
by Contributed | Jan 28, 2021 | Technology
This article is contributed. See the original author and article here.

Want to learn how to use Microsoft Teams effectively at your hospital? Join Mary Buonanno, Healthcare Chief Technology Officer at The Ergonomic Group, and Margaret Campbell, Director at HealthNET Consulting, as they share their real-world experience with Microsoft Teams during COVID-19 in a multi-facility acute care hospital environment.
Topics will include:
• Why MS Teams
• COVID-19’s impact
• Using MS Teams in an EHR implementation
• Benefits realized / lessons learned
• Technology considerations for a successful deployment
You’ll learn practical tips — and even hear some Teams insight from Microsoft support — on how Microsoft Teams can help your hospital improve operational efficiencies.
Join us on Wednesday, February 10th from 2-3 PM EST.
Presenters:
Sam Brown, Teams Technical Specialist, Microsoft
by Contributed | Jan 28, 2021 | Technology
This article is contributed. See the original author and article here.
UEFI signing is a service provided by the Windows Hardware Dev Center dashboard by which developers submit UEFI firmware binaries targeted to x86, x86-64, or ARM computers. After these binaries are approved through manual review, the owners can install them on PCs that have secure boot enabled with the Microsoft 3rd Party UEFI CA permitted.
While Microsoft reserves the right to sign or not sign submissions at its discretion, you should adhere to these requirements. Doing so will help you achieve faster turnaround times for getting a submission signed and help avoid revocation. Microsoft may conduct follow-up reviews, including but not limited to questionnaires, package testing, and other security testing of these requirements before signing.
The following list contains the latest requirements for the UEFI signing process. These requirements are to ensure the security promise of secure boot, and to help expedite the turnaround of signing submissions.
- UEFI submissions require an EV certificate and an Azure Active Directory (AAD) account.
- Only production quality code (for example, “release to manufacturing” code, rather than test or debug modules) that will be released to customers (no internal-only code or tools) are eligible for UEFI signing. For internal-use code, you should add your own key to the Secure Boot database UEFI variable or turn off Secure Boot during development and testing.
- Microsoft UEFI CA signs only those products that are for public availability and are needed for inter-operability across all UEFI Secure Boot supported devices. If a product is specific to a particular OEM or organization and is not available externally, you should sign it with your private key and add the certificate to Secure Boot database.
- Code submitted for UEFI signing must not be subject to GPLv3 or any license that purports to give someone the right to demand authorization keys to be able to install modified forms of the code on a device. Code that is subject to such a license that has already been signed might have that signature revoked. For example, GRUB 2 is licensed under GPLv3 and will not be signed.
- If there’s a known malware vector related to code that uses certain techniques, that code will not be signed and is subject to revocation. For example, the use of versions of GRUB that aren’t Secure Boot enlightened will not be signed.
- If there are known security vulnerabilities in your submission code, the submission will not be signed, even if your functionality doesn’t expose that code. For example, the latest known secure versions of OpenSSL are 0.9.8za and 1.0.1h, so if your submission contains earlier versions that contain known vulnerabilities, the submission will not be signed.
- You must test your product, following the Pre-Submission testing document (for UEFI Submissions), before submitting for signing.
- Microsoft will not sign EFI submissions that use EFI_IMAGE_SUBSYSTEM_EFI_RUNTIME_DRIVER. Instead, we recommend transitioning to EFI_IMAGE_SUBSYSTEM_EFI_BOOT_SERVICE_DRIVER. This prevents unnecessary use of runtime EFI drivers.
- Use of EFI Byte Code (EBC): Microsoft will not sign EFI submissions that are EBC-based submissions.
- If your submission is a DISK encryption or a File/Volume based encryption, then you MUST make sure that you either don’t encrypt the EFI system partition or if you do encrypt, be sure to decrypt it and make it available by the time Windows is ready to boot.
- If your submission is comprised of many different EFI modules, multiple DXE drivers, and multiple boot applications, Microsoft may request that you consolidate your EFI files into a minimal format. An example may be a single boot application per architecture, and a consolidation of DXE drivers into one binary.
- If your submission is a SHIM (handing off execution to another bootloader), then you must first submit to the SHIM review board and be approved before a submission will be signed. This review board will check to ensure the following:
- Code signing keys must be backed up, stored, and recovered only by personnel in trusted roles, using at least dual-factor authorization in a physically secured environment.
- The private key must be protected with a hardware cryptography module. This includes but is not limited to HSMs, smart cards, smart card–like USB tokens, and TPMs.
- The operating environment must achieve a level of security at least equal to FIPS 140-2 Level 2.
- If embedded certificates are EV certificates, you should meet all of the above requirements. We recommend that you use an EV certificate because this will speed up UEFI CA signing turnaround.
- Submitter must design and implement a strong revocation mechanism for everything the shim loads, directly and subsequently.
- If you lose keys or abuse the use of a key, or if a key is leaked, any submission relying on that key will be revoked.
- Some shims are known to present weaknesses into the SecureBoot system. For a faster signing turnaround, we recommend that you use source code of 0.8 or higher from shim – GitHub branch.
- If your submission contains iPXE functionality, then additional security steps are required. Previously, Microsoft has completed an in depth security review of 2Pint’s iPXE branch. In order for new submissions with iPXE to be signed, they must complete the following steps:
- Pull and merge from 2Pint’s commit: http://git.ipxe.org/ipxe.git/commitdiff/7428ab7
- Get a security review from a verified vendor. Refer vendor to the iPXE Security Assurance Review blog post. Emphasis of the review should be on:
- NFS functionality being removed
- Wireless functionality being removed
- Non-UEFI loaders are not included
- Ensuring all known reported security problems are fixed (identified in the iPXE Security Assurance Review blog post).
- Share the specific commits that are made to the project, allowing Microsoft to ensure the expected changes are made.
For questions about the UEFI Signing process, contact uefisign@microsoft.com
by Contributed | Jan 28, 2021 | Technology
This article is contributed. See the original author and article here.
Join Anna Hoffman and Buck Woody as they take a tour of the incredible learning resource the Microsoft Engineering team has put together. From labs to full hands-on workshops and much more, you’ll find a wealth of high-quality, free-cost training. You’ll also learn about many of the other valuable references and assets you can find at SQL Workshops.
To get started with SQL Workshops, click here.
Watch on Data Exposed
View/share our latest episodes on Channel 9 and YouTube!
by Contributed | Jan 28, 2021 | Technology
This article is contributed. See the original author and article here.
Howdy folks!
In November, I shared that we’re simplifying the MFA management experience to manage all authentication methods directly in Azure AD. This change has been successfully rolled out to cloud-only customers. To make this transition smooth for hybrid customers, starting February 1, 2021, we will be updating the authentication numbers of synced users to accurately reflect the phone numbers used for MFA.
Daniel Wood, a Program Manager on the Identity Security team will share the details of this change for hybrid customers. As always, please share your feedback in the comments below or reach out to the team with any questions.
Best regards,
Alex Simons (Twitter: Alex_A_Simons)
Corporate Vice President of Program Management
Microsoft Identity Division
———————————————————
Hi everyone,
It’s never been more important to enforce MFA. As part of our efforts to make hybrid MFA deployments simpler and more secure, we’ll be updating empty authentication numbers with users’ public phone numbers if those numbers are being used for MFA. This change doesn’t affect the end user experience, but here’s what you’ll see as an admin after February 1:
Changes to user records
Starting February 1, 2021, for synced users who are using public profile numbers for MFA, Microsoft will copy the public number to users’ corresponding authentication number. Once the authentication number is populated, the MFA service will call that authentication number, instead of the public number. Microsoft will copy subsequent changes to the public number over to the authentication number until May 1, 2021 (except deletions of the public number).
Managing users’ authentication numbers
Going forward, you can manage your users’ authentication numbers directly in Azure AD using:
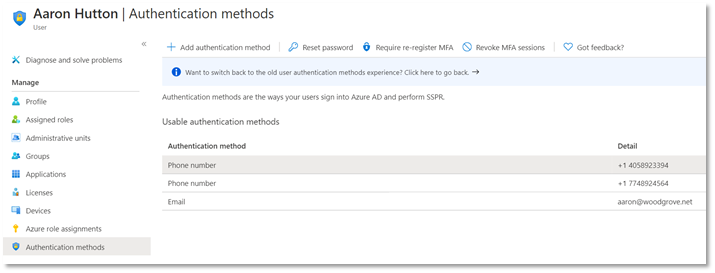
1. The user authentication methods UX

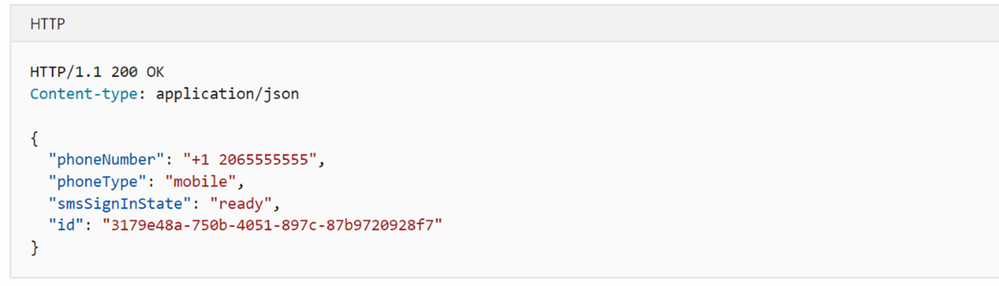
2. Microsoft Graph authentication methods APIs
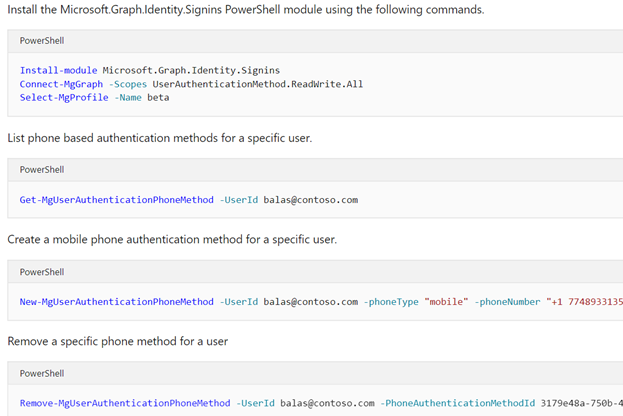
3. Microsoft.Graph.Identity.Signins PowerShell module
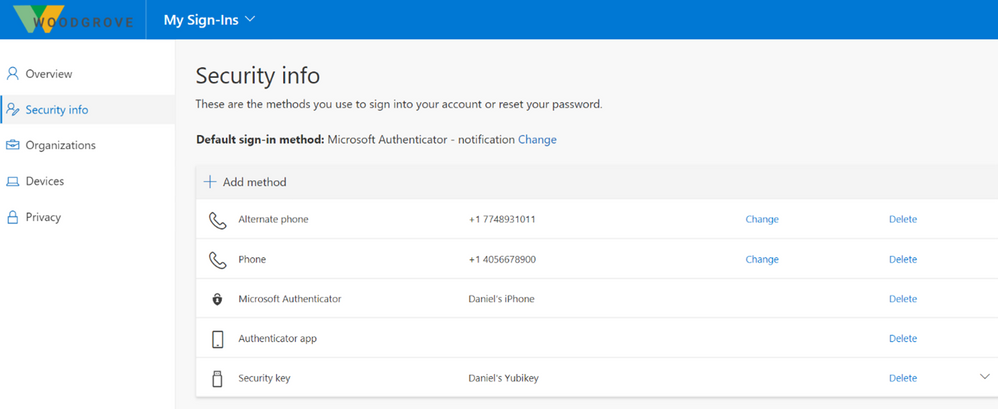
4. End users can update their authentication numbers in the security info tab of MyAccount.
We hope these changes will significantly simplify how users and admins manage their authentication methods while enhancing security. Please let us know your thoughts by leaving a comment below.
Best,
Daniel Wood (Twitter: Daniel_E_Wood)
Program Manager,
Microsoft Identity Division

by Contributed | Jan 28, 2021 | Technology
This article is contributed. See the original author and article here.

COVID is driving a tsunami of digital transformation initiatives in Healthcare and Life Science. But what’s the role and impact of electronic signatures within that industry vertical? During this webinar, Jayashree Ramakrishna (Adobe Head of Industry Strategy: Healthcare and Life Science) and Michael Point (Adobe Head of Technical Product Marketing and Evangelism) took our audience through a high-level overview of this highly regulated vertical and talk about what’s in-store for Health and Life Sciences in the Age of Digitization.
In this recorded demonstration, you will see how Adobe Sign can help support Virtual Consult by bringing patients and clinicians together and sign important documents such as a HIPPA Consent form in Microsoft Teams meeting. Check out the recording here:
Resources:
Presenters:

Jay Ramakrishna, Adobe Head of Industry Strategy: Healthcare and Life Science

Michael Point, Adobe Head of Technical Product Marketing and Evangelism
Producers:

Sam Brown, Microsoft Teams Technical Specialist

Pete Anello, Senior Microsoft Teams Technical Specialist
Recent Comments