
by Contributed | Jan 16, 2021 | Technology
This article is contributed. See the original author and article here.

Introduction into security principles in the context of database systems
By Andreas Wolter
While many of us are practicing ‘social distancing’, and spend lots of time at home, I am finally finding the time to share some of the topics with the public that I have been working on since I joined Microsoft at the end of 2018.
In the recent years and with increasing frequency, one of the asks in terms of Security to the SQL Engine On-Prem as well as SQL Azure Database has been coming up with solutions to help accomplish “Separation of Duties”. This is a good thing, because it reassures my point of view that Separation of Duties is becoming increasingly important in IT and specifically Cloud-based systems.
On the other hand, we noticed that there is not a broad understanding in the technical community yet as to what Separation of Duties (aka SoD) really means and how it can be accomplished today. It occurs to me that the understanding is often vague and sometimes even contradicting depending on who you ask. It might therefore help to provide some context and guidance on what SoD really is and how it relates to other commonly referenced security principles that have been established over the last decades in IT.
If you are not already an expert in IT security, I hope that you will find this series useful.
Intro: Motivation
Security principles in information technology or cybersecurity (I won’t touch on physical security in these articles) exist as guidelines to assist design and decision processes in architecture, implementation, and reactive procedures when incidents happen. The purpose is to help designing for security in the first place, by using common proven patterns, and to be able to effectively assess a systems security.
Building secure systems from the start can be an expensive task, but over the years we have all seen security incidents which can cost millions and cause companies or even banks to go out of business. (i.e. see https://www.ibm.com/ae-en/security/data-breach )
One word of caution: Simply complying with these security principles provides no guarantee of preventing successful attacks. Some attackers invest a lot of time thinking to come up with ever new methods and exploit attack vectors which may not have been considered before.
But following these security principles helps to reach the following objectives:
- Reducing the blast radius of an attack
- i.e. attackers may not gain access to all targeted services because of partitioning or may not be able to elevate to all permissions to gain access to all documents
- Increasing the time for a successful attack
- this also goes back to #1 as it becomes harder to gain sufficient access
- Increasing the chances of early detection (!!)
- More controls and audits usually mean more chances of raising triggers or errors along the way
- Improving forensic abilities after detection
- Better audit trails allow for more successful investigations
Security a first
Therefore, I strongly advise to implement the proper security controls from start. And this is not just because it is common knowledge among IT architects that changing running systems is more expensive than making sure that Security is a main pillar in the architecture from the start.
To take it one step further: security should be THE FIRST pillar to be implemented. What I mean by that is that, ideally, nothing gets deployed before all security measures have been put in place. Otherwise, it is easily possible to admit backdoors or other security issues in the foundation, purposefully or not, that remain undetected. The very first measure therefore should be to put Auditing in place. We will talk more about Auditing in a later article.
Contents
This series of articles will provide an overview on the most commonly cited security principles and concepts which are often used when talking about Separation of Duties – or even intermingled with it – and briefly clarify their meaning and relation. Expect a lot of keywords (not buzzwords though, I promise)
Principle of Least Privilege (POLP) Need to know
Delegation of Authority Separation of Privilege
Audit Trail Separation of Duties
– These articles will be released one by one over the next weeks and the links will then be updated one by one as well.
One more principle you should keep in mind when designing security: “KISS” – Keep it simple, stupid
As already mentioned in my article from 2017 (Separation of Duties (SoD) and role-based security conception in SQL Server), it is absolutely vital to keep the user experience as simple as possible. Anything “too much” of an effort (and that can be just “too many clicks”) will lead to users to try to find ways around it. And they will.
Example
A common example of that is the shared Admin account. Instead of having one elevated account per person, often especially in small shops, developers share one common privileged account. Among other things this renders Auditing almost useless as no one can really tell who did what.
Note
Separation of concerns (SoC)
Over time I have heard it being used when actually “Separation of Duties” was meant. SoC is NOT a security principle and rather a basic programming design principle which leads to modular (or “functional”) programming. Hopefully, this clears up this common mix-up.
Wikipedia-Article: https://en.wikipedia.org/wiki/Separation_of_concerns
Let me know if you find this series helpful and what else you want to hear about in the future.
Andreas
Special thanks to
Raul Garcia, former SQL Security PM and “honorable member for life” :) – your knowledge in Security and SQL Security helped me make sure to not overlook anything important and meet a certain quality bar ;)
Steven Gott, one of our most senior Security Engineers, for your critical viewpoints which help me look ahead, although I know I can’t possible mention everything.
Ralf Dietrich from Sarpedon Quality Lab® Germany for countless hours of brainstorming about secure architectures even while being based in separate time zones.
“Security Logo” by pixabay is licensed under CC0

by Contributed | Jan 16, 2021 | Technology
This article is contributed. See the original author and article here.

Introduction into security principles in the context of database systems
By Andreas Wolter
While many of us are practicing ‘social distancing’, and spend lots of time at home, I am finally finding the time to share some of the topics with the public that I have been working on since I joined Microsoft at the end of 2018.
In the recent years and with increasing frequency, one of the asks in terms of Security to the SQL Engine On-Prem as well as SQL Azure Database has been coming up with solutions to help accomplish “Separation of Duties”. This is a good thing, because it reassures my point of view that Separation of Duties is becoming increasingly important in IT and specifically Cloud-based systems.
On the other hand, we noticed that there is not a broad understanding in the technical community yet as to what Separation of Duties (aka SoD) really means and how it can be accomplished today. It occurs to me that the understanding is often vague and sometimes even contradicting depending on who you ask. It might therefore help to provide some context and guidance on what SoD really is and how it relates to other commonly referenced security principles that have been established over the last decades in IT.
If you are not already an expert in IT security, I hope that you will find this series useful.
Intro: Motivation
Security principles in information technology or cybersecurity (I won’t touch on physical security in these articles) exist as guidelines to assist design and decision processes in architecture, implementation, and reactive procedures when incidents happen. The purpose is to help designing for security in the first place, by using common proven patterns, and to be able to effectively assess a systems security.
Building secure systems from the start can be an expensive task, but over the years we have all seen security incidents which can cost millions and cause companies or even banks to go out of business. (i.e. see https://www.ibm.com/ae-en/security/data-breach )
One word of caution: Simply complying with these security principles provides no guarantee of preventing successful attacks. Some attackers invest a lot of time thinking to come up with ever new methods and exploit attack vectors which may not have been considered before.
But following these security principles helps to reach the following objectives:
- Reducing the blast radius of an attack
- i.e. attackers may not gain access to all targeted services because of partitioning or may not be able to elevate to all permissions to gain access to all documents
- Increasing the time for a successful attack
- this also goes back to #1 as it becomes harder to gain sufficient access
- Increasing the chances of early detection (!!)
- More controls and audits usually mean more chances of raising triggers or errors along the way
- Improving forensic abilities after detection
- Better audit trails allow for more successful investigations
Security a first
Therefore, I strongly advise to implement the proper security controls from start. And this is not just because it is common knowledge among IT architects that changing running systems is more expensive than making sure that Security is a main pillar in the architecture from the start.
To take it one step further: security should be THE FIRST pillar to be implemented. What I mean by that is that, ideally, nothing gets deployed before all security measures have been put in place. Otherwise, it is easily possible to admit backdoors or other security issues in the foundation, purposefully or not, that remain undetected. The very first measure therefore should be to put Auditing in place. We will talk more about Auditing in a later article.
Contents
This series of articles will provide an overview on the most commonly cited security principles and concepts which are often used when talking about Separation of Duties – or even intermingled with it – and briefly clarify their meaning and relation. Expect a lot of keywords (not buzzwords though, I promise)
Principle of Least Privilege (POLP) Need to know
Delegation of Authority Separation of Privilege
Audit Trail Separation of Duties
– These articles will be released one by one over the next weeks and the links will then be updated one by one as well.
One more principle you should keep in mind when designing security: “KISS” – Keep it simple, stupid
As already mentioned in my article from 2017 (Separation of Duties (SoD) and role-based security conception in SQL Server), it is absolutely vital to keep the user experience as simple as possible. Anything “too much” of an effort (and that can be just “too many clicks”) will lead to users to try to find ways around it. And they will.
Example
A common example of that is the shared Admin account. Instead of having one elevated account per person, often especially in small shops, developers share one common privileged account. Among other things this renders Auditing almost useless as no one can really tell who did what.
Note
Separation of concerns (SoC)
Over time I have heard it being used when actually “Separation of Duties” was meant. SoC is NOT a security principle and rather a basic programming design principle which leads to modular (or “functional”) programming. Hopefully, this clears up this common mix-up.
Wikipedia-Article: https://en.wikipedia.org/wiki/Separation_of_concerns
Let me know if you find this series helpful and what else you want to hear about in the future.
Andreas
Special thanks to
Raul Garcia, former SQL Security PM and “honorable member for life” :) – your knowledge in Security and SQL Security helped me make sure to not overlook anything important and meet a certain quality bar ;)
Steven Gott, one of our most senior Security Engineers, for your critical viewpoints which help me look ahead, although I know I can’t possible mention everything.
Ralf Dietrich from Sarpedon Quality Lab® Germany for countless hours of brainstorming about secure architectures even while being based in separate time zones.
“Security Logo” by pixabay is licensed under CC0

by Contributed | Jan 16, 2021 | Technology
This article is contributed. See the original author and article here.
Paralyzed in an accident from the waist down, Arjun* thought he would never walk again.
However, the 30-year-old, backed by his loved ones and a generous community, soon turned to a team of technologists and scientists, including MVP Praveen Srivatsa, for a second chance at life. The result is an impressive feat: an exoskeleton powered by Microsoft technologies which restores mobility to those without it.
Praveen, a six-time MVP titleholder from Bangalore who served as the team CTO, says it was Arjun’s relatives who noted the potential of exoskeletons but their prohibitive price point. “Moreover, those exoskeletons could not help patients with an injury higher up the spinal cord due to lack of upper body strength,” he says. Not one to give up, the family rallied a team and raised more than $1 million to build a patented third-generation exoskeleton that could help people with any kind of injury to stand up and walk again.
The device is a robotic system powered by a NI cRIO controller and driven by a Windows Surface tablet. The software platform leverages Azure Web, Storage, Azure SQL and Azure Functions. The robotic device streams IoT data through the Azure IoT Hub and Stream Analytics makes it possible to monitor the robot behavior in real-time. The actual gait profile and customized rehabilitation are controlled by a proprietary machine learning algorithm that is being trained on Azure ML.
The device is currently in a premier hospital in Bangalore for patient rehabilitation and data collection for different types of injuries. “Our vision is to be able to provide highly personalized rehabilitation from different types of injuries and enable people from different walks of life to not only to get back their mobility, but also to be able to lead their own life with dignity,” Praveen says. “And we wish to do this in a very affordable manner so that it can impact the lives of a much wider base of people affected by different injuries.”
Praveen says the exoskeleton team enjoyed large community support from the early days of the project. Doctors started stepping in to provide guidance on how to rehabilitate patients with different injuries, and retired officials came forward to provide insights on how the government could support this initiative on a larger scale.
Moreover, institutes like IIIT Bangalore came forward to assist on the research around machine learning and gait algorithms. “In fact, the technology community stepped in and offered crowdsourced data collection for human gait to enable us to create a gait profile baseline for our algorithms,” Praveen says.
“This initiative could not have progressed at this pace without the strong support of the community around us,” he says.
Editor’s Note: Microsoft MVP has used an alias for the patient to protect their anonymity.

by Contributed | Jan 16, 2021 | Technology
This article is contributed. See the original author and article here.

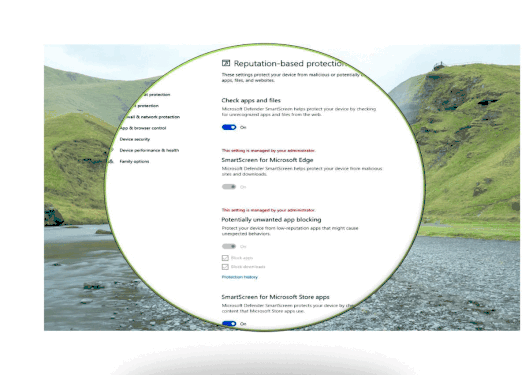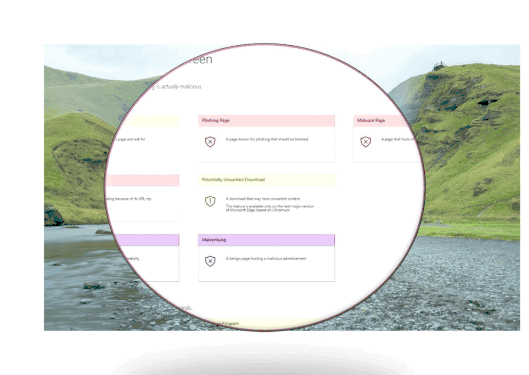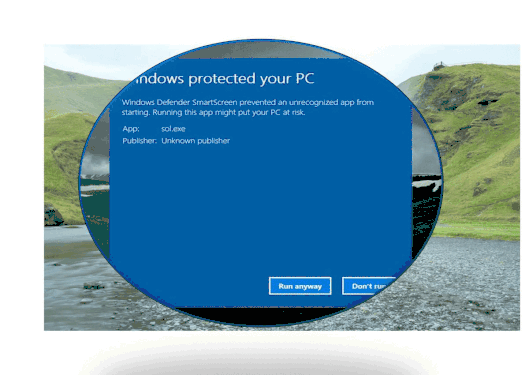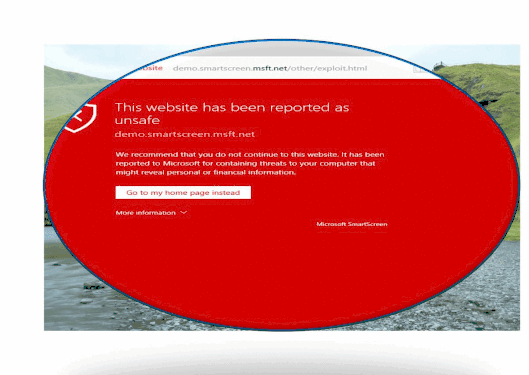
SmartScreen has become a part of Windows 10 OS, it was named as Windows Defender SmartScreen. It is useful to protect not just Edge, Internet Explorer browsers but also other applications such as third-party browsers, Email Client and Apps from malicious Web link attack, malicious Web download threat. Let us have a quick look into SmartScreen functionalities:
- Anti-phishing and anti-malware support. Microsoft Defender SmartScreen helps to protect users from sites that are reported to host phishing attacks or attempt to distribute malicious software.
- Prevent drive-by attacks. Drive-by attacks are web-based attacks that tend to start on a trusted site, targeting security vulnerabilities in commonly used software. Because drive-by attacks can happen even if the user does not click or download anything on the page, the danger often goes unnoticed.
- Reputation-based URL and app protection. Microsoft Defender SmartScreen evaluates a website’s URLs to determine if they’re known to distribute or host unsafe content. It also provides reputation checks for apps, checking downloaded programs and the digital signature used to sign a file. If a URL, a file, an app, or a certificate has an established reputation, users won’t see any warnings. If, however, there’s no reputation, the item is marked as a higher risk and presents a warning to the user.
- Improved heuristics and diagnostic data. Microsoft Defender SmartScreen is constantly learning and endeavoring to stay up to date, so it can help to protect you against potentially malicious sites and files.
- Blocking URLs associated with potentially unwanted applications. software that can cause your machine to run slowly, display unexpected ads, or at worst, install other software
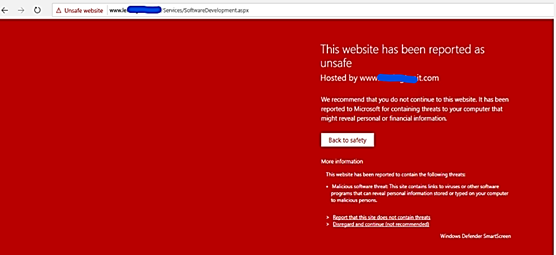
Website blacklist block example
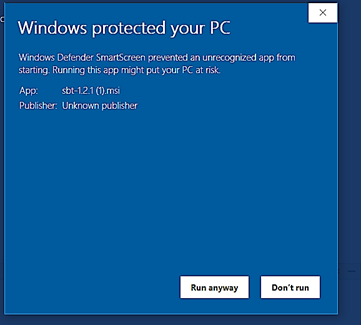
App blocked by Defender SmartScreen example:
Starting with Windows 10 version 1703 to 2004 you will configure SmartScreen directly by Windows Defender SmartScreen GPO (not through Edge GPO anymore): Administrative TemplatesWindows ComponentsWindows Defender SmartScreenMicrosoft Edge
Submit File for Whitelisting to Microsoft Security Intelligence
You may experience false positive block or warning by Defender SmartScreen when accessing in-house Web App’s URL or Website URLs and you need to whitelist those URLs.
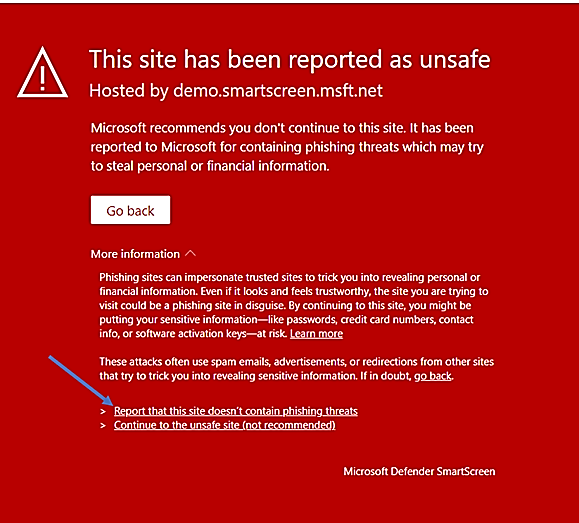
General rule, there will usually be a direct link in the product app notification for error reporting to Microsoft Security Support. In case of Defender SmartScreen, the link shown in the notification as seen here:
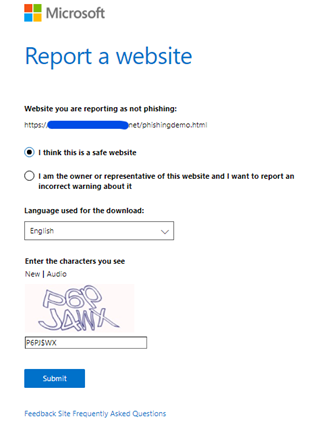
You should provide the information to the Defender SmartScreen Support Team if your Site gets a false-positive alarm of blockage or gets a false positive warning of unknow web site, …, the following screenshot shown the report’s content:
For download block or download warning report of false-positive, you could manually submit the sample files by accessing the WDSI Website and choose to submit as an enterprise user or a developer user. (You could also submit file as a home user too.)
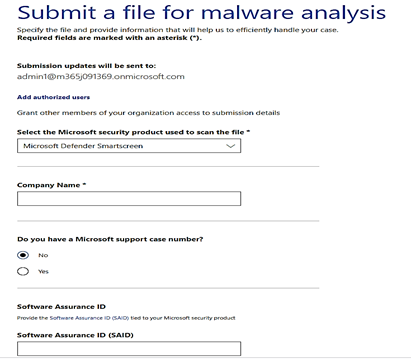
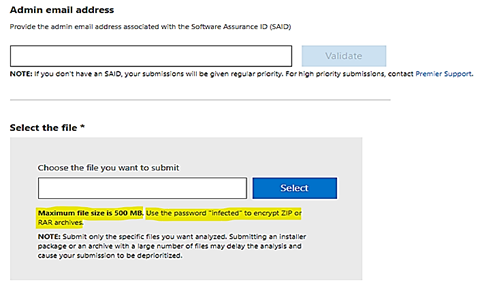
- To upload sample file with size more than 500MB, you could compress it by Zip or RAR archive.
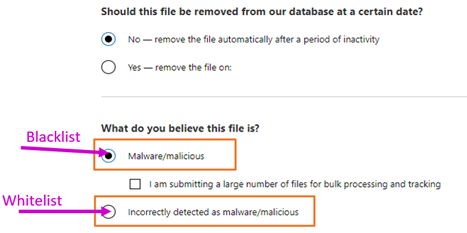
- You could report file for Blacklist to block access to it or report file for Whitelist to allow access.
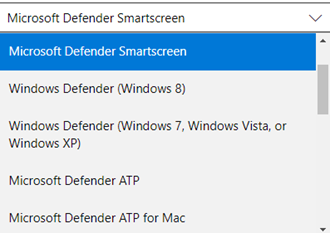
- You could submit filtering request for almost any of Microsoft’s software and service as per the dropped down list of the above Form:
Microsoft goal is to minimize false warnings or blocks. In the rare case of a false warning, Microsoft offered a web-based feedback system to help users and website owners report any errors as quickly as possible. These reports are verified by the support team and mistakes are corrected. Enterprise Premier Customer will get the highest priority in response time.
Flash Player should be removed from the Sites after December 2020
- Flash will not be disabled by default from Microsoft Edge classic (Edge legacy) or Internet Explorer 11 prior to its removal by December of 2020.
- Group policies are available for enterprise admins and IT pros to change the Flash behavior
Flash will be completely removed from all browsers by December 31, 2020, via Windows Update. Companies reliant on Flash for development and playback of content are encouraged to remove the dependency on Adobe Flash prior to December 2020.
Reference:

by Contributed | Jan 15, 2021 | Technology
This article is contributed. See the original author and article here.
Surface tools that assist IT admins with core security, management, and diagnostic tasks have been updated with support the latest enterprise devices. Updated tools include:
- Surface Diagnostic Tool for Business. Eases support experience through Surface Diagnostics. This tool provides a full suite of diagnostic tests and software repairs to quickly investigate, troubleshoot, and resolve hardware, software, and firmware issues with Surface devices. Note that Surface Hub Hardware Diagnostics is already built into the Teams OS device for easier troubleshooting and is available in Microsoft Stores for download.

Built in support
In addition, the latest versions of Surface Data Eraser, Surface Brightness Control , Surface Asset Tag already have built in support for Surface Pro 7+.
Download
You can download these and other tools from Surface Tools for IT, available on the Microsoft Download Center. Surface Pro 7+ and Surface Hub 2S 85” are available for purchase now.




Recent Comments