by Scott Muniz | Jan 27, 2021 | Security, Technology
This article is contributed. See the original author and article here.
Original release date: January 27, 2021
CISA has released a malware analysis report on Supernova malware affecting unpatched SolarWinds Orion software. The report contains indicators of compromise (IOCs) and analyzes several malicious artifacts. Supernova is not part of the SolarWinds supply chain attack described in Alert AA20-352A.
CISA encourages users and administrators to review Malware Analysis Report MAR-10319053-1.v1 and the SolarWinds advisory for more information on Supernova.
This product is provided subject to this Notification and this Privacy & Use policy.
by Contributed | Jan 27, 2021 | Technology
This article is contributed. See the original author and article here.
Event Trigger in Azure Data Factory is the building block to build an event-driven ETL/ELT architecture (EDA). Data Factory’s native integration with Azure Event Grid let you trigger processing pipeline based upon certain events. Currently, Event Triggers support events with Azure Data Lake Storage Gen2 and General Purpose version 2 storage accounts, including Blob Created and Blob Deleted.
As with any architecture, it’s sometimes critical to enforce Role Based Access Control (RBAC) to ensure that only certain members on the team can access certain sensitive information. Unauthorized access to listen to, subscribe to updates from, and trigger pipelines linked to blob accounts should be strictly prohibited.
Azure Data Factory make it really easy for you and enforce the following rules:
- To successfully create a new or update an existing Event Trigger, the Azure account signed into the Data Factory needs to have owner access to the relevant storage account. Otherwise, the operation with fail with Access Denied
- Data Factory needs no special permission to your Event Grid, and you do not need to assign special RBAC permission to Data Factory service principal for the operation.
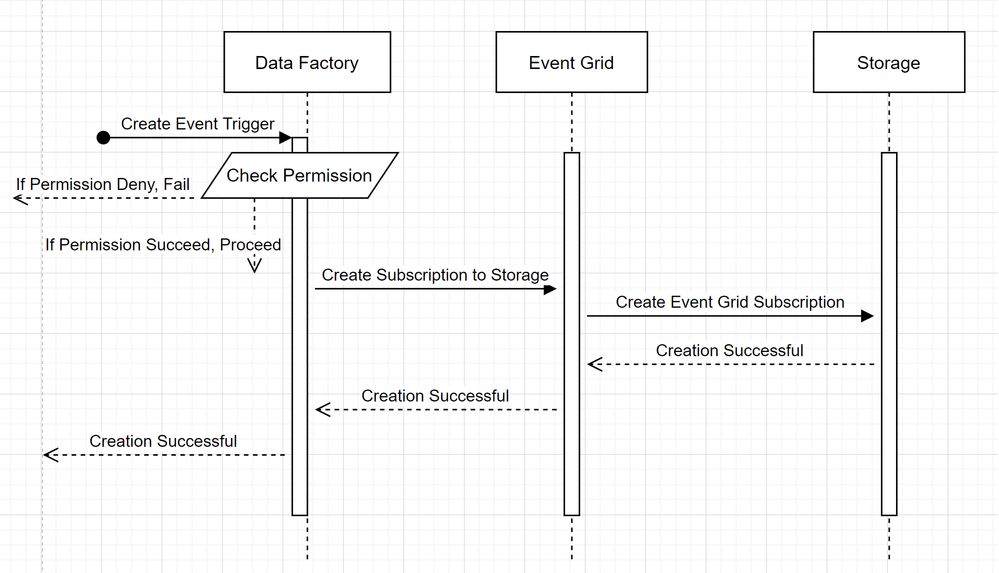
In order to understand how Azure Data Factory delivers the two promises, let’s take a step back and take a sneak peek behind the scene. These are the high level architecture for integration among Data Factory, Storage, and Event Grid.
- Create a new Event Trigger
 Two noticeable callouts from the flows are:
Two noticeable callouts from the flows are:
- Azure Data Factory makes no direct contact with Storage account. Request to create a subscription is instead relayed and processed by Event Grid. Hence, your Data Factory needs no permission to Storage account in this stage
- Access control and permission checking happens on Azure Data Factory side. Before ADF issues a request to subscribe to Storage event, it checks the permission for the user. More specifically, it checks whether the Azure account signed in and attempting to create the Event trigger have owner access to the relevant Storage account. If the permission check fails, trigger creation also fails
- Storage event trigger Data Factory pipeline run
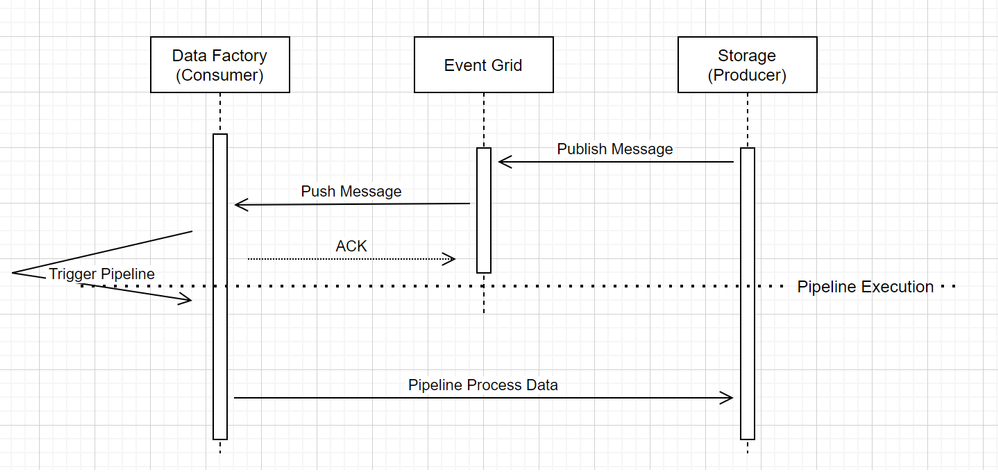
When it comes to Event triggering pipeline in Data Factory, two noticeable call outs in the workflow:
- Event Grid uses a Push model that it relays the message as soon as possible when storage drops the message into the system. This is different from messaging system, such as Kafka where a Pull system is used.
- Event Trigger on Azure Data Factory serves as an active listener to the incoming message and it properly triggers the associated pipeline.
- Event Trigger itself makes no direct contact with Storage account
- That said, if you have a Copy or other activity inside the pipeline to process the data in Storage account, Data Factory will make direct contact with Storage, using the credentials stored in the Linked Service. Please ensure that Linked Service is set up appropriately
- However, if you make no reference to the Storage account in the pipeline, you do not need to grant permission to Data Factory to access Storage account
What’s in the bag for the future?
The team is currently in the process of expanding functionalities for Event Trigger. Soon, we will support Custom Event in Event Grid to give customers even more flexibilities in defining the Event Driven Architecture. Please keep an eye out for the exciting announcement, as we test the functionality thoroughly and gradually roll it out to General Availability.
by Contributed | Jan 27, 2021 | Technology
This article is contributed. See the original author and article here.
After the Windows updates from November 2020, you might be facing some issues running Bulk Inserts or working with linked servers, if you keep an open session for more than 10 hours.
Some recent changes were done on the Windows side when it comes to the way S4U (Unconstrained delegation) Kerberos tickets work.
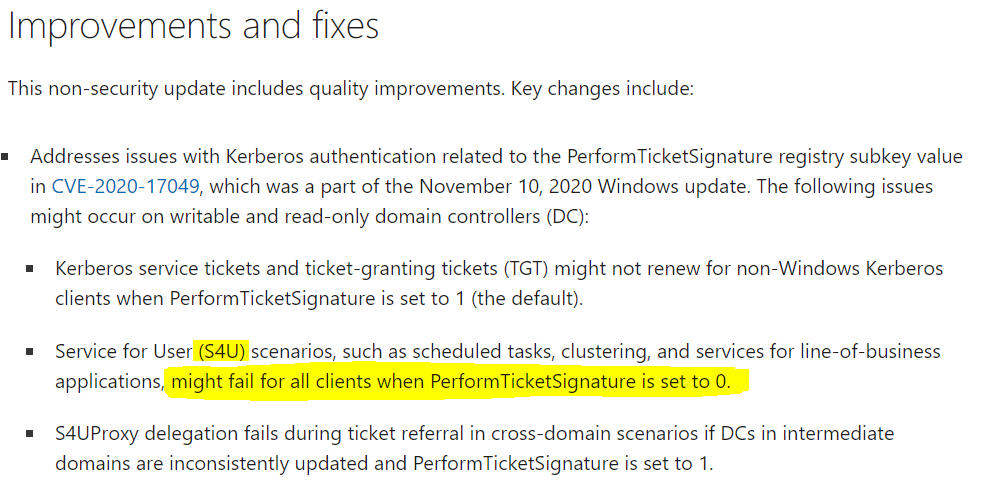
This is a long existing SQL issue where it expects to be able to have long lived delegatable sessions without the user ever re-authenticating. This issue is normally hidden by the fact that you can renew the TGT for up to 7 days by default. However, a recent patch for PerformTicketSignatures was released and the default setting does not issue renewable tickets.
Managing deployment of Kerberos S4U changes for CVE-2020-17049 (microsoft.com)
After installing this update on domain controllers (DCs) and read-only domain controllers (RODCs) in your environment, you might encounter Kerberos authentication and ticket renewal issues. This is caused by an issue in how CVE-2020-17049 was addressed in these updates.
|
Solution:
To solve this problem, there are two possibilities:
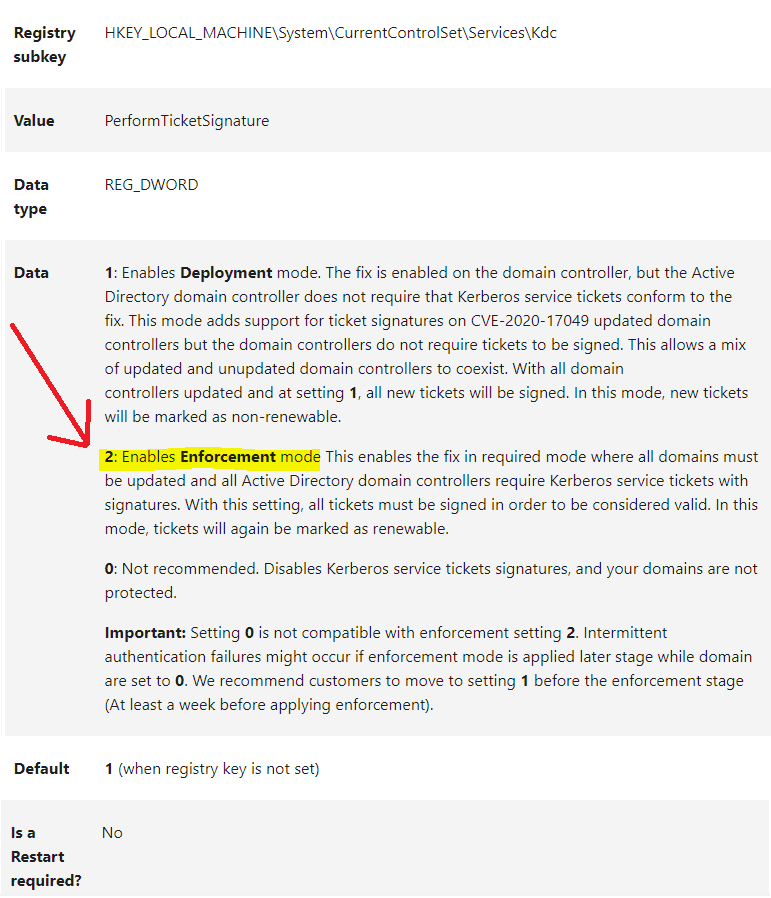
1. Install in all Domain Controllers the December 2020 update and Change the PerformTicketSignature key to 2 on all Domain Controllers
December 8, 2020—KB4593226 (OS Build 14393.4104) (microsoft.com)
Managing deployment of Kerberos S4U changes for CVE-2020-17049 (microsoft.com)
2. Change the authentication to Constrained delegation (S4UProxy)
The issue only happens with unconstrained delegation (S4U). So, the same problem will not happen in a constrained delegation environment.
Unconstrained delegation is considered vulnerable and a configuration with constrained delegation or resource based constrained delegation would be the most secure approach.
Other Windows Server Versions:
The same issue can be found in all Windows Security Patches after November 2020
Windows Server 2012 R2 – KB4586845
Windows Server 2012 – KB4586834
Credits:
Thank you to @dineu , Support Escalation Engineer from SQL Server Networking Team, for your help writing this post.
by Contributed | Jan 27, 2021 | Technology
This article is contributed. See the original author and article here.
Final Update: Wednesday, 27 January 2021 13:35 UTC
We’ve confirmed that all systems are back to normal with no customer impact as of 01/27, 13:00 UTC. Our logs show the incident started on 01/25, 08:00 UTC and that during the 2 Days & 5 Hours that it took to resolve the issue some of customers experienced “No Data found” message or may not be able to get data while looking at the logs.
- Root Cause: The failure was due to backend service.
- Incident Timeline: 2 Days & 5 Hours – 01/25, 08:00 UTC through 01/27, 13:00 UTC
We understand that customers rely on Azure Log Analytics as a critical service and apologize for any impact this incident caused.
-Madhav
Initial Update: Wednesday, 27 January 2021 10:37 UTC
We are aware of issues within Azure Log Analytics and are actively investigating. Some customers may view “No Data found” message or may not be able to get data while looking at the logs.
- Work Around: The data can be queried from workspace directly incase user have access to it.
- Next Update: Before 01/27 15:00 UTC
We are working hard to resolve this issue and apologize for any inconvenience.
-Mohini
by Contributed | Jan 27, 2021 | Technology
This article is contributed. See the original author and article here.
Initial Update: Wednesday, 27 January 2021 10:37 UTC
We are aware of issues within Azure Log Analytics and are actively investigating. Some customers may view “No Data found” message or may not be able to get data while looking at the logs.
- Work Around: The data can be queried from workspace directly incase user have access to it.
- Next Update: Before 01/27 15:00 UTC
We are working hard to resolve this issue and apologize for any inconvenience.
-Mohini


Recent Comments