by Scott Muniz | Apr 27, 2021 | Security, Technology
This article is contributed. See the original author and article here.
Google has released Chrome version 90.0.4430.93 for Windows, Mac, and Linux. This version addresses vulnerabilities that an attacker could exploit to take control of an affected system.
CISA encourages users and administrators to review the Chrome Release Note and apply the necessary updates.

by Contributed | Apr 27, 2021 | Business, Microsoft 365, Technology
This article is contributed. See the original author and article here.
Today, we’re pleased to announce that the Microsoft Office and OneNote apps are now available for Amazon Fire tablets in the Amazon Appstore. Combined with the Outlook and OneDrive apps already available for Amazon Fire tablets, these apps extend your Microsoft 365 benefits across even more devices. We’ve timed the release of these apps in…
The post Microsoft 365 apps now available for Amazon Fire tablets appeared first on Microsoft 365 Blog.
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.
by Contributed | Apr 27, 2021 | Technology
This article is contributed. See the original author and article here.
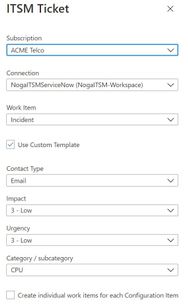
Today’s organizations are using multiple tools and environments for their day-to-day operation. As a result, many prefer a one central management system to operate their service across the stack. The integration of Azure Monitor Alerts with ITSM ticketing systems (e.g. ServiceNow) was created with this goal in mind.
Azure Monitor is a cloud-based offering that helps you to reliably monitor the performance and availability of your cloud services. Azure Monitor collects and analyzes telemetry from your cloud as well as on-premises environments. Azure Monitor alerts uses this data and gives proactively notifies you when a metric value or a log query result indicates a problem.
Why do we need integration between Azure Alerts and ITSM systems?
Integrating a monitoring and service management systems provides a single view of tickets/incidents in one central system regardless the underlying cloud technology. Thus, it enables a multi-cloud strategy of monitoring both cloud and on-premises services integrated with all the other monitored items in an organization.
When an organization has common processes and one unified KPI management system, they can operate across their stack view and improve per the operational and business needs.
How can we establish the integration between Azure Alerts and ITSM systems?
out of the various ways to integrate, in this article we will explore two integration options ITSM connector integration and logic app.
As a customer, you can select how you want to be notified about an alert using action group. Notification can go through email, SMS, Webhook or even an automated solution. You can also choose to use ITSM or a Logic app:
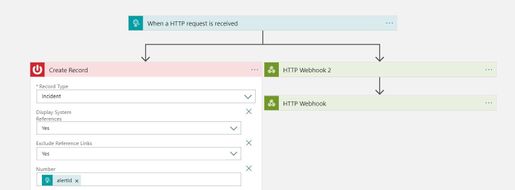
- ITSM Connector: ITSM connector lets you send alerts to an external ticketing system such as ServiceNow.

- Logic app: Logic apps let you write processing rules and use a built-in connector that will send the alerts to an external ticketing system such as ServiceNow.
What are the pros and cons for each option?
ITSM connector:
- Plug and Play: ITSM is a built-in solution within Azure Monitor, meaning that with a simple configuration you can send Azure alerts to the ticketing system.
- Bi-directional: The ITSM connector can also pull incidents and change requests from ServiceNow into an Azure Monitor Log Analytics workspace. This allows you to consume the data using Azure Monitor tools (for example using dashboard).
- Multi-Partners: The integration supports more than ServiceNow. It supports Microsoft System Center as well as BMC helix. The next generation of the integration is referred to as secure export.
Logic app:
- Flexible: Logic apps are more flexible. In the sense that you can define custom logic which builds a custom payload to send to ServiceNow when an alert fires.
- Complexity: The logic app rules can be very complex.
In conclusion, the main difference between the two is the robustness of the integration. ITSM is easy to use though albeit less flexible. Logic apps on the other hand are very flexible, but the configuration might be complex. As a customer, you need to define your priorities and evaluate which is the best solution for your organization.
by Contributed | Apr 27, 2021 | Technology
This article is contributed. See the original author and article here.
In Logic App, sometimes we need to merge two Json arrays into one based on reference ID.
The normal way is to iterate one array -> filter the items with same ID in another array -> insert the items.
But there’s another achievement to do it is using “Azure Monitor Logs” connector and pass arrays as dynamic content in the query which will be less time consumption and higher performance.
Background
In Azure Monitoring query, we can not only retrieve the data which stored in the database, but also pass dynamic content into it and convert it as data table.
https://docs.microsoft.com/en-us/azure/data-explorer/kusto/query/scalar-data-types/dynamic
Scenario
I have 2 Json arrays like following:
Array 1:
[
{
“@odata.type”: “#microsoft.graph.user”,
“id”: “e9b26715-b94e-xxxxxxxxxxxxxxxxx”,
“userPrincipalName”: “user2@xxx.onmicrosoft.com”
}
……
{
“@odata.type”: “#microsoft.graph.user”,
“id”: “8e98ee70-d769-xxxxxxxxxxxxxxxxx”,
“userPrincipalName”: “user3@xxx.onmicrosoft.com”
}
]
Array2:
[
{
“@odata.type”: “#microsoft.graph.user”,
“id”: “e9b26715-b94e-xxxxxxxxxxxxxxxxx”,
“displayName”: “user2”
},
……
{
“@odata.type”: “#microsoft.graph.user”,
“id”: “8e98ee70-d769-xxxxxxxxxxxxxxxxx”,
“displayName”: “user3”
}
]
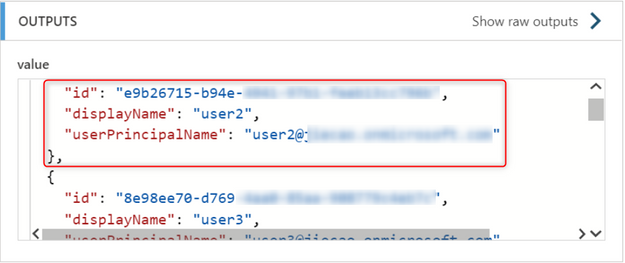
In this scenario, these 2 arrays need to be merged into one array which has id, displayName and userPrincipalName field.
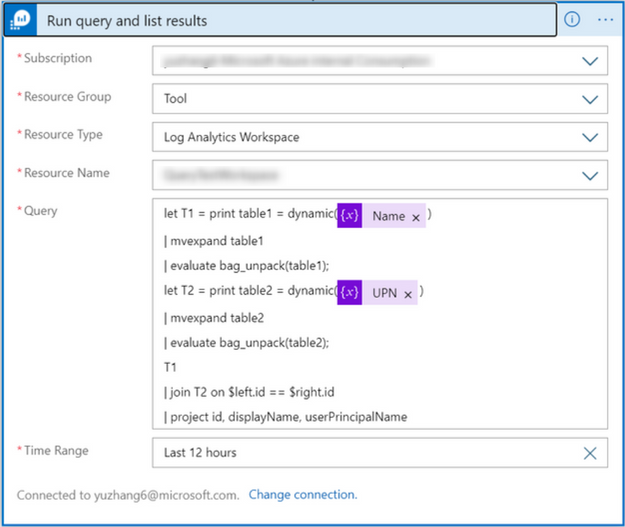
We only need to create a Azure Monitor Log – Run query and list result action like following and pass these 2 json arrays as dynamic content:

After run the LA, we can get the merged array.
Limitation
The values of type dynamic is limited to 1MB, so this workaround not support for handling large size data.
by Contributed | Apr 27, 2021 | Technology
This article is contributed. See the original author and article here.
Guest post by Microsoft Customer Engineer, Daniele De Angelis.
It’s a pleasure to be here again on the ITOpsTalk.com  .
.
Recently I had the opportunity to try the Microsoft Universal Print, the new cloud printing service on Azure.
Today I want to share with you a possible scenario where you can implement and manage this new great Azure cloud service.
If you read multiple time this article here the fast link to the specifics steps:
UP Requirements.
STEP 1 – Assign Universal Print License to users.
STEP 2 – Install the UP Connector.
STEP 3 – Register the Printers.ms
STEP 4 – Share the Printers.
STEP 5 – Add Printers on W10 Clients.
Conclusions
SCENARIO DESCRIPTION
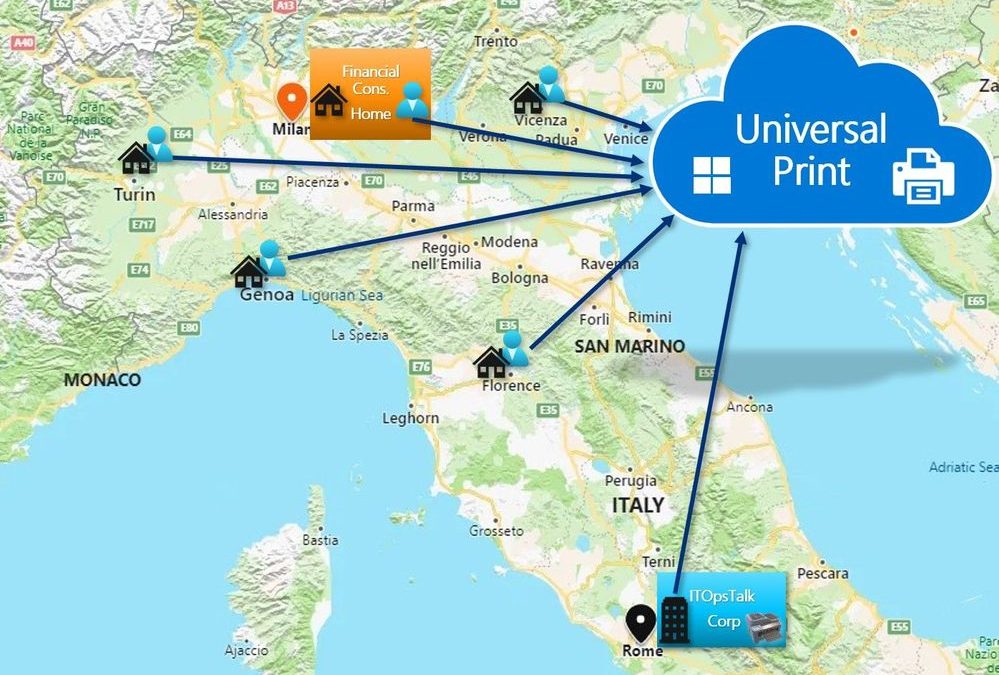
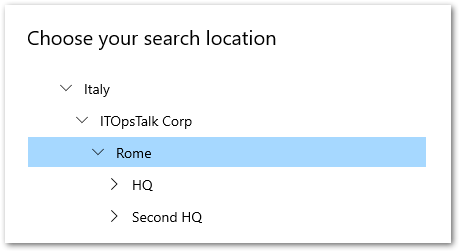
We have an enterprise company called “ITOpsTalk Corp.” located in Rome that actually have few peoples working onsite (the CEO is one of this peoples “the Capitan never leave the boat”) and many others instead are working from home. The IT department want to give the possibility to the remote users to print documents in the HQ in Rome by registering the printers located on the corporate print server to the cloud. Also the financial consultant of the company, located in Milan, is working from home and she is responsible to send to the CEO the Financial documents to sign, but how she can locate the printer in the CEO Office?
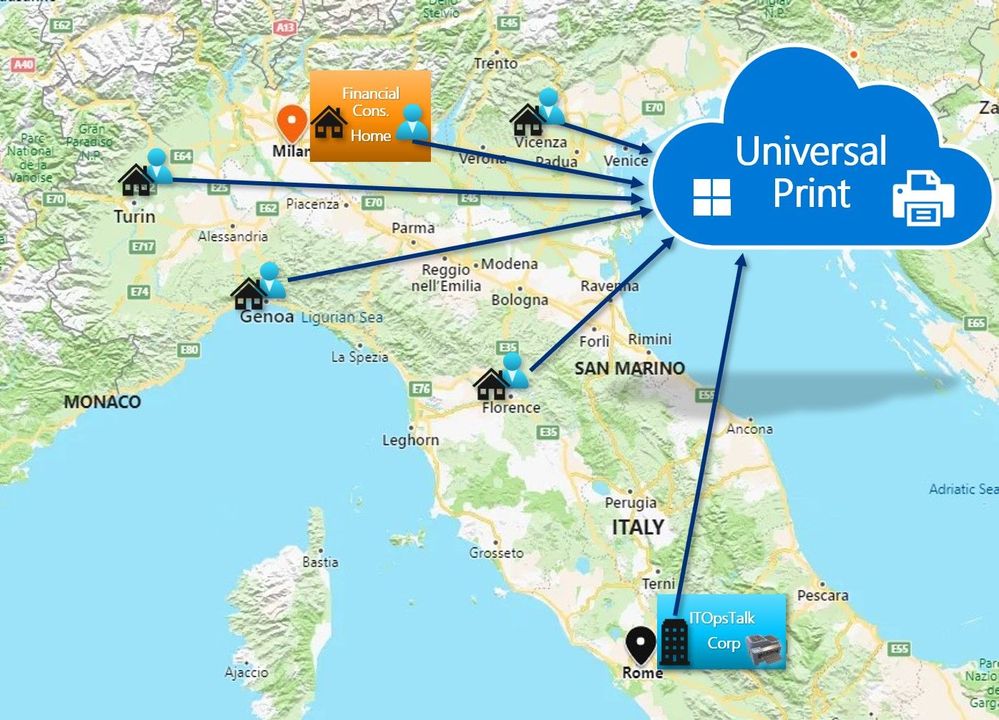 Italy Map with the location of the remote users.
Italy Map with the location of the remote users.
TECHNICAL DETAILS
The ITOpsTalk corp actually do not have Universal print compatible printers, but have standard network printers, also the IT department is using a Printer Server on Windows Server 2016 to centrally manage the the printers. All the remote users and the financial consultant are using a Windows 10 build 1909 joined to Azure AD in the ITOpsTalk Tenant.
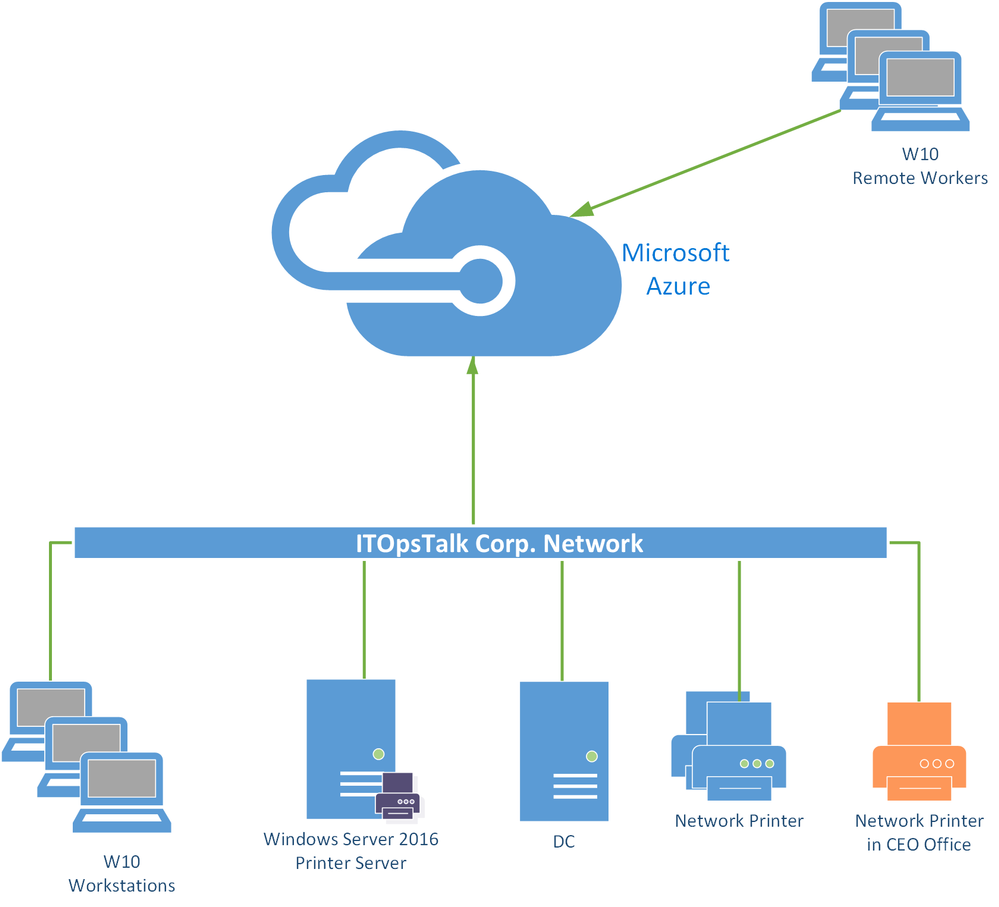 ITOpsTalk Copr Network Diagram.
ITOpsTalk Copr Network Diagram.
UP REQUIREMENTS
- Cloud Requirements:
- W10 Clients Requirements:
- Build version 1903 or later required.
- An Internet Connection.
- Device can be AAD Joined or Hybrid AD Joined or AAD Registered.
- User Requirements:
- Connector Requirement:
Windows 10 64-bit, version 1809 or later (Pro or Enterprise)
Windows Server 2016 64-bit or later (Windows Server 2019 64-bit or later is recommended)
NET Framework 4.7.2 or later.
- A continuous connection to the internet.
Access to the following endpoints: *.print.microsoft.com ; *.microsoftonline.com ; *.azure.com ; *.msftauth.net ; go.microsoft.com ; aka.ms
Reference: Installing the Universal Print connector | Microsoft Docs
STEP 1 – Assign Universal Print License to users.
- Universal Print by default is included with business and educational Microsoft 365 and Windows 10 subscriptions, but you need to know that can also be purchased as a standalone license.
Subscription Type
|
Universal Print
|
Microsoft 365 Enterprise F3, E3, E5, A3, A5
|
Included
|
Windows 10 Enterprise E3, E5, A3, A5
|
Included
|
Microsoft 365 Business Premium
|
Included
|
Universal Print
|
Standalone
|
- In typical scenario the IT department can decide to create a Group or Dynamic Group to assign UP license to desired users in the company. To assign the UP (Universal Print) licenses you can use the Azure Portal or the Admin Portal or even the PowerShell.
From Azure portal ==> Azure Active Directory ==> Licenses ==> Select the desired licenses ==> Assign the Dynamic Group
 Assign license to Dynamic Group.
Assign license to Dynamic Group.
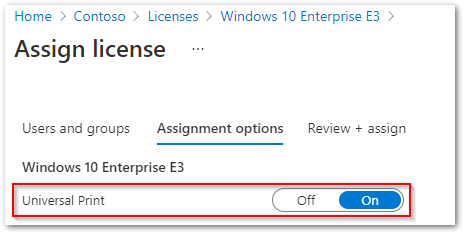 Universal Print enable license.
Universal Print enable license.
- Remember: you need to assign also the UP license also to the Printer Administrators.
STEP 2 – Install the UP Connector.
Before we start this section, we need to answer to this questions:
- Why we need the connector? Because the customer do not have UP compatible printers but standard network printers.
- Were I need to place the connector? In this scenario the better place is the “Printer Server” because have the network visibility of the printers.
- I have a Linux Server can I install it on it? We ♥ Linux but some things need to done by Windows
 , so the answer is no.
, so the answer is no.
Let’s start with the deploy of the Universal Connector:
- Download the Universal Print connector from https://aka.ms/upconnector. (this is a direct download link)
- Install the connector on the “Printer Server“:
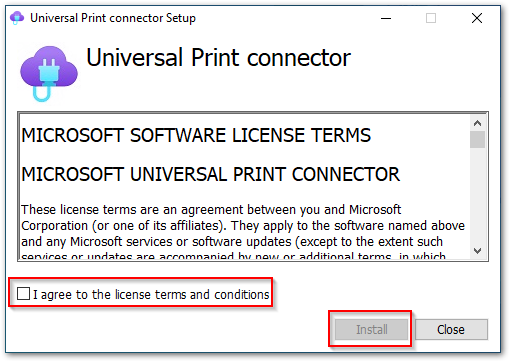 Universal Print Connector EULA.
Universal Print Connector EULA.
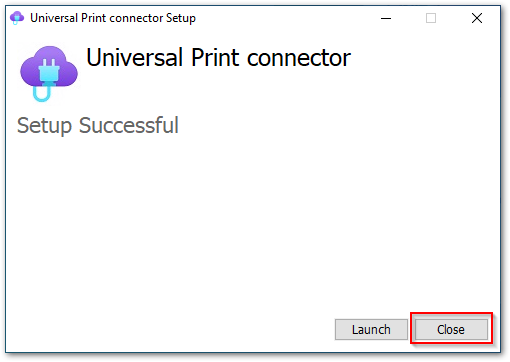 Universal Print Connector Installed Successfully.
Universal Print Connector Installed Successfully.
- After the installation, we need to register the UP connector on Azure, and to do so we need a Global Admin or a Printer Administrator:
- Start the connector.
 UP Connector Desktop Icon
UP Connector Desktop Icon
- Login with a Printer Administrator Credential in the tenant of the ITOpsTalk Corp.
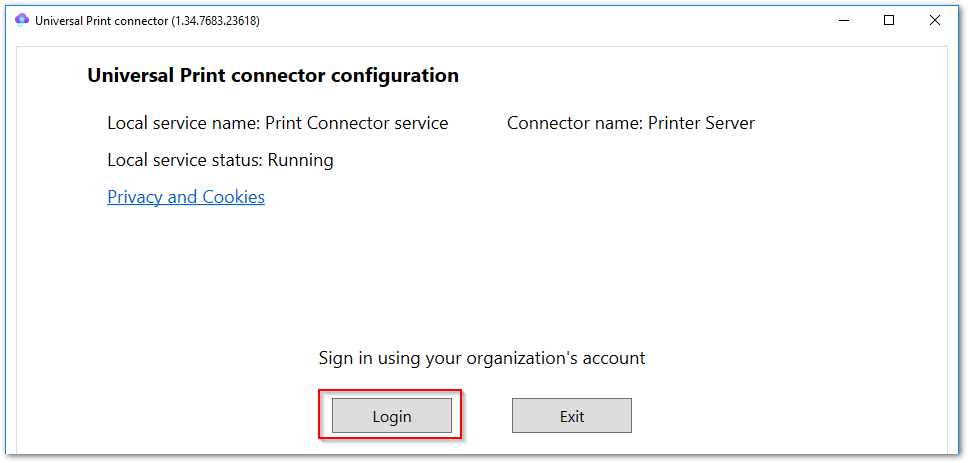 UP Connector Login.
UP Connector Login.
- Insert a name for the connector and Register it on the Azure Tenant.
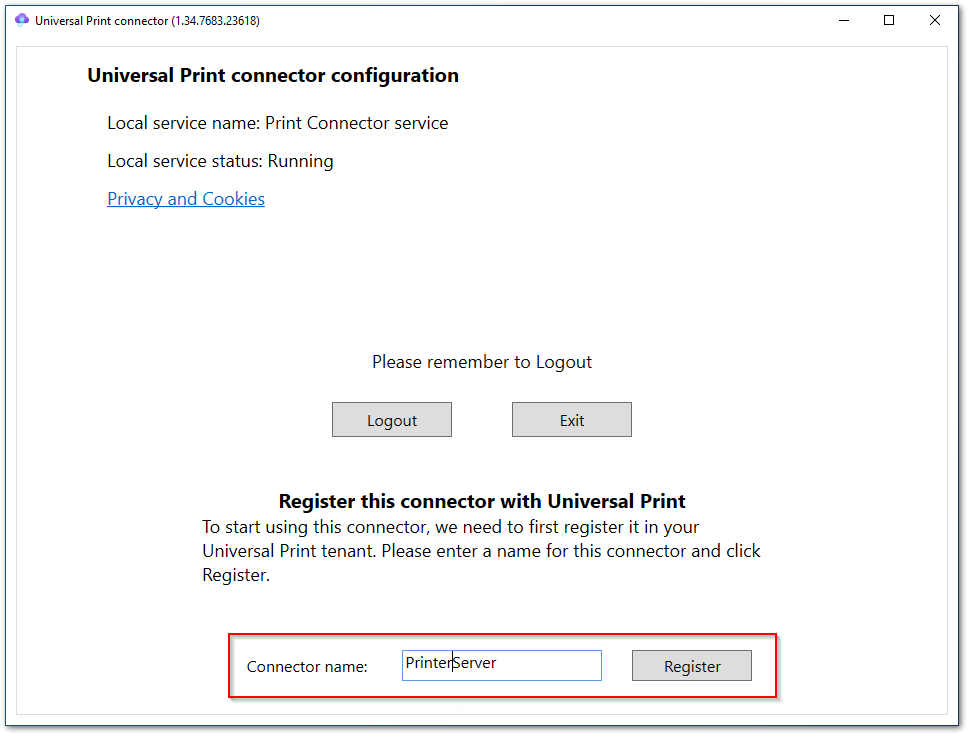 UP Connector name.
UP Connector name.
- Now if we go to the azure portal, and from the global search we type “Universal print” under the resource menu we can find the connectors menu and here we can see the connector just registered.
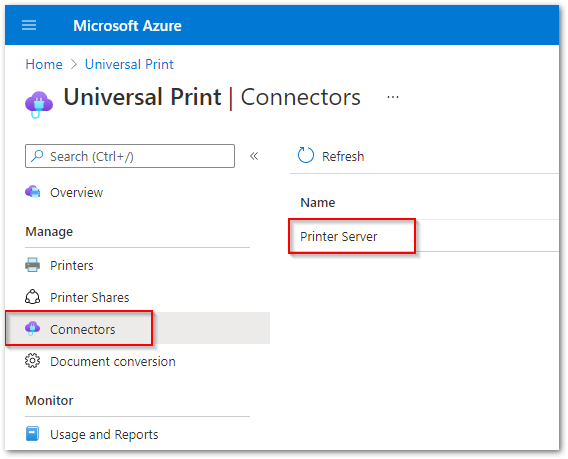 UP Connector on Azure Portal.
UP Connector on Azure Portal.
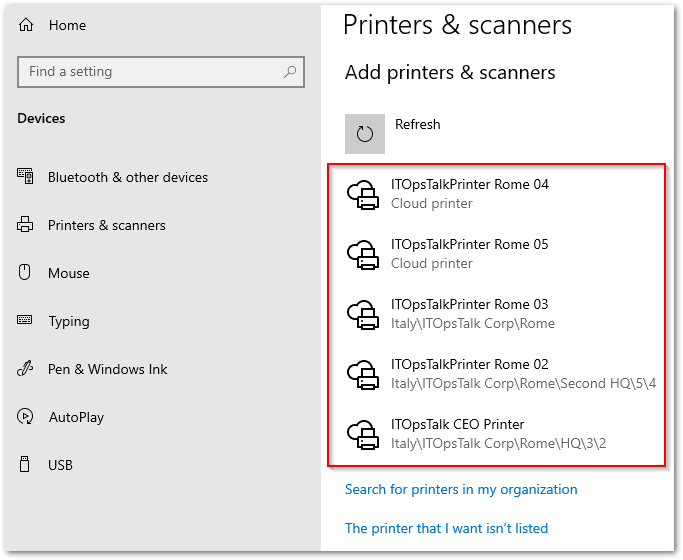
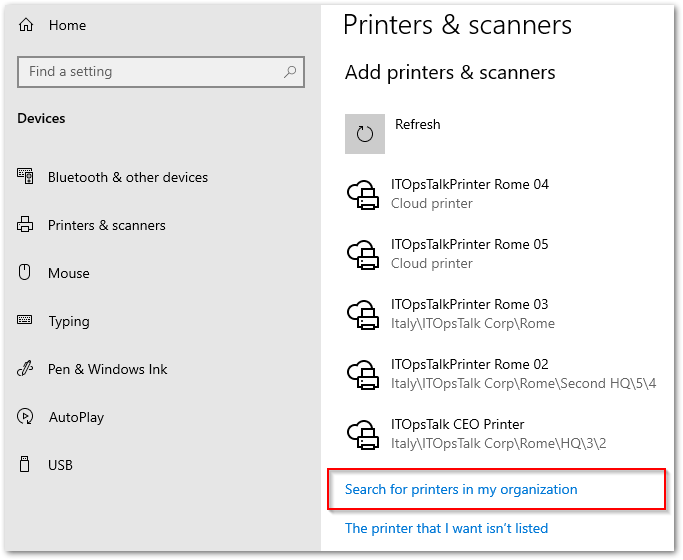
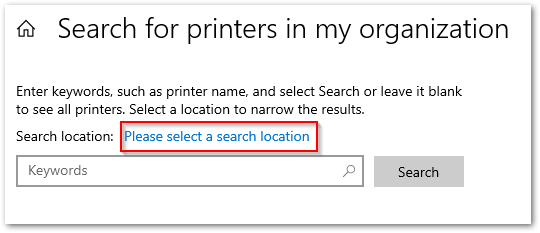
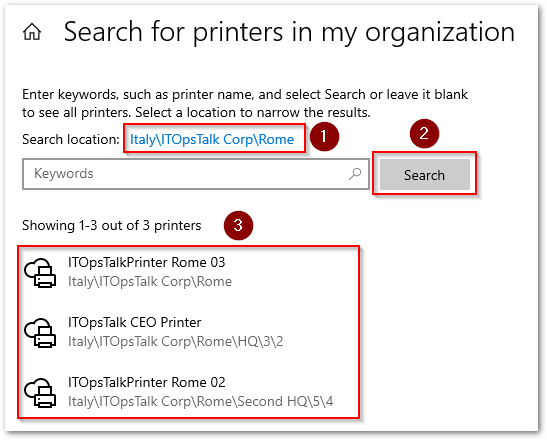
STEP 3 – Register the Printers.
- After complete the connector registration, we need to register the printers on the cloud by selecting it from the connector interface:
NOTE: You need to keep in mind that the connector is able to register only the printers that are visible as a “local printers“. 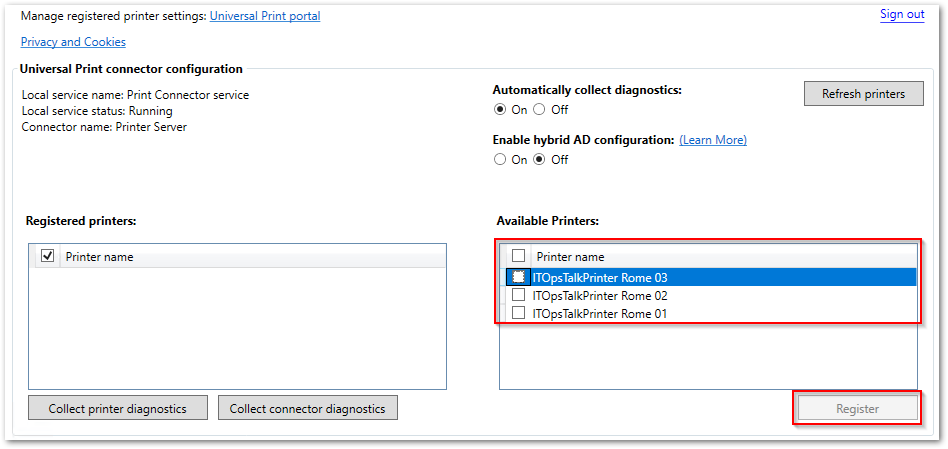 UP Connector register printers.
UP Connector register printers.
- Here you can see that one printers is registered and other two are in-progress.
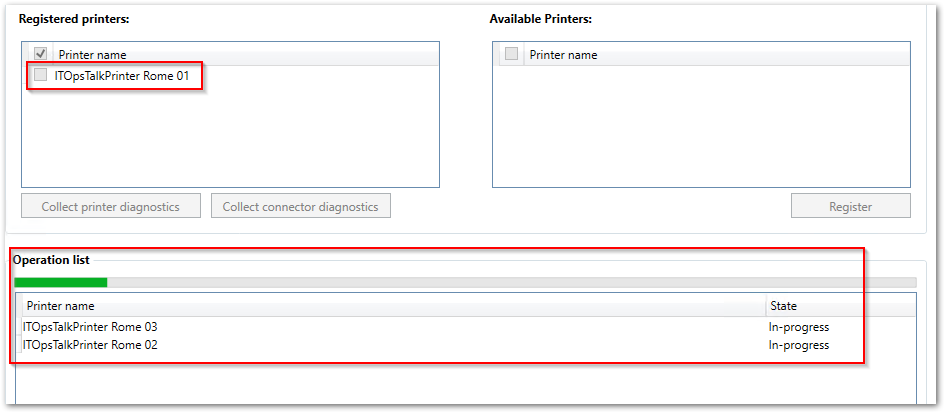 UP Connector register printer progress.
UP Connector register printer progress.
- After successfully complete the printer registration you need to remember to “Sign Out” from the connector but why?
The user account used to login in the connector, do not represent a service account used by the connector service visible in the Windows services, but will only be used to register the printers from the connector interface to the Azure tenant and managing it.
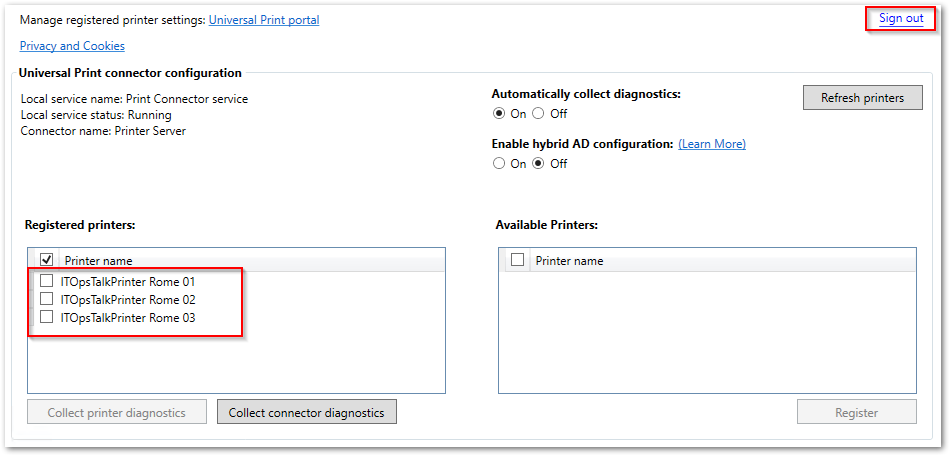 UP Connector Register printers completed.
UP Connector Register printers completed.
STEP 4 – Share the Printers.
- After completing successfully the printer registration, from the Azure Portal we are able to see in the Universal Print service, the registered printers:
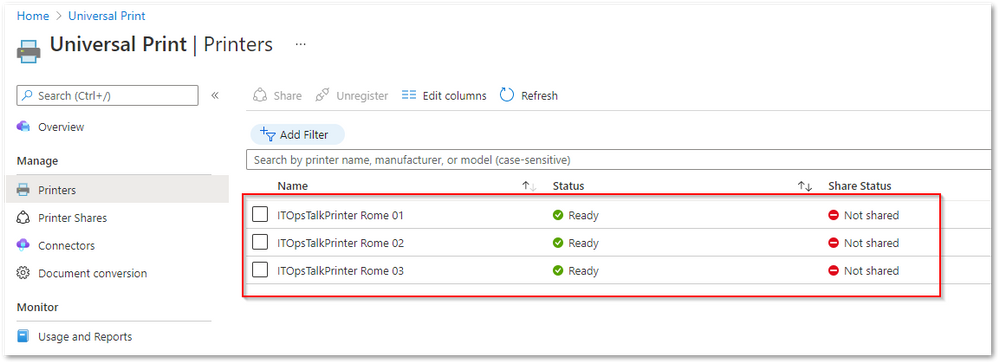 Registered printers on the Azure portal.
Registered printers on the Azure portal.
- Now we have two way to share the printers:
- Select multiple Printers and use the command “Share” to share immediately the printers with the same exact name of each printer and the same “Access Control” (this means the same users or groups that you will select will have access to the printers)
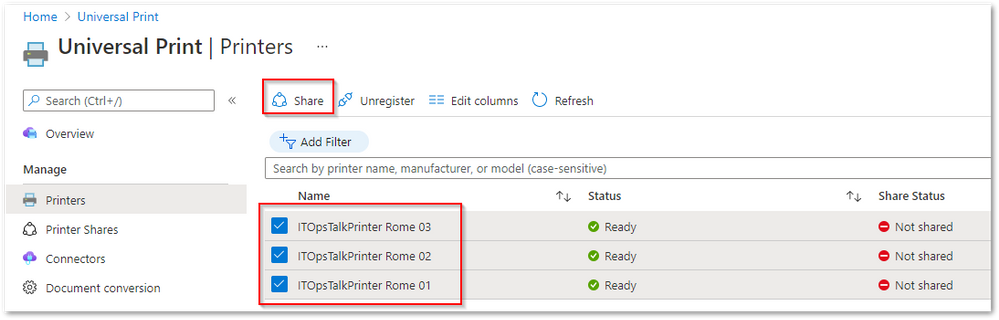 Share multiple printers at the same time from the Azure portal.
Share multiple printers at the same time from the Azure portal.
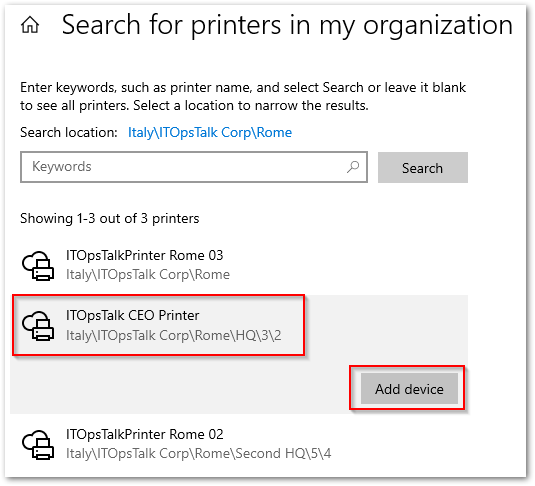
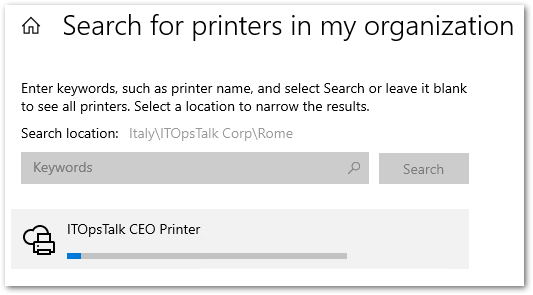
- Or you can click on a printer name and from the command bar use the “Share Printer“:
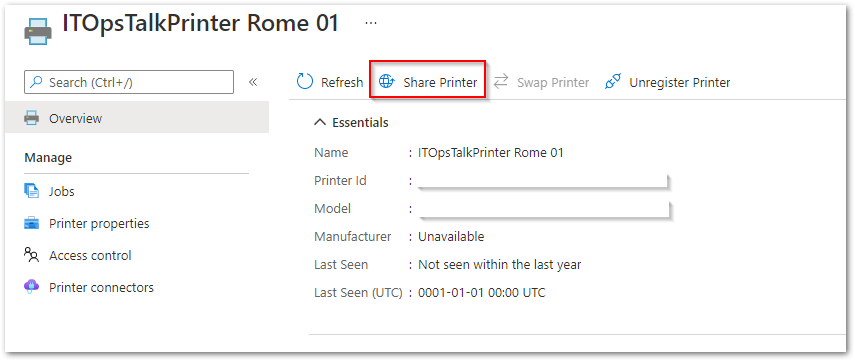 Share one single printer from the Azure portal.
Share one single printer from the Azure portal.
In this way you can specify a different “Share Name” and specify different members for each printer share.
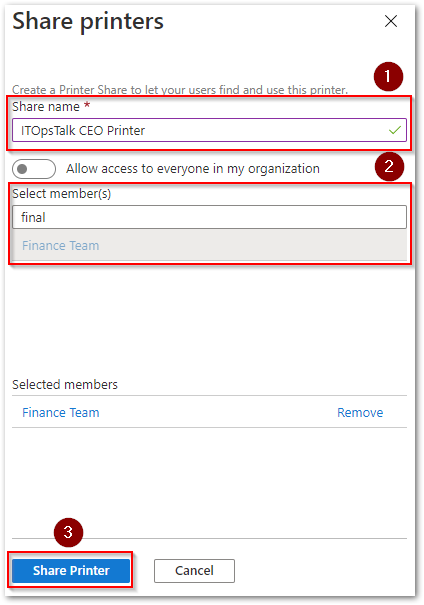 Share Printer with a custom name.
Share Printer with a custom name.
As you can see with this share name “ITOpsTalk CEO Printer” the financial consultant is able to identify really fast the CEO Printer, but also only the Finance Team is able to print using this printer.
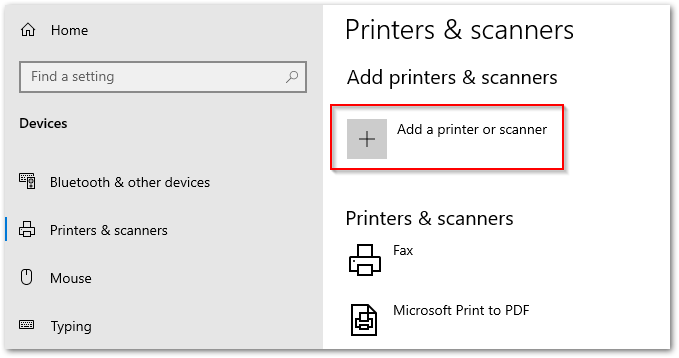
STEP 5 – Add Printers on W10 Clients.
Conclusions
Remember, we love the Azure Portal to configure printers/shares or even the access control, but when we have a huge numbers of printers we love much more the PowerShell module dedicated to Universal print:
Install-Module UniversalPrintManagement
PowerShell Module – Universal Print | Microsoft Docs
In my honest opinion I think that the Universal Print represent something really powerful for the customers that want to simplify the printing infrastructure (especially if you have Universal Print enabled printers), also I think that we are only at the beginning of this journey our Product Group is working really hard to expand the functionality of this service, and to provide us feedback please look below in the Reference section.
I really hope with that this article, if you already have subscription that include the Universal Print license, you will start from tomorrow to try to deploy this great service in your environment, starting always from a pilot and then expand it to all your enterprise.
Enjoy the Universal Print and please don’t have fear to ask me questions! 
Official Reference.

























Recent Comments