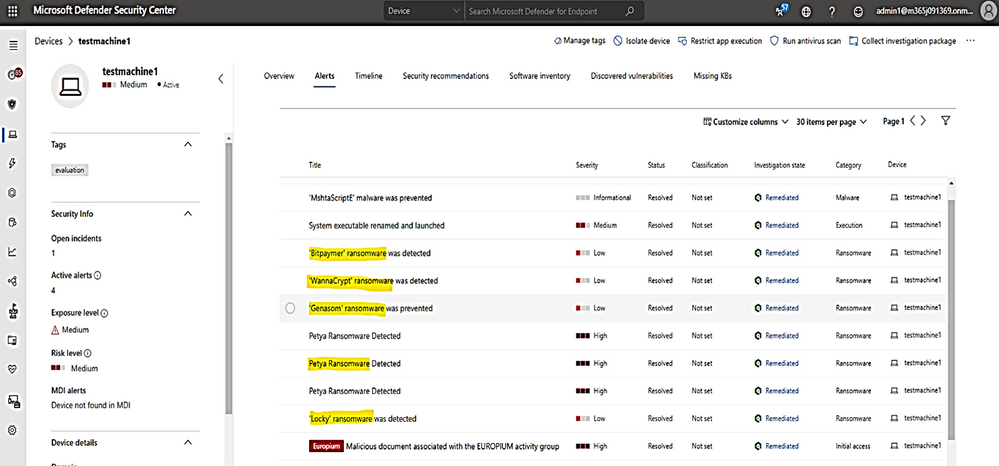
Click on WannaCrypt ransomware to show the details about malicious file named Llac.exe and how long it stayed before being quarantined (3 minutes and 15 seconds):
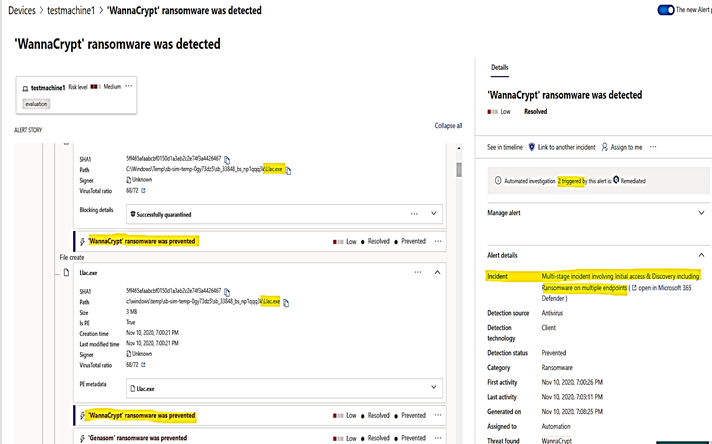
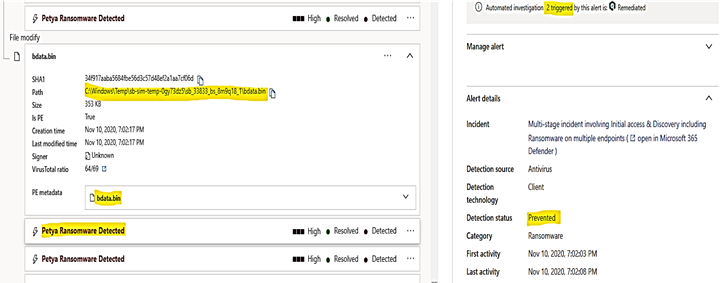
Click on Petya ransomware to show detail of malicious file named bdata.bin, it was existed within only 5 seconds and been quarantined:
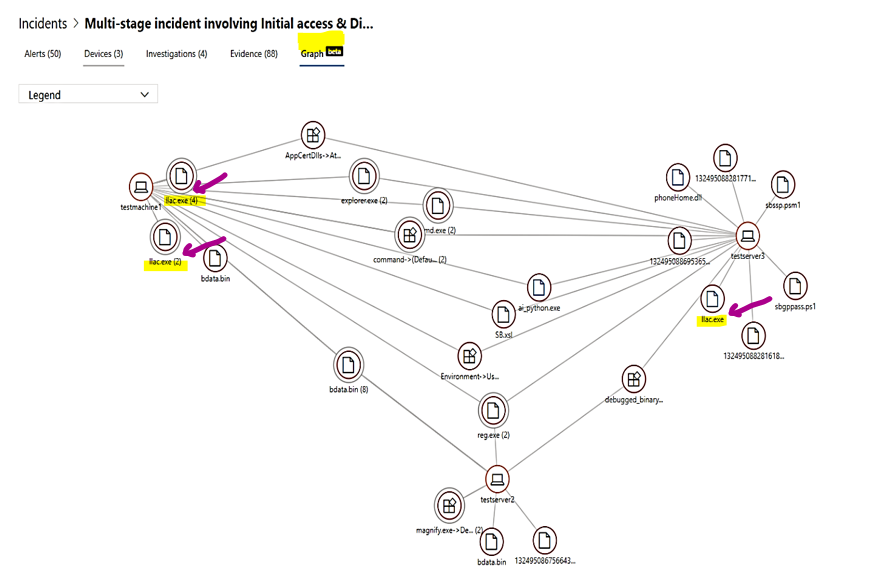
The ransomware attack overview and its entities are shown in the incident named “Multi-stage incident involving Initial access & Discovery including Ransomware on multiple Endpoints” tree graph,
- The Wanacry Ransomware file, llac.exe was blocked at source on testmachine1 with a total of 6 failed attempts.
- The Wanacry Ransomware file, llac.exe was blocked at source on testserver3.
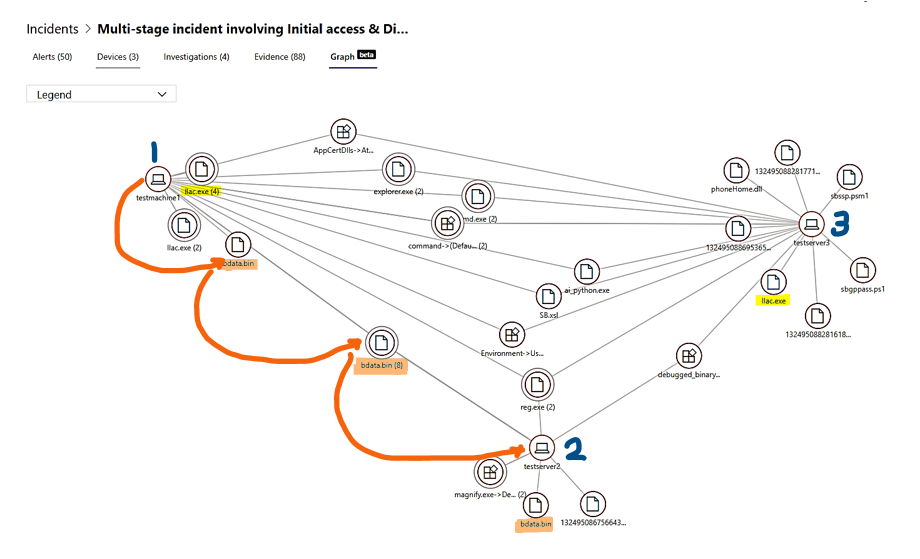
- The Petya ransomware file, bdata.bin had been laterally spread out to testserver2 before it was stopped.
|
Ransomware Action
|
MD for Endpoint and MD for Identity Alert |
| Malicious services were created on remote servers using the same admin credentials, using WMI Event to drop command payload. |
MD for Endpoint Alert: WMI suspicious Event
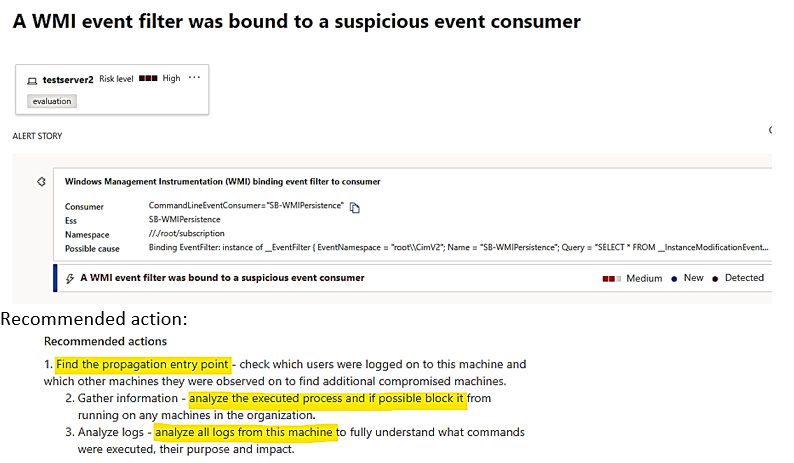
|
| PowerShell is used to download more malicious payloads.
|
MD for Endpoint Alert |
| Credential theft activity |
MD for Identity Alert about overpass the hash attack:
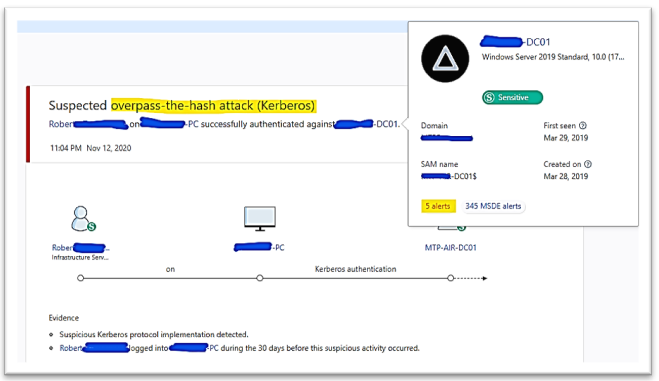
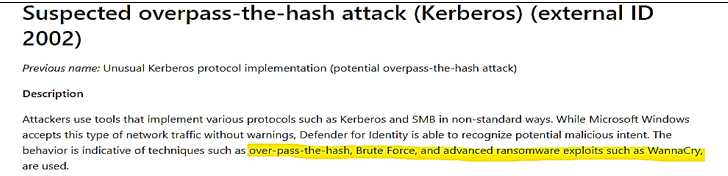
|
| Impersonate action on privilege account and privilege group membership by PowerShell script. |
Alert by MD for Identity and displayed in Cloud App Security Portal:
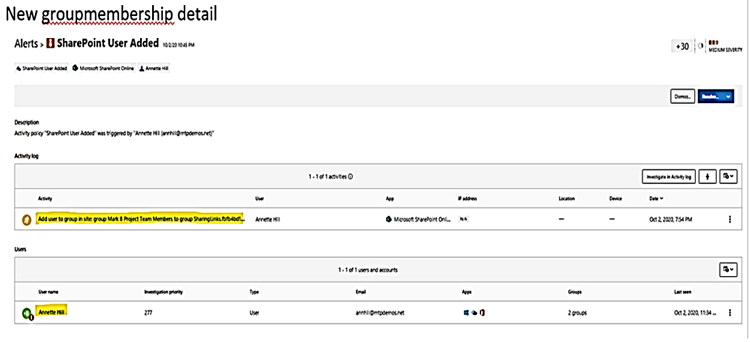
|
| Keyboard hijack activity |
Alert by Defender for Endpoint:
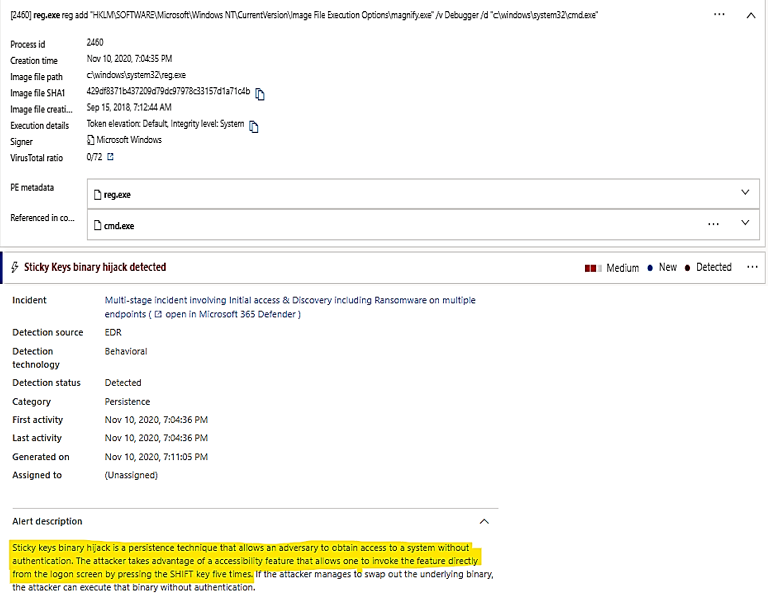
|
| Fileless attacks with memory payload. |
These activities could be detected by AMSI, Microsoft’s Anti-Malware Scanning Interface, when it inspects the in-memory process. MD for Endpoint raised the alert, details as follow:
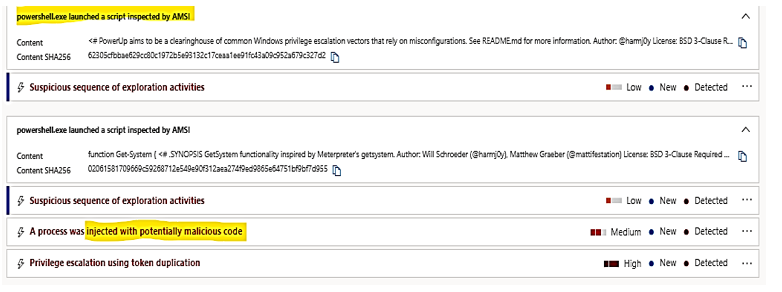
|
| Mimikatz was used as a credential theft tool, It was detected and blocked from installation.
Mimikatz files were quarantined. |
Alert by MD for Endpoint
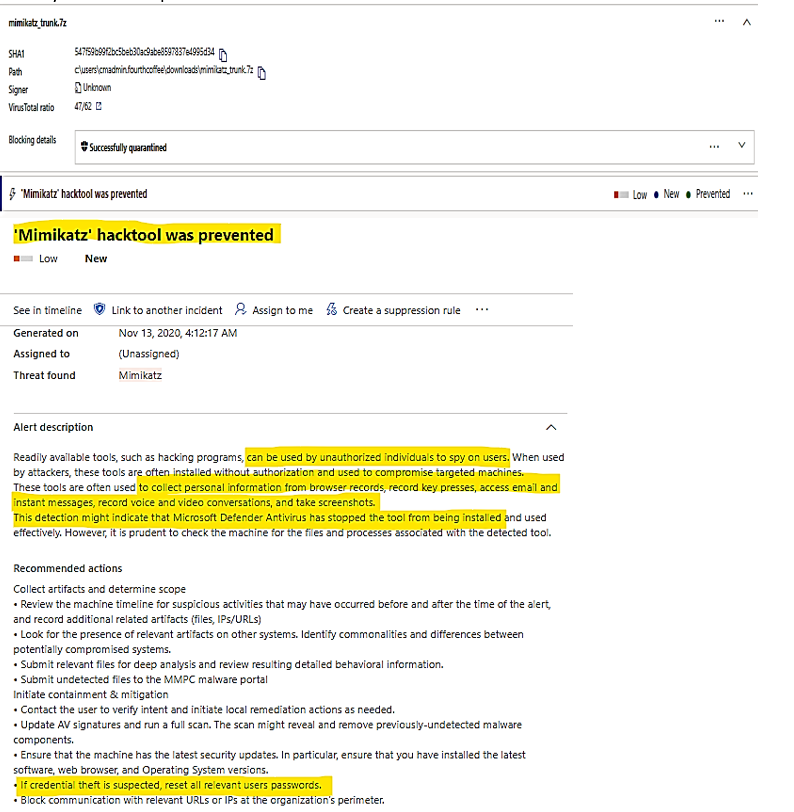
|
| Backdoor activity detected |
Alerted by MD for Endpoint:
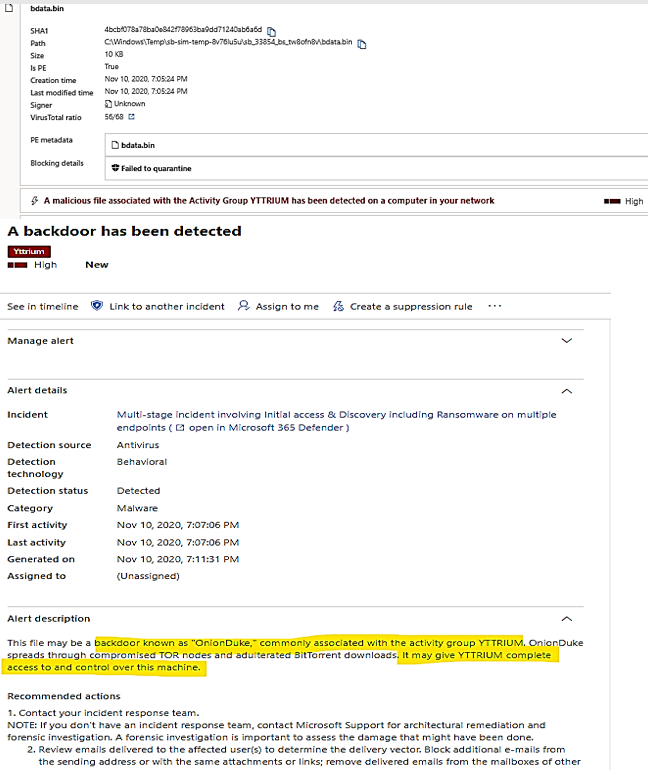
|
| Ransomware Payload and encryption activities are prevented beforehand. |
There is no domain dominant – alert event.
There is no encryption – alert event. |
Ryuk Ransomware Prevention and Protection strategy provided by MD for Endpoint – Threat Analytics.
Microsoft Defender for Endpoint Analytics proposed an analyst report and mitigation (plan) against the Ryuk ransomware. Each of the attack step in Ryuk’s killing chain is mapped to the protection measures which include Antivirus-EDR (MD for Endpoint), Azure ATP (MD for Identity), Multi Factors Authentication MFA, Attack Surface Reduction rules for Office Macro, Windows Host Firewall, and Tamper Protection Security Policy.
The detail of Ryuk attack based on MITRE ATT&CK process is shown in the following image, each Ransomware action step of the attack sequence was mapped to one or multiple counter attack measure:
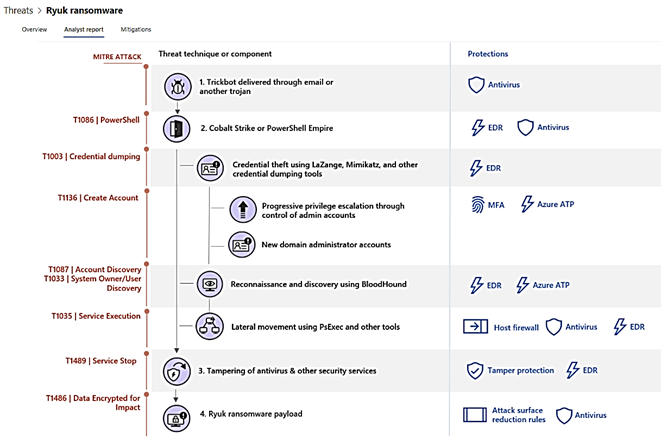
Mitigations provided by MD for Endpoint – Threat Analytics
- Apply these mitigations to reduce the impact of this threat:
- Utilize the Microsoft Defender Firewall and your network firewall to prevent RPC and SMB communication among endpoints whenever possible. This limits lateral movement as well as other attack activities.
- Turn on tamper protection features to prevent attackers from stopping security services.
- Enforce strong, randomized local administrator passwords. Use tools like LAPS.
- Monitor for clearing of event logs. Windows generates a security event ID 1102 when this occurs.
- Ensure internet-facing assets have the latest security updates. Audit these assets regularly for suspicious activity.
- Determine where highly privileged accounts are logging on and exposing credentials. Monitor and investigate logon events (event ID 4624) for logon type attributes. Highly privileged accounts should not be present on workstations.
- Turn on cloud-delivered protection and automatic sample submission on Microsoft Defender Antivirus. These capabilities use artificial intelligence and machine learning to quickly identify and stop new and unknown threats.
- Turn on attack surface reduction rules, including rules that block credential theft, ransomware activity, and suspicious use of PsExec and WMI.
- Check the recommendations card for the deployment status of monitored mitigations in “Threat & Vulnerability Management” under “Remediation”.
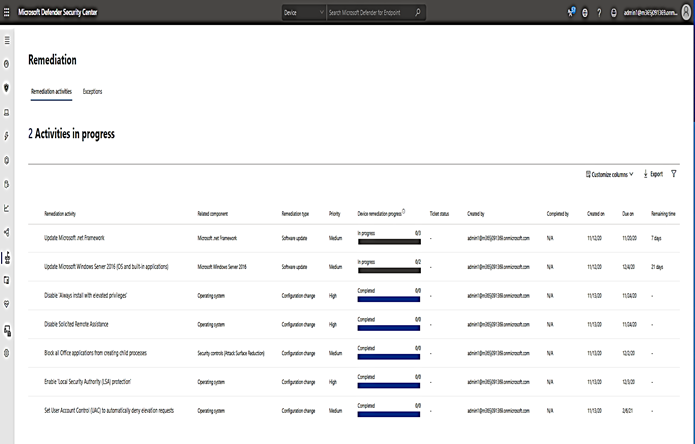
If Security Administrators enable EDR and all features of Defender, setup alert notification and completely finish all of the Defender Endpoint and Defender Identity’s remediation plans against each ransomware and malware, then, I guess, our colleagues may have a much better sleep at night, knowing that their systems are safe and well protected from ransomware and other malware threats.
To get to the 100% level of protection your defender strategy should always include Windows 10 Defender Guard (Application Guard, Credential Guard, Exploit Guard with Attack Surface Reduction rules, System Guard, …) together with MD for Endpoint deployed on workstations and servers and MD for Identity applied to all domain controllers.
I hope the info is useful,
Have a valuable time with your Defender!
___________________________________
Reference:
by Contributed | Nov 24, 2020 | Technology
This article is contributed. See the original author and article here.
What is the Certificate Validation Issue?
DigiCert introduced a new CA which reuses the signing key of an existing and still-valid CA. This means there are 2 different CA certificates in circulation, and either can be included in the chain built for a certificate signed by this shared key. Existing certificates declared in Service Fabric clusters by subject with issuer pinning are at risk of spontaneously failing validation.
How to identify if your cluster is susceptible to the Certificate Validation Issue?
This issue affects any SF cluster that uses a Cluster certificate that is a DigiCert-issued X509 certificate(s), declared by common name with issuer pinning with the following configuration:
- Certificate’s Authority Key Identifier Extension matches
- OId: 2.5.29.35
- KeyID=0f80611c823161d52f28e78d4638b42ce1c6d9e2
- SHA1 thumbprint 1F:B8:6B:11:68:EC:74:31:54:06:2E:8C:9C:C5:B1:71:A4:B7:CC:B4
- valid until 08/Mar/2023
- serial # 01:FD:A3:EB:6E:CA:75:C8:88:43:8B:72:4B:CF:BC:91
- SHA1 thumbprint 62:6D:44:E7:04:D1:CE:AB:E3:BF:0D:53:39:74:64:AC:80:80:14:2C
- valid until 22/Sep/2030
- serial #02:74:2e:aa:17:ca:8e:21:c7:17:bb:1f:fc:fd:0c:a0 ()
- Pinned-issuer list for cluster configuration includes 1fb86b1168ec743154062e8c9cc5b171a4b7ccb4 but does not include 626D44E704D1CEABE3BF0D53397464AC8080142C
If your cluster is not configured using the above properties, you may disregard the rest of this post.
Symptoms in impacted environments
- One or more cluster nodes appear down/unhealthy.
- Cluster is unreachable, whether from the Azure portal or directly (SFX/other clients).
- Event logs show errors like: “authorization failure: CertificateNotMatched”.
- Pending upgrades are not progressing/appear to be stuck.
Required Action
- Follow the Trouble Shooting guide with Mitigation steps: Troubleshooting Guide
- Mitigation specified in the TSG must be applied by you.
If you have any questions or concerns, please contact us by opening a support request. In addition, here are your general support options for Service Fabric: Learn about Azure Service Fabric Support options – Azure Service Fabric | Microsoft Docs.
by Contributed | Nov 24, 2020 | Azure, Microsoft, Technology
This article is contributed. See the original author and article here.
With the new changes to the Azure CLI, building applications has become much easier. This blog post walks you through key changes that can help enhance your productivity.
Some major changes include:
- A simplified single command for creating a new Postgres single server on Azure.
- The ability to use contextual information between CLI commands to help reduce the number of keystrokes for each command.
- New values for the parameter –public to create firewall rules as a part of the create experience.
- New command – list connection strings.
- Improved readable tabular formatted output for sku list and server list commands.
Note: Download the latest official release of the Azure CLI from the Azure CLI page or the dev build from the GitHub Azure CLI homepage.
Important: While this post focuses on Azure Database for PostgreSQL Single server, the changes described apply equally to our Flexible server deployment model.
1. Single command for creating a single server instance
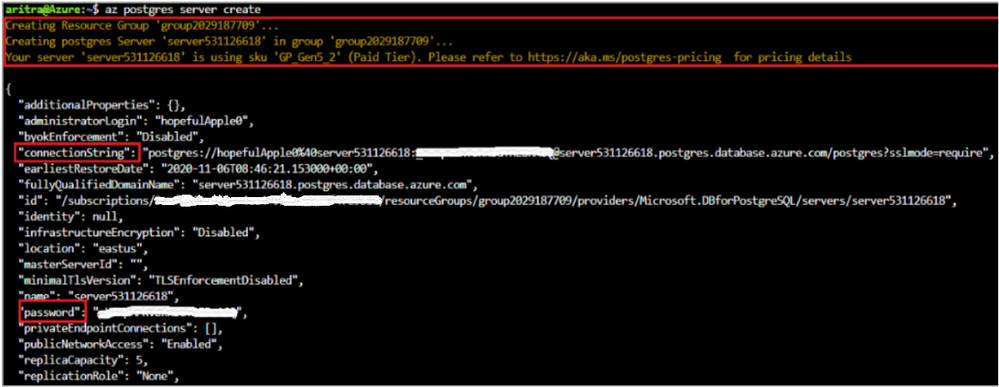
Login to your Azure account using `az login`, select your subscription (if different from default), and then run the command `az postgres server create’ to create a Postgres Single Server Instance on Azure.
Note the following key points:
- A resource group with a random name is created for you in the default region.
- A server-name, admin username, and password are auto-generated for you.
- The text in yellow indicates what is going on behind the scenes. The server gets created with the defaults which can be found using `az postgres server create –help`.
- Two new fields (password and connection-string) are introduced in the output.
- To override a default value, pass that parameter with the value of your choice.
2. Support for param-persist
Azure Database for PostgreSQL server CLI commands now support persisting values of parameters with the `az config param-persist` command , which locally stores information such as location, resource group, administrator login and server name for every sequential CLI command you execute. You can easily turn on param persist to store information using `az config param-persist on`. With param persist turned on, you can see the contextual information using `az config param-persist show`. You can always turn off support for param persist by using `az config param-persist off`.
A summary of points that you might find helpful is listed below:
- Fields commonly stored in param persist are location, resource group, server name and administrator login.
- The param persist is designed to hold only one value for any parameter – which is always from the latest executed command.
- Turning off the param persist does not automatically clear the stored fields. You can clear up all or specific values in the param persist using the commands in `az config param-persist delete`.
- An example of how param persist can reduce the effort is shown below.
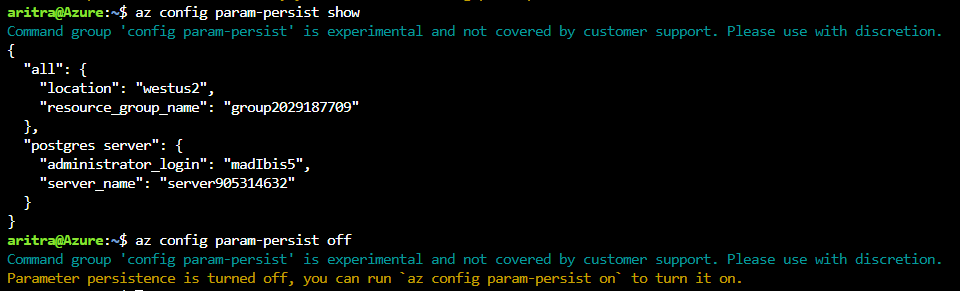
- Note how there is no longer a need to supply the server name and resource group in the firewall creation command when you add a new firewall rule to the server you just created.
az postgres server firewall-rule create -n firewall-rule-1 --start-ip-address 107.223.9.21 --end-ip-address 107.223.9.27
- When in confusion about the values fetched from param persist – look for the text ‘Command argument values from local context’ field in the command output as shown below.
Local context is turned on. Its information is saved in working directory /home/aritra. You can run `az local-context off` to turn it off.
Command argument values from local context: --resource-group: group2029187709, --server-name: server905314632
{- Finished ..
"endIpAddress": "107.223.9.27",
"id": "/subscriptions/<your-subscription-id>/resourceGroups/group2029187709/providers/Microsoft.DBforPostgreSQL/servers/server905314632/firewallRules/firewall-rule-1",
"name": "firewall-rule-1",
"resourceGroup": "group2029187709",
"startIpAddress": "107.223.9.21",
"type": "Microsoft.DBforPostgreSQL/servers/firewallRules"
}
3. New values for the –public parameter in az postgres server create command
When creating a Postgres server using our managed database service on Azure, you want to get started quickly. You can now let the create experience take care of the accessibility based on the value you pass for the –public parameter in the create command. When a server is created with any of these newly supported values, a new field `firewallName` will show up in the output of the create command. In addition to the existing values of ‘Enabled’ and ‘Disabled’, we are now supporting the below values:
Scenario |
Command |
Allow all IPs from 0.0.0.0-255.255.255.255 |
az postgres server create –public all |
Allow access to your client IP only |
az postgres server create –public <SingleIP> |
Allow all IPs within a range |
az postgres server create –public <StartIP-DestinationIP> |
Allow access to all Azure Services |
az postgres server create –public 0.0.0.0 |
Allow public access, but add allowed IPs later |
az postgres server create –public Enabled.
Note : You need to add allowed IPs using `firewall-rule create` command
|
4. New command – az postgres server show-connection-string
`az postgres server show-connection-string`: Lists the connections string for connecting your Postgres database to applications such as ADO.NET, JDBC, JDBC Spring, Node.JS, PHP, Python, and Ruby.
az postgres server show-connection-string -s server905314632 -u flexibleHorse
All placeholder fields within {} in the connection string can be substituted with actual values when you pass them as parameters in the above command.
{
"connectionStrings": {
"C++ (libpq)": "host=server905314632.postgres.database.azure.com port=5432 dbname={database} user=flexibleHorse@server905314632 password={password} sslmode=require",
"ado.net": "Server=server905314632.postgres.database.azure.com;Database={database};Port=5432;User Id=flexibleHorse@server905314632;Password={password};",
"jdbc": "jdbc:postgresql://server905314632.postgres.database.azure.com:5432/{database}?user=flexibleHorse@server905314632&password={password}",
"node.js": "var client = new pg.Client('postgres://flexibleHorse@server905314632:{password}@server905314632.postgres.database.azure.com:5432/{database}');",
"php": "host=server905314632.postgres.database.azure.com port=5432 dbname={database} user=flexibleHorse@server905314632 password={password}",
"psql_cmd": "postgresql://flexibleHorse@server905314632:{password}@server905314632.postgres.database.azure.com/{database}?sslmode=require",
"python": "cnx = psycopg2.connect(database='{database}', user='flexibleHorse@server905314632', host='server905314632.postgres.database.azure.com', password='{password}', port='5432')",
"ruby": "cnx = PG::Connection.new(:host => 'server905314632.postgres.database.azure.com', :user => 'flexibleHorse@server905314632', :dbname => '{database}', :port => '5432', :password => '{password}')"
}
}
5. Improved readable tabular format
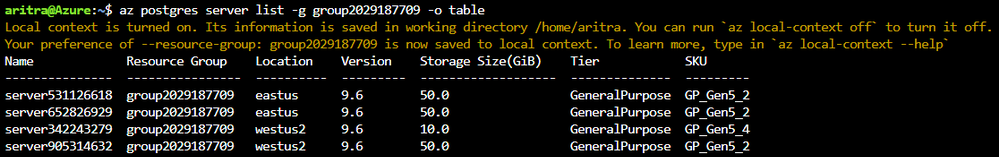
For the commands below, the latest version of the Azure CLI supports viewing output in a tabular format, which provides you with a snapshot view.
- `az postgres server list-skus -l eastus -o table`
- `az postgres server list [-g <group_name>] [-n <server_name>] -o table`
- Not supplying -g and –n would list all servers in the subscription.
- Supplying -g and -n would list the details of a single server.
- Supplying only -g would list the details of all servers in the resource group.
Use powerful Azure CLI utilities with single server CLI
Azure CLI has powerful utilities that can be used with PostgreSQL Server CLI commands from finding right commands, getting readable output or even running REST APIs.
- az find to find the command you are looking.
- Use the
–help argument to get a complete list of commands and subgroups of a group.
- Change the output formatting to table or tsv or yaml formats as you see fit.
- Use az interactive mode which provides interactive shell with auto-completion, command descriptions, and examples.
- Use az upgrade to update your CLI and extensions.
- Use az rest command that lets you call your service endpoints to run GET, PUT, PATCH methods in a secure way.
The improvements have been designed to support the best possible experience for developers to create and manage their PostgreSQL servers. We’d love for you to try out the improvements and share your feedback for new CLI commands or issues with existing ones.

by Contributed | Nov 24, 2020 | Technology
This article is contributed. See the original author and article here.
Sync Up is your monthly podcast hosted by the OneDrive team taking you behind the scenes of OneDrive, shedding light on how OneDrive connects you to all your files in Microsoft 365 so you can share and work together from anywhere. You will hear from experts behind the design and development of OneDrive, as well as customers and Microsoft MVPs. Each episode will also give you news and announcements, special topics of discussion, and best practices for your OneDrive experience.
So, get your ears ready and Subscribe to Sync up podcast!
Episode 15, “OneDrive helps SMBs achieve secure productivity” focusses on the tools available for small and medium businesses (SMBs) to enhance productivity with OneDrive and Microsoft
365 especially as they adapt to remote work. This month cohosts Ankita Kirti and Jason Moore talk with Paul Diamond, Product Marketing Manager for OneDrive for home and SMBs
and Matthew Woodget, founder of Go Narrative, which helps companies improve their team alignment, marketing engagement and sales conversions by building narratives and optimizing messaging. Matthew shares how he leverages OneDrive within his small business and the group discusses most useful OneDrive features for SMBs as well as some tips and tricks.
Tune in!
Meet your show hosts and guests for the episode:

Jason Moore is the principal group program manager for OneDrive and the Microsoft 365 files experience. He loves files, folders, and metadata. Twitter: @jasmo
Ankita Kirti is a product manager on the Microsoft 365 product marketing team responsible for OneDrive for Business. Twitter: @Ankita_Kirti21
Paul Diamond is a Product Marketing Manager for OneDrive for home and SMB.
Matthew Woodget is the founder of GoNarrative, which helps companies improve their team alignment, marketing engagement and sales conversions by building narratives and optimizing messaging. Twitter: @mattwoodget
Listen to the show! If you like what you hear, we’d love for you to Subscribe, Rate and Review it on iTunes or wherever you get your podcasts.
Quick links to the podcast
Links to resources mentioned in the show:
Be sure to visit our show page to hear all the episodes, access the show notes, and get bonus content. And stay connected to the OneDrive community blog where we’ll share more information per episode, guest insights, and take any questions from our listeners and OneDrive users. We, too, welcome your ideas for future episodes topics and segments. Keep the discussion going in comments below.
As you can see, we continue to evolve OneDrive as a place to access, share, and collaborate on all your files in Office 365, keeping them protected and readily accessible on all your devices, anywhere. We, at OneDrive, will shine a recurring light on the importance of you, the user. We will continue working to make OneDrive and related apps more approachable. The OneDrive team wants you to unleash your creativity. And we will do this, together, one episode at a time.
Thanks for your time reading and listening to all things OneDrive,
Ankita Kirti – OneDrive | Microsoft
by Contributed | Nov 24, 2020 | Azure, Microsoft, Technology
This article is contributed. See the original author and article here.
XR Tea Party: BabylonJS & WebXR
Aysegul Yonet
Azure Stack Hub Partner Solutions Series – Cloud Assert
Thomas Maurer
This week, Tiberiu Radu (Azure Stack Hub PM) and I, had the chance to speak to Azure Stack Hub Partner Cloud Assert.
How To Measure The Power Consumption of Your Frontend Application | Sustainable Software
Asim Hussain
The second principle of Sustainable Software Engineering is to build energy efficient applications. The very first step in that direction is to measure the energy your application consumes, also known as its energy cost. Once you measure or estimate the energy cost of your application,
Sarah Lean
Browse content tagged with “Cloud Adoption Framework Series” on Channel 9.
DevOps Cloud Days, Day 3, Nov 18, 2020 – JFrog & Microsoft Azure
Jessica Deen
Join JFrog and Microsoft Azure to learn about integrations and future development. Secure your applications and modernize your business.
Scaling an Online Virtual World with Serverless Tech
Em Lazer-Walker
I help run an annual game design conference called Roguelike Celebration. Naturally, this year we wer…
Monitoring IoT systems from edge to cloud with Datadog
Paul DeCarlo
Microsoft Azure has a strong and active partnership with Datadog , the leading cloud-based monitoring and observability platform. Recently, Datadog and
Static Web App PR Workflow for Azure App Service using Azure DevOps Pt 2 (But what if my code is in GitHub) | Azure DevOps Blog
Abel Wang
Static Web App PR Workflow for Azure App Service using Azure DevOps Pt 2 (But what if my code is in GitHub) In part 1 (Static Web App PR Workflow for Azure App Service), I walked you you through how to set up that sweet pull request workflow for Static Web Apps for your app if your app was: hosted in Azure App Service your code in Azure Repos your CI pipeline in Azure Pipelines.
Azure DevOps Boards and Excel!
Sarah Lean
Use Excel to help manage your Azure DevOps Board items!
AzUpdate: New Priority Account capabilities in Microsoft 365, Bastion and Vnet peering, and more
Anthony Bartolo
Another busy week for cloud services at Microsoft. Here are the news items the team at AzUpdate are covering this week: New Priority Account capabilities now available in Microsoft 365, Azure Bastion and VNet peering can be used together, New integrations between GitHub and Azure Policy allow for better manage policy definitions and assignments, New constrained vCPUs capable VMs now available and of course the Microsoft Learn module of the week.
HOW TO: Create a Windows Server 2019 NAS / FileServer from the command line
Rick Claus
Windows Server 2019 default install has no GUI or Desktop. How do you go about setting this thing up from the command line? In this post I give you the How To on how to setup a simple File Server to replace an old NAS device that was failing in my home lab. We’re talking PowerShell to configure Storage Spaces, User Accounts, SMB Shares, Power Profiles and more!
Control holiday lights with Python, Azure IoT and Power Apps
Jim Bennett
No more controlling your holiday lights by hand – instead use IoT and a no-code mobile app!. Tagged with pythonfunbites, azure, python, iot.
Azure Stack Hub Partner Solutions Series – Cloud Assert
Thomas Maurer
This week, Tiberiu Radu (Azure Stack Hub PM @rctibi) and I, had the chance to speak to Azure Stack Hub Partner Cloud Assert.
AzureFunBytes – Episode 21 – @Azure Security with @deanbryen
Jay Gordon
Security is always the primary concern for those deploying applications into the cloud. This week on… Tagged with azure, security, tutorial, beginners.
Translating text with just a few lines of code using Azure Cognitive Services
Christopher Harrison
This article is part of #PythonFunBites. An old co-worker of mine is fond of saying “we’re not launc… Tagged with pythonbites, azure, python, ai.
Getting started with web dev using Flask
Christopher Harrison
This article is part of #PythonFunBites. There’s a lot of different web dev frameworks out there, an… Tagged with pythonfunbites, python, flask, webdev.
Set up Azure Shell locally – part 2
Pierre Roman
Azure Cloud Shell running in Visual Studio Code – differences with VS Code.
Working with Jupyter Notebooks in Visual Studio Code
Jasmine Greenaway
How to use Jupyter Notebooks in Visual Studio Code. Tagged with pythonfunbites, azure, python.
What’s New in Azure DevOps Docs For October? | Azure DevOps Blog
Abel Wang
What’s new for October1, 2020 – October 31, 2020 Hey hey! New docs have dropped for Azure DevOps for the month of October. What has changed? Oh, just things like… Delete and recover packages Remove, delete, or restore work items Use the Cross-platform CLI for Azure DevOps using personal access tokens (PATs) …and much more!
AzureFunBytes Short – Azure Containers (Kubernetes, Container Instances, More) | Azure DevOps Blog
Jay Gordon
Containers provide an easy way to run batch jobs without having to manage an environment and dependencies. Dynamic compute options, such as Azure Container Instances (ACI), can be used to efficiently ingest source data, process it, and place it in a durable store such as Azure Blob storage.
The Python Community is Stronger Together
Nina Zakharenko
Some thoughts on how to stay connected with the Python Community in 2020.
Microsoft 365 PnP Weekly – Episode 105 – Microsoft 365 Developer Blog
Waldek Mastykarz
Connect to the latest conferences, trainings, and blog posts for Microsoft 365, Office client, and SharePoint developers. Join the Microsoft 365 Developer Program.
Microsoft Autonomous Driving Startups Program
Adi Polak
Join us for an exceptional conversation with Aditya from the Microsoft Autonomous Driving program. Aditya shares the trends in Autonomous Driving, what startups are building, how Microsoft can help,
Lisa At The Edge Podcast – Thomas Maurer – Career Development & Azure Arc
Thomas Maurer
Lisa At The Edge Podcast – Thomas Maurer – Career Development & Azure Arc we talked about Azure Arc and Azure Hybrid Cloud!
Control holiday lights with Python, Azure IoT and Power Apps
Jim Bennett
As the December holiday season descends, some cultures celebrate with lights, where’s other folks have breaks from school and are looking for a fun





Recent Comments