by Contributed | Jun 29, 2021 | Technology
This article is contributed. See the original author and article here.
React class type is available
React is a popular JavaScript library for building user interfaces (UI). It is a declarative way to create reusable components for your website. Learn how to create a lab that uses React and some popular JavaScript libraries Redux and JSX. We describe how to install NodeJS, which is a convenient way to run a web server for your React application.
We created two example classes so you could use the operating system of your choice.
The React Development on Windows class type shows how to install Visual Studio 2019 for your development environment. The article includes:
- Lab Account settings needed to use Visual Studio 2019 marketplace image.
- Recommended lab settings.
- How to install debugger extensions for your browser.
- How to allow teacher to view student’s website.
- Example costing for the class.
The React Development on Linux class type shows how to install Visual Studio Code for your development environment. The article includes:
- Recommended lab settings.
- How to install Visual Studio Code and needed extensions.
- How to install debugger extensions for your browser
- How to allow teacher to view student’s website.
- Example costing for the class.
Thanks,
Azure Lab Services Team
by Contributed | Jun 29, 2021 | Technology
This article is contributed. See the original author and article here.
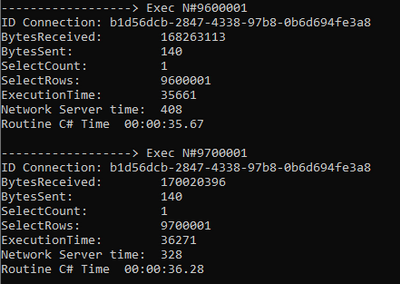
Today, I received a very good question from a customer about what is the command timeout that external tables is using. Following I would like to share with you my experience playing with this.
We need to know that the command timeout is configured by application side, so, for this reason, I developed a small C# application with the following characteristics:
- Every loop I’m increasing the SELECT TOP in 100000 rows.
- PerformanceVarcharNVarchar3 is an external tables that contains around 1.000.000.000 of rows.
- I used the connection statistiics to obtain the time invested on every operation.
- Changing the command timeout to multiple values (in this case to 0) the operation will wait until the command timeout is reached.
for (int tries = 1; tries <= nRows; tries+=100000)
{
stopWatch.Start();
C.SqlCommand command = new C.SqlCommand("SELECT top " + tries.ToString() + "* FROM [PerformanceVarcharNVarchar3]", oConn);
command.CommandTimeout = 0;
Console.WriteLine("------------------> Exec N#" + tries.ToString());
command.ExecuteNonQuery();
IDictionary currentStatistics = oConn.RetrieveStatistics();
if (bMetric)
{
Console.WriteLine("ID Connection: " + oConn.ClientConnectionId.ToString());
Console.WriteLine("BytesReceived: " + currentStatistics["BytesReceived"]);
Console.WriteLine("BytesSent: " + currentStatistics["BytesSent"]);
Console.WriteLine("SelectCount: " + currentStatistics["SelectCount"]);
Console.WriteLine("SelectRows: " + currentStatistics["SelectRows"]);
Console.WriteLine("ExecutionTime: " + currentStatistics["ExecutionTime"]);
Console.WriteLine("Network Server time: " + currentStatistics["NetworkServerTime"]);
}

In this situation, as we could see, the command timeout that a query that is running using External Table will be the same that the application has.
Enjoy!

by Jenna Restuccia | Jun 29, 2021 | ADA Compliance, American Sign Language, Assistive Technologies, Tips and Tricks
- Adjust your meeting rooms.
Does your meeting room have rows of chairs, making it difficult to make eye contact? A rounded seating arrangement is more conducive for the deaf as they can see other’s faces. This format enables them to read lips if they wish, see and interpret the tone in which the person is speaking, and know who is talking. This small change can help reduce misunderstandings.
- Set up a Video Relay Service (VRS) device.
A VRS device is a device used to enable a deaf person to make and receive phone calls through an interpreter. This innovation allows a deaf person to contact suppliers, clients or make any call required within their workspace.
- Supply an Interpreter.
It may seem acceptable to work around having an interpreter by writing notes. This practice can cause many misunderstandings as English is not the native language of the Deaf. Providing an interpreter is essential for the work and the growth of deaf employees. These additional services will help increase the ease with which deaf employees can find information or communicate with co-workers.
Making the workplace an accessible space for deaf and hard-of-hearing individuals is an ongoing challenge and necessity for many employers. It is essential to have a well-developed strategy for ensuring that the workplace is easily adaptable to the specific needs of workers. One way to achieve this goal is through the development of a workplace accessibility plan, which should include policies, procedures, and guidelines for training and customizing workstations. While most organizations have policies in place for providing access to information in situations where such communication may be critical, they often fall short when it comes to providing reasonable accommodation for workers of all abilities. Thus, it is imperative to implement a comprehensive plan that considers deaf and hard-of-hearing employees’ unique needs.
It is crucial to train employees on how to make a workplace accessible to disabled individuals. Training should include how to handle emergencies, use ASL, and use electronic or mechanical devices. Employees who do not know how to make a workspace accessible may not perform on a team properly. It is also vital that managers provide cultural training and information to their employees to understand their team members and how to respect and encourage them. If your business offers deaf-accessible products or services, promote them!
by Contributed | Jun 29, 2021 | Technology
This article is contributed. See the original author and article here.
By Adrian Moore – Sr Program Manager | Microsoft Endpoint Manager
As part of the Microsoft 365 license, your company is likely entitled to adopt Microsoft Endpoint Manager, which brings together Microsoft Intune and Configuration Manager into a unified platform to help protect and manage your organization’s devices and apps. Now what? Let’s go through the basics of managing your organization’s devices and mobile applications with Microsoft Intune.
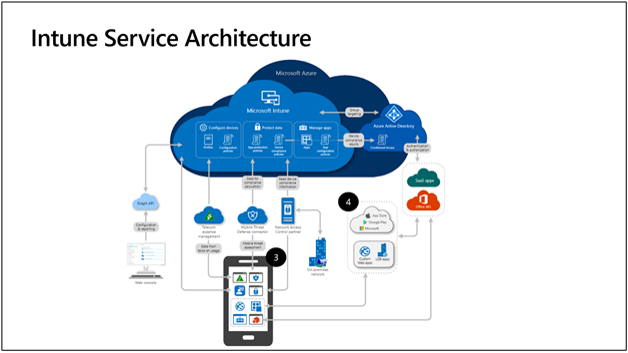
A global cloud service architecture
Microsoft Intune was architected from the cloud and for the cloud and is closely tied with Azure Active Directory (Azure AD). Intune controls integrate with Azure AD and Conditional Access (CA) policies to help you manage access to your organization’s apps and devices and protect and isolate corporate data. Intune enhances CA with device–based compliance and can also take risk signals from Microsoft Defender for Endpoint, as well as mobile threat defense (MTD) apps. Intune also integrates with network access control (NAC) solutions to ensure only compliant devices can connect to your corporate network.
App stores are key parts of an Intune deployment. For iOS devices, you can use either the Apple Volume Purchase Program (VPP), which is part of Apple Business Manager, or the App Store. In the case of Android, either the Google Play app store for device administrator devices, or Managed Google Play for Android Enterprise devices can be used. For Windows, the Windows Store for Business provides a great experience for app deployment.
Your administrative management experience is centralized from the Microsoft Endpoint Manager admin center, which uses Microsoft Graph calls to the Intune . Every action from app configuration to mobile device management settings to security in the admin center is a Microsoft Graph call. If you’re not familiar with Graph, take some time to understand it—specifically how it integrates with Microsoft Intune.
 Intune Service Architecture.
Intune Service Architecture.
Initially, Intune began as a combination of a set of services running on physical machines in a private datacenter, and a set of distributed services running on Azure. By 2018, all Intune services were re-architected to run on Microsoft Azure. Today, Intune’s cloud services are built on Azure Service Fabric. All services are deployed to a Service Fabric cluster consisting of a group of front-end and middle-tier nodes. We refer to these clusters as an Azure Scale Unit, or ASU.
Here’s what the architecture looks like:
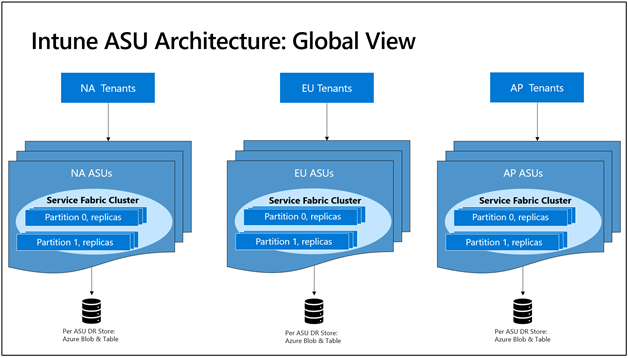 Intune ASU Architecture: Global View.
Intune ASU Architecture: Global View.
- There are 18 clusters spread over three regions in North America, Europe, and Asia Pacific. Each cluster has about 5,000 services running, all partitioned to scale out.
- The clusters are completely isolated and independent of one other. They are hosted in different subscriptions and datacenters and cannot access each other.
- We back up data to an external persisted Azure table/blob storage. This enables fast recovery for replicas in case of catastrophic failure.
Moving from physical machines in a private datacenter to a cloud-based, micro-service architecture enabled Microsoft to scale Intune to billions of devices and apps and to rapidly deliver new innovations. Customers experienced increased reliability, stability, and performance of the service. You can find out more about the development of this architecture in the blog post How we built (rebuilt!) Intune into a leading globally scaled cloud service.
Planning and deployment
A successful adoption or migration to Microsoft Intune starts with a plan. This plan depends on your company’s current device management solution, business goals, and technical requirements. Additionally, you should include key stakeholders who will support and collaborate with the plan.
The following resources will help plan and deploy Intune:
Device enrollment
You can manage devices and apps, and how they access company data, in Intune. To use Intune mobile device management (MDM), the devices must first be enrolled in the Intune service. When a device is enrolled, it’s issued an MDM certificate. This certificate is used to communicate with the Intune service.
Devices can be enrolled on the following platforms. For the specific versions, see Supported operating systems:
- Android
- iOS/iPadOS
- macOS
- Windows
Different platforms may have additional requirements. For example, iOS/iPadOS and macOS devices require an MDM push certificate from Apple.
The following resources will help you learn more about device enrollment for each platform:
Compliance policies
MDM solutions like Intune can help set requirements for users and devices to protect organizational data. In Intune, you manage these requirements with compliance policies. There are two parts to compliance policies in Intune:
- Compliance policy settings – Tenant-wide settings that are like a built-in compliance policy that every device receives. Compliance policy settings set a baseline for how compliance policy works in your Intune environment, including whether devices that haven’t received any device compliance policies are compliant or noncompliant.
- Device compliance policy – Platform-specific rules administrators can configure and deploy to groups of users or devices. These rules define requirements for devices, like minimum operating systems or the use of disk encryption. Devices must meet these rules to be considered compliant.
The following articles will help you understand how to create and monitor compliance policies in Intune, as well as how to integrate with MTD and NAC solutions, and Conditional Access:
Intune app protection policies
Intune app protection policies (APP) allow you to protect organizational data within an application. Together with app configuration capabilities, you can implement mobile application management (MAM) in Intune to help protect sensitive data that is accessed from both managed and unmanaged devices. With MAM without enrollment (MAM-WE), you can use Intune to manage work or school-related apps, including productivity apps such as the Microsoft Office apps, on almost any device, including personal devices in bring-your-own-device (BYOD) scenarios. See the official list of Microsoft Intune protected apps available for public use.
To get an overview of app protection policies and how they work, check out the following articles:
Delivering apps to devices
Intune supports a wide range of apps, including store apps for iOS, macOS, Android, and Windows, and line–of–business (LOB) apps. You can manage app deployment from the Microsoft Endpoint Manager admin center. Also, you can use Intune to orchestrate store app deployment with Managed Google Play, the Apple App Store, and the Microsoft Store.
Check out these resources to find out how to add and manage apps with Intune:
Privacy and personal data in Intune
You should understand how Intune collects, stores, retains, processes, secures, shares, audits, and exports personal data. Microsoft Intune does not use any personal data collected as part of providing the service for profiling, advertising, or marketing purposes.
The following resources will help you understand privacy and personal data in Intune:
Intune service updates
New feature releases for Intune typically have a six to eight-week cadence, from planning to release, called a sprint. Intune releases use a YYMM naming convention. For example, 2107 would be a July 2021 release.
How updates are released
Our monthly release process is a methodical update of many different environments, first across multiple Azure services and then in the admin center which makes it available for use. environment called Self Host is the first environment to receive the release. This is used only by the Intune engineering teams. hen roll out to the Microsoft tenant, which manages over 650,000 devices. Once we’ve validated there are no key issues with the services, we then begin rolling out to customer environments in a phased approach. Once all tenants have been successfully updated, we update the Microsoft Endpoint Manager admin center. This phased approach lets us identify issues before they impact the service or our customers.
Updating the Company Portal app is a different process. Microsoft is subject to the release requirements and processes of the Apple App Store and Google Play, and sometimes mobile carriers. It isn’t always possible to align Intune release updates with updates to the Company Portal. See UI updates for Intune end-user apps for information on Company Portal updates.
How can I tell if a service update is complete for my tenant?
- Sign in to the Microsoft Endpoint Manager admin center.
- Select Tenant administration > Tenant status to see your tenant’s name and location, MDM authority, account status, and service release number. In the example below, the tenant has the 2104 (April 2021) service release.
 Example screenshot of the Tenant admin > Tenant status blade.
Example screenshot of the Tenant admin > Tenant status blade.
Keeping up to date about releases
Keeping up to date about releases and changes is an important part of your Intune deployment. Intune provides several ways to stay current about latest updates to the service:
- What’s new in Intune – week in in Microsoft Intune, including an overview of the current release, notices, information about earlier releases, and other information. Content is published at the end of the current sprint once the UI updates start rolling out in the Microsoft Endpoint Manager admin center.
- Message Center – When the service update is completely rolled out, you’ll see a message posted in the Tenant status – Service health and message center, or you can view the same messages in the Message Center at portal.office.com. We use service APIs to pull just the Microsoft Endpoint Manager messages from Office into the Microsoft Endpoint Manager admin center UI.
- Microsoft Intune Tenant Status page – A centralized hub where you can view current information and communications about the Intune service and your tenant status.
- Navigate to the Microsoft Endpoint Manager admin center.
- Select Tenant administration > Tenant status > Service Health > Message center.
- Select a message under INTUNE MESSAGE CENTER to read it.
- Get the latest announcements from Twitter — @IntuneSuppTeam.
Intune also shares information about updates in development, posts service incidents in Microsoft Endpoint Manager admin center, and can send email notifications. To learn how to stay current with this information, see Staying up to date on Intune new features, service changes, and service health.
We hope you found this overview of Intune helpful. Check out Tips and tricks for managing Intune to continue learning how to get the best out of your Intune deployment.
Resources and feedback
For additional information on this subject, see the following documentation:
Microsoft Intune overview
Device management overview
Tutorial: Walkthrough Intune in Microsoft Endpoint Manager
High-level architecture for Microsoft Intune
If you have any questions, reply to this post or reach out to @IntuneSuppTeam on Twitter.
by Contributed | Jun 29, 2021 | Technology
This article is contributed. See the original author and article here.
Today we are announcing the availability of quarterly Cumulative Updates (CUs) for Exchange Server 2016 and Exchange Server 2019. These CUs include fixes for customer reported issues, all previously released security updates, and a new security feature.
A full list of fixes is contained in the KB article for each CU, but we wanted to highlight the new security feature.
Exchange Server AMSI Integration
As mentioned in our recent blog post, the June 2021 CUs include new Exchange Server integration with AMSI (Antimalware Scan Interface). AMSI exists in Windows Server 2016 and Windows Server 2019, and the new integration is available in Exchange 2016 and Exchange 2019 when running on either of those operating systems. For Exchange 2016, AMSI integration is available only when running on Windows Server 2016. It is not available for Exchange 2016 running on Windows Server 2012 or Windows Server 2012 R2.
AMSI integration in Exchange Server provides the ability for an AMSI-capable antivirus/antimalware solution to scan content in HTTP requests sent to Exchange Server and block a malicious request before it is handled by Exchange Server. The scan is performed in real-time by any AMSI-capable antivirus/antimalware solution that runs on the Exchange server as the server begins to process the request. This provides automatic mitigation and protection that compliments the existing antimalware protection in Exchange Server to help make your Exchange servers more secure.
Because we know that some of our customers modify the web.config file on their Exchange Server, we wanted to let you know that installation of the June 2021 CUs will add a new section in the web.config of every HTTP service under <Modules>. The entry will be called “HttpRequestFilteringModule” and it must be present for AMSI integration to work.
Release Details
The KB articles that describe the fixes in each release and product downloads are as follows:
Additional Information
Microsoft recommends all customers test the deployment of any update in their lab environment to determine the proper installation process for your production environment.
These updates contain schema and directory changes and so require you prepare Active Directory (AD) and all domains. You can find more information on that process here. Schema changes can be tracked here. For best practices for successful installation, please see this document.
If updating from an older version of the CU, please see Exchange Update Wizard for detailed steps to follow.
Also, to prevent installation issues you should ensure that the Windows PowerShell Script Execution Policy is set to Unrestricted on the server being upgraded or installed. To verify the policy settings, run the Get-ExecutionPolicy cmdlet from PowerShell on the machine being upgraded. If the policies are NOT set to Unrestricted you should use these resolution steps to adjust the settings.
If you plan to install the update with the unattended install option using either PowerShell or a command prompt, make sure you specify either the full path to the setup.exe file or use a “.” in front of the command if you are running it directly from the folder containing the update. If you do not, Exchange Setup may indicate that it completed successfully when it did not. Read more here.
Note: Customers in Exchange hybrid deployments and those using Exchange Online Archiving with an on-premises Exchange deployment are required to deploy a supported CU for the product version in use.
For the latest information on the Exchange Server and product announcements please see What’s New in Exchange Server and Exchange Server Release Notes.
Note: Documentation may not be fully available at the time this post is published.
The Exchange Server team







Recent Comments