by Scott Muniz | Dec 21, 2020 | Security, Technology
This article is contributed. See the original author and article here.
| adremsoft — netcrunch |
AdRem NetCrunch 10.6.0.4587 has a Cross-Site Request Forgery (CSRF) vulnerability in the NetCrunch web client. Successful exploitation requires a logged-in user to open a malicious page and leads to account takeover. |
2020-12-16 |
5.8 |
CVE-2019-14481
MISC
MISC |
| adremsoft — netcrunch |
AdRem NetCrunch 10.6.0.4587 has a Server-Side Request Forgery (SSRF) vulnerability in the NetCrunch server. Every user can trick the server into performing SMB requests to other systems. |
2020-12-16 |
4 |
CVE-2019-14476
MISC
MISC |
| altran — picotcp |
An issue was discovered in picoTCP 1.7.0. The code for creating an ICMPv6 echo replies doesn’t check whether the ICMPv6 echo request packet’s size is shorter than 8 bytes. If the size of the incoming ICMPv6 request packet is shorter than this, the operation that calculates the size of the ICMPv6 echo replies has an integer wrap around, leading to memory corruption and, eventually, Denial-of-Service in pico_icmp6_send_echoreply_not_frag in pico_icmp6.c. |
2020-12-11 |
5 |
CVE-2020-17443
MISC
MISC |
| altran — picotcp |
An issue was discovered in picoTCP 1.7.0. The code for parsing the hop-by-hop IPv6 extension headers does not validate the bounds of the extension header length value, which may result in Integer Wraparound. Therefore, a crafted extension header length value may cause Denial-of-Service because it affects the loop in which the extension headers are parsed in pico_ipv6_process_hopbyhop() in pico_ipv6.c. |
2020-12-11 |
5 |
CVE-2020-17442
MISC
MISC |
| altran — picotcp |
An issue was discovered in picoTCP and picoTCP-NG through 1.7.0. The code that processes DNS responses in pico_mdns_handle_data_as_answers_generic() in pico_mdns.c does not check whether the number of answers/responses specified in a DNS packet header corresponds to the response data available in the packet, leading to an out-of-bounds read, invalid pointer dereference, and Denial-of-Service. |
2020-12-11 |
5 |
CVE-2020-24340
MISC
MISC |
| altran — picotcp |
An issue was discovered in picoTCP and picoTCP-NG through 1.7.0. The DNS domain name record decompression functionality in pico_dns_decompress_name() in pico_dns_common.c does not validate the compression pointer offset values with respect to the actual data present in a DNS response packet, causing out-of-bounds reads that lead to Denial-of-Service. |
2020-12-11 |
5 |
CVE-2020-24339
MISC
MISC |
| altran — picotcp |
An issue was discovered in picoTCP 1.7.0. The code for processing the IPv6 headers does not validate whether the IPv6 payload length field is equal to the actual size of the payload, which leads to an Out-of-Bounds read during the ICMPv6 checksum calculation, resulting in either Denial-of-Service or Information Disclosure. This affects pico_ipv6_extension_headers and pico_checksum_adder (in pico_ipv6.c and pico_frame.c). |
2020-12-11 |
6.4 |
CVE-2020-17441
MISC
MISC |
| altran — picotcp |
An issue was discovered in picoTCP and picoTCP-NG through 1.7.0. When an unsupported TCP option with zero length is provided in an incoming TCP packet, it is possible to cause a Denial-of-Service by achieving an infinite loop in the code that parses TCP options, aka tcp_parse_options() in pico_tcp.c. |
2020-12-11 |
5 |
CVE-2020-24337
MISC
MISC |
| altran — picotcp |
An issue was discovered in picoTCP and picoTCP-NG through 1.7.0. The TCP input data processing function in pico_tcp.c does not validate the length of incoming TCP packets, which leads to an out-of-bounds read when assembling received packets into a data segment, eventually causing Denial-of-Service or an information leak. |
2020-12-11 |
6.4 |
CVE-2020-24341
MISC
MISC |
| altran — picotcp |
An issue was discovered in picoTCP 1.7.0. The code for processing the IPv6 destination options does not check for a valid length of the destination options header. This results in an Out-of-Bounds Read, and, depending on the memory protection mechanism, this may result in Denial-of-Service in pico_ipv6_process_destopt() in pico_ipv6.c. |
2020-12-11 |
5 |
CVE-2020-17445
MISC
MISC |
| altran — picotcp |
An issue was discovered in picoTCP 1.7.0. The routine for processing the next header field (and deducing whether the IPv6 extension headers are valid) doesn’t check whether the header extension length field would overflow. Therefore, if it wraps around to zero, iterating through the extension headers will not increment the current data pointer. This leads to an infinite loop and Denial-of-Service in pico_ipv6_check_headers_sequence() in pico_ipv6.c. |
2020-12-11 |
5 |
CVE-2020-17444
MISC
MISC |
| alumni_management_system_project — alumni_management_system |
A Remote Code Execution vulnerability exists in DourceCodester Alumni Management System 1.0. An authenticated attacker can upload arbitrary file in the gallery.php page and executing it on the server reaching the RCE. |
2020-12-15 |
6.5 |
CVE-2020-28072
MISC |
| amazee — lagoon |
The GitLab Webhook Handler in amazee.io Lagoon before 1.12.3 has incorrect access control associated with project deletion. |
2020-12-14 |
5 |
CVE-2020-35236
MISC
MISC
MISC
MISC |
| apache — airflow |
In Apache Airflow versions prior to 1.10.13, the Charts and Query View of the old (Flask-admin based) UI were vulnerable for SSRF attack. |
2020-12-14 |
5 |
CVE-2020-17513
MISC |
| apache — airflow |
The “origin” parameter passed to some of the endpoints like ‘/trigger’ was vulnerable to XSS exploit. This issue affects Apache Airflow versions prior to 1.10.13. This is same as CVE-2020-13944 but the implemented fix in Airflow 1.10.13 did not fix the issue completely. |
2020-12-11 |
4.3 |
CVE-2020-17515
MLIST
MLIST
MLIST
MLIST
MISC
MLIST |
| apache — airflow |
In Airflow versions prior to 1.10.13, when creating a user using airflow CLI, the password gets logged in plain text in the Log table in Airflow Metadatase. Same happened when creating a Connection with a password field. |
2020-12-14 |
4 |
CVE-2020-17511
MISC |
| askey — ap5100w_firmware |
Askey AP5100W devices through AP5100W_Dual_SIG_1.01.097 are affected by WPS PIN offline brute-force cracking. This arises because of issues with the random number selection for the Diffie-Hellman exchange. By capturing an attempted (and even failed) WPS authentication attempt, it is possible to brute force the overall authentication exchange. This allows an attacker to obtain the recovered WPS PIN in minutes or even seconds, and eventually obtain the Wi-Fi PSK key, gaining access to the Wi=Fi network. |
2020-12-11 |
4.3 |
CVE-2020-15023
MISC
CONFIRM
MISC |
| awstats — awstats |
In AWStats through 7.8, cgi-bin/awstats.pl?config= accepts a partial absolute pathname (omitting the initial /etc), even though it was intended to only read a file in the /etc/awstats/awstats.conf format. NOTE: this issue exists because of an incomplete fix for CVE-2017-1000501 and CVE-2020-29600. |
2020-12-12 |
5 |
CVE-2020-35176
MISC |
| bitdefender — antivirus_plus |
An Origin Validation Error vulnerability in the SafePay component of Bitdefender Antivirus Plus allows a web resource to misrepresent itself in the URL bar. This issue affects: Bitdefender Antivirus Plus versions prior to 25.0.7.29. |
2020-12-14 |
4.3 |
CVE-2020-15733
CONFIRM |
| brocade — fabric_os |
Brocade Fabric OS versions before v9.0.0, v8.2.2c, v8.2.1e, v8.1.2k, v8.2.0_CBN3, v7.4.2g contain an improper input validation weakness in the command line interface when secccrypptocfg is invoked. The vulnerability could allow a local authenticated user to run arbitrary commands and perform escalation of privileges. |
2020-12-11 |
4.6 |
CVE-2020-15375
CONFIRM |
| brocade — fabric_os |
Brocade Fabric OS versions before v9.0.0 and after version v8.1.0, configured in Virtual Fabric mode contain a weakness in the ldap implementation that could allow a remote ldap user to login in the Brocade Fibre Channel SAN switch with “user” privileges if it is not associated with any groups. |
2020-12-11 |
4 |
CVE-2020-15376
CONFIRM |
| citrix — gateway_plug-in |
Improper privilege management on services run by Citrix Gateway Plug-in for Windows, versions before and including 13.0-61.48 and 12.1-58.15, allows an attacker to modify arbitrary files. |
2020-12-14 |
5 |
CVE-2020-8258
MISC |
| classroombookings — classroombookings |
SQL Injection in Classbooking before 2.4.1 via the username field of a CSV file when adding a new user. |
2020-12-14 |
6.5 |
CVE-2020-35382
MISC |
| cmsmadesimple — cms_made_simple |
Cross Site Scripting (XSS) vulnerability in the Showtime2 Slideshow module in CMS Made Simple (CMSMS) 2.2.4. |
2020-12-17 |
4.3 |
CVE-2020-20138
MISC |
| contiki-ng — contiki-ng |
An issue was discovered in Contiki through 3.0. An Integer Overflow exists in the uIP TCP/IP Stack component when parsing TCP MSS options of IPv4 network packets in uip_process in net/ipv4/uip.c. |
2020-12-11 |
5 |
CVE-2020-13988
MISC
MISC |
| contiki-os — contiki |
An issue was discovered in Contiki through 3.0. A memory corruption vulnerability exists in the uIP TCP/IP stack component when handling RPL extension headers of IPv6 network packets in rpl_remove_header in net/rpl/rpl-ext-header.c. |
2020-12-11 |
5 |
CVE-2020-13985
MISC
MISC |
| contiki-os — contiki |
An issue was discovered in Contiki through 3.0. An infinite loop exists in the uIP TCP/IP stack component when processing IPv6 extension headers in ext_hdr_options_process in net/ipv6/uip6.c. |
2020-12-11 |
5 |
CVE-2020-13984
MISC
MISC |
| contiki-os — contiki |
An issue was discovered in Contiki through 3.0. An infinite loop exists in the uIP TCP/IP stack component when handling RPL extension headers of IPv6 network packets in rpl_remove_header in net/rpl/rpl-ext-header.c. |
2020-12-11 |
5 |
CVE-2020-13986
MISC
MISC |
| contiki-os — contiki |
An issue was discovered in Contiki through 3.0. An Out-of-Bounds Read vulnerability exists in the uIP TCP/IP Stack component when calculating the checksums for IP packets in upper_layer_chksum in net/ipv4/uip.c. |
2020-12-11 |
5 |
CVE-2020-13987
MISC
MISC |
| dell — bsafe_micro_edition_suite |
Dell BSAFE Micro Edition Suite, versions prior to 4.5, are vulnerable to an Unchecked Return Value Vulnerability. An unauthenticated remote attacker could potentially exploit this vulnerability to modify and corrupt the encrypted data. |
2020-12-16 |
5 |
CVE-2020-5359
MISC |
| dell — bsafe_micro_edition_suite |
Dell BSAFE Micro Edition Suite, versions prior to 4.5, are vulnerable to a Buffer Under-Read Vulnerability. An unauthenticated remote attacker could potentially exploit this vulnerability resulting in undefined behaviour, or a crash of the affected systems. |
2020-12-16 |
5 |
CVE-2020-5360
MISC |
| directoriespro — directories_pro |
A cross-site scripting (XSS) vulnerability exists in the SabaiApps WordPress Directories Pro plugin version 1.3.45 and previous, allows attackers who have convinced a site administrator to import a specially crafted CSV file to inject arbitrary web script or HTML as the victim is proceeding through the file import workflow. |
2020-12-14 |
4.3 |
CVE-2020-29304
MISC
FULLDISC
MISC
MISC |
| directoriespro — directories_pro |
A cross-site scripting (XSS) vulnerability in the SabaiApp Directories Pro plugin 1.3.45 for WordPress allows remote attackers to inject arbitrary web script or HTML via a POST to /wp-admin/admin.php?page=drts/directories&q=%2F with _drts_form_build_id parameter containing the XSS payload and _t_ parameter set to an invalid or non-existent CSRF token. |
2020-12-14 |
4.3 |
CVE-2020-29303
MISC
FULLDISC
CONFIRM
MISC |
| eclipse — che |
A flaw was found in Eclipse Che in versions prior to 7.14.0 that impacts CodeReady Workspaces. When configured with cookies authentication, Theia IDE doesn’t properly set the SameSite value, allowing a Cross-Site Request Forgery (CSRF) and consequently allowing a cross-site WebSocket hijack on Theia IDE. This flaw allows an attacker to gain full access to the victim’s workspace through the /services endpoint. To perform a successful attack, the attacker conducts a Man-in-the-middle attack (MITM) and tricks the victim into executing a request via an untrusted link, which performs the CSRF and the Socket hijack. The highest threat from this vulnerability is to confidentiality, integrity, as well as system availability. |
2020-12-14 |
6.8 |
CVE-2020-14368
MISC |
| egavilanmedia — barcodes_generator |
EGavilan Barcodes generator 1.0 is affected by: Cross Site Scripting (XSS) via the index.php. An Attacker is able to inject the XSS payload in the web application each time a user visits the website. |
2020-12-15 |
4.3 |
CVE-2020-35396
MISC
MISC
MISC |
| egavilanmedia — expense_management_system |
XSS in the Add Expense Component of EGavilan Media Expense Management System 1.0 allows an attacker to permanently store malicious JavaScript code via the ‘description’ field |
2020-12-15 |
4.3 |
CVE-2020-35395
MISC
MISC |
| envoyproxy — envoy |
Envoy before 1.16.1 logs an incorrect downstream address because it considers only the directly connected peer, not the information in the proxy protocol header. This affects situations with tcp-proxy as the network filter (not HTTP filters). |
2020-12-15 |
5.8 |
CVE-2020-35470
MISC
MISC
MISC |
| envoyproxy — envoy |
Envoy before 1.16.1 mishandles dropped and truncated datagrams, as demonstrated by a segmentation fault for a UDP packet size larger than 1500. |
2020-12-15 |
5 |
CVE-2020-35471
MISC
MISC
MISC |
| epson — eps_tse_server_8_firmware |
Lack of an anti-CSRF token in the entire administrative interface in EPSON EPS TSE Server 8 (21.0.11) allows an unauthenticated attacker to force an administrator to execute external POST requests by visiting a malicious website. |
2020-12-16 |
6.8 |
CVE-2020-28931
MISC |
| ethereum — go_ethereum |
Go Ethereum, or “Geth”, is the official Golang implementation of the Ethereum protocol. In Geth before version 1.9.25 a denial-of-service vulnerability can make a LES server crash via malicious GetProofsV2 request from a connected LES client. This vulnerability only concerns users explicitly enabling les server; disabling les prevents the exploit. The vulnerability was patched in version 1.9.25. |
2020-12-11 |
4 |
CVE-2020-26264
MISC
MISC
MISC
CONFIRM |
| f5 — big-ip_access_policy_manager |
On BIG-IP versions 14.0.0-14.0.1 and 13.1.0-13.1.3.4, certain traffic pattern sent to a virtual server configured with an FTP profile can cause the FTP channel to break. |
2020-12-11 |
5 |
CVE-2020-5949
CONFIRM |
| f5 — big-ip_access_policy_manager |
On BIG-IP versions 16.0.0-16.0.0.1, 15.1.0-15.1.0.5, 14.1.0-14.1.2.7, 13.1.0-13.1.3.4, 12.1.0-12.1.5.2, and 11.6.1-11.6.5.2, undisclosed endpoints in iControl REST allow for a reflected XSS attack, which could lead to a complete compromise of the BIG-IP system if the victim user is granted the admin role. |
2020-12-11 |
6.8 |
CVE-2020-5948
CONFIRM |
| f5 — big-ip_advanced_firewall_manager |
In certain configurations on version 13.1.3.4, when a BIG-IP AFM HTTP security profile is applied to a virtual server and the BIG-IP system receives a request with specific characteristics, the connection is reset and the Traffic Management Microkernel (TMM) leaks memory. |
2020-12-11 |
5 |
CVE-2020-27713
CONFIRM |
| f5 — big-ip_advanced_firewall_manager |
On BIG-IP 14.1.0-14.1.2.6, undisclosed endpoints in iControl REST allow for a reflected XSS attack, which could lead to a complete compromise of the BIG-IP system if the victim user is granted the admin role. |
2020-12-11 |
5 |
CVE-2020-5950
MISC
CONFIRM |
| fasterxml — jackson-databind |
FasterXML jackson-databind 2.x before 2.9.10.8 mishandles the interaction between serialization gadgets and typing, related to org.apache.commons.dbcp2.datasources.PerUserPoolDataSource. |
2020-12-17 |
6.8 |
CVE-2020-35490
MISC
MISC |
| fasterxml — jackson-databind |
FasterXML jackson-databind 2.x before 2.9.10.8 mishandles the interaction between serialization gadgets and typing, related to org.apache.commons.dbcp2.datasources.SharedPoolDataSource. |
2020-12-17 |
6.8 |
CVE-2020-35491
MISC
MISC |
| fleetdm — fleet |
Fleet is an open source osquery manager. In Fleet before version 3.5.1, due to issues in Go’s standard library XML parsing, a valid SAML response may be mutated by an attacker to modify the trusted document. This can result in allowing unverified logins from a SAML IdP. Users that configure Fleet with SSO login may be vulnerable to this issue. This issue is patched in 3.5.1. The fix was made using https://github.com/mattermost/xml-roundtrip-validator If upgrade to 3.5.1 is not possible, users should disable SSO authentication in Fleet. |
2020-12-17 |
6.8 |
CVE-2020-26276
MISC
MISC
CONFIRM
MISC
MISC |
| flexmonster — pivot_table_&_charts |
Cross Site Scripting (XSS) vulnerability in Remote Report component under the Open menu in Flexmonster Pivot Table & Charts 2.7.17. |
2020-12-17 |
4.3 |
CVE-2020-20140
MISC |
| flexmonster — pivot_table_&_charts |
Cross Site Scripting (XSS) vulnerability in the Remote JSON component Under the Connect menu in Flexmonster Pivot Table & Charts 2.7.17. |
2020-12-17 |
4.3 |
CVE-2020-20139
MISC |
| flexmonster — pivot_table_&_charts |
Cross Site Scripting (XSS) vulnerability in the “To Remote CSV” component under “Open” Menu in Flexmonster Pivot Table & Charts 2.7.17. |
2020-12-17 |
4.3 |
CVE-2020-20142
MISC |
| flexmonster — pivot_table_&_charts |
Cross Site Scripting (XSS) vulnerability in the To OLAP (XMLA) component Under the Connect menu in Flexmonster Pivot Table & Charts 2.7.17. |
2020-12-17 |
4.3 |
CVE-2020-20141
MISC |
| fnet_project — fnet |
An issue was discovered in FNET through 4.6.4. The code for IPv6 fragment reassembly tries to access a previous fragment starting from a network incoming fragment that still doesn’t have a reference to the previous one (which supposedly resides in the reassembly list). When faced with an incoming fragment that belongs to a non-empty fragment list, IPv6 reassembly must check that there are no empty holes between the fragments: this leads to an uninitialized pointer dereference in _fnet_ip6_reassembly in fnet_ip6.c, and causes Denial-of-Service. |
2020-12-11 |
5 |
CVE-2020-17469
CONFIRM
MISC
MISC |
| fnet_project — fnet |
An issue was discovered in FNET through 4.6.4. The code that initializes the DNS client interface structure does not set sufficiently random transaction IDs (they are always set to 1 in _fnet_dns_poll in fnet_dns.c). This significantly simplifies DNS cache poisoning attacks. |
2020-12-11 |
5 |
CVE-2020-17470
CONFIRM
MISC
MISC |
| fnet_project — fnet |
An issue was discovered in FNET through 4.6.4. The code for processing the hop-by-hop header (in the IPv6 extension headers) doesn’t check for a valid length of an extension header, and therefore an out-of-bounds read can occur in _fnet_ip6_ext_header_handler_options in fnet_ip6.c, leading to Denial-of-Service. |
2020-12-11 |
5 |
CVE-2020-17468
CONFIRM
MISC
MISC |
| fnet_project — fnet |
An issue was discovered in FNET through 4.6.4. The code for processing resource records in mDNS queries doesn’t check for proper ” termination of the resource record name string, leading to an out-of-bounds read, and potentially causing information leak or Denial-or-Service. |
2020-12-11 |
6.4 |
CVE-2020-24383
MISC
MISC |
| fnet_project — fnet |
An issue was discovered in FNET through 4.6.4. The code for processing the hostname from an LLMNR request doesn’t check for ” termination. Therefore, the deduced length of the hostname doesn’t reflect the correct length of the actual data. This may lead to Information Disclosure in _fnet_llmnr_poll in fnet_llmnr.c during a response to a malicious request of the DNS class IN. |
2020-12-11 |
6.4 |
CVE-2020-17467
CONFIRM
MISC
MISC |
| foxitsoftware — foxit_reader |
An issue was discovered in Foxit Reader and PhantomPDF 10.1.0.37527 and earlier. There is a null pointer access/dereference while opening a crafted PDF file, leading the application to crash (denial of service). |
2020-12-15 |
4.3 |
CVE-2020-28203
MISC |
| frappe — frappe |
Frappe Framework 12 and 13 does not properly validate the HTTP method for the frappe.client API. |
2020-12-11 |
5 |
CVE-2020-35175
MISC
MISC |
| frappe — frappe |
In two-factor authentication, the system also sending 2fa secret key in response, which enables an intruder to breach the 2fa security. |
2020-12-11 |
5 |
CVE-2020-27508
MISC
MISC |
| gallagher — command_centre |
Type confusion in Gallagher Command Centre Server allows a remote attacker to crash the server or possibly cause remote code execution. This issue affects: Gallagher Command Centre 8.30 versions prior to 8.30.1236(MR1); 8.20 versions prior to 8.20.1166(MR3); 8.10 versions prior to 8.10.1211(MR5); version 8.00 and prior versions. |
2020-12-14 |
6.5 |
CVE-2020-16103
MISC |
| gallagher — command_centre |
Improper Authentication vulnerability in Gallagher Command Centre Server allows an unauthenticated remote attacker to create items with invalid configuration, potentially causing the server to crash and fail to restart. This issue affects: Gallagher Command Centre 8.30 versions prior to 8.30.1299(MR2); 8.20 versions prior to 8.20.1218(MR4); 8.10 versions prior to 8.10.1253(MR6); 8.00 versions prior to 8.00.1252(MR7); version 7.90 and prior versions. |
2020-12-14 |
6.4 |
CVE-2020-16102
MISC |
| gallagher — command_centre |
SQL Injection vulnerability in Enterprise Data Interface of Gallagher Command Centre allows a remote attacker with ‘Edit Enterprise Data Interfaces’ privilege to execute arbitrary SQL against a third party database if EDI is configured to import data from this database. This issue affects: Gallagher Command Centre 8.30 versions prior to 8.30.1236(MR1); 8.20 versions prior to 8.20.1166(MR3); 8.10 versions prior to 8.10.1211(MR5); 8.00 versions prior to 8.00.1228(MR6); version 7.90 and prior versions. |
2020-12-14 |
6.5 |
CVE-2020-16104
MISC |
| gehealthcare — 3.0t_signa_hdxt_firmware |
GE Healthcare Imaging and Ultrasound Products may allow specific credentials to be exposed during transport over the network. |
2020-12-14 |
5 |
CVE-2020-25175
MISC |
| gitlab — gitlab |
Information about the starred projects for private user profiles was exposed via the GraphQL API starting from 12.2 via the REST API. This affects GitLab >=12.2 to <13.4.7, >=13.5 to <13.5.5, and >=13.6 to <13.6.2. |
2020-12-11 |
4 |
CVE-2020-26415
CONFIRM
MISC |
| gitlab — gitlab |
Removed group members were able to use the To-Do functionality to retrieve updated information on confidential epics starting in GitLab EE 13.2 before 13.6.2. |
2020-12-11 |
4 |
CVE-2020-26412
CONFIRM
MISC |
| gitlab — gitlab |
Information disclosure via GraphQL in GitLab CE/EE 13.1 and later exposes private group and project membership. This affects versions >=13.6 to <13.6.2, >=13.5 to <13.5.5, and >=13.1 to <13.4.7. |
2020-12-11 |
5 |
CVE-2020-26417
CONFIRM
MISC |
| gitlab — gitlab |
An issue has been discovered in GitLab CE/EE affecting all versions starting from 13.4 before 13.6.2. Information disclosure via GraphQL results in user email being unexpectedly visible. |
2020-12-11 |
5 |
CVE-2020-26413
CONFIRM
MISC
MISC |
| gitlab — gitlab |
A limited information disclosure vulnerability exists in Gitlab CE/EE from >= 12.2 to <13.4.7, >=13.5 to <13.5.5, and >=13.6 to <13.6.2 that allows an attacker to view limited information in user’s private profile |
2020-12-11 |
5 |
CVE-2020-26408
CONFIRM
MISC
MISC |
| gitlab — gitlab |
A potential DOS vulnerability was discovered in all versions of Gitlab starting from 13.4.x (>=13.4 to <13.4.7, >=13.5 to <13.5.5, and >=13.6 to <13.6.2). Using a specific query name for a project search can cause statement timeouts that can lead to a potential DOS if abused. |
2020-12-11 |
4 |
CVE-2020-26411
CONFIRM
MISC |
| gitlab — gitlab |
A DOS vulnerability exists in Gitlab CE/EE >=10.3, <13.4.7,>=13.5, <13.5.5,>=13.6, <13.6.2 that allows an attacker to trigger uncontrolled resource by bypassing input validation in markdown fields. |
2020-12-11 |
4 |
CVE-2020-26409
CONFIRM
MISC
MISC |
| gitlab — gitlab |
An issue was discovered in Gitlab CE/EE versions >= 13.1 to <13.4.7, >= 13.5 to <13.5.5, and >= 13.6 to <13.6.2 allowed an unauthorized user to access the user list corresponding to a feature flag in a project. |
2020-12-11 |
4 |
CVE-2020-13357
CONFIRM
MISC
MISC |
| gjson_project — gjson |
GJSON before 1.6.4 allows attackers to cause a denial of service via crafted JSON. |
2020-12-15 |
5 |
CVE-2020-35380
MISC |
| gnome — glib |
** DISPUTED ** GNOME GLib before 2.65.3 has an integer overflow, that might lead to an out-of-bounds write, in g_option_group_add_entries. NOTE: the vendor’s position is “Realistically this is not a security issue. The standard pattern is for callers to provide a static list of option entries in a fixed number of calls to g_option_group_add_entries().” The researcher states that this pattern is undocumented. |
2020-12-14 |
4.6 |
CVE-2020-35457
MISC
MISC
MISC |
| google — android |
In destroyResources of ComposerClient.h, there is possible memory corruption due to a use after free. This could lead to local escalation of privilege with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-11Android ID: A-155769496 |
2020-12-15 |
4.6 |
CVE-2020-0484
MISC |
| google — android |
In openAssetFileListener of ContactsProvider2.java, there is a possible permission bypass due to an insecure default value. This could lead to local escalation of privilege to change contact data with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-11Android ID: A-150857116 |
2020-12-15 |
4.6 |
CVE-2020-0486
MISC |
| google — android |
In HalCamera::requestNewFrame of HalCamera.cpp, there is a possible use-after-free due to a race condition. This could lead to local escalation of privilege with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-11Android ID: A-169282240 |
2020-12-15 |
4.4 |
CVE-2020-0474
MISC |
| google — android |
In onCreate of HandleApiCalls.java, there is a possible permission bypass due to a confused deputy. This could lead to local escalation of privilege that allows an app to set or dismiss the alarm with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-11Android ID: A-150612638 |
2020-12-15 |
4.6 |
CVE-2020-27030
MISC |
| google — android |
In phNxpNciHal_send_ext_cmd of phNxpNciHal_ext.cc, there is a possible out of bounds write due to a missing bounds check. This could lead to local escalation of privilege in the NFC server with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-11Android ID: A-153731369 |
2020-12-15 |
4.6 |
CVE-2020-27036
MISC |
| google — android |
In areFunctionsSupported of UsbBackend.java, there is a possible access to tethering from a guest account due to a missing permission check. This could lead to local escalation of privilege with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-11Android ID: A-166125765 |
2020-12-15 |
4.6 |
CVE-2020-0485
MISC |
| google — android |
In getLockTaskLaunchMode of ActivityRecord.java, there is a possible way for any app to start in Lock Task Mode due to a permissions bypass. This could lead to local escalation of privilege with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-11Android ID: A-158833495 |
2020-12-15 |
4.6 |
CVE-2020-27052
MISC |
| google — android |
In restartWrite of Parcel.cpp, there is a possible memory corruption due to a use after free. This could lead to local escalation of privilege with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-11Android ID: A-157066561 |
2020-12-15 |
4.6 |
CVE-2020-27044
MISC |
| google — android |
In onFactoryReset of BluetoothManagerService.java, there is a missing permission check. This could lead to local escalation of privilege with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-11Android ID: A-159061926 |
2020-12-15 |
4.6 |
CVE-2020-27054
MISC |
| google — android |
In smp_br_state_machine_event of smp_br_main.cc, there is a possible out of bounds read due to a missing bounds check. This could lead to remote information disclosure triggered by a malformed Bluetooth packet, with no additional execution privileges needed. User interaction is not needed for exploitation. Bounds Sanitizer mitigates this in the default configuration.Product: AndroidVersions: Android-11Android ID: A-162327732 |
2020-12-15 |
5 |
CVE-2020-27024
MISC |
| google — android |
An issue was discovered in the GPS daemon on Samsung mobile devices with O(8.x), P(9.0), and Q(10.0) (non-Qualcomm chipsets) software. Attackers can obtain sensitive location information because the configuration file is incorrect. The Samsung ID is SVE-2020-18678 (December 2020). |
2020-12-18 |
5 |
CVE-2020-35552
MISC |
| google — android |
In DrmManagerService::~DrmManagerService() of DrmManagerService.cpp, there is a possible memory corruption due to a use after free. This could lead to local escalation of privilege with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-11Android ID: A-155647761 |
2020-12-15 |
4.6 |
CVE-2020-0483
MISC |
| google — android |
In xfrm6_tunnel_free_spi of net/ipv6/xfrm6_tunnel.c, there is a possible use after free due to improper locking. This could lead to local escalation of privilege with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-168043318 |
2020-12-15 |
4.6 |
CVE-2020-27066
MISC |
| google — android |
In isSubmittable and showWarningMessagesIfAppropriate of WifiConfigController.java and WifiConfigController2.java, there is a possible insecure WiFi configuration due to improper input validation. This could lead to remote information disclosure with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-11Android ID: A-161378819 |
2020-12-15 |
5 |
CVE-2020-27055
MISC |
| google — android |
In BitstreamFillCache of bitstream.cpp, there is a possible out of bounds read due to a heap buffer overflow. This could lead to remote information disclosure with no additional execution privileges needed. User interaction is needed for exploitation.Product: AndroidVersions: Android-11Android ID: A-154058264 |
2020-12-15 |
4.3 |
CVE-2020-0492
MISC |
| google — android |
In the l2tp subsystem, there is a possible use after free due to a race condition. This could lead to local escalation of privilege with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-152409173 |
2020-12-15 |
4.4 |
CVE-2020-27067
MISC |
| google — android |
In Parse_data of eas_mdls.c, there is a possible out of bounds write due to a missing bounds check. This could lead to remote code execution in the media extractor with no additional execution privileges needed. User interaction is needed for exploitation.Product: AndroidVersions: Android-11Android ID: A-151096540 |
2020-12-15 |
6.8 |
CVE-2020-0489
MISC |
| google — android |
In callUnchecked of DocumentsProvider.java, there is a possible permissions bypass due to a missing permission check. This could lead to local escalation of privilege allowing a caller to copy, move, or delete files accessible to DocumentsProvider with no additional execution privileges needed. User interaction is needed for exploitation.Product: AndroidVersions: Android-11Android ID: A-157320716 |
2020-12-15 |
6.8 |
CVE-2020-0480
MISC |
| google — android |
In RW_SendRawFrame of rw_main.cc, there is a possible out of bounds write due to a missing bounds check. This could lead to local escalation of privilege with no additional execution privileges needed. User interaction is needed for exploitation.Product: AndroidVersions: Android-11Android ID: A-157650117 |
2020-12-15 |
6.8 |
CVE-2020-27048
MISC |
| google — android |
In rw_t3t_send_raw_frame of rw_t3t.cc, there is a possible out of bounds write due to a missing bounds check. This could lead to local escalation of privilege with no additional execution privileges needed. User interaction is needed for exploitation.Product: AndroidVersions: Android-11Android ID: A-157649467 |
2020-12-15 |
6.8 |
CVE-2020-27049
MISC |
| google — android |
In rw_i93_send_cmd_write_multi_blocks of rw_i93.cc, there is a possible out of bounds write due to a heap buffer overflow. This could lead to local escalation of privilege with no additional execution privileges needed. User interaction is needed for exploitation.Product: AndroidVersions: Android-11Android ID: A-157650365 |
2020-12-15 |
6.8 |
CVE-2020-27050
MISC |
| google — android |
In NFA_RwI93WriteMultipleBlocks of nfa_rw_api.cc, there is a possible out of bounds write due to an integer overflow. This could lead to local escalation of privilege with no additional execution privileges needed. User interaction is needed for exploitation.Product: AndroidVersions: Android-11Android ID: A-157650338 |
2020-12-15 |
6.8 |
CVE-2020-27051
MISC |
| google — android |
In callUnchecked of DocumentsProvider.java, there is a possible permissions bypass. This could lead to local escalation of privilege allowing a malicious app to access files available to the DocumentProvider without user permission, with no additional execution privileges needed. User interaction is needed for exploitation.Product: AndroidVersions: Android-11Android ID: A-157294893 |
2020-12-15 |
6.8 |
CVE-2020-0479
MISC |
| google — android |
In ce_t4t_update_binary of ce_t4t.cc, there is a possible out of bounds read due to a missing bounds check. This could lead to local information disclosure with no additional execution privileges needed. User interaction is needed for exploitation.Product: AndroidVersions: Android-11Android ID: A-157649298 |
2020-12-15 |
4.3 |
CVE-2020-27047
MISC |
| google — android |
In process of C2SoftVorbisDec.cpp, there is a possible resource exhaustion due to a memory leak. This could lead to remote denial of service with no additional execution privileges needed. User interaction is needed for exploitation.Product: AndroidVersions: Android-11Android ID: A-154302257 |
2020-12-15 |
4.3 |
CVE-2020-27038
MISC |
| google — android |
In TextView of TextView.java, there is a possible app hang due to improper input validation. This could lead to remote denial of service with no additional execution privileges needed. User interaction is needed for exploitation.Product: AndroidVersions: Android-11Android ID: A-140218875 |
2020-12-15 |
4.3 |
CVE-2020-27029
MISC |
| google — android |
During boot, the device unlock interface behaves differently depending on if a fingerprint registered to the device is present. This could lead to local information disclosure with no additional execution privileges needed. User interaction is needed for exploitation.Product: AndroidVersions: Android-11Android ID: A-79776455 |
2020-12-15 |
4.3 |
CVE-2020-27026
MISC |
| google — android |
In FLAC__bitreader_read_rice_signed_block of bitreader.c, there is a possible out of bounds read due to a heap buffer overflow. This could lead to remote information disclosure with no additional execution privileges needed. User interaction is needed for exploitation.Product: AndroidVersions: Android-11Android ID: A-156076070 |
2020-12-15 |
4.3 |
CVE-2020-0499
MISC |
| google — android |
In decode_packed_entry_number of codebook.c, there is a possible out of bounds read due to a heap buffer overflow. This could lead to remote information disclosure with no additional execution privileges needed. User interaction is needed for exploitation.Product: AndroidVersions: Android-11Android ID: A-160633884 |
2020-12-15 |
4.3 |
CVE-2020-0498
MISC |
| google — android |
In createNameCredentialDialog of CertInstaller.java, there exists the possibility of improperly installed certificates due to a logic error. This could lead to remote information disclosure with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-11Android ID: A-163413737 |
2020-12-14 |
5 |
CVE-2020-0460
MISC |
| google — android |
In sdp_server_handle_client_req of sdp_server.cc, there is a possible out of bounds read due to a missing bounds check. This could lead to remote information disclosure from the bluetooth server with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-10 Android-11 Android-8.0 Android-8.1 Android-9Android ID: A-169342531 |
2020-12-14 |
5 |
CVE-2020-0463
MISC |
| google — android |
In ih264d_parse_ave of ih264d_sei.c, there is a possible out of bounds read due to a heap buffer overflow. This could lead to remote information disclosure with no additional execution privileges needed. User interaction is needed for exploitation.Product: AndroidVersions: Android-11Android ID: A-152895390 |
2020-12-15 |
4.3 |
CVE-2020-0494
MISC |
| google — android |
In extend_frame_lowbd of restoration.c, there is a possible out of bounds write due to a missing bounds check. This could lead to local escalation of privilege with no additional execution privileges needed. User interaction is needed for exploitation.Product: AndroidVersions: Android-11Android ID: A-150780418 |
2020-12-15 |
6.8 |
CVE-2020-0478
MISC |
| google — android |
In readBlock of MatroskaExtractor.cpp, there is a possible denial of service due to resource exhaustion. This could lead to remote denial of service with no additional execution privileges needed. User interaction is needed for exploitation.Product: AndroidVersions: Android-11Android ID: A-156819528 |
2020-12-15 |
4.3 |
CVE-2020-0491
MISC |
| google — android |
In floor1_info_unpack of floor1.c, there is a possible out of bounds read due to a missing bounds check. This could lead to remote information disclosure with no additional execution privileges needed. User interaction is needed for exploitation.Product: AndroidVersions: Android-11Android ID: A-155560008 |
2020-12-15 |
4.3 |
CVE-2020-0490
MISC |
| google — android |
In ihevc_inter_pred_chroma_copy_ssse3 of ihevc_inter_pred_filters_ssse3_intr.c, there is a possible information disclosure due to uninitialized data. This could lead to remote information disclosure with no additional execution privileges needed. User interaction is needed for exploitation.Product: AndroidVersions: Android-11Android ID: A-158484516 |
2020-12-15 |
4.3 |
CVE-2020-0488
MISC |
| google — android |
In createInputConsumer of WindowManagerService.java, there is a possible way to block and intercept input events due to a missing permission check. This could lead to local escalation of privilege with no additional execution privileges needed. User interaction is needed for exploitation.Product: AndroidVersions: Android-11Android ID: A-162324374 |
2020-12-15 |
6.8 |
CVE-2020-0475
MISC |
| google — android |
In read_metadata_vorbiscomment_ of stream_decoder.c, there is possible memory exhaustion due to a memory leak. This could lead to remote denial of service with no additional execution privileges needed. User interaction is needed for exploitation.Product: AndroidVersions: Android-11Android ID: A-124775381 |
2020-12-15 |
4.3 |
CVE-2020-0487
MISC |
| google — android |
In extend_frame_highbd of restoration.c, there is a possible out of bounds write due to a heap buffer overflow. This could lead to remote information disclosure with no additional execution privileges needed. User interaction is needed for exploitation.Product: AndroidVersions: Android-11 Android-10Android ID: A-166268541 |
2020-12-14 |
4.3 |
CVE-2020-0470
MISC |
| google — android |
In writeBurstBufferBytes of SPDIFEncoder.cpp, there is a possible out of bounds read due to an incorrect bounds check. This could lead to local information disclosure with no clear exfiltration path, with no additional execution privileges needed. User interaction is needed for exploitation.Product: AndroidVersions: Android-11Android ID: A-145262423 |
2020-12-15 |
4.3 |
CVE-2020-0244
MISC |
| google — android |
In CE_SendRawFrame of ce_main.cc, there is a possible out of bounds write due to a heap buffer overflow. This could lead to local escalation of privilege with no additional execution privileges needed. User interaction is needed for exploitation.Product: AndroidVersions: Android-11Android ID: A-157649398 |
2020-12-15 |
6.8 |
CVE-2020-27045
MISC |
| google — asylo |
An arbitrary memory overwrite vulnerability in Asylo versions up to 0.6.0 allow an attacker to make an Ecall_restore function call to reallocate untrusted code and overwrite sections of the Enclave memory address. We recommend updating your library. |
2020-12-15 |
4.6 |
CVE-2020-8935
CONFIRM |
| haxx — curl |
curl 7.21.0 to and including 7.73.0 is vulnerable to uncontrolled recursion due to a stack overflow issue in FTP wildcard match parsing. |
2020-12-14 |
5 |
CVE-2020-8285
MISC
MISC
MISC
MLIST
FEDORA
FEDORA |
| haxx — curl |
curl 7.62.0 through 7.70.0 is vulnerable to an information disclosure vulnerability that can lead to a partial password being leaked over the network and to the DNS server(s). |
2020-12-14 |
5 |
CVE-2020-8169
MISC
MISC |
| haxx — curl |
curl 7.41.0 through 7.73.0 is vulnerable to an improper check for certificate revocation due to insufficient verification of the OCSP response. |
2020-12-14 |
5 |
CVE-2020-8286
MISC
MISC
MLIST
FEDORA
FEDORA |
| haxx — curl |
A malicious server can use the FTP PASV response to trick curl 7.73.0 and earlier into connecting back to a given IP address and port, and this way potentially make curl extract information about services that are otherwise private and not disclosed, for example doing port scanning and service banner extractions. |
2020-12-14 |
4.3 |
CVE-2020-8284
MISC
MISC
MLIST
FEDORA
FEDORA |
| haxx — curl |
curl 7.20.0 through 7.70.0 is vulnerable to improper restriction of names for files and other resources that can lead too overwriting a local file when the -J flag is used. |
2020-12-14 |
4.6 |
CVE-2020-8177
MISC
MISC |
| haxx — libcurl |
Due to use of a dangling pointer, libcurl 7.29.0 through 7.71.1 can use the wrong connection when sending data. |
2020-12-14 |
5 |
CVE-2020-8231
MISC
MISC |
| i18n_project — i18n |
This affects the package i18n before 2.1.15. Vulnerability arises out of insufficient handling of erroneous language tags in src/i18n/Concrete/TextLocalizer.cs and src/i18n/LocalizedApplication.cs. |
2020-12-11 |
5 |
CVE-2020-7791
MISC
MISC
MISC |
| ibm — financial_transaction_manager_for_multiplatform |
IBM Financial Transaction Manager for SWIFT Services for Multiplatforms 3.2.4 returns the product version and release information on the login dialog. This information could be used in further attacks against the system. |
2020-12-16 |
5 |
CVE-2020-4908
XF
CONFIRM |
| ibm — financial_transaction_manager_for_multiplatform |
IBM Financial Transaction Manager for SWIFT Services for Multiplatforms 3.2.4 could allow a remote attacker to obtain sensitive information when a detailed technical error message is returned in the browser. This information could be used in further attacks against the system. |
2020-12-16 |
5 |
CVE-2020-4907
XF
CONFIRM |
| ibm — financial_transaction_manager_for_multiplatform |
IBM Financial Transaction Manager for SWIFT Services for Multiplatforms 3.2.4 could allow an remote attacker to obtain sensitive information, caused by a man in the middle attack. By SSL striping, an attacker could exploit this vulnerability to obtain sensitive information. |
2020-12-16 |
4.3 |
CVE-2020-4905
XF
CONFIRM |
| ibm — financial_transaction_manager_for_multiplatform |
IBM Financial Transaction Manager for SWIFT Services for Multiplatforms 3.2.4 is vulnerable to cross-site request forgery which could allow an attacker to execute malicious and unauthorized actions transmitted from a user that the website trusts. |
2020-12-16 |
4.3 |
CVE-2020-4904
XF
CONFIRM |
| ibm — security_key_lifecycle_manager |
IBM Security Key Lifecycle Manager 3.0.1 and 4.0 could allow a remote attacker to obtain sensitive information when a detailed technical error message is returned in the browser. This information could be used in further attacks against the system. IBM X-Force ID: 190290. |
2020-12-17 |
4 |
CVE-2020-4846
XF
CONFIRM |
| ibm — sterling_b2b_integrator |
IBM Sterling B2B Integrator 5.2.0.0 through 6.0.3.2 Standard Edition is vulnerable to cross-site scripting. This vulnerability allows users to embed arbitrary JavaScript code in the Web UI thus altering the intended functionality potentially leading to credentials disclosure within a trusted session. IBM X-Force ID: 186094. |
2020-12-16 |
4.3 |
CVE-2020-4657
XF
CONFIRM |
| ibm — sterling_file_gateway |
IBM Sterling File Gateway 2.2.0.0 through 6.0.3.2 is vulnerable to cross-site scripting. This vulnerability allows users to embed arbitrary JavaScript code in the Web UI thus altering the intended functionality potentially leading to credentials disclosure within a trusted session. IBM X-Force ID: 186095. |
2020-12-16 |
4.3 |
CVE-2020-4658
XF
CONFIRM |
| ibm — tivoli_netcool/impact |
IBM Tivoli Netcool Impact 7.1.0.0 through 7.1.0.19 Interim Fix 7 could allow a remote attacker to bypass security restrictions, caused by a reverse tabnabbing flaw. An attacker could exploit this vulnerability and redirect a vitcim to a phishing site. IBM X-Force ID: 190294. |
2020-12-15 |
5.8 |
CVE-2020-4849
XF
CONFIRM |
| icinga — icinga |
Icinga 2 v2.8.0 through v2.11.7 and v2.12.2 has an issue where revoked certificates due for renewal will automatically be renewed, ignoring the CRL. This issue is fixed in Icinga 2 v2.11.8 and v2.12.3. |
2020-12-15 |
6.4 |
CVE-2020-29663
MISC
MISC |
| igniterealtime — openfire |
Ignite Realtime Openfire 4.6.0 has plugins/clientcontrol/spark-form.jsp Reflective XSS. |
2020-12-12 |
4.3 |
CVE-2020-35200
MISC |
| ini_project — ini |
This affects the package ini before 1.3.6. If an attacker submits a malicious INI file to an application that parses it with ini.parse, they will pollute the prototype on the application. This can be exploited further depending on the context. |
2020-12-11 |
6.8 |
CVE-2020-7788
MISC
MISC |
| irfanview — irfanview |
irfanView 4.56 contains an error processing parsing files of type .pcx. Which leads to out-of-bounds writing at i_view32+0xdb60. |
2020-12-16 |
5 |
CVE-2020-35133
MISC
MISC |
| jasper_project — jasper |
There’s a flaw in jasper’s jpc encoder in versions prior to 2.0.23. Crafted input provided to jasper by an attacker could cause an arbitrary out-of-bounds write. This could potentially affect data confidentiality, integrity, or application availability. |
2020-12-11 |
6.8 |
CVE-2020-27828
MISC
MISC
FEDORA
FEDORA |
| keysight — database_connector |
An issue was discovered in the Keysight Database Connector plugin before 1.5.0 for Confluence. A malicious user could insert arbitrary JavaScript into saved macro parameters that would execute when a user viewed a page with that instance of the macro. |
2020-12-15 |
6.8 |
CVE-2020-35121
MISC |
| keysight — keysight_database_connector |
An issue was discovered in the Keysight Database Connector plugin before 1.5.0 for Confluence. A malicious user could bypass the access controls for using a saved database connection profile to submit arbitrary SQL against a saved database connection. |
2020-12-15 |
4 |
CVE-2020-35122
MISC |
| linux — linux_kernel |
A use-after-free flaw was found in kernel/trace/ring_buffer.c in Linux kernel (before 5.10-rc1). There was a race problem in trace_open and resize of cpu buffer running parallely on different cpus, may cause a denial of service problem (DOS). This flaw could even allow a local attacker with special user privilege to a kernel information leak threat. |
2020-12-11 |
5.4 |
CVE-2020-27825
MISC |
| linuxfoundation — spinnaker |
Nolan Ray from Apple Information Security identified a security vulnerability in Spinnaker, all versions prior to version 1.23.4, 1.22.4 or 1.21.5. The vulnerability exists within the handling of SpEL expressions that allows an attacker to read and write arbitrary files within the orca container via authenticated HTTP POST requests. |
2020-12-11 |
6.5 |
CVE-2020-9301
CONFIRM |
| mediawiki — mediawiki |
MediaWiki before 1.35.1 allows XSS via BlockLogFormatter.php. Language::translateBlockExpiry itself does not escape in all code paths. For example, the return of Language::userTimeAndDate is is always unsafe for HTML in a month value. This affects MediaWiki 1.12.0 and later. |
2020-12-18 |
4.3 |
CVE-2020-35479
MISC
MISC
DEBIAN |
| mediawiki — mediawiki |
In MediaWiki before 1.35.1, the combination of Html::rawElement and Message::text leads to XSS because the definition of MediaWiki:recentchanges-legend-watchlistexpiry can be changed onwiki so that the output is raw HTML. |
2020-12-18 |
4.3 |
CVE-2020-35474
MISC
MISC |
| mediawiki — mediawiki |
MediaWiki before 1.35.1 allows XSS via BlockLogFormatter.php. MediaWiki:blanknamespace potentially can be output as raw HTML with SCRIPT tags via LogFormatter::makePageLink(). This affects MediaWiki 1.33.0 and later. |
2020-12-18 |
4.3 |
CVE-2020-35478
MISC
MISC |
| medtronic — mycarelink_smart_model_25000_firmware |
Medtronic MyCareLink Smart 25000 all versions contain an authentication protocol vuln where the method used to auth between MCL Smart Patient Reader and MyCareLink Smart mobile app is vulnerable to bypass. This vuln allows attacker to use other mobile device or malicious app on smartphone to auth to the patient’s Smart Reader, fools the device into thinking its communicating with the actual smart phone application when executed in range of Bluetooth. |
2020-12-14 |
5.8 |
CVE-2020-25183
MISC |
| microfocus — filr |
Unauthorized disclosure of sensitive information vulnerability in Micro Focus Filr product. Affecting all 3.x and 4.x versions. The vulnerability could be exploited to disclose unauthorized sensitive information. |
2020-12-11 |
4 |
CVE-2020-25838
CONFIRM |
| mitel — micollab |
The SAS portal of Mitel MiCollab before 9.2 could allow an attacker to access user credentials due to improper input validation, aka SQL Injection. |
2020-12-18 |
6.5 |
CVE-2020-25608
MISC |
| mitel — micollab |
The AWV component of Mitel MiCollab before 9.2 could allow an attacker to gain access to a web conference due to insufficient access control for conference codes. |
2020-12-18 |
5 |
CVE-2020-25610
MISC |
| mitel — micollab |
The NuPoint Messenger of Mitel MiCollab before 9.2 could allow an attacker with escalated privilege to access user files due to insufficient access control. Successful exploit could potentially allow an attacker to gain access to sensitive information. |
2020-12-18 |
4 |
CVE-2020-25612
MISC |
| mitel — micollab |
The AWV portal of Mitel MiCollab before 9.2 could allow an attacker to gain access to conference information by sending arbitrary code due to improper input validation, aka XSS. Successful exploitation could allow an attacker to view user conference information. |
2020-12-18 |
4.3 |
CVE-2020-25611
MISC |
| mitel — micollab |
The AWV component of Mitel MiCollab before 9.2 could allow an attacker to view system information by sending arbitrary code due to improper input validation, aka XSS. |
2020-12-18 |
4.3 |
CVE-2020-25606
MISC |
| mpxj — mpxj |
common/InputStreamHelper.java in Packwood MPXJ before 8.3.5 allows directory traversal in the zip stream handler flow, leading to the writing of files to arbitrary locations. |
2020-12-14 |
5 |
CVE-2020-35460
MISC
MISC |
| mquery_project — mquery |
lib/utils.js in mquery before 3.2.3 allows a pollution attack because a special property (e.g., __proto__) can be copied during a merge or clone operation. |
2020-12-11 |
5 |
CVE-2020-35149
MISC |
| necplatforms — aterm_sa3500g_firmware |
Aterm SA3500G firmware versions prior to Ver. 3.5.9 allows an attacker on the adjacent network to send a specially crafted request to a specific URL, which may result in an arbitrary command execution. |
2020-12-14 |
5.8 |
CVE-2020-5635
MISC
MISC
MISC |
| necplatforms — aterm_sa3500g_firmware |
Aterm SA3500G firmware versions prior to Ver. 3.5.9 allows an attacker with an administrative privilege to send a specially crafted request to a specific URL, which may result in an arbitrary command execution. |
2020-12-14 |
5.2 |
CVE-2020-5636
MISC
MISC
MISC |
| necplatforms — aterm_sa3500g_firmware |
Improper validation of integrity check value vulnerability in Aterm SA3500G firmware versions prior to Ver. 3.5.9 allows an attacker with an administrative privilege to execute a malicious program. |
2020-12-14 |
5.2 |
CVE-2020-5637
MISC
MISC
MISC |
| node-notifier_project — node-notifier |
This affects the package node-notifier before 9.0.0. It allows an attacker to run arbitrary commands on Linux machines due to the options params not being sanitised when being passed an array. |
2020-12-11 |
6.8 |
CVE-2020-7789
MISC
MISC
MISC |
| openasset — digital_asset_management |
OpenAsset Digital Asset Management (DAM) through 12.0.19 does not correctly sanitize user supplied input in multiple parameters and endpoints, allowing for reflected cross-site scripting attacks. |
2020-12-14 |
4.3 |
CVE-2020-28859
MISC
MISC |
| openasset — digital_asset_management |
OpenAsset Digital Asset Management (DAM) 12.0.19 and earlier failed to implement access controls on /Stream/ProjectsCSV endpoint, allowing unauthenticated attackers to gain access to potentially sensitive project information stored by the application. |
2020-12-14 |
5 |
CVE-2020-28861
MISC
MISC
FULLDISC
MISC |
| openasset — digital_asset_management |
OpenAsset Digital Asset Management (DAM) through 12.0.19 does not correctly determine the HTTP request’s originating IP address, allowing attackers to spoof it using X-Forwarded-For in the header, by supplying localhost address such as 127.0.0.1, effectively bypassing all IP address based access controls. |
2020-12-14 |
5 |
CVE-2020-28856
MISC
MISC
FULLDISC
MISC |
| openasset — digital_asset_management |
OpenAsset Digital Asset Management (DAM) through 12.0.19, does not correctly sanitize user supplied input in multiple parameters and endpoints, allowing for stored cross-site scripting attacks. |
2020-12-14 |
4.3 |
CVE-2020-28857
MISC
MISC
FULLDISC
MISC |
| openasset — digital_asset_management |
OpenAsset Digital Asset Management (DAM) through 12.0.19 does not correctly verify whether a request made to the application was intentionally made by the user, allowing for cross-site request forgery attacks on all user functions. |
2020-12-14 |
6.8 |
CVE-2020-28858
MISC
MISC
FULLDISC
MISC |
| openasset — digital_asset_management |
OpenAssetDigital Asset Management (DAM) through 12.0.19 does not correctly sanitize user supplied input, incorporating it into its SQL queries, allowing for authenticated blind SQL injection. |
2020-12-14 |
6.5 |
CVE-2020-28860
MISC
MISC
FULLDISC
MISC |
| opener_project — opener |
A denial-of-service vulnerability exists in the Ethernet/IP server functionality of the EIP Stack Group OpENer 2.3 and development commit 8c73bf3. A large number of network requests in a small span of time can cause the running program to stop. An attacker can send a sequence of requests to trigger this vulnerability. |
2020-12-11 |
5 |
CVE-2020-13530
CONFIRM |
| p11-kit_project — p11-kit |
An issue was discovered in p11-kit 0.21.1 through 0.23.21. Multiple integer overflows have been discovered in the array allocations in the p11-kit library and the p11-kit list command, where overflow checks are missing before calling realloc or calloc. |
2020-12-16 |
5 |
CVE-2020-29361
MISC
MISC |
| pega — pega_platform |
Pega Platform through 8.4.x is affected by Cross Site Scripting (XSS) via the ConnectionID parameter, as demonstrated by a pyActivity=Data-TRACERSettings.pzStartTracerSession request to a PRAuth URI. |
2020-12-15 |
4.3 |
CVE-2020-23957
MISC |
| pixar — openusd |
An out of bounds memory corruption vulnerability exists in the way Pixar OpenUSD 20.05 reconstructs paths from binary USD files. A specially crafted malformed file can trigger an out of bounds memory modification which can result in remote code execution. To trigger this vulnerability, victim needs to access an attacker-provided malformed file. |
2020-12-11 |
6.8 |
CVE-2020-13520
MISC |
| pluck-cms — pluck |
A file upload restriction bypass vulnerability in Pluck CMS before 4.7.13 allows an admin privileged user to gain access in the host through the “manage files” functionality, which may result in remote code execution. |
2020-12-16 |
6.5 |
CVE-2020-29607
MISC |
| polarisoffice — polaris_ml_report |
An issue was discovered in ML Report Program. There is a stack-based buffer overflow in function sub_41EAF0 at MLReportDeamon.exe. The function will call vsprintf without checking the length of strings in parameters given by attacker. And it finally leads to a stack-based buffer overflow via access to crafted web page. This issue affects: Infraware ML Report 2.19.312.0000. |
2020-12-16 |
6.8 |
CVE-2020-7837
MISC |
| redhat — keycloak |
A flaw was found in Keycloak before 13.0.0 where an external identity provider, after successful authentication, redirects to a Keycloak endpoint that accepts multiple invocations with the use of the same “state” parameter. This flaw allows a malicious user to perform replay attacks. |
2020-12-15 |
4 |
CVE-2020-14302
MISC |
| redhat — keycloak |
A flaw was found in Keycloak before 13.0.0, where it is possible to force the server to call out an unverified URL using the OIDC parameter request_uri. This flaw allows an attacker to use this parameter to execute a Server-side request forgery (SSRF) attack. |
2020-12-15 |
5 |
CVE-2020-10770
MISC |
| s-cart — s-cart |
The package s-cart/core before 4.4 are vulnerable to Cross-site Scripting (XSS) via the admin panel. |
2020-12-15 |
4.3 |
CVE-2020-28456
MISC
MISC
MISC
MISC |
| schneider-electric — bmep584040_firmware |
A CWE-754: Improper Check for Unusual or Exceptional Conditions vulnerability exists in Modicon M580, Modicon M340, Legacy Controllers Modicon Quantum & Modicon Premium (see security notifications for affected versions), that could cause denial of service when a specially crafted Read Physical Memory request over Modbus is sent to the controller. |
2020-12-11 |
5 |
CVE-2020-7537
CONFIRM |
| schneider-electric — bmep584040_firmware |
A CWE-754: Improper Check for Unusual or Exceptional Conditions vulnerability exists in Modicon M580, Modicon M340, Legacy Controllers Modicon Quantum & Modicon Premium (see security notifications for affected versions), that could cause denial of service when a specially crafted Read Physical Memory request over Modbus is sent to the controller. |
2020-12-11 |
5 |
CVE-2020-7543
CONFIRM |
| schneider-electric — bmep584040_firmware |
A CWE-754: Improper Check for Unusual or Exceptional Conditions vulnerability exists in Modicon M580, Modicon M340, Legacy Controllers Modicon Quantum & Modicon Premium (see security notifications for affected versions), that could cause denial of service when a specially crafted Read Physical Memory request over Modbus is sent to the controller. |
2020-12-11 |
5 |
CVE-2020-7542
CONFIRM |
| schneider-electric — bmxp341000_firmware |
A CWE-425: Direct Request (‘Forced Browsing’) vulnerability exists in the Web Server on Modicon M340, Legacy Offers Modicon Quantum and Modicon Premium and associated Communication Modules (see security notification for affected versions), that could cause disclosure of sensitive data when sending a specially crafted request to the controller over HTTP. |
2020-12-11 |
5 |
CVE-2020-7541
CONFIRM |
| schneider-electric — bmxp341000_firmware |
A CWE-754 Improper Check for Unusual or Exceptional Conditions vulnerability exists in the Web Server on Modicon M340, Legacy Offers Modicon Quantum and Modicon Premium and associated Communication Modules (see security notification for affected versions), that could cause a denial of service vulnerability when a specially crafted packet is sent to the controller over HTTP. |
2020-12-11 |
5 |
CVE-2020-7539
CONFIRM |
| schneider-electric — bmxp341000_firmware |
A CWE-754: Improper Check for Unusual or Exceptional Conditions vulnerability exists in the Web Server on Modicon M340, Legacy Offers Modicon Quantum and Modicon Premium and associated Communication Modules (see security notification for affected versions), that could cause denial of HTTP and FTP services when a series of specially crafted requests is sent to the controller over HTTP. |
2020-12-11 |
5 |
CVE-2020-7549
CONFIRM |
| schneider-electric — bmxp341000_firmware |
A CWE-22: Improper Limitation of a Pathname to a Restricted Directory (‘Path Traversal’ Vulnerability Type) vulnerability exists in the Web Server on Modicon M340, Legacy Offers Modicon Quantum and Modicon Premium and associated Communication Modules (see security notification for affected versions), that could cause disclosure of information when sending a specially crafted request to the controller over HTTP. |
2020-12-11 |
5 |
CVE-2020-7535
CONFIRM |
| schneider-electric — easergy_t300_firmware |
A CWE-311: Missing Encryption of Sensitive Data vulnerability exists in Easergy T300 (firmware 2.7 and older), that would allow an attacker to read network traffic over HTTP protocol. |
2020-12-11 |
5 |
CVE-2020-28216
MISC
CONFIRM |
| schneider-electric — easergy_t300_firmware |
A CWE-311: Missing Encryption of Sensitive Data vulnerability exists in Easergy T300 (firmware 2.7 and older), that would allow an attacker to read network traffic over HTTP protocol. |
2020-12-11 |
5 |
CVE-2020-28217
MISC
CONFIRM |
| schneider-electric — easergy_t300_firmware |
A CWE-1021: Improper Restriction of Rendered UI Layers or Frames vulnerability exists in Easergy T300 (firmware 2.7 and older), that would allow an attacker to trick a user into initiating an unintended action. |
2020-12-11 |
4.3 |
CVE-2020-28218
MISC
CONFIRM |
| schneider-electric — ecostruxure_control_expert |
A CWE-123: Write-what-where Condition vulnerability exists in EcoStruxure™ Control Expert (all versions) and Unity Pro (former name of EcoStruxure™ Control Expert) (all versions), that could cause a crash of the software or unexpected code execution when opening a malicious file in EcoStruxure™ Control Expert software. |
2020-12-11 |
6.8 |
CVE-2020-7560
CONFIRM |
| schneider-electric — modicon_m258_firmware |
A CWE-119: Improper Restriction of Operations within the Bounds of a Memory Buffer vulnerability exists in Modicon M258 Firmware (All versions prior to V5.0.4.11) and SoMachine/SoMachine Motion software (All versions), that could cause a buffer overflow when the length of a file transferred to the webserver is not verified. |
2020-12-11 |
5.2 |
CVE-2020-28220
CONFIRM |
| siemens — logo!_8_bm_firmware |
A vulnerability has been identified in LOGO! 8 BM (incl. SIPLUS variants) (All versions < V8.3). The implemented encryption for communication with affected devices is prone to replay attacks due to the usage of a static key. An attacker could change the password or change the configuration on any affected device if using prepared messages that were generated for another device. |
2020-12-14 |
5 |
CVE-2020-25229
CONFIRM |
| siemens — logo!_8_bm_firmware |
A vulnerability has been identified in LOGO! 8 BM (incl. SIPLUS variants) (All versions < V8.3). Due to the usage of an outdated cipher mode on port 10005/tcp, an attacker could extract the encryption key from a captured communication with the device. |
2020-12-14 |
5 |
CVE-2020-25230
CONFIRM |
| siemens — logo!_8_bm_firmware |
A vulnerability has been identified in LOGO! 8 BM (incl. SIPLUS variants) (All versions < V8.3). Due to the usage of an insecure random number generation function and a deprecated cryptographic function, an attacker could extract the key that is used when communicating with an affected device on port 8080/tcp. |
2020-12-14 |
5 |
CVE-2020-25232
CONFIRM |
| siemens — logo!_8_bm_firmware |
A vulnerability has been identified in LOGO! 8 BM (incl. SIPLUS variants) (All versions < V8.3). The password used for authentication for the LOGO! Website and the LOGO! Access Tool is sent in a recoverable format. An attacker with access to the network traffic could derive valid logins. |
2020-12-14 |
5 |
CVE-2020-25235
CONFIRM |
| siemens — sicam_a8000_cp-8000_firmware |
A vulnerability has been identified in SICAM A8000 CP-8000 (All versions < V16), SICAM A8000 CP-8021 (All versions < V16), SICAM A8000 CP-8022 (All versions < V16). A web server misconfiguration of the affected device can cause insecure ciphers usage by a user´s browser. An attacker in a privileged position could decrypt the communication and compromise confidentiality and integrity of the transmitted information. |
2020-12-14 |
4.9 |
CVE-2020-28396
CONFIRM |
| siemens — simatic_et_200sp_open_controller_firmware |
A vulnerability has been identified in SIMATIC ET 200SP Open Controller (incl. SIPLUS variants) (V20.8), SIMATIC S7-1500 Software Controller (V20.8). The web server of the affected products contains a vulnerability that could allow a remote attacker to trigger a denial-of-service condition by sending a specially crafted HTTP request. |
2020-12-14 |
5 |
CVE-2020-15796
CONFIRM |
| siemens — xhq |
A vulnerability has been identified in XHQ (All Versions < 6.1). The web interface could allow a Cross-Site Request Forgery (CSRF) attack if an unsuspecting user is tricked into accessing a malicious link. |
2020-12-14 |
6.8 |
CVE-2019-19289
CONFIRM |
| siemens — xhq |
A vulnerability has been identified in XHQ (All Versions < 6.1). The web interface could allow attackers to traverse through the file system of the server based by sending specially crafted packets over the network without authentication. |
2020-12-14 |
4 |
CVE-2019-19287
CONFIRM |
| siemens — xhq |
A vulnerability has been identified in XHQ (All Versions < 6.1). The web interface could allow SQL injection attacks if an attacker is able to modify content of particular web pages. |
2020-12-14 |
6.5 |
CVE-2019-19286
CONFIRM |
| siemens — xhq |
A vulnerability has been identified in XHQ (All Versions < 6.1). The application’s web server could expose non-sensitive information about the server’s architecture. This could allow an attacker to adapt further attacks to the version in place. |
2020-12-14 |
5 |
CVE-2019-19283
CONFIRM |
| siemens — xhq |
A vulnerability has been identified in XHQ (All Versions < 6.1). The web interface could allow Cross-Site Scripting (XSS) attacks if unsuspecting users are tricked into accessing a malicious link. |
2020-12-14 |
4.3 |
CVE-2019-19288
CONFIRM |
| smartystreets — liveaddressplugin.js |
A cross-Site Scripting (XSS) vulnerability in this.showInvalid and this.showInvalidCountry in SmartyStreets liveAddressPlugin.js 3.2 allows remote attackers to inject arbitrary web script or HTML via any address parameter (e.g., street or country). |
2020-12-11 |
4.3 |
CVE-2020-29455
MISC
MISC
MISC |
| solarwinds — n-central |
An issue was discovered in SolarWinds N-Central 12.3.0.670. The AdvancedScripts HTTP endpoint allows CSRF. |
2020-12-16 |
6.8 |
CVE-2020-25622
MISC
MISC
MISC |
| sonatype — nexus_repository_manager |
Sonatype Nexus Repository Manager 3.x before 3.29.0 allows a user with admin privileges to configure the system to gain access to content outside of NXRM via an XXE vulnerability. Fixed in version 3.29.0. |
2020-12-17 |
5.5 |
CVE-2020-29436
CONFIRM |
| spatie — browsershot |
This affects the package spatie/browsershot from 0.0.0. By specifying a URL in the file:// protocol an attacker is able to include arbitrary files in the resultant PDF. |
2020-12-11 |
5 |
CVE-2020-7790
MISC
MISC |
| stivasoft — phpjabbers_appointment_scheduler |
Multiple cross-site scripting (XSS) vulnerabilities exist in PHPJabbers Appointment Scheduler 2.3, in the index.php admin login webpage (with different request parameters), allows remote attackers to inject arbitrary web script or HTML. |
2020-12-15 |
4.3 |
CVE-2020-35416
MISC
MISC
MISC |
| themexa — secure_file_manager |
** UNSUPPORTED WHEN ASSIGNED ** vendor/elfinder/php/connector.minimal.php in the secure-file-manager plugin through 2.5 for WordPress loads elFinder code without proper access control. Thus, any authenticated user can run the elFinder upload command to achieve remote code execution. NOTE: This vulnerability only affects products that are no longer supported by the maintainer. |
2020-12-14 |
6.5 |
CVE-2020-35235
MISC
MISC |
| tibco — partnerexpress |
The REST API component of TIBCO Software Inc.’s TIBCO PartnerExpress contains a vulnerability that theoretically allows an unauthenticated attacker with network access to obtain an authenticated login URL for the affected system via a REST API. Affected releases are TIBCO Software Inc.’s TIBCO PartnerExpress: version 6.2.0. |
2020-12-15 |
6.4 |
CVE-2020-27147
CONFIRM
CONFIRM |
| tiki — tikiwiki_cms/groupware |
TikiWiki 21.2 allows templates to be edited without CSRF protection. This could allow an unauthenticated, remote attacker to conduct a cross-site request forgery (CSRF) attack and perform arbitrary actions on an affected system. The vulnerability is due to insufficient CSRF protections for the web-based management interface of the affected system. An attacker could exploit this vulnerability by persuading a user of the interface to follow a maliciously crafted link. A successful exploit could allow the attacker to perform arbitrary actions on an affected system with the privileges of the user. These action include allowing attackers to submit their own code through an authenticated user resulting in local file Inclusion. If an authenticated user who is able to edit TikiWiki templates visits an malicious website, template code can be edited. |
2020-12-11 |
6.8 |
CVE-2020-29254
MISC
MISC
MISC |
| ua-parser-js_project — ua-parser-js |
The package ua-parser-js before 0.7.23 are vulnerable to Regular Expression Denial of Service (ReDoS) in multiple regexes (see linked commit for more info). |
2020-12-11 |
5 |
CVE-2020-7793
MISC
MISC
MISC
MISC |
| ui — edgemax_edgepower_24v_firmware |
A security issue was found in EdgePower 24V/54V firmware v1.7.0 and earlier where, due to missing CSRF protections, an attacker would have been able to perform unauthorized remote code execution. |
2020-12-14 |
6.8 |
CVE-2020-8282
MISC |
| uip_project — uip |
An issue was discovered in uIP 1.0, as used in Contiki 3.0 and other products. When the Urgent flag is set in a TCP packet, and the stack is configured to ignore the urgent data, the stack attempts to use the value of the Urgent pointer bytes to separate the Urgent data from the normal data, by calculating the offset at which the normal data should be present in the global buffer. However, the length of this offset is not checked; therefore, for large values of the Urgent pointer bytes, the data pointer can point to memory that is way beyond the data buffer in uip_process in uip.c. |
2020-12-11 |
6.4 |
CVE-2020-17437
MISC
MISC |
| uip_project — uip |
The code that processes DNS responses in uIP through 1.0, as used in Contiki and Contiki-NG, does not check whether the number of responses specified in the DNS packet header corresponds to the response data available in the DNS packet, leading to an out-of-bounds read and Denial-of-Service in resolv.c. |
2020-12-11 |
6.4 |
CVE-2020-24334
MISC
MISC |
| uip_project — uip |
An issue was discovered in uIP 1.0, as used in Contiki 3.0 and other products. The code that parses incoming DNS packets does not validate that domain names present in the DNS responses have ” termination. This results in errors when calculating the offset of the pointer that jumps over domain name bytes in DNS response packets when a name lacks this termination, and eventually leads to dereferencing the pointer at an invalid/arbitrary address, within newdata() and parse_name() in resolv.c. |
2020-12-11 |
5 |
CVE-2020-17440
MISC
MISC |
| weseek — growi |
Directory traversal vulnerability in GROWI versions prior to v4.2.3 (v4.2 Series), GROWI versions prior to v4.1.12 (v4.1 Series), and GROWI v3 series and earlier GROWI versions prior to v4.2.3 (v4.2 Series), GROWI versions prior to v4.1.12 (v4.1 Series), and GROWI v3 series and earlier allows remote attackers to alter the data by uploading a specially crafted file. |
2020-12-16 |
5 |
CVE-2020-5683
MISC
MISC
MISC |
| weseek — growi |
Improper input validation in GROWI versions prior to v4.2.3 (v4.2 Series), GROWI versions prior to v4.1.12 (v4.1 Series), and GROWI v3 series and earlier GROWI versions prior to v4.2.3 (v4.2 Series), GROWI versions prior to v4.1.12 (v4.1 Series), and GROWI v3 series and earlier allows remote attackers to cause a denial of service via unspecified vectors. |
2020-12-16 |
5 |
CVE-2020-5682
MISC
MISC
MISC |
| westerndigital — dashboard |
Western Digital Dashboard before 3.2.2.9 allows DLL Hijacking that leads to compromise of the SYSTEM account. |
2020-12-12 |
6.9 |
CVE-2020-29654
CONFIRM |
| wireshark — wireshark |
Crash in USB HID protocol dissector and possibly other dissectors in Wireshark 3.4.0 and 3.2.0 to 3.2.8 allows denial of service via packet injection or crafted capture file. |
2020-12-11 |
5 |
CVE-2020-26421
CONFIRM
MISC
MISC |
| wireshark — wireshark |
Memory leak in Kafka protocol dissector in Wireshark 3.4.0 and 3.2.0 to 3.2.8 allows denial of service via packet injection or crafted capture file. |
2020-12-11 |
5 |
CVE-2020-26418
CONFIRM
MISC
MISC |
| wireshark — wireshark |
Memory leak in RTPS protocol dissector in Wireshark 3.4.0 and 3.2.0 to 3.2.8 allows denial of service via packet injection or crafted capture file. |
2020-12-11 |
5 |
CVE-2020-26420
CONFIRM
MISC
MISC |
| wireshark — wireshark |
Memory leak in the dissection engine in Wireshark 3.4.0 allows denial of service via packet injection or crafted capture file. |
2020-12-11 |
5 |
CVE-2020-26419
CONFIRM
MISC
MISC |
| wp-ecommerce — easy_wp_smtp |
The easy-wp-smtp plugin before 1.4.4 for WordPress allows Administrator account takeover, as exploited in the wild in December 2020. If an attacker can list the wp-content/plugins/easy-wp-smtp/ directory, then they can discover a log file (such as #_debug_log.txt) that contains all password-reset links. The attacker can request a reset of the Administrator password and then use a link found there. |
2020-12-14 |
5 |
CVE-2020-35234
MISC
MISC |
| x.org — x_server |
A flaw was found in xorg-x11-server before 1.20.10. A heap-buffer overflow in XkbSetDeviceInfo may lead to a privilege escalation vulnerability. The highest threat from this vulnerability is to data confidentiality and integrity as well as system availability. |
2020-12-15 |
4.6 |
CVE-2020-25712
MISC
MISC |
| xen — xen |
An issue was discovered in Xen through 4.14.x. A bounds check common to most operation time functions specific to FIFO event channels depends on the CPU observing consistent state. While the producer side uses appropriately ordered writes, the consumer side isn’t protected against re-ordered reads, and may hence end up de-referencing a NULL pointer. Malicious or buggy guest kernels can mount a Denial of Service (DoS) attack affecting the entire system. Only Arm systems may be vulnerable. Whether a system is vulnerable depends on the specific CPU. x86 systems are not vulnerable. |
2020-12-15 |
4.9 |
CVE-2020-29571
DEBIAN
MISC |
| xen — xen |
An issue was discovered in Xen through 4.14.x. Recording of the per-vCPU control block mapping maintained by Xen and that of pointers into the control block is reversed. The consumer assumes, seeing the former initialized, that the latter are also ready for use. Malicious or buggy guest kernels can mount a Denial of Service (DoS) attack affecting the entire system. |
2020-12-15 |
4.9 |
CVE-2020-29570
MLIST
DEBIAN
MISC |
| xen — xen |
An issue was discovered in Xen through 4.14.x. Some OSes (such as Linux, FreeBSD, and NetBSD) are processing watch events using a single thread. If the events are received faster than the thread is able to handle, they will get queued. As the queue is unbounded, a guest may be able to trigger an OOM in the backend. All systems with a FreeBSD, Linux, or NetBSD (any version) dom0 are vulnerable. |
2020-12-15 |
4.9 |
CVE-2020-29568
MISC |
| xen — xen |
An issue was discovered in Xen 4.6 through 4.14.x. When acting upon a guest XS_RESET_WATCHES request, not all tracking information is freed. A guest can cause unbounded memory usage in oxenstored. This can lead to a system-wide DoS. Only systems using the Ocaml Xenstored implementation are vulnerable. Systems using the C Xenstored implementation are not vulnerable. |
2020-12-15 |
4.9 |
CVE-2020-29485
DEBIAN
MISC |
| xen — xen |
An issue was discovered in Xen through 4.14.x. When a Xenstore watch fires, the xenstore client that registered the watch will receive a Xenstore message containing the path of the modified Xenstore entry that triggered the watch, and the tag that was specified when registering the watch. Any communication with xenstored is done via Xenstore messages, consisting of a message header and the payload. The payload length is limited to 4096 bytes. Any request to xenstored resulting in a response with a payload longer than 4096 bytes will result in an error. When registering a watch, the payload length limit applies to the combined length of the watched path and the specified tag. Because watches for a specific path are also triggered for all nodes below that path, the payload of a watch event message can be longer than the payload needed to register the watch. A malicious guest that registers a watch using a very large tag (i.e., with a registration operation payload length close to the 4096 byte limit) can cause the generation of watch events with a payload length larger than 4096 bytes, by writing to Xenstore entries below the watched path. This will result in an error condition in xenstored. This error can result in a NULL pointer dereference, leading to a crash of xenstored. A malicious guest administrator can cause xenstored to crash, leading to a denial of service. Following a xenstored crash, domains may continue to run, but management operations will be impossible. Only C xenstored is affected, oxenstored is not affected. |
2020-12-15 |
4.9 |
CVE-2020-29484
DEBIAN
MISC |
| xen — xen |
An issue was discovered in Xen through 4.14.x. Access rights of Xenstore nodes are per domid. Unfortunately, existing granted access rights are not removed when a domain is being destroyed. This means that a new domain created with the same domid will inherit the access rights to Xenstore nodes from the previous domain(s) with the same domid. Because all Xenstore entries of a guest below /local/domain/<domid> are being deleted by Xen tools when a guest is destroyed, only Xenstore entries of other guests still running are affected. For example, a newly created guest domain might be able to read sensitive information that had belonged to a previously existing guest domain. Both Xenstore implementations (C and Ocaml) are vulnerable. |
2020-12-15 |
4.6 |
CVE-2020-29481
MLIST
DEBIAN
MISC |
| xen — xen |
An issue was discovered in Xen through 4.14.x. A guest may access xenstore paths via absolute paths containing a full pathname, or via a relative path, which implicitly includes /local/domain/$DOMID for their own domain id. Management tools must access paths in guests’ namespaces, necessarily using absolute paths. oxenstored imposes a pathname limit that is applied solely to the relative or absolute path specified by the client. Therefore, a guest can create paths in its own namespace which are too long for management tools to access. Depending on the toolstack in use, a malicious guest administrator might cause some management tools and debugging operations to fail. For example, a guest administrator can cause “xenstore-ls -r” to fail. However, a guest administrator cannot prevent the host administrator from tearing down the domain. All systems using oxenstored are vulnerable. Building and using oxenstored is the default in the upstream Xen distribution, if the Ocaml compiler is available. Systems using C xenstored are not vulnerable. |
2020-12-15 |
4.9 |
CVE-2020-29482
DEBIAN
MISC |
| xen — xen |
An issue was discovered in Xen through 4.14.x. Xenstored and guests communicate via a shared memory page using a specific protocol. When a guest violates this protocol, xenstored will drop the connection to that guest. Unfortunately, this is done by just removing the guest from xenstored’s internal management, resulting in the same actions as if the guest had been destroyed, including sending an @releaseDomain event. @releaseDomain events do not say that the guest has been removed. All watchers of this event must look at the states of all guests to find the guest that has been removed. When an @releaseDomain is generated due to a domain xenstored protocol violation, because the guest is still running, the watchers will not react. Later, when the guest is actually destroyed, xenstored will no longer have it stored in its internal data base, so no further @releaseDomain event will be sent. This can lead to a zombie domain; memory mappings of that guest’s memory will not be removed, due to the missing event. This zombie domain will be cleaned up only after another domain is destroyed, as that will trigger another @releaseDomain event. If the device model of the guest that violated the Xenstore protocol is running in a stub-domain, a use-after-free case could happen in xenstored, after having removed the guest from its internal data base, possibly resulting in a crash of xenstored. A malicious guest can block resources of the host for a period after its own death. Guests with a stub domain device model can eventually crash xenstored, resulting in a more serious denial of service (the prevention of any further domain management operations). Only the C variant of Xenstore is affected; the Ocaml variant is not affected. Only HVM guests with a stubdom device model can cause a serious DoS. |
2020-12-15 |
4.9 |
CVE-2020-29483
DEBIAN
MISC |
| xen — xen |
An issue was discovered in Xen through 4.14.x. When they require assistance from the device model, x86 HVM guests must be temporarily de-scheduled. The device model will signal Xen when it has completed its operation, via an event channel, so that the relevant vCPU is rescheduled. If the device model were to signal Xen without having actually completed the operation, the de-schedule / re-schedule cycle would repeat. If, in addition, Xen is resignalled very quickly, the re-schedule may occur before the de-schedule was fully complete, triggering a shortcut. This potentially repeating process uses ordinary recursive function calls, and thus could result in a stack overflow. A malicious or buggy stubdomain serving a HVM guest can cause Xen to crash, resulting in a Denial of Service (DoS) to the entire host. Only x86 systems are affected. Arm systems are not affected. Only x86 stubdomains serving HVM guests can exploit the vulnerability. |
2020-12-15 |
4.9 |
CVE-2020-29566
DEBIAN
MISC |
| xen — xen |
An issue was discovered in Xen through 4.14.x. Nodes in xenstore have an ownership. In oxenstored, a owner could give a node away. However, node ownership has quota implications. Any guest can run another guest out of quota, or create an unbounded number of nodes owned by dom0, thus running xenstored out of memory A malicious guest administrator can cause a denial of service against a specific guest or against the whole host. All systems using oxenstored are vulnerable. Building and using oxenstored is the default in the upstream Xen distribution, if the Ocaml compiler is available. Systems using C xenstored are not vulnerable. |
2020-12-15 |
4.9 |
CVE-2020-29486
DEBIAN
MISC |
| xen — xen |
An issue was discovered in Xen 4.14.x. When moving IRQs between CPUs to distribute the load of IRQ handling, IRQ vectors are dynamically allocated and de-allocated on the relevant CPUs. De-allocation has to happen when certain constraints are met. If these conditions are not met when first checked, the checking CPU may send an interrupt to itself, in the expectation that this IRQ will be delivered only after the condition preventing the cleanup has cleared. For two specific IRQ vectors, this expectation was violated, resulting in a continuous stream of self-interrupts, which renders the CPU effectively unusable. A domain with a passed through PCI device can cause lockup of a physical CPU, resulting in a Denial of Service (DoS) to the entire host. Only x86 systems are vulnerable. Arm systems are not vulnerable. Only guests with physical PCI devices passed through to them can exploit the vulnerability. |
2020-12-15 |
4.9 |
CVE-2020-29567
MISC |
| xstream_project — xstream |
XStream is a Java library to serialize objects to XML and back again. In XStream before version 1.4.15, a Server-Side Forgery Request vulnerability can be activated when unmarshalling. The vulnerability may allow a remote attacker to request data from internal resources that are not publicly available only by manipulating the processed input stream. If you rely on XStream’s default blacklist of the Security Framework, you will have to use at least version 1.4.15. The reported vulnerability does not exist if running Java 15 or higher. No user is affected who followed the recommendation to setup XStream’s Security Framework with a whitelist! Anyone relying on XStream’s default blacklist can immediately switch to a whilelist for the allowed types to avoid the vulnerability. Users of XStream 1.4.14 or below who still want to use XStream default blacklist can use a workaround described in more detailed in the referenced advisories. |
2020-12-16 |
5 |
CVE-2020-26258
CONFIRM
MLIST
MISC |
| xstream_project — xstream |
XStream is a Java library to serialize objects to XML and back again. In XStream before version 1.4.15, is vulnerable to an Arbitrary File Deletion on the local host when unmarshalling. The vulnerability may allow a remote attacker to delete arbitrary know files on the host as log as the executing process has sufficient rights only by manipulating the processed input stream. If you rely on XStream’s default blacklist of the Security Framework, you will have to use at least version 1.4.15. The reported vulnerability does not exist running Java 15 or higher. No user is affected, who followed the recommendation to setup XStream’s Security Framework with a whitelist! Anyone relying on XStream’s default blacklist can immediately switch to a whilelist for the allowed types to avoid the vulnerability. Users of XStream 1.4.14 or below who still want to use XStream default blacklist can use a workaround described in more detailed in the referenced advisories. |
2020-12-16 |
6.4 |
CVE-2020-26259
CONFIRM
MLIST
MISC |
| zyxel — p1302-t10_v3_firmware |
Insecure direct object reference vulnerability in Zyxel’s P1302-T10 v3 with firmware version 2.00(ABBX.3) and earlier allows attackers to gain privileges and access certain admin pages. |
2020-12-14 |
5 |
CVE-2020-20183
CONFIRM |
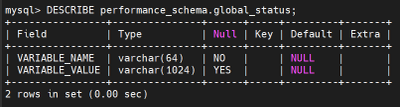
by Contributed | Dec 21, 2020 | Technology
This article is contributed. See the original author and article here.
Let’s be honest, performance tuning can be stressful. Luckily, MySQL natively provides a system schema called performance_schema to log all the server runtime information. Using performance_schema, you can do a lot of magic work to understand your server slowness. Further, leveraging the power of Azure Log Analytics, you can achieve even more!
This blog will illustrate how to automatically upload the output of performance_schema metrics to Azure Log Analytics and then use Log Analytics to generate different types of report for performance monitor/investigating purpose.
Azure DB for MySQL offers some metrics in Azure Portal that allows users to check the CPU, Memory, Connection activity etc. However, at times, this information may not be sufficient enough to understand why CPU utilization is going high. With the help of performance_schema, you will learn more about your MySQL server runtime status.
As many of you may already know, the following command in MySQL will return a long list of server metrics.
SHOW GLOBAL STATUS;
However, the challenges with the results of the earlier command is:
The value of each metric is an cumulative value since the server ran, which means all of those metric value will keep increasing until a restart is triggered. This makes it hard to determine the change that reflects the server running status;
There is no historical value to compare and draw any conclusions.
Therefore, it will be very handy if we can record historical data and data changes, it will allow us to perform data analysis to understand what changed and draw some conclusions. Luckily, Azure Log Analytics can help us achieve it!
Here is the idea:
Get an output of global status with change data captured
Get the data frequently
Automatically upload them in Azure Log Analytics workspace.
Use KUSTO query to generate report based on those metrics to fulfill different purposes.
Now let’s getting start!
Understand the data to collect for monitoring !!!
As mentioned, the metrics are returned by below SQL statement.
SHOW GLOBAL STATUS;
Since the returned value is not historical, the idea applied here is
Get the current output and save the data into a table
After some time, get another output and do the subtraction with the data stored in Step #1 based on metric name
After subtraction, update the value in Step #1 as the new benchmark for later use
The first step is to create a table used to storing the data, just like the sample below.
CREATE DATABASE globalstatus;
USE globalstatus;
/*
-- metric_name will be matched the VARIABLE_NAME in performance_schema.global_status
-- origin_metric_value will be copied directly from performance_schema.global_status when calling
*/
Create table my_global_status (
metric_name varchar(64) NOT NULL UNIQUE,
origin_metric_value varchar(1024)
);
The data type I select for each column is the same as the types defined in performance_schema global_status table to ensure consistency (Below is the default definition of the table global_status in performance_schema).

Then we will need insert the current output from global status into the table we created and use it to store historical data. As the output of global status comes from performance_schema, it can simply be achieved by the following SQL statement (Please note, the global status can be queried from information_schema as well. However, information_schema will be deprecated so you may want to consider using performance_schema instead.)
-- Copy metric value from performance_schema
INSERT INTO my_global_status (metric_name, origin_metric_value) SELECT * FROM performance_schema.global_status;
You can check if the insert is successful by querying both information_schema and your new created table to compare.
The next step is to extract the values changed. Before doing so, let’s evaluate this approach from performance perspective to ensure it doesnt impact the MySQL server performance negatively. We call the global status frequently (I would say per minute), and we will also need to update the historical metric value table at a similar frequency. To minimize the performance impact, it is better to avoid disk IO frequently. So let’s decide to calculate the metric value change on the fly and do not store it anywhere in the MySQL server.
Below is the SQL query I used to do so. The idea here is to use the currently queried output and subtract it from the stored values on the fly.
/*
-- To get the difference between current metric value and previous checked value
1, get the current value from performance_schema
2, get the current stored value in metric_value column
3, if metric_name matched VARIABLE_NAME from performance_schema, do the subtraction
4, insert the substracted value into the column of the table we created above [OPTIONAL]
*/
-- 3 get the subtraction
SELECT m.metric_name, g.VARIABLE_VALUE - m.origin_metric_value AS metric_value FROM
-- 1 get the current value from performance_schema
(SELECT VARIABLE_NAME, VARIABLE_VALUE FROM performance_schema.global_status) AS g,
-- 2 get the current stored value in metric_value column
(SELECT metric_name, origin_metric_value FROM globalstatus.my_global_status) AS m
WHERE m.metric_name = g.VARIABLE_NAME ;
Once the above is done, please don’t forget to update the historical table in the same time because it will be used as a benchmark for next call.
UPDATE globalstatus.my_global_status m, performance_schema.global_status g SET m.origin_metric_value = g.VARIABLE_VALUE Where m.metric_name = g.VARIABLE_NAME;
Get the data changes on the fly and persist the changes into a log file for analysis !!!
We now have the historical data collected, and we can get the data change, so then we will need to make it running automatically to save the change output.
The idea is
- Query the global_status every minute and get the data change at the same pace (you can define your own preferred frequency)
- Save the output into a log file
Let’s first work on how to generate the log file manually once. If this can be done, then an automation work can be down via multiple ways.
As explained above, we are trying to avoid disk IOs on your Azure DB for MySQL. Therefore I would suggest to save the output into an log file stored in an VM. The first thought came into my mind is the SQL clause like
SELECT ... INTO OUTFILE ...
Unfortunately, as a PaaS , this is not supported because the host machine cannot be accessed to save any output in a PaaS environment. However, mysql.exe utility provides the similar feature that works perfectly smooth with other file management commands in a terminal.
Taking an example of Linux, mysql.exe with -e option will allow users to execute SQL queries and get returns in a terminal, like below.
x_xiao2_bnu@xixia-ubt18-orcas:~$ mysql -h servername.mysql.database.azure.com -u user@servername -pXXXXXX -e "SHOW GLOBAL STATUS;"
mysql: [Warning] Using a password on the command line interface can be insecure.
+-----------------------------------------------+------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
| Variable_name | Value |
+-----------------------------------------------+------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
| Aborted_clients | 5301
| Aborted_connects | 2
| Binlog_cache_disk_use | 0
| Binlog_cache_use | 666
| Binlog_io_read | 24462
| Binlog_io_reads | 5
| Binlog_io_writes | 723
| Binlog_io_written | 1833438
...
And it also allows users to save the output into a preferred file directory when querying at the same time:
x_xiao2_bnu@xixia-ubt18-orcas:~$ mysql -h shawnx-db.mysql.database.azure.com -u x_xiao2_bnu@shawnx-db -pXXXXXXXX -e "SELECT * FROM information_schema.global_status; " >> /home/x_xiao2_bnu/mysql_shawn_status/innodb_status.log
Please note that the “>>” used here means that the output will be appended in the log, and if not exists, will create one. In contrast, “>” means that create a new file and overwrite the exists one. Since we will constantly get the output, we should use “>>” here to append each historical metric value in the log. Using the same approach, you can capture the data changes in a log file using the command below:
x_xiao2_bnu@xixia-ubt18-orcas:~$ mysql
-h shawnx-db.mysql.database.azure.com
-u x_xiao2_bnu@shawnx-db
-pXXXXXXXXX
-e "
USE globalstatus;SELECT m.metric_name, g.VARIABLE_VALUE - m.origin_metric_value AS metric_value FROM (SELECT VARIABLE_NAME, VARIABLE_VALUE FROM performance_schema.global_status) AS g, (SELECT metric_name, origin_metric_value FROM globalstatus.my_global_status) AS m WHERE m.metric_name = g.VARIABLE_NAME ; UPDATE globalstatus.my_global_status m, performance_schema.global_status g SET m.origin_metric_value = g.VARIABLE_VALUE Where m.metric_name = g.VARIABLE_NAME;" >> /home/x_xiao2_bnu/mysql_shawn_status/mysql_global_status.log
Now the problem is that, though an output of the metric value can be logged, the generated file contains plain metric value change. To make the metric value analyzable, we should add timestamp for each called metrics.
Since the returned output have many rows (378 actually), to avoid confusions with rows appended after each execution, I decided to insert a timestamp at the beginning of each row as a prefix and the timestamp should be the time when fetching the output. To achieve this, a script to iterate each row will be needed and the sample script could be the one below:
while IFS= read -r line; do
printf '%s %sn' "$(date +%Y-%m-%dT%H:%M:%S)" "$line";
done
To further make this work with the mysql.exe -e, I created the above script as a function and call the function along with mysql SQL execution:
querytime() {
while IFS= read -r line; do
printf '%s %sn' "$(date +%Y-%m-%dT%H:%M:%S)" "$line";
done
}
mysql
-h servername.mysql.database.azure.com
-u user@servername
-pXXXXX
-e "
USE globalstatus;SELECT m.metric_name, g.VARIABLE_VALUE - m.origin_metric_value AS metric_value FROM (SELECT VARIABLE_NAME, VARIABLE_VALUE FROM performance_schema.global_status) AS g, (SELECT metric_name, origin_metric_value FROM globalstatus.my_global_status) AS m WHERE m.metric_name = g.VARIABLE_NAME ; UPDATE globalstatus.my_global_status m, performance_schema.global_status g SET m.origin_metric_value = g.VARIABLE_VALUE Where m.metric_name = g.VARIABLE_NAME;" | querytime >> /home/x_xiao2_bnu/mysql_shawn_status/mysql_global_status.log
Then the output should be looks something like below
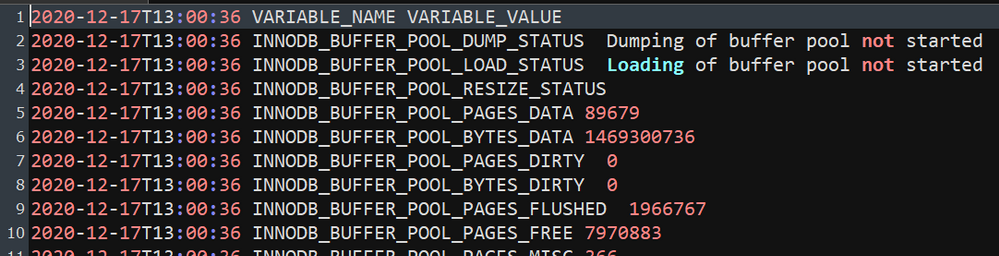
The last step of this part is to make this process automatically repeat every minute. In Linux, the most popular scheduler is crontab. If we can ask crontab to help run this command every minute, we will get the time-lined metric value change in one log file that could be used for later analysis.
So here listed what I did:
- Created a bash file (.sh) with below script:
#!/bin/bash
querytime() {
while IFS= read -r line; do
printf '%s %sn' "$(date +%Y-%m-%dT%H:%M:%S)" "$line";
done
}
mysql
-h servername.mysql.database.azure.com
-u user@servername
-pXXXXXX
-e "
USE globalstatus;SELECT m.metric_name, g.VARIABLE_VALUE - m.origin_metric_value AS metric_value FROM (SELECT VARIABLE_NAME, VARIABLE_VALUE FROM performance_schema.global_status) AS g, (SELECT metric_name, origin_metric_value FROM globalstatus.my_global_status) AS m WHERE m.metric_name = g.VARIABLE_NAME ; UPDATE globalstatus.my_global_status m, performance_schema.global_status g SET m.origin_metric_value = g.VARIABLE_VALUE Where m.metric_name = g.VARIABLE_NAME;" | querytime >> /home/x_xiao2_bnu/mysql_shawn_status/mysql_global_status.log
- Made this file runnable in Linux:
- Schedule in crontab to run this script every minute (this configuration is every easy and there are tons of detailed instructions online)
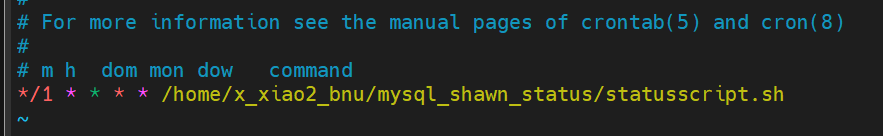
Please note that, if this script kept running, the log file will constantly grow. To save the storage space, I would suggest to have another process to purge the log by deleting some old data. For example, run a cleaner job every day to delete first 10k rows. There will be one of the many ways to do this but lets not focus it here in this article.
Use Azure Log Analytics for faster and easier analytics !!!
In the last part, it is time to constantly upload the log generated from above steps to Azure Log Analytics workspace. Before setting this up, the first step is to link your VM used for data collection where the log stored and your Azure Log Analytics Workspace.
- If you don’t already have Log Analytics workspace, then create one in Portal.
- After creation, navigate to Log Analytics workspace in your Azure Portal and select Virtual Machine from the left side blade menu. The right side should list out your Azure VM. Select the VM where the performance_schema global_status data change log saved. Then a service called OMS agent will be installed on selected VM, so this may take some time.
Once the above is completed, please refer to the document at https://docs.microsoft.com/en-us/azure/azure-monitor/platform/data-sources-custom-logs#step-1-open-the-custom-log-wizard to configure custom log upload. This will help you walk through the process and your log will automatically uploaded to your Log Analytics workspace.
Analyze the data !!!
Till now, the most of the steps are completed and we are now reaching the final step – analyzing the data. If you have never got chances to play around with Log Analytics, I would recommend you refer to the document Log Analytics tutorial – Azure Monitor, which should be a good start. For our task here, you can first verify if your log started to show in custom log session:
If the answer is yes, then Congratulations. You are now ready to monitor and investigate your Azure MySQL performance. Get your hands dirty with data analysis !
Let’s see how our log looks like in Azure Log Analytics:
As seen above, if we queried the custom log with no filter conditions, it will return all columns but only RawData column is what we need to care about because it is our logged global metrics value. So we will need to clean this data to format it in a more read-friendly format (The query used below can be found in the documentation Overview – Azure Data Explorer | Microsoft Docs )
MyGlobalSatus_CL
| extend originalEventTimestamp = todatetime(extract("([0-9-A-Za-z:]+)", 1, RawData, typeof(string)))
| extend metric_name = tostring(split(split(RawData," ",1)[0], " ", 0)[0])
| extend metric_value = toreal(split(split(RawData," ",1)[0], " ", 1)[0])
| project originalEventTimestamp, metric_name, metric_value
And the output should be like:
Now it looks much better and cleaner. We can play around with this data now.
First let’s try to get innodb data IO request and I am sharing below query I used:
MyGlobalSatus_CL
| extend originalEventTimestamp = todatetime(extract("([0-9-A-Za-z:]+)", 1, RawData, typeof(string)))
| extend metric_name = tostring(split(split(RawData," ",1)[0], 't', 0)[0])
| extend metric_value = toreal(split(split(RawData," ",1)[0], " ", 1)[0])
| where metric_name in ('Binlog_io_read', 'Binlog_io_written', 'Innodb_data_read', 'Innodb_data_reads', 'Innodb_data_writes', 'Innodb_data_written', 'Innodb_log_writes', 'Innodb_log_written')
| extend TIMESTAMP = bin(originalEventTimestamp, 30s)
| extend Binlog_io_read_tmp = iff(metric_name =~ 'Binlog_io_read', metric_value, 0.0),
Binlog_io_written_tmp = iff(metric_name =~ 'Binlog_io_written', metric_value, 0.0),
Innodb_data_read_tmp = iff(metric_name =~ 'Innodb_data_read', metric_value, 0.0),
Innodb_data_reads_tmp = iff(metric_name =~ 'Innodb_data_reads', metric_value, 0.0),
Innodb_data_writes_tmp = iff(metric_name =~ 'Innodb_data_writes', metric_value, 0.0),
Innodb_data_written_tmp = iff(metric_name =~ 'Innodb_data_written', metric_value, 0.0),
Innodb_log_writes_tmp = iff(metric_name =~ 'Innodb_log_writes', metric_value, 0.0),
Innodb_log_written_tmp = iff(metric_name =~ 'Innodb_log_written', metric_value, 0.0)
| summarize Binlog_io_read_in_MB = max(Binlog_io_read_tmp)/1024/1024,
Binlog_io_written_in_MB = max(Binlog_io_written_tmp)/1024/1024,
Innodb_data_read_in_MB = max(Innodb_data_read_tmp)/1024/1024,
Innodb_data_reads = max(Innodb_data_reads_tmp),
Innodb_data_writes = max(Innodb_data_writes_tmp),
Innodb_data_written_in_MB = max(Innodb_data_written_tmp)/1024/1024,
Innodb_log_writes = max(Innodb_log_writes_tmp),
Innodb_log_written_in_MB = max(Innodb_log_written_tmp)/1024/1024
by TIMESTAMP
| order by TIMESTAMP asc
| render timechart
The output generated a graph like:
At the bottom, you can select or unselect the counters to display only concerned metrics. This will help effectively check how much IO on your InnoDB engine.
Similarly, below query can be used to check the number of DDL or DML queries:
This will tell you how your workload changed and what types of queries contributed the most load. If you observed a correlation with your CPU usage, then it is caused by some queries.
Below is to check logical read for your MySQL. If the value of innodb_buffer_pool_read_requests is high, then it proves that you have full table scan (at least large table scan) or may be missing indexes on some tables, which will consume a lot of CPU.
MyGlobalSatus_CL
| extend originalEventTimestamp = todatetime(extract("([0-9-A-Za-z:]+)", 1, RawData, typeof(string)))
| extend metric_name = tolower(tostring(split(split(RawData," ",1)[0], " ", 0)[0]))
| extend metric_value = toreal(split(split(RawData," ",1)[0], " ", 1)[0])
| where metric_name in ('innodb_buffer_pool_read_requests', 'innodb_buffer_pool_reads')
| extend TIMESTAMP = bin(originalEventTimestamp, 1s)
| project TIMESTAMP, originalEventTimestamp, metric_name, metric_value
| extend Innodb_buffer_pool_read_requests_tmp = iff(metric_name =~ 'Innodb_buffer_pool_read_requests', metric_value, 0.0),
Innodb_buffer_pool_reads_tmp = iff(metric_name =~ 'Innodb_buffer_pool_reads', metric_value, 0.0)
| summarize Innodb_buffer_pool_read_requests = max(Innodb_buffer_pool_read_requests_tmp),
Innodb_buffer_pool_reads = max(Innodb_buffer_pool_reads_tmp)
by TIMESTAMP
| order by TIMESTAMP asc
| render timechart
Last But Not Least!
Please note that, based on usage and impact of VM, network latency, and MySQL load, there could be some differences when fetching those metrics value and when getting the subtractions. So there may be some scenarios that the value does not reflect the real case correctly. There could be many ways to get those data and put into analysis.
I hope the above idea could somewhat inspire you to explore more.
Thank you!


![Setting Correct Default Mode for Forms in a Canvas App | [Quick Tip]](https://www.drware.com/wp-content/uploads/2020/12/insertedform-638x675.png)
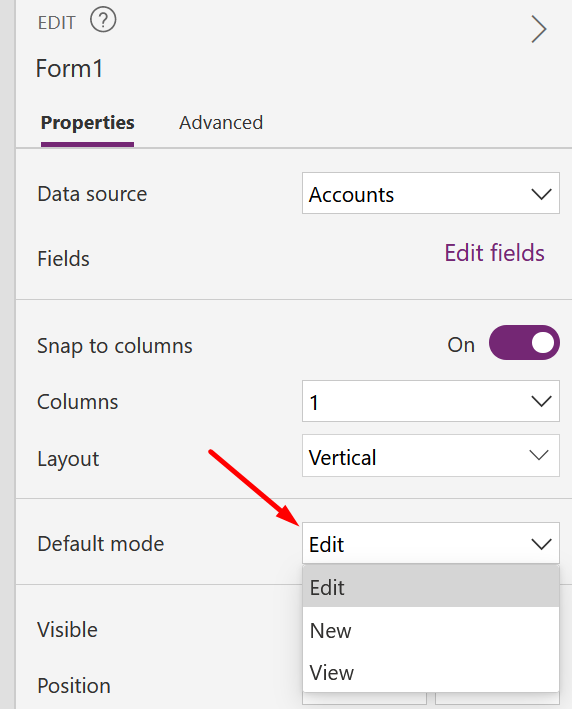
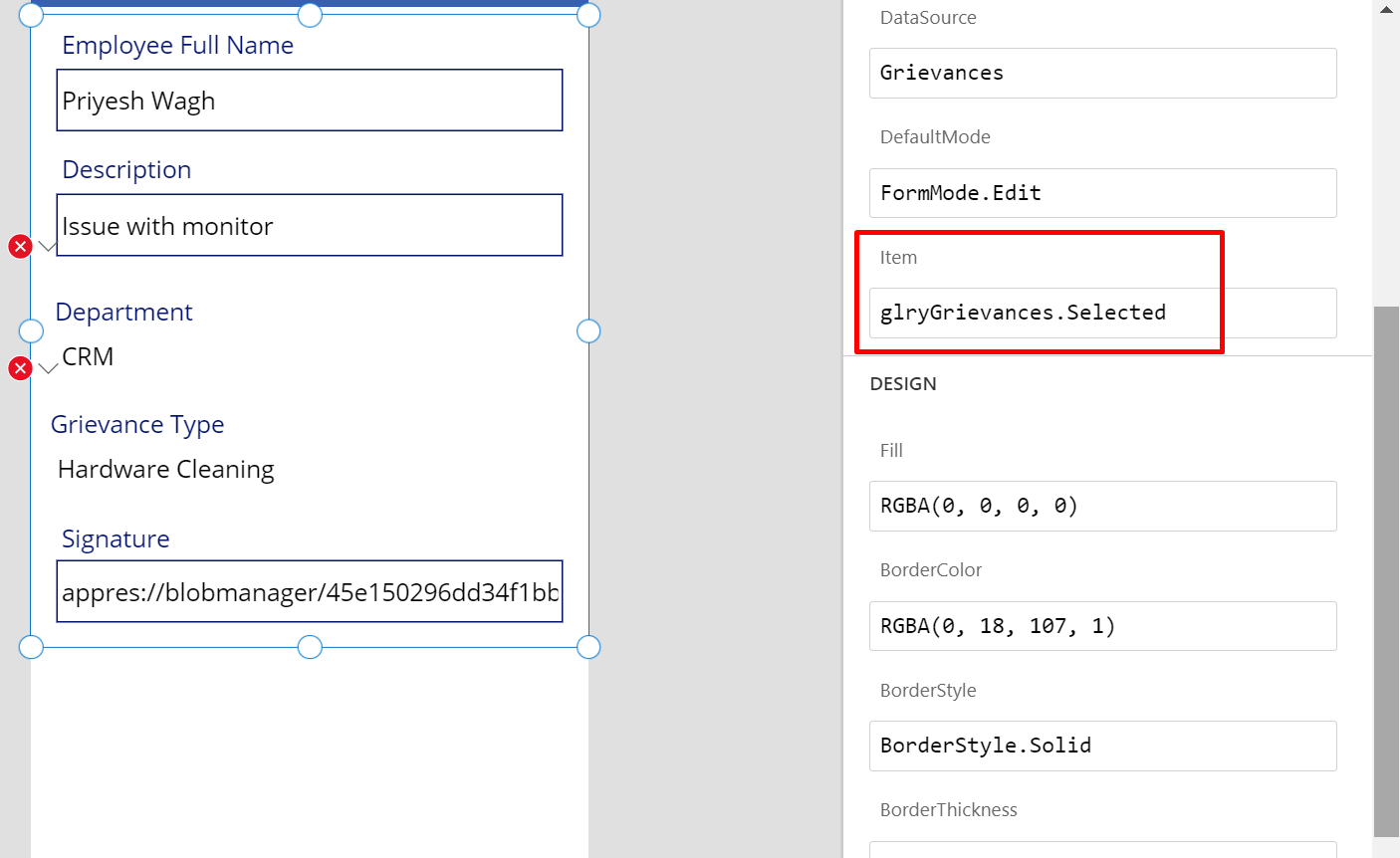
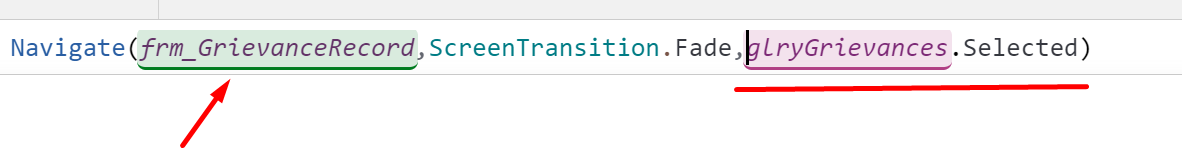
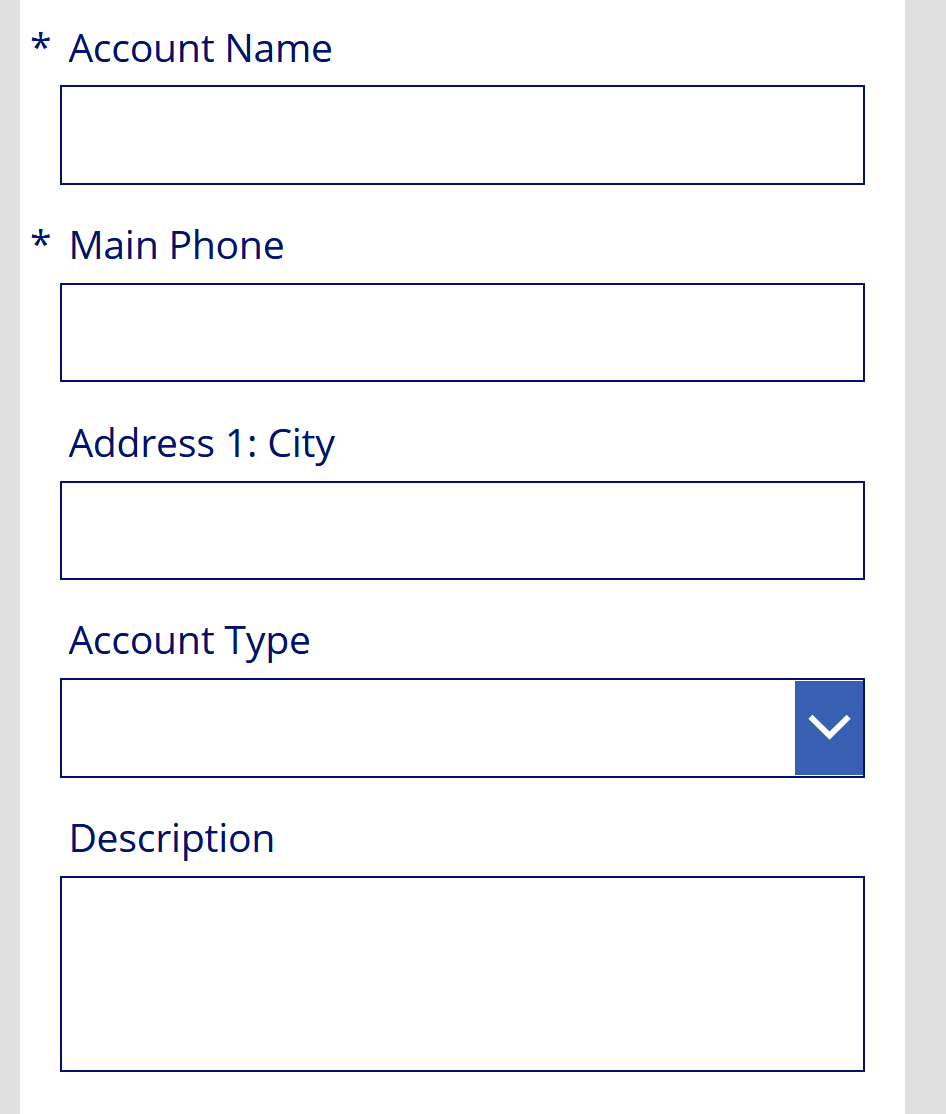

Recent Comments