by Contributed | Jan 13, 2021 | Technology
This article is contributed. See the original author and article here.
We are happy to announce the availability of the Microsoft Defender for Identity sensor for Active Directory Federation Server (AD FS) after successfully piloting the feature with customers in Private Preview over the last few months.
Advanced identity protection can help prevent lateral movement by attackers
Microsoft Defender for Identity is a cloud-based security solution that leverages your on-premises Active Directory signals to identify, detect, and investigate advanced threats, compromised identities, and malicious insider actions directed at your organization.
Until now, Microsoft Defender for Identity has protected domain controllers in either on-premises or hybrid environments. By installing the sensor on the domain controller, you are gaining access to the core value from our product:
- Attack surface reduction – Increases on-premises identity resiliency against malicious intent – both internal and external.
- Detect malicious attempts to compromise on-premises identities, move laterally within your organizations and gain persistency in your Active Directory environment.
- Investigate the activities of identities and gain further insights into their behaviors to respond to compromised identities in order to stop further expansion across domains (when you use Microsoft Defender for Identity through the Microsoft Cloud App Security or Microsoft 365 Security Center console experiences)
While Active Directory continues to play a major role in most organizations, we must always look to how we can enhance our identity protection capabilities through the power of the cloud. Our products have constantly evolving roadmaps that are built from the fantastic work our security research teams carry out. Continuous improvement based on customer feedback and the evolving threat landscape are a key part of helping to keep our customers secure and protected.
AD FS enables federated Identity and access management by securely sharing digital identity and access rights across security and enterprise boundaries. While we recommend customers upgrade their existing on-premises AD FS systems to Azure AD to gain the protections that a cloud identity solution can provide, we understand that some customers are on different journeys – which is why we are introducing today new capabilities from Microsoft Defender for Identity to protect your AD FS environment.
Best practices to reduce your attack surface from Solorigate with AD FS
As we have seen in recent events related to Solorigate, on-premises compromise can propagate to the cloud. We plan our security with an “assume breach” philosophy and layer in defense-in-depth protections and controls to stop attackers sooner when they do gain access. To protect privileged accounts, we recommend best practices such as those outlined here, and implementing Privileged Access Workstations (PAW).
With credential compromise still being one of the most common entry methods for a potential attacker, services like AD FS are often a target for bad actors given that it’s a critical element of identity and access management infrastructure. We encourage customers to adopt best practices like enabling MFA and general credential hygiene because credential theft is a common entry point.
Additional information on Solorigate and guidance for security admins, operations and hunters can be found at our Solorigate resource center.
Given what we know about the importance of AD FS, let’s explore the impact of introducing an AD FS sensor as part of Microsoft Defender for Identity’s capabilities:
Protect AD FS from on-premises attacks
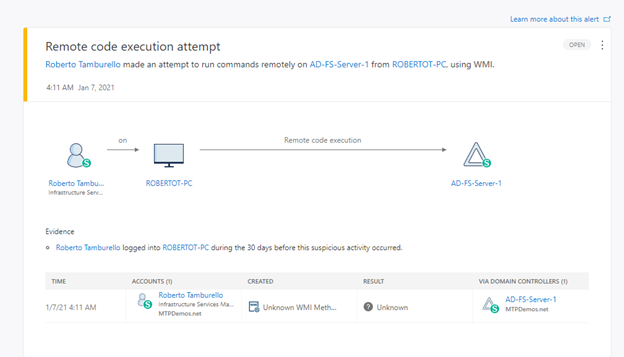
Much like the existing domain controller sensor, Microsoft Defender for Identity’s new capability for AD FS provides visibility into advanced persistent threats, detecting attempts to compromise the AD FS server through techniques such as remote code execution or attempts to install malicious services.

(figure 1. Remote code execution attempt against AD FS server)
Microsoft Defender for Identity detections are better with AD FS
With the new sensor, there are two detections that immediately take advantage of the information and signals being captured from AD FS. These are:
- Suspected Brute Force attack (LDAP) and
- Account enumeration reconnaissance
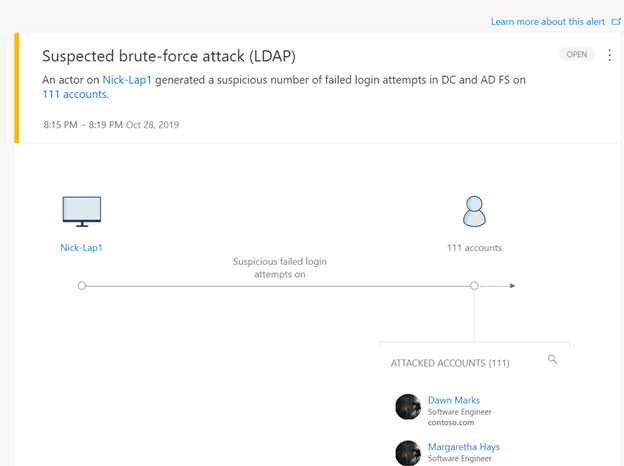
(figure 2. Brute force attack with failed logons from DC and AD FS)
Microsoft Defender for Identity activities are better with AD FS
Correlating login data from both AD FS sensor and Active Directory sensors enables Microsoft Defender for Identity to analyze further user behavior. For example, some authentication activities, such as failed logins, are visible only to the AD FS server. On other successful logins, Microsoft Defender for Identity can now correlate login information from Active Directory with data from the AD FS server, including whether multi factor authentication occurred when the request was made, the user context, and more.
Here is an example of the enrichment mentioned above in user activity log in Microsoft Defender for Identity before and after the AD FS sensor is installed:
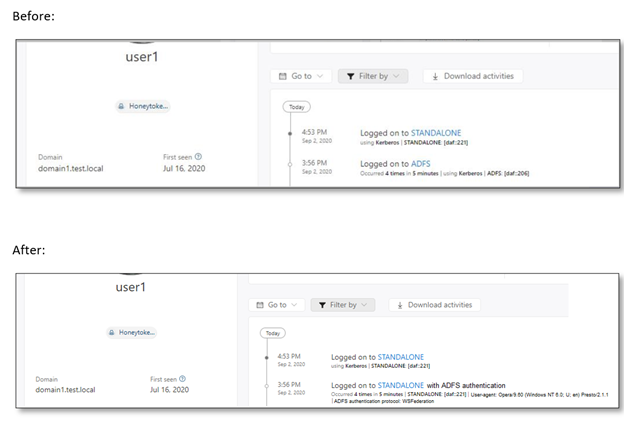
(figure 3. User activity log before and after AD FS sensor has been installed)
The new benefit we are adding enhances Microsoft Defender for Identity by introducing the ability to see the actual device the account was logged into with additional context. This will provide further enrichment in a similar way that RADIUS information provides to Microsoft Defender for Identity when contributing VPN login activities. More information from identity sources makes for more context and as a result, better detections.
Tag the AD FS as a sensitive entity further enhances protection
After installing an AD FS sensor, the AD FS servers in the Microsoft Defender for Identity portal will be automatically tagged as sensitive. This extends functionality that already marks other high value asset servers as sensitive, such as DHCP servers, DNS servers, Microsoft Exchange servers and Certificate Authority servers.
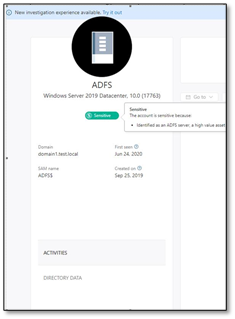
(figure 4. AD FS asset tagged as sensitive)
What’s next?
The requirements for installing the AD FS sensor are:
- Windows Server 2016 or later (required for the appropriate audit logs)
- Domain controller is not installed on the same server as AD FS
- Audit logs enabled on the AD FS server
If you meet these requirements, download the latest deployment package from the sensor configuration page.
To learn more about the requirements and how to enable audit logs, click here.
Get started today
Are you just starting your Microsoft Defender for Identity journey? Begin a trial of Microsoft 365 Defender to experience the benefits of the most comprehensive, integrated, and secure threat protection solution for your organization.
Join the Microsoft Defender for Identity community for the latest updates and news about Identity Security Posture Management assessments, detections and other updates.
Once again, further information and information for security admins, operations and hunters on Solorigate can be found at our Solorigate resource center
by Scott Muniz | Jan 13, 2021 | Security, Technology
This article is contributed. See the original author and article here.
This Analysis Report uses the MITRE Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK®) framework. See the ATT&CK for Enterprise framework for all referenced threat actor tactics and techniques.
The Cybersecurity and Infrastructure Security Agency (CISA) is aware of several recent successful cyberattacks against various organizations’ cloud services. Threat actors are using phishing and other vectors to exploit poor cyber hygiene practices within a victims’ cloud services configuration. The information in this report is derived exclusively from several CISA incident response engagements and provides the tactics, techniques, and procedures; indicators of compromise (IOCs) that CISA observed as part of these engagements; and recommended mitigations for organization to strengthen their cloud environment configuration to protect against, detect, and respond to potential attacks.
For a downloadable copy of IOCs, see AR21-013A.stix.
Note: the activity and information in this Analysis Report is not explicitly tied to any one threat actor or known to be specifically associated with the advanced persistent threat actor attributed with the compromise of SolarWinds Orion Platform software and other recent activity.
Background
These types of attacks frequently occurred when victim organizations’ employees worked remotely and used a mixture of corporate laptops and personal devices to access their respective cloud services. Despite the use of security tools, affected organizations typically had weak cyber hygiene practices that allowed threat actors to conduct successful attacks.
Technical Details
The cyber threat actors involved in these attacks used a variety of tactics and techniques—including phishing, brute force login attempts, and possibly a “pass-the-cookie” attack—to attempt to exploit weaknesses in the victim organizations’ cloud security practices.
Phishing
CISA observed cyber threat actors using phishing emails with malicious links to harvest credentials for users’ cloud service accounts (Phishing: Spearphishing Link [T1566.002]). The cyber actors designed emails that included a link to what appeared to be a secure message and also emails that looked like a legitimate file hosting service account login. After a targeted recipient provided their credentials, the threat actors then used the stolen credentials to gain Initial Access [TA0001] to the user’s cloud service account (Valid Accounts [T1078]). CISA observed the actors’ logins originating from foreign locations (although the actors could have been using a proxy or The Onion Router (Tor) to obfuscate their location). The actors then sent emails from the user’s account to phish other accounts within the organization. In some cases, these emails included links to documents within what appeared to be the organization’s file hosting service.
In one case, an organization did not require a virtual private network (VPN) for accessing the corporate network. Although their terminal server was located within their firewall, due to remote work posture, the terminal server was configured with port 80 open to allow remote employees to access it—leaving the organization’s network vulnerable. The threat actor attempted to exploit this by launching brute force login attempts (Brute Force [T1110]).
Forwarding Rules
In several engagements, CISA observed threat actors collecting sensitive information by taking advantage of email forwarding rules, which users had set up to forward work emails to their personal email accounts (Email Collection: Email Forwarding Rule [T1114.003]).
Modified Forwarding
In one case, CISA determined that the threat actors modified an existing email rule on a user’s account—originally set by the user to forward emails sent from a certain sender to a personal account—to redirect the emails to an account controlled by the actors. The threat actors updated the rule to forward all email to the threat actors’ accounts.
Keyword Search Rule
Threat actors also modified existing rules to search users’ email messages (subject and body) for several finance-related keywords (which contained spelling mistakes) and forward the emails to the threat actors’ account.
New Rule Creation and Forwarding
In addition to modifying existing user email rules, the threat actors created new mailbox rules that forwarded certain messages received by the users (specifically, messages with certain phishing-related keywords) to the legitimate users’ Really Simple Syndication (RSS) Feeds or RSS Subscriptions folder in an effort to prevent warnings from being seen by the legitimate users.
Authentication
CISA verified that the threat actors successfully signed into one user’s account with proper multi-factor authentication (MFA). In this case, CISA believes the threat actors may have used browser cookies to defeat MFA with a “pass-the-cookie” attack (Use Alternate Authentication Material: Web Session Cookie [T1550.004]).
The threat actors attempted brute force logins (Brute Force [T1110]) on some accounts. However, this activity was not successful. This thwarted attempt was due, in part, to the threat actors not guessing a correct username/password combination, as well as the organization’s use of MFA to access their cloud environment.
CISA recommends the following steps for organizations to strengthen their cloud security practices.
- Implement conditional access (CA) policies based upon your organization’s needs.
- Establish a baseline for normal network activity within your environment.
- Routinely review both Active Directory sign-in logs and unified audit logs for anomalous activity.
- Enforce MFA.
- Routinely review user-created email forwarding rules and alerts, or restrict forwarding.
- Have a mitigation plan or procedures in place; understand when, how, and why to reset passwords and to revoke session tokens.
- Follow recommend guidance on securing privileged access.
- Consider a policy that does not allow employees to use personal devices for work. At a minimum, use a trusted mobile device management solution.
- Resolve client site requests internal to your network.
- Consider restricting users from forwarding emails to accounts outside of your domain.
- Allow users to consent only to app integrations that have been pre-approved by an administrator.
- Audit email rules with enforceable alerts via the Security and Compliance Center or other tools that use the Graph API to warn administrators to abnormal activity.
- Implement MFA for all users, without exception.
- Conditional access should be understood and implemented with a zero-trust mindset.
- Ensure user access logging is enabled. Forward logs to a security information and event management appliance for aggregation and monitoring so as to not lose visibility on logs outside of logging periods.
- Use a CA policy to block legacy authentication protocols.
- Verify that all cloud-based virtual machine instances with a public IP do not have open Remote Desktop Protocol (RDP) ports. Place any system with an open RDP port behind a firewall and require users to use a VPN to access it through the firewall.
- Focus on awareness and training. Make employees aware of the threats—such as phishing scams—and how they are delivered. Additionally, provide users training on information security principles and techniques as well as overall emerging cybersecurity risks and vulnerabilities.
- Establish blame-free employee reporting and ensure that employees know who to contact when they see suspicious activity or when they believe they have been a victim of a cyberattack. This will ensure that the proper established mitigation strategy can be employed quickly and efficiently.
- Ensure existing built-in filtering and detection products (e.g., those for spam, phishing, malware, and safe attachments and links are enabled.
- Organizations using M365 should also consider the following steps.
- Assign a few (one to three) trusted users as electronic discovery (or eDiscovery) managers to conduct forensic content searches across the entire M365 environment (Mailboxes, Teams, SharePoint, and OneDrive) for evidence of malicious activity.
- Disable PowerShell remoting to Exchange Online for regular M365 users. Disabling for non-administrative users will lower the likelihood of a compromised user account being used to programmatically access tenant configurations for reconnaissance.
- Do not allow an unlimited amount of unsuccessful login attempts. To configure these settings, see password smart lockout configuration and sign-in activity reports.
- Consider using a tool such as Sparrow or Hawk—open-source PowerShell-based tools used to gather information related to M365—to investigate and audit intrusions and potential breaches.[1][2]
Resources
January 13, 2021: Initial Version
by Contributed | Jan 13, 2021 | Technology
This article is contributed. See the original author and article here.
We are looking for people who have an inspiring story to share about why they got certified and how it impacted their life, career, or personal development. We’ll be featuring select stories starting at the next Microsoft Ignite March 2-4, 2021.
We know that Microsoft Certification can help you build confidence, get recognized as a leader, and unlock new opportunities. But we want to hear it from you. If you achieved a Microsoft Certification (fundamentals, role-based, or specialty), tell us your experience and how it’s helped you. What did you do to prepare? How has being certified changed your career? What new insights did you gain after becoming certified? Your video should be under 3 minutes.
Is English not your native language? No problem! We would love for you to submit your video in your native language.
Things to consider
- Make sure to start by introducing yourself – include your name and the fact that you’re “proud to be certified.”
- When you record your video, make sure you have good, even lighting in front of you so we can clearly see your face, keep your camera at eye level (you don’t want to be looking up or down), use an external microphone if you have one, and turn off anything wherever you’re recording that could be creating additional noise like your cell phone, radios, fans, etc.
- Keep your background clutter free.
- Keep videos to a maximum of 3 minutes in length. We know you’re excited about your certifications, but give us the highlights and we can always follow up with you for more information.
- And maybe most importantly, be yourself. Tell us what excites you in your own words or even your native language – and have some fun with it!
We are excited to hear your stories and highlight some of you at the next Microsoft Ignite on March 2-4, 2021. Make sure to submit your video prior to January 31, 2021 at 11:59pm Pacific Time.
Share your story today!
by Scott Muniz | Jan 13, 2021 | Security, Technology
This article is contributed. See the original author and article here.
CISA is aware of several recent successful cyberattacks against various organizations’ cloud services. Threat actors used a variety of tactics and techniques, including phishing and brute force logins, to attempt to exploit weaknesses in cloud security practices.
In response, CISA has released Analysis Report AR21-013A: Strengthening Security Configurations to Defend Against Attackers Targeting Cloud Services which provides technical details and indicators of compromise to help detect and respond to potential attacks.
CISA encourages users and administrators to review AR21-013A and apply the recommendations to strengthen cloud environment configurations.


Recent Comments