by Contributed | Dec 15, 2020 | Technology
This article is contributed. See the original author and article here.
Hopefully, you had a chance to read Get a bird’s eye view of your data estate with Azure Purview Data Insights blog, to get an understanding of all that you can achieve with Azure Purview Data Insights. Below I offer a deeper dive into how you can convert the Data Insights into actionable measures.
Answer questions with Purview Insights
Imagine you are a member of the governance team in your company and you have a charter that requires all assets with Credit Card Number to be stored in a specific location within a database. Like most companies today, critical information is typically secured in a single location. But monitoring over time is a challenge.
With Azure Purview however, you can map and classify the data comprehensively. Here’s how we can help you ratify your earlier decision regarding critical information.
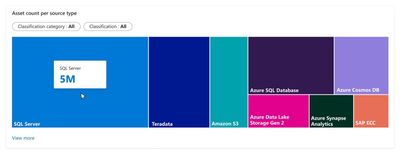
1) Start at Asset Insights. First, you see the data estate has multiple source types with millions of assets, which is expected. You pick classification category as Personal and classification as Credit Card Number. You notice, however, that Credit Card Number is stored in multiple locations including your petabyte sized data lake that is generously accessed. This violates your corporate credit card storage policy and must be addressed.

Figure 1
2) You dive into ADLS Gen 2 where you discovered data classified as Credit Card Number. Click on “View more” and pick ADLS Gen 2 from the list.
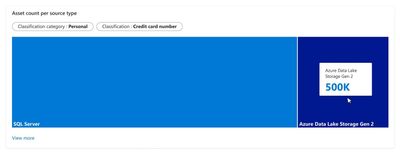
Figure 2
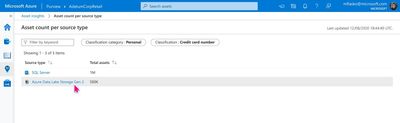
Figure 3
3) You can click on Asset count and view the list of assets that are classified as containing Credit Card Number.
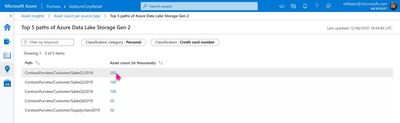
Figure 4
4) Contact the owners of the Data Lake – You can now find out the data owners by clicking on the assets from the list and contact them with next steps.
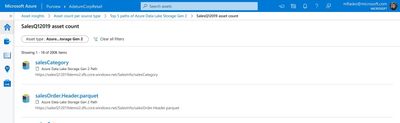
Figure 5
Conclusion
Azure Purview Data Insights helps you get a bird’s eye view of your data estate and deep dive into a specific area to answer a question or solve a problem.
Azure Purview Data Insights caters to a diverse set of users – from technical and business oriented users. Learn more about how we answer a business user’s questions using Glossary insights.
If you manage scans in Azure Purview, Insights can help you get an overview of all your scans through Scan insights. Learn more about Insights concepts today and Create an Azure purview account.
For more information, check out a demo of Azure Purview or start a conversation within the Azure Purview tech community.
More Resources
Read more about Azure Purview
Have a question? Check out our Frequently Asked Questions
by Contributed | Dec 15, 2020 | Technology
This article is contributed. See the original author and article here.
You’ve started scanning, classifying, and discovering the data at your company with Azure Purview. You’re now ready to engage with Azure Purview Data Insights – you can now assess data usage across your company with specific insights for data catalog administrators, data stewards, data officers, compliance and security officers. In Azure Purview Data Insights, you will gain access to important, eye-opening details about data residing in on-premises, multi-cloud and SaaS apps.
Azure Purview Data Insights creates a bird’s eye view across your data estate and allows you to drill into report data and take to understand your data, govern your data, govern your data glossary, and address anomalies in your data estate from inside the Azure Purview experience. Data officers and security officers can answer questions through Azure Purview Data Insights such as: what data does your company have, where is your company’s data, what classification of data is held within a data asset, what is the sensitivity of data in an asset, and how is my data estate changing over time. Let’s look at the Purview Data Insights reports you can check out right away!
Azure Purview Data Insights
Azure Purview Data Insights can be found by navigating to the Insights icon.

Asset Insights
Asset insights provides a panoramic view across the data estate managed by Azure Purview. This experience offers insights into the progression of data assets including how many data sources have been scanned, how many assets were discovered, and how many discovered assets were classified. You can select a system- or user-defined classification and view the distribution of assets by source type, for the classification. For example, below shows the distribution of assets classified as ‘Email Address’. With View more, you can also see the top 5 folders containing the filtered classification.
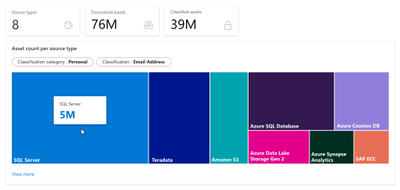
For file-based assets (Azure Blob, ADLS Gen 1 and ADLS Gen 2), Asset Insights enables a deeper look into size and file type trends, as well as files not associated with resource sets. This enables you to quickly identify anomalies in data assets. For instance, if you have a specific resource set pattern for your ADLS Gen 2 account, use the “Assets without Resource set” graph to identify files that do not follow the resource set pattern. Asset Insights allows you to drill down and contact the asset owner to address the anomaly.
To learn more, visit Asset Insights documentation
Scan Insights
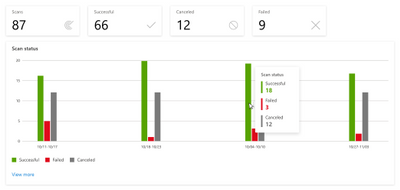
Scan insights provides a view of scan progress across the last 30 days. This allows you to gain insights about scans and understand when scans are failing. Scanning sets the stage for the additional insights. With View more, you can see scan names by count of successful, canceled, and failed scans. If you want to drill deeper, Insights can help you navigate to scan history to see exactly when the scans were run with a failed, canceled, or successful outcome.
To learn more, visit Scan Insights documentation
Glossary Insights
A glossary provides a vocabulary for business users to manage business terms attached to assets. Glossary Insights enables you as a business user, to understand total terms in the glossary, count of approved and expired terms and understand the usage of terms applied to assets. Glossary Insights also helps business users complete their glossary by showing terms with missing experts or stewards. With View more, you can see which terms are missing information and you can navigate to Glossary to remediate immediately.
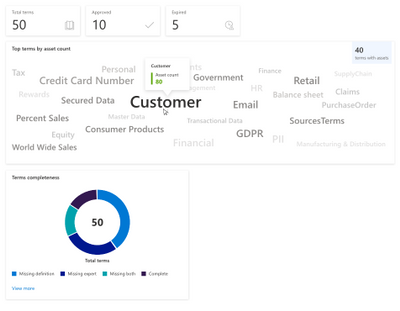
To learn more, visit Glossary Insights documentation
Classification Insights
Classification insights help you understand the types of information found in your organization’s data estate, and where classified data is located. In Azure Purview, classifications are used to identify content of a specific type in your data estate.
Classifications insights showcase what set of assets contain sensitive information types like Credit Card information, SSNs and email addresses were found. .Use the report to identify data with specific classifications and understand required actions, such as adding additional security to the repositories, or moving data to a more secure location.
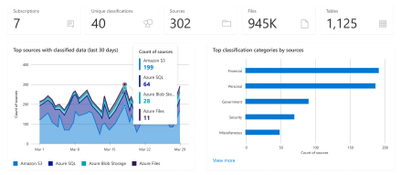
To learn more, visit Classification Insights documentation
Microsoft Information Protection sensitivity labels Insights
Microsoft Information Protection sensitivity labels enable you to classify and protect your organization’s data, while ensuring user productivity and their ability to collaborate isn’t hindered. With Azure Purview, you can now extend these sensitivity labels to your Azure assets and gain insights into the state of your data. Sensitivity labels insights provide you an overview of the sensitivity labels applied in your data estate, as well as a drilldown to the labeled files and databases.
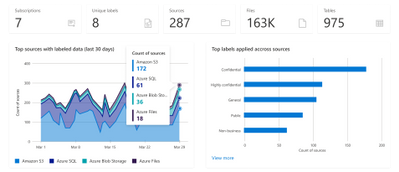
To learn more, visit Sensitivity label insights documentation
File Extensions Insights
After scanning your assets, Azure Purview will detect the file types found in your data estate and provide you with details about each file type as part of File Extensions Insights report. Use the report to identify how many different file types you have, how many files of each type are found, where those files are, and whether they can be scanned for sensitive data or not.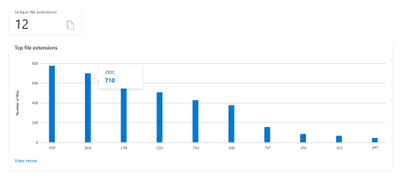
To learn more, visit File extension Insights documentation
Filter for Close-up Insights
Each set of Insights offers you the ability to filter to dimensions that help you understand your data estate. Use the time, source type, file type, classification category, and classification to customize the report. Please read about these concepts in the documentation here

Conclusion
Azure Purview data insights offers a wealth of information to help you understand your data. From the panoramic view across your data of Asset Insights to in-depth view to act on specific assets to understanding the sensitivity of data with Classification Insights and Sensitivity Labels.
Create an Azure Purview account today and start understanding your data supply chain from raw data to business insights with free scanning for all your SQL Server on-premises and Power BI online.
For more information, check out a demo of Azure Purview or start a conversation within the Azure Purview tech community.
Read More
Read more about Azure Purview
Have a question? Check out our Frequently Asked Questions
by Contributed | Dec 15, 2020 | Technology
This article is contributed. See the original author and article here.
TL;DR – What-if is now Generally Available. We have closed over 90 customer-reported issues, improved the depth of the policy-aware capabilities, and made it easier for resource providers to fix their own what-if noise issues. While you might still encounter noise, these can now be resolved by the owning resource provider team, so issues should be resolved faster.
Why do I need what-if?
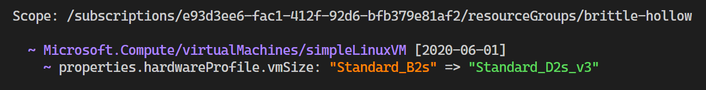
Deploying an ARM template can be a time-consuming process, which is why it is particularly frustrating if your deployment does not execute as expected. This creates a challenging and long dev/test loop, which can get frustrating very quickly! To help with this problem, we have introduced a new capability for ARM templates called What-if, which allows you to preview the effects of a template deployment before it is executed, allowing you to validate that the changes are expected before starting the deployment process. In this example, I am updating a Linux VM by upgrading the VM size. Before deploying, I can see that it is the only expected change and I can deploy with confidence.

What-if has been in a public preview for the last few months, and as part of our GA release, we are introducing the following improvements:
- Major noise-reduction and other enhancements to what-if quality. We have closed ~90 publicly reported issues from the what-if noise github repo. In addition, we have set up an internal pipeline to allow each resource provider to resolve their own what-if noise related to ARM API compliance, which is often the root cause of the issue. As a result, we expect to see a rapid, continual improvement of what-if quality going forward.
- What-if is now “policy aware” for the modify effect. This means if a property will be modified by policy, it will be captured in the what-if response. For example, if a tag is going to be added by a modify policy, this will be reflected in the what-if output for the relevant resources. What-if is already policy-aware for the deny effect, so deployments that will fail due to policy will be caught quickly with what-if. We plan to also support the audit effect as part of our post-GA improvements.
How do I get started with what-if?
What-if is available as part of the deployment cmdlets in the PowerShell Az module and the deployment commands in Az CLI. If you have a recent release of either of these tools, you likely already have them available. You will need version 4.2 or later of PowerShell Az and version 2.5 or later for Az CLI.
The easiest way to run what-if is simply by appending either -Confirm in Az PowerShell or –confirm-with-what-if or -c in Az CLI to the commands you are already using:
Az PowerShell:
New-AzResourceGroupDeployment -TemplateFile ./azureDeploy.json -ResourceGroupName my-rg -Confirm
Az CLI:
az deployment group create -f ./azureDepoy.json -g my-rg --confirm-with-what-if
This will emit a user-friendly formatted text output to the console like the screenshot above and ask you if you’d like to proceed with the deployment, but you can also return the results as JSON so you can interrogate the results programmatically. You can also run what-if without the confirm behavior if you’d like to use what-if for a CI/CD approval workflow.
For a full walkthrough, you can use the what-if How To guide.
Some notes on what-if noise
During the public preview, our primary goal was to reduce the amount of noise you would see in the what-if response. These were cases where what-if told you, incorrectly, that a change was going to take place even though no change would occur. You all in the Azure community have done a great job opening issues in the what-if repo and exposing us to the noise you encountered. All told, we have closed ~90 noise issues so far and will continue to burn down the list.
At the same time, we have instituted more quality gates for resource provider teams to ensure their resources are modelled correctly. This quality check will ensure what-if works as expected with no noise in the response. As a result of this, what-if quality should continue to get improve at a quicker pace.
While the quality of what-if has increased dramatically, it is still possible to find what-if noise depending on the resource types you deploy in your templates. If you encounter noise, you should still open an issue in the what-if repo and we can get it routed to the right team to get it fixed quickly.
As always, if you have any questions or problems with deployment scripts, don’t hesitate to reach out at alfran@microsoft.com, on twitter or on GitHub.
by Contributed | Dec 15, 2020 | Technology
This article is contributed. See the original author and article here.
TL;DR – Deployment Scripts is now Generally Available, and as part of this release we’ve made deployment scripts more reliable and easier to use with an improved permissions model.
Why do I need Deployment Scripts?
Often during an ARM Template deployment, there is an operation that needs to be performed that cannot be done natively in the template – either because there is no explicit support or because the operation takes place outside of Azure. For example, you may need to populate data in a database, deploy a Kubernetes manifest, or get a new IP address from an IPAM system. Customers will often fill this gap by running a script in a release pipeline or manually performing the task before or after the deployment occurs.
Deployment Scripts allow you to complete these “last mile” scenarios as part of your ARM Template deployments by running your bash or PowerShell script in a native Deployment Scripts resource. Deployment Scripts has been available in public preview for a few months, and today we are making Deployment Scripts generally available.
What’s new for GA?
With our GA release we are adding the following features and capabilities:
- You are no longer required to provide a User-assigned Managed Identity for the script to be executed. This is for use cases that do not require authentication to Azure, such as a data transformation or communication with a non-Azure API or if you’d rather use a service principal to authenticate to Azure instead of a Managed Identity. This makes executing deployment scripts much lower friction with less prerequisites.
- The underlying resources that are required for a deployment script to execute (Azure Container Instance and Storage Account) will no longer be created with the Managed Identity. Instead, we use the permissions of the AAD principal that created the deployment to create them. For a principal to create a deploymentScript they will now need the following permissions:
"Microsoft.Resources/deploymentScripts/*",
"Microsoft.ContainerInstance/containerGroups/*",
"Microsoft.Storage/storageAccounts/*"
We will use the permissions of the AAD principal executing the deployment to create these resources and register the underlying ContainerInstance Resource Provider. As a result of this change, the permissions granted to the managed identity can be more limited as it only requires what the script needs to run successfully.
- Better error handling for RBAC replication issues. You should now be able to reliably assign permissions to the Managed Identity in the same template that creates the deployment script without any authentication issues. This makes it easier to create a “self-contained” template deployment script template. During the preview, we noticed issues to do replication delays that prevented from working well.
How do I get started?
If you are already familiar with ARM Templates, getting started with Deployment Scripts is easy. Simply add a resource of type Microsoft.Resources/deploymentScripts to your ARM template:
{
"type": "Microsoft.Resources/deploymentScripts",
"apiVersion": "2020-10-01",
"kind": "AzurePowerShell",
"name": "[parameters('dsName')]",
"location": "[parameters('location')]",
"properties": {
"azPowerShellVersion": "3.0",
"scriptContent": "
$DeploymentScriptOutputs['test'] = 'test this output'
Write-Host 'I am a deployment script'
",
"forceUpdateTag": "[parameters('timestamp')]", // utcNow()
"retentionInterval": "PT4H"
}
}
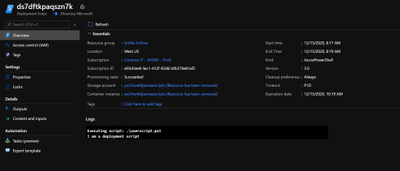
Once the script has executed I can view the details of the script execution in PowerShell, CLI, or in the Azure Portal

For more details, take a look at the below guides and examples.
We have seen a lot of awesome use cases be developed for deployment scripts during the public preview and we are looking forward to hearing how these new GA capabilities improve the experience even further. As always, if you have any questions or problems with deployment scripts, don’t hesitate to reach out at alfran@microsoft.com, on twitter or on GitHub.
Happy Deployment Scripting!
by Contributed | Dec 15, 2020 | Technology
This article is contributed. See the original author and article here.
‘Tis the season! Did you grab a Microsoft-themed sweater? Sold out? Don’t worry. We’ve created three SharePoint-themed winter holiday sweaters to back you up – in Microsoft Teams, or to use as wallpaper on your desktop.
Make your productivity festive and intranet’ty! Grab the png’s and follow the ‘how to’ link below.
 SharePoint holiday sweater background – abstract.
SharePoint holiday sweater background – abstract.
Download SharePoint holiday sweater background – abstract.
 SharePoint holiday sweater background – Hanukkah.
SharePoint holiday sweater background – Hanukkah.
Download SharePoint holiday sweater background – Hanukkah.
 SharePoint holiday sweater background – Christmas.
SharePoint holiday sweater background – Christmas.
Download SharePoint holiday sweater background – Christmas.
Learn how to change your background for a Microsoft Teams meeting.
Special thanks to our design team for creating the fun.
View more Microsoft background and wallpapers.
Stay safe and happy holidays,
Wenvi Hidayat



Recent Comments