by Contributed | Apr 28, 2021 | Technology
This article is contributed. See the original author and article here.
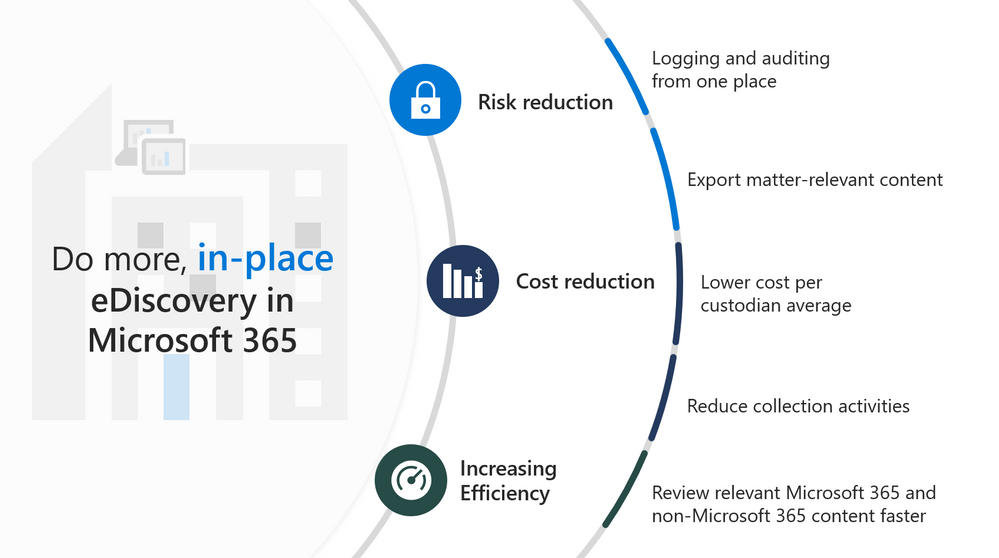
Watch this webinar to learn about what’s new in Advanced eDiscovery, including enhancements to collections and review set, as well as a new predictive coding module. You’ll also learn about what features are coming next in Advanced eDiscovery.

Watch on-demand
Resources:
Overview of the Advanced eDiscovery solution in Microsoft 365 – Microsoft 365 Compliance | Microsoft Docs
Technical Sessions
This webinar was presented on April 7, 2021, and the recording can be found here .
Attached to this post are:
- The FAQ document that summarizes the questions and answers that came up over the course of both webinars.
- A PDF copy of the presentation.
Thanks to those of you who participated during the two sessions and if you haven’t already, don’t forget to check out our resources available on the Tech Community.
Thanks!
@Robin_Baldwin on behalf of the MIP and Compliance CXE team

by Contributed | Apr 28, 2021 | Technology
This article is contributed. See the original author and article here.

Call Summary:
Topics covered in this month’s community call include – Make your Power Apps sessions persistent when switching Microsoft Teams tabs! (Making your Teams mobile and desktop power apps off-line capable), Power Apps Custom Functions Library (sharing your great work – find, use, submit samples), Make your Power Apps user experience awesome with Gestalt design principles (create visually compelling model driven apps), and Recent Power Apps News and Community Contributions. This session included Q&A in chat. The call was hosted by Todd Baginski (Canviz). Demo presenters include Hardit Bhatia, Matthew Devaney, April Dunnam, Hiro Nagao, Geetha Sivasailam, Hugo Bernier, Anton Robbins and Rory Neary. Recorded on April 21, 2021. Thank for attending the call or viewing it on demand.
Demos:
Make your Power Apps sessions persistent when switching Microsoft Teams tabs! – tired of losing data captured in your Microsoft Teams-based Power Apps when you leave the app to respond to a chat message or go to another channel? Learn how to store data and then reload data when restarting your Power App to effectively achieve session data persistence. Hint – make your app off-line capable. Works on desktop too!
Power Apps Custom Functions Library – now that it is possible to create user defined custom functions in Power Apps the DRY principle applies, so let’s share! The custom functions library is the new Power Platform samples repository. Find, use, and submit custom functions, Power app, Power Automate and Power Virtual Agents samples. Not sure where to start? Community contributor training offered at PnP | Sharing Is Caring
Make your Power Apps user experience awesome with Gestalt design principles – how you layout objects in your Power Apps UI is a mixture of art, industry standard, and Gestalt. In Power Apps, objects are in a 2D frame. In this demo, you will understand how and why using Gestalt principles in app design matters in a world where users do not typically read manuals and adoption is largely based on visual perceptions.
Recent News & Cool Stuff:
Actions:
Learn more:
Stay connected:
by Contributed | Apr 28, 2021 | Technology
This article is contributed. See the original author and article here.
While recently working with a customer’s Governance Risk and Compliance team (GRC) the discussion pivoted to the ability to exempt Azure resources from policies or disable the policy to reflect the Secure Score correctly for their environment. GRC teams may want on a quarterly or monthly basis to produce a report of the exemptions to review and discuss or hand over to auditors looking to see the exemption story.
The Exemption capabilities in Azure Security Center utilize Azure Policy exemptions that have been around for a bit now. @Tom Janetscheck has written quite a bit about the capability and provided some unique Workflow automations around
Submitting a exemption via Logic App
Notifying an Exemption via Logic App
Both are very great workflow automations the GRC team can adopt at an enterprise. Your GRC team may be looking for an easy to pull report they could download around the exemptions and the azure resources to quickly audit findings.
Let’s examine a few ways you can pull this information within the Azure Portal, Azure Resource Graph, and use a new PowerShell Script to download a detailed report.
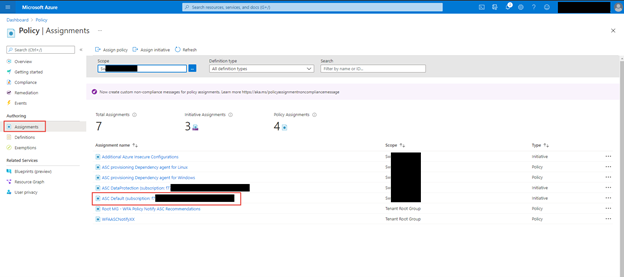
Azure Portal – Policy – Assignments blade
When you want a quick view of the exemptions for a particular subscription within the Azure Portal for Policy you can leverage the Assignments blade to list those exemptions. In addition, if you have written access you can update or create new exemptions as well.
Within the Azure Portal go to Policy and click on the Assignments blade, within there, click on ASC Default assignment.

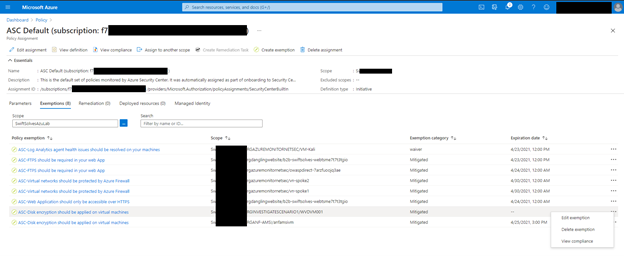
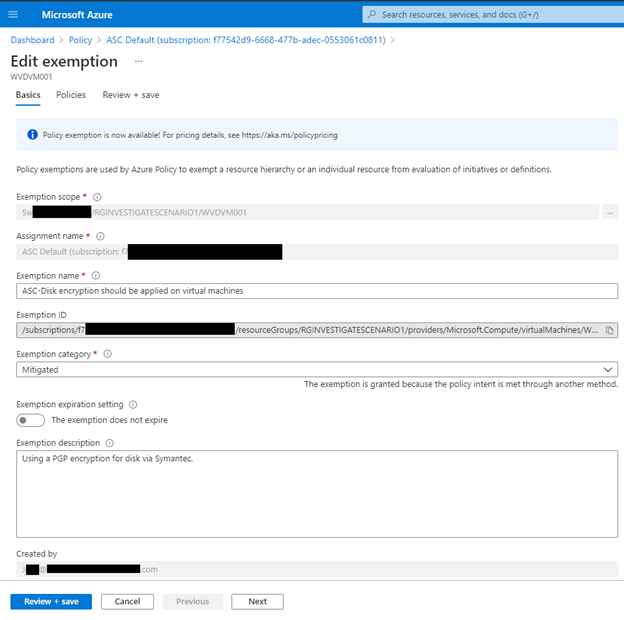
Click on the Exemptions Tab, if you have write access to policy assignments you can also click on the … and edit the exemption too see more details
Azure Resource Graph
Some of the exemption values are stored as data in Azure Resource Graph and specifically the securityresources table. If you are unfamiliar with the Azure Resource Graph the Azure Portal’s top search bar is also powered by it and helps return fast results. It is a great way to not invoke a GET Azure Resource API call for each Azure resource details and configurations as their state and information are stored here.
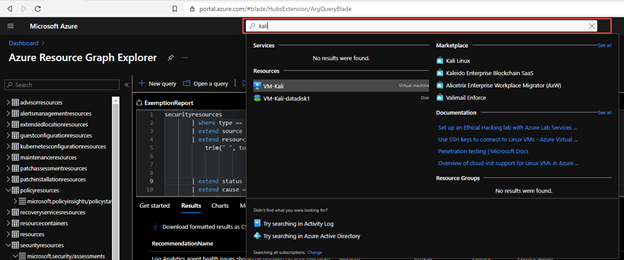
Within the table Azure does store some information around the ASC recommendations and their states, including the exemptions and policies disabled.
You can now run a KQL query in Azure Resource Graph to generate a report.
securityresources
| where type == "microsoft.security/assessments"
| extend source = tostring(properties.resourceDetails.Source)
| extend resourceId =
trim(" ", tolower(tostring(case(source =~ "azure", properties.resourceDetails.Id,
source =~ "aws", properties.resourceDetails.AzureResourceId,
source =~ "gcp", properties.resourceDetails.AzureResourceId,
extract("^(.+)/providers/Microsoft.Security/assessments/.+$",1,id)))))
| extend status = trim(" ", tostring(properties.status.code))
| extend cause = trim(" ", tostring(properties.status.cause))
| extend assessmentKey = tostring(name)
| where cause == "Exempt" or cause == "OffByPolicy"
| extend ResourceName = tostring(split(resourceId,'/')[8]), RecommendationName = tostring(properties.displayName), Source = properties.resourceDetails.Source, StatusCause = tostring(properties.status.cause), StatusDescription = properties.status.description, RecommendationSeverity = tostring(properties.metadata.severity)
| project RecommendationName, RecommendationSeverity, ResourceName, StatusCause, StatusDescription, resourceGroup, Source, subscriptionId
| sort by RecommendationSeverity, RecommendationName
For a comprehensive and better visual listing experience, be sure to set the query to run on all Azure Subscriptions and Formatted Results turned on. You can then download the report to a CSV file for the auditors or for review of the exceptions and disabled policies.
You can find the KQL query here in the Azure Security Center GitHub repo.
Generate-ExemptionReport.ps1
For a more comprehensive and detailed report that includes Notes in the exemption, expiration dates for exemptions, and who created the exemptions you can now utilize the following PowerShell script which executes across Azure Subscriptions and invokes an API to get the details:
Microsoft.Authorization/policyExemptions?api-version=2020-07-01-preview
To use the script you can download here from the GitHub Repo and open PowerShell.
Within PowerShell be sure to log into an Azure using Connect-AzAccount and using the login of someone who has a large amount of reader access across your Azure enterprises subscriptions. You may see some errors please ignore for now as the script will be tuned over time to support additional scenarios.
The end result is nicely generated CSV with all the details around the exemptions that can be imported into Excel, PowerBI, or other data visualization products.
As an example you can import into into Excel, Open a new Excel sheet and got to the ‘Data’ tab and use the button ‘From Test/CSV’
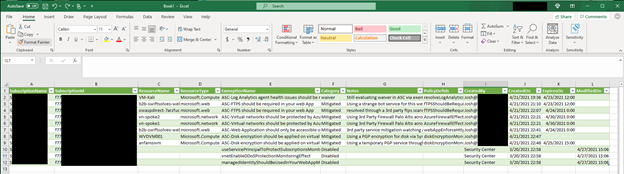
Once imported you can pivot and filter as needed
In this article you explored several ways to examine and generate an exemption report. You can use the Azure Portal – Policy – Assignments blade to quickly view all the Exemptions. You can use the Azure Resource Graph and a KQL Query to generate a simplified exemption and policy disable report. Finally you can use a PowerShell script to generate a detailed exemption and policy disable report that includes notes, expiration date and time, and who created the exemption. These reports can be used in a quarterly or month basis for you GRC team to review and discuss or handed over to auditors looking to see the exemption story.
Special thanks to:
@Yuri Diogenes for reviewing this post
by Contributed | Apr 28, 2021 | Technology
This article is contributed. See the original author and article here.
Gain rich control over the approval, scheduling, and protection of content delivered from Windows Update thanks to the new Microsoft Graph APIs, now available in public preview! Powered by the Windows Update for Business deployment service, these APIs enable IT professionals and app developers to:
- Approve and schedule specific feature updates to be delivered from Windows Update – including skipping or not taking feature updates.
- Stage deployments over a period of days or weeks using rich expressions (ex: deploy 20H2 to 500 devices per day, beginning on May 11, 2021)
- Bypass pre-configured Windows Update for Business policies to immediately deploy a security update across your organization.
- Deliver safer update results by leveraging automatic pilots for any deployment.
Microsoft Graph is the gateway to Microsoft 365, making it easy to build apps that span organizations, users, and devices. By connecting deployment service capabilities with Microsoft Graph, app developers can easily build rich update management tools and extend these experiences with contextual user data (such as leveraging a user’s calendar data when scheduling an update).
And the best part is, if you have one of the following Windows or Microsoft 365 subscriptions, you can start using the deployment service today!
- Windows 10 Enterprise E3 or E5 (included in Microsoft 365 F3, E3, or E5)
- Windows 10 Education A3 or A5 (included in Microsoft 365 A3 or A5)
- Windows Virtual Desktop Access E3 or E5
- Microsoft 365 Business Premium
What is the Windows Update for Business deployment service?
The Windows Update for Business deployment service is the bridge between you and Windows Update. It allows you to approve and schedule content approvals directly through a service-to-service architecture.

Here is a common scenario for the deployment service:
- Using a management tool, you select the target devices and approve content to be deployed. This tool may be PowerShell, a Microsoft Graph app, or a complete endpoint management solution such as Microsoft Endpoint Manager.
- The tool conveys your approval, scheduling details, and device selection to the deployment service.
- The deployment service processes the content approval and compares it with previously approved content. Final update applicability is determined and conveyed to Windows Update, which then offers the approved content to devices on their next check for updates.
This service-to-service architecture complements existing Windows Update for Business policies while providing unique benefits:
- Update management now goes beyond the individual device – allowing you to easily understand what updates are applicable to your organization and how best to stage deployments.
- Reacting to update challenges is faster than ever before – whether you need to pause or accelerate a deployment.
- New features and capabilities are immediately delivered to all in-support Windows versions – no operating system servicing required.
The Windows Update for Business deployment service is an enterprise-grade solution that provides full control over managed content and is already certified compliant with several industry compliance standards, including: ISO 27001, FedRAMP High, HiTRUST, and SOC II.
Try the service today
With today’s public preview release, you can use the Windows Update for Business deployment service directly through the Microsoft Graph API and associated SDKs, as well as Azure PowerShell. If you’re an IT pro, you can leverage these APIs and SDKs within your in-house solutions. If you’re a management tool vendor, these APIs and SDKs can help you provide deployment service capabilities to your customers through multi-tenant apps.
To begin exploring the deployment service, we encourage you to use Microsoft Graph Explorer or a proven industry solution, such as Postman.
Using Microsoft Graph Explorer to interact with the deployment service
Microsoft Graph Explorer is a tool that makes it simple to make requests and see responses against Microsoft Graph. To begin using Microsoft Graph Explorer with the deployment service, sign in using your tenant.
Next, provide consent for Graph Explorer to access the deployment service on behalf of your organization. Click the settings gear icon next to your account after signing in and choose Permissions. Select WindowsUpdates.ReadWrite.All and then select the Consent action.
You are now ready to begin using the service. In the left pane, you will find several samples for Windows Updates. Start with a basic operation like list catalog entries.
 Interacting with the Windows Update for Business deployment service via Microsoft Graph Explorer
Interacting with the Windows Update for Business deployment service via Microsoft Graph Explorer
While you can immediately query for data provided by the deployment service—such as available content to deploy—querying for other content, such as deployments, will depend on what have been created for your tenant. You can use Microsoft Graph Explorer to explore the capabilities provided by the deployment service and understand how to incorporate these into your apps, including:
- Enroll in update management. Enroll devices in feature update management by setting the enrollmentUpdateCategory to feature. This will stop offering feature updates to enrolled devices until explicitly approved using the deployment service.
- Create deployment (expedited security update). If a new critical security update is released and you want to reach compliance as rapidly as possible, you can deploy the update as expedited and control settings like the number of days until devices are required to restart.
- Create deployment (rate-based gradual rollout). Stage a deployment over time so that devices are offered the feature update at regular intervals and according to a specified number of devices per offer.
- Create deployment (date-based gradual rollout). Stage a deployment over time so that devices are offered the update at regular intervals until all devices receive the update by a targeted end date/time. You may also use a start date/time with any deployment to control when to begin offering the update.
- Update deployment (replace monitoring rules). Apply monitoring rules to any deployment to detect a threshold of issues, such as number of rollbacks, and then pause the deployment or alert you to the problem.
To learn more about these operations and the associated capabilities, please see our Microsoft Graph API documentation.
Using Postman to interact with the deployment service
Like Graph Explorer, Postman is an easy tool for interacting with the deployment service and a great way to familiarize yourself with the supported operations. For detailed instructions, see Use Postman with the Microsoft Graph API.
Note
When you reach step 3.9, follow the procedure to add and consent Delegated Permissions for WindowsUpdates.ReadWrite.All.
When you reach step 6, expand the Windows Updates (beta) folder of the Postman collection to see operations you can perform with the deployment service.
|
Select a request such as List catalog entries, ensure any required variables are populated, then click Send to interact with the service.
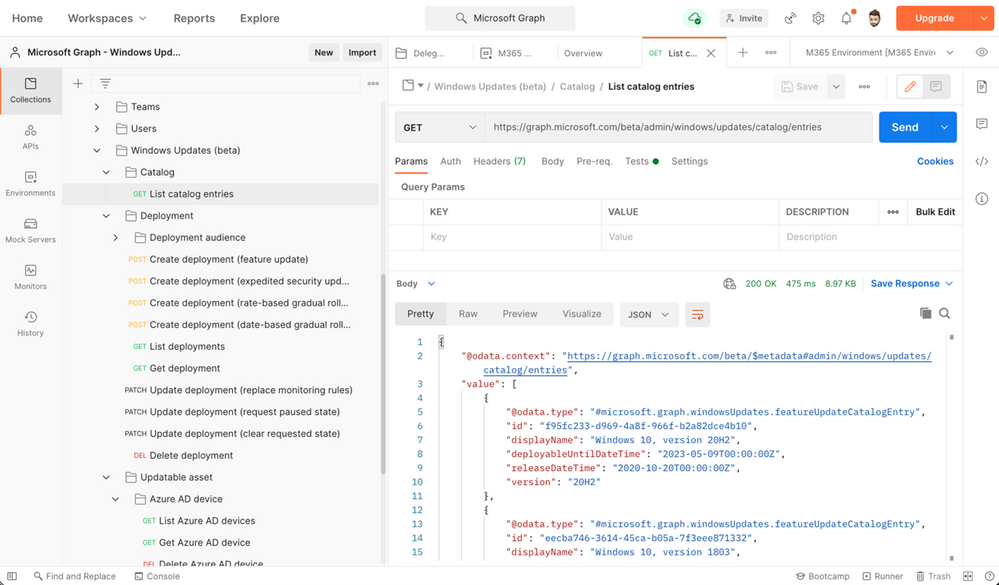 Interacting with the Windows Update for Business deployment service via Postman
Interacting with the Windows Update for Business deployment service via Postman

















Recent Comments