by Contributed | Jul 8, 2021 | Technology
This article is contributed. See the original author and article here.
Tracking your project’s software dependencies is an integral part of the machine learning lifecycle. But managing these entities and ensuring reproducibility can be a challenging process leading to delays in the training and deployment of models. Azure Machine Learning Environments capture the Python packages and Docker settings for that are used in machine learning experiments, including in data preparation, training, and deployment to a web service. And we are excited to announce the following feature releases:
Environments UI in Azure Machine Learning studio
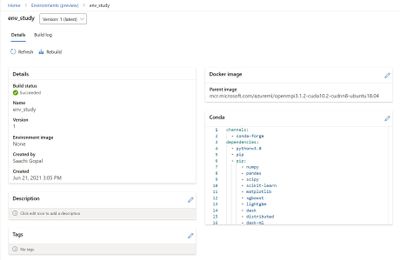
The new Environments UI in Azure Machine Learning studio is now in public preview.
- Create and edit environments through the Azure Machine Learning studio.
- Browse custom and curated environments in your workspace.
- View details around properties, dependencies (Docker and Conda layers), and image build logs.
- Edit tag and description along with the ability to rebuild existing environments.

Curated Environments
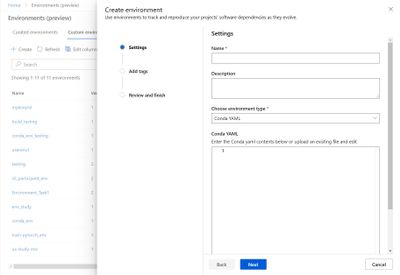
Curated environments are provided by Azure Machine Learning and are available in your workspace by default. They are backed by cached Docker images that use the latest version of the Azure Machine Learning SDK and support popular machine learning frameworks and packages, reducing the run preparation cost and allowing for faster deployment time. Environment details as well as their Dockerfiles can be viewed through the Environments UI in the studio. Use these environments to quickly get started with PyTorch, Tensorflow, Sci-kit learn, and more.
Inference Prebuilt Docker Images
At Microsoft Build 2021 we announced Public Preview of Prebuilt docker images and curated environments for Inferencing workloads. These docker images come with popular machine learning frameworks and Python packages. These are optimized for inferencing only and provided for CPU and GPU based scenarios. They are published to Microsoft Container Registry (MCR). Customers can pull our images directly from MCR or use Azure Machine Learning curated environments. The complete list of inference images is documented here: List of Prebuilt images and curated environments.
The difference between current base images and inference prebuilt docker images:
- The prebuilt docker images run as non-root.
- The inference images are smaller in size than compared to current base images. Hence, improving the model deployment latency.
- If users want to add extra Python dependencies on top of our prebuilt images, they can do so without triggering an image build during model deployment. Our Python package extensibility solution provides two ways for customers to install these packages:
- Dynamic Installation: This method is recommended for rapid prototyping. In this solution, we dynamically install extra python packages during container boot time.
- Create a requirements.txt file alongside your score.py script.
- Add all your required packages to the requirements.txt file.
- Set the AZUREML_EXTRA_REQUIREMENTS_TXT environment variable in your Azure Machine Learning environment to the location of requirements.txt file.
- Pre-installed Python packages: This method is recommended for production deployments. In this solution, we mount the directory containing the packages.
- Set AZUREML_EXTRA_PYTHON_LIB_PATH environment variable, and point it to the correct site packages directory.
https://channel9.msdn.com/Shows/Docs-AI/Prebuilt-Docker-Images-for-Inference/player
Dynamic installation:
https://docs.microsoft.com/en-us/azure/machine-learning/how-to-prebuilt-docker-images-inference-python-extensibility#dynamic-installation
Summary
Use the environments to track and reproduce your projects’ software dependencies as they evolve.

by Grace Finlay | Jul 8, 2021 | Business, Marketing
Content marketing offers a long-term value that can’t be easily found with paid advertising, but paid advertising will help get the right traffic to increase your content marketing efforts. They go hand-in-hand. So, what are these types of Digital Advertising for small businesses? This article will give you an idea.
Social Media Platforms: There are many social media platforms which include Facebook, LinkedIn, Twitter, and YouTube. If you have a blog or a website, consider adding a Facebook account to increase the reach of your digital advertising. You can set up a fan page on Facebook to share your posts and get your friends to share your posts as well. Similarly, there are plenty of other social media platforms which will allow you to place Google ads and vice versa. The great thing about these media platforms is that you can track the ROI of your ads by adding an app on your Facebook page or a tracking code in your Google AdWords account.
Facebook Ads: With Facebook, you can run two types of digital advertising campaigns. A single-page campaign and a group campaign. In a single-page campaign, you’ll place a single ad on your Facebook page. In a group campaign, you’d have a list of users to whom you’d wish to advertise. Running this type of campaign is easy since you can run different ads for different groups.
Email Marketing: Email marketing has become quite popular these days, especially for businesses with a solid client base. To make the most out of your email advertising campaign, you can use email marketing or SMS marketing. Email marketing is an effective way of reaching out to your target audience. Unlike Facebook and Google, you can also track your email advertising campaigns through web analytics.
Pay Per Click Marketing: This kind of Digital Advertising for small businesses is usually done through Google AdWords. Basically, you place the ads of your chosen vendors on Google search results and wait for the clicks to flow in. What you pay here is not a one-time cost; you’ll be charged every time the ad is clicked on. The good thing about it is that the cost per click may vary depending on the quality of the advertisers. So, if you’re running a low-budget advertising campaign, you may want to consider using the pay-per-click program.
These are just some of the many ways by which you can use the platforms provided by the internet. You can find an advertising platform suitable for your business based on the type of products or services you provide. The key is to create awareness of your brand and ensure that your target audience will become familiar with your ads.
by Scott Muniz | Jul 8, 2021 | Security, Technology
This article is contributed. See the original author and article here.
CISA has released an analysis and infographic detailing the findings from the Risk and Vulnerability Assessments (RVAs) conducted in Fiscal Year (FY) 2020 across multiple sectors.
The analysis details a sample attack path a cyber threat actor could take to compromise an organization with weaknesses that are representative of those CISA observed in FY20 RVAs. The infographic provides a high-level snapshot of five potential attack paths and breaks out the most successful techniques for each tactic that the RVAs documented. Both the analysis and the infographic map threat actor behavior to the MITRE ATT&CK® framework.
CISA encourages network defenders to review the analysis and infographic and apply the recommended mitigations to protect against the observed tactics and techniques. For information on CISA RVAs and additional services, visit the CISA Cyber Resource Hub.
by Contributed | Jul 8, 2021 | Technology
This article is contributed. See the original author and article here.
Mithun Prasad, PhD, Senior Data Scientist at Microsoft
“I don’t have enough relevant data for my project”! Nearly every data scientist has uttered this sentence at least once. When developing robust machine learning models, we typically require a large amount of high-quality data. Obtaining such data and more so, labelled or annotated data can be time-consuming, tedious and expensive if we have to rely on experts. Hence, there is a compelling need to generate data for modelling using an automated or a semi-automated way. Specifically, in this work, we explore how we can utilize Open AI’s Generative Pre-trained Transformer 3 (GPT-3) for generating data to build models for identifying how credible news articles are.
GPT-3
GPT-3 is a language model that leverages deep learning to generate human-like text. GPT-3 was introduced by Open AI in May 2020 as a successor to their previous language model (LM) GPT-2. It is considered to be better than GPT-2. In fact, with around 175 billion trainable parameters, OpenAI GPT-3’s full version is one of the largest models trained so far.
Fake News Generation
In this blog post, we discuss the collaborative work between Microsoft’s ACE team and the Dataclair AI lab of O2 Czech Republic, where the goal is to identify fake news. Fake news is defined as a made-up story with an intention to deceive or to mislead. The general motive to spread such news is to mislead the readers, damage the reputation of any entity, or gain from sensationalism. The creation of a dataset for identifying credible news requires skilled annotators and moreover, the task of comparing proposed news articles with the original news articles itself is a daunting task as it’s highly subjective and opinionated. This is where the recent advances in natural language modelling and those in text generation capabilities can come to the rescue. We explore how new language models such as GPT-3 can help by generating new data.
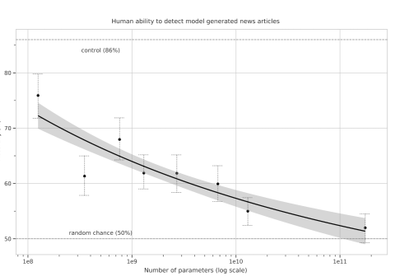
We generate fake news data using GPT-3 by providing prompts that contain a few sample fake news articles in the Czech language. Doing something like this would have been unthinkable a few years ago, but the massive advancement of text generation through language models opened doors to such experiments. As the research paper describing GPT-3 shows, GPT-3 is very good at generating news articles of high quality that even humans are not capable of detecting as computer-generated:

Source: https://arxiv.org/pdf/2005.14165.pdf
The plot also shows how text generating models improved via having access to more parameters. GPT-3 is the furthest to the right and the plot conveys how accurately people were able to recognize generated articles from those written by humans.
Prompt Engineering
“Prompts” are a way to get the model to produce text by specifying an instruction in natural language and showing some demonstrations of how to follow the instructions well. GPT-3 has an incredible capacity to mimic writing styles. When the prompt is set up correctly, GPT-3 adheres to the example just enough to copy those underlying elements (for example: includes or excludes citations, etc.) and introduce a new twist to the generated text. It is even capable of creating its own complex arguments. Thus, it is not just a replication of pre-existing data, but a creation of new and original articles from which the model can learn.
An example of a prompt and parameters used to generate fake news are as follows in bold. The generated text is in italics.
Generate a news article based on the headline and with the same style of writing as given in the example.
Headline: Where do leftist extremists get the audacity to speak for the nation?
Text:
My fellow Czechs, we must shake off the shame that the USA, Brussels and other countries have been forced on us with the help of our own “experts” and “journalists”. The same people who are now digging into our nation with the help of a genuine community of the USA and Brussels – the Pekarová and other forces…
Parameters:
Temperature: 0.7, Max tokens: 1000, Top p: 1, Frequency penalty: 0, Presence penalty 0
From these parameters, the most important ones are temperature and max tokens. Temperature controls randomness in the text. Therefore, a temperature of 0.7 was chosen to produce less deterministic results that still follow the structure and writing style of the example. Max token value was set to 1000 tokens (~4000 characters) because this is the average length of a news article. It should be noted that when working with GPT-3, the process of finding the right parameters is about experimentation.
Admittedly, there are still challenges to deal with. One of them is the need to manually inspect if GPT-3 returns articles that are relevant and in the right credibility category. Due to the sensitivity of the topic of article credibility, data quality checks will need to be implemented. Another minor limitation is that while GPT-3 understands many articles that it has been trained on, it has problems when analysing newer topics. For example, it is unable to fully grasp the significance of COVID-19 and it usually avoids writing about it due to not having enough knowledge about the global pandemic. Thus, it generates less realistic articles when faced with such a topic.
Nevertheless, if those obstacles are kept in mind, GPT-3 can help make dataset creation faster and more reliable. This is something that the O2 CZ team plans to utilize for their disinformation recognition AI model. “Our model extracts different features (aggressivity, clickbait etc.) from the article via smaller extraction modules. Those features are then evaluated by the deep learning classification module and subsequently transformed into one number by the ensemble method. For the system to work, we need as many articles as possible for training the classification module, which we hope to obtain with the help of GPT-3,” described by Filip Trhlik, a Data Scientist at the Dataclair AI lab.
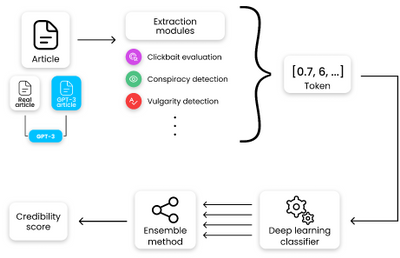
Disinformation recognition AI model diagram
In conclusion, artificially generating new data is a very exciting use case of language models and even though the data generated requires a small amount of manual inspection, it is very beneficial for downstream modelling tasks. The ability to generate a large amount of synthetic data in a short time is very promising.
by Contributed | Jul 8, 2021 | Technology
This article is contributed. See the original author and article here.
Create an HTTP Trigger Function
- Create an HTTP Trigger C# function with a name of your liking.
- Use an App Service Hosting Plan SKU or Standard or Premium, both support VNET integration. You may use Standard plan for this set up, as it is cheaper.
- Replace the out of the box code for the HTTP Trigger with the following code.
#r “Newtonsoft.Json”
#r “System.Text.Json”
using System.Net;
using Microsoft.AspNetCore.Mvc;
using Microsoft.Extensions.Primitives;
using Newtonsoft.Json;
using System.Collections.Generic;
using System.Net.Http;
using System.Net.Http.Headers;
using System.Text.Json;
using System.Threading.Tasks;
using System.Globalization;
using System.Text.Json.Serialization;
//using System.Exception;
public class Repository
{
[JsonPropertyName(“name”)]
public string Name { get; set; }
[JsonPropertyName(“description”)]
public string Description { get; set; }
[JsonPropertyName(“html_url”)]
public Uri GitHubHomeUrl { get; set; }
[JsonPropertyName(“homepage”)]
public Uri Homepage { get; set; }
[JsonPropertyName(“watchers”)]
public int Watchers { get; set; }
[JsonPropertyName(“pushed_at”)]
public string JsonDate { get; set; }
public DateTime LastPush =>
DateTime.ParseExact(JsonDate, “yyyy-MM-ddTHH:mm:ssZ”, CultureInfo.InvariantCulture);
}
public static async Task<IActionResult> Run(HttpRequest req, ILogger log)
{
log.LogInformation(“C# HTTP trigger function processed a request.”);
string name = req.Query[“name”];
string requestBody = await new StreamReader(req.Body).ReadToEndAsync();
dynamic data = JsonConvert.DeserializeObject(requestBody);
name = name ?? data?.name;
string responseMessage = string.IsNullOrEmpty(name)
? “This HTTP triggered function executed successfully. Pass a name in the query string or in the request body for a personalized response.”
: $“Hello, {name}. This HTTP triggered function executed successfully.”;
// Testing this…disregard for demo
// ReadTextFile();
log.LogInformation(“Performing ProcessRepositories code section…”);
var repositories = await ProcessRepositories();
foreach (var repo in repositories)
{
if (repo == null)
{
continue;
}
log.LogInformation($“Repo Name: {repo.Name}”);
log.LogInformation($“Repo Description: {repo.Description}”);
}
return new OkObjectResult(responseMessage);
}
// Ref URL: https://github.com/dotnet/samples/blob/master/csharp/getting–started/console–webapiclient/Program.cs
private static async Task<List<Repository>> ProcessRepositories()
{
var client = new HttpClient();
client.DefaultRequestHeaders.Accept.Clear();
client.DefaultRequestHeaders.Accept.Add( new MediaTypeWithQualityHeaderValue(“application/vnd.github.v3+json”) );
client.DefaultRequestHeaders.Add(“User-Agent”, “.NET Foundation Repository Reporter”);
var streamTask = client.GetStreamAsync(“https://api.github.com/orgs/dotnet/repos”);
var repositories = await System.Text.Json.JsonSerializer.DeserializeAsync<List<Repository>>(await streamTask);
return repositories;
}
// Ref URL – https://docs.microsoft.com/en–us/dotnet/csharp/programming–guide/file–system/how–to–read–from–a–text–file
private void ReadTextFile(ILogger log)
{
try
{
// Example #1
// Read the file as one string.
string text = System.IO.File.ReadAllText(@“10.10.2.5testtestfile.txt”);
// Display the file contents to the console. Variable text is a string.
log.LogInformation(“Contents of WriteText.txt = {0}”, text);
}
catch(Exception ex)
{
log.LogInformation(“Exception = {0}”, ex.Message);
}
}
Run the HTTP Trigger and see the Function run successfully
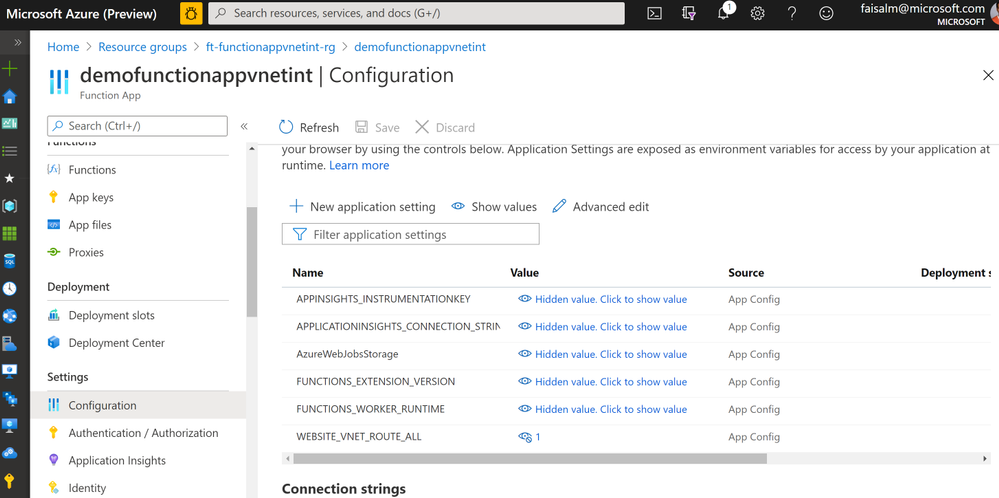
- Create a Config Variable WEBSITE_VNET_ROUTE_ALL in Application settings for the function and set the value to 1.
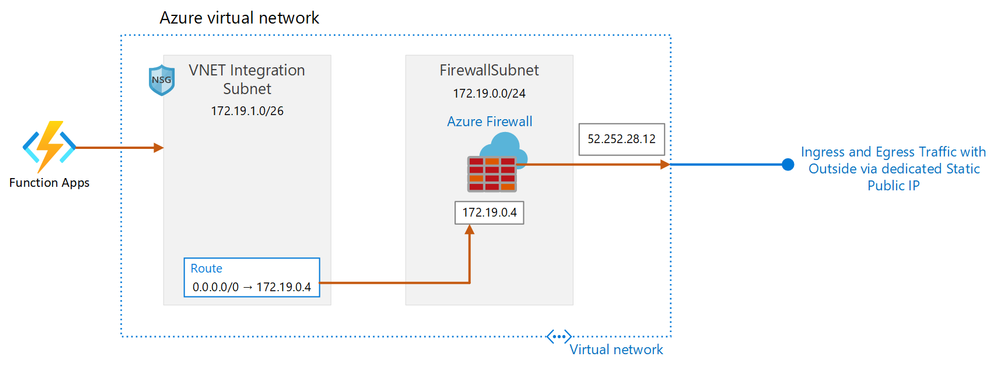
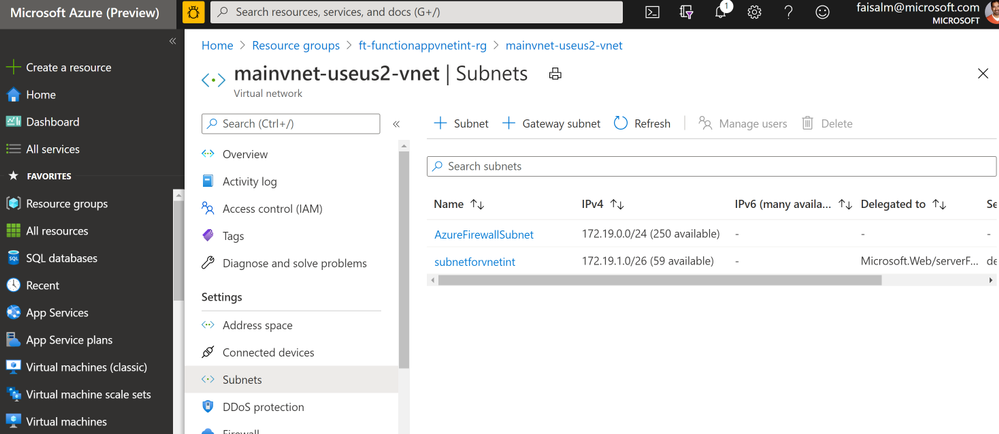
Create a VNET and required subnets
- Ensure a subnet AzureFirewallSubnet is created, dedicated for the Azure Firewall.
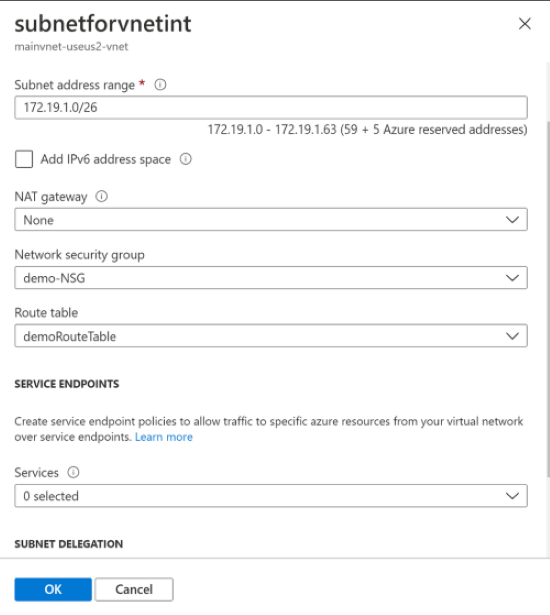
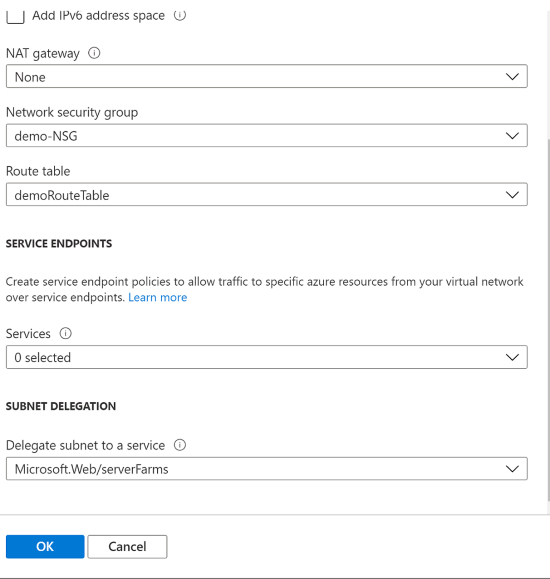
- In the subnet for VNET integration, set the Delegate subnet to a service to Microsoft.Web/serverFarms
Create Simple NSG
- Create an out of the box NSG rule and associate that to the VNET Integration Subnet
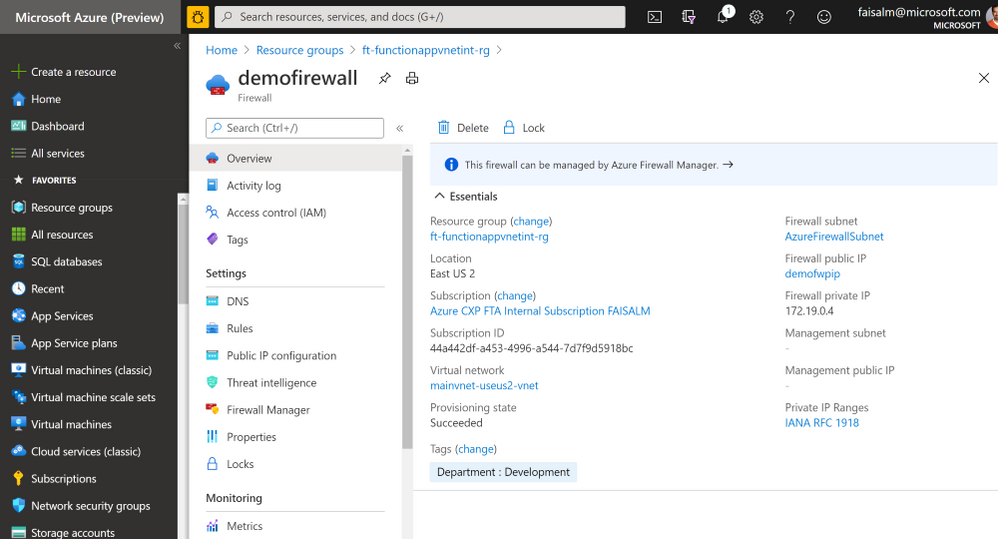
Create an Azure Firewall
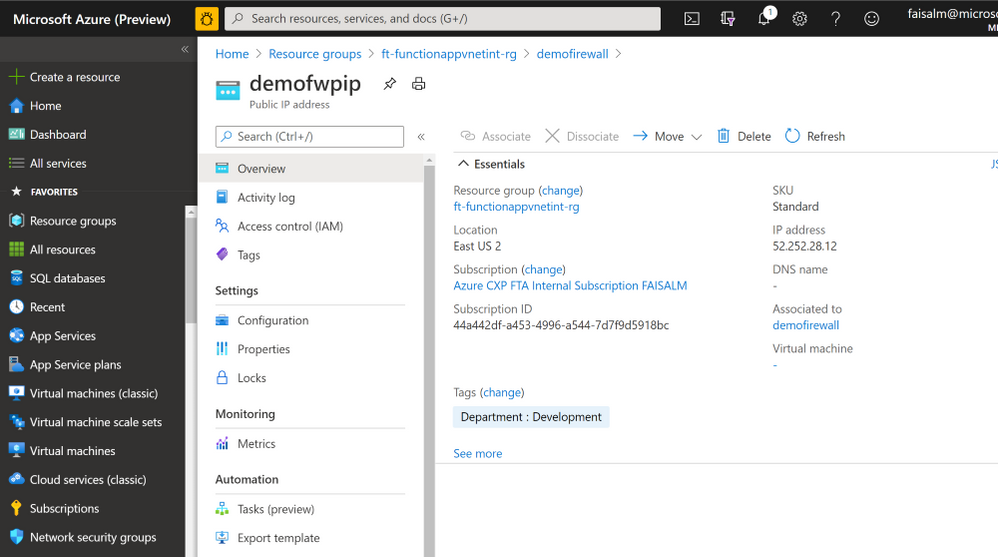
- Using the AzureFirewallSubnet subnet, create an Azure Firewall. Once provisioned, note down the Firewall private IP
- Click on the public IP name listed under Firewall public IP and note down the Firewall public IP, in this case 52.252.28.12. The name is provided during Azure Firewall creation.
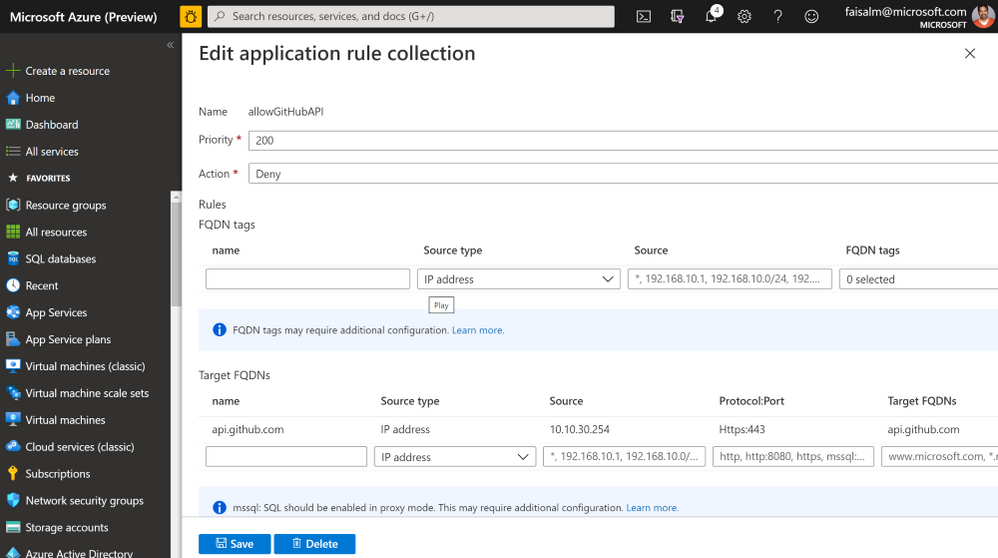
- Click on Rules under Settings for the Firewall. Navigate to Application Rules and create an application rule collection as below. Note: to test the scenario, rule Action will be set to Deny or Allow.
- Set the values as shown above
- Set the target FQDN to api.github.com
- Protocol:Port Https:443
- Set the source to the CIDR of the subnet for VNET integration, this is the easiest way. Alternatively, you may set the source to the IP assigned by the VNET integration subnet to the function app. This can be done by enabling the logs and seeing the details for the logs for AzureFirewall, the assigned IP address is listed.
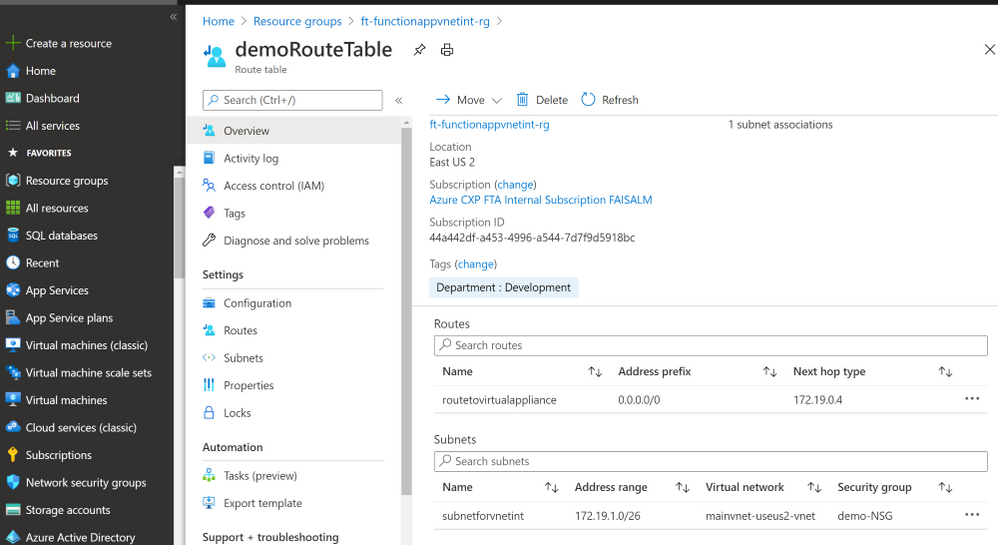
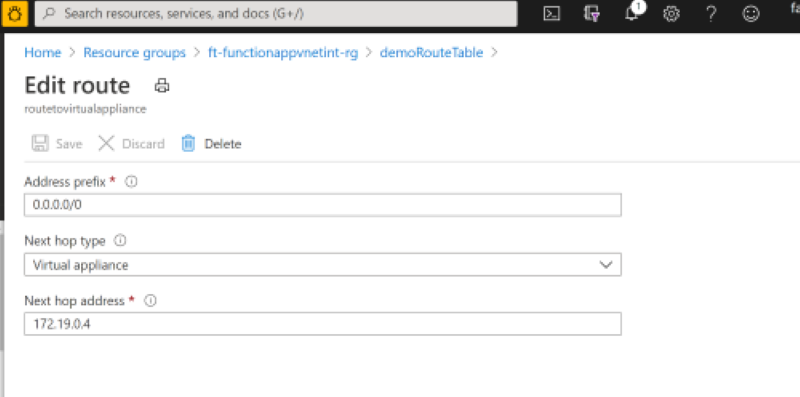
Create Route Table
- Create a route such that the next hop is for the private IP of the virtual appliance, in this case the private IP of the Azure Firewall
Set the application rule to Deny, and run the Azure Function. You will see the Function will respond with an error in the output window. This is because the Firewall is blocking the traffic via the outbound public static IP.
Now set the Application Rule in the Azurefirewall to Allow and run the Azure Function. The call is now successful, retrieving the GitHub repositories per the logic in the HTTP Trigger function, this is viewable in the output window.
The public static outbound IP address is Firewall public IP, in this case 52.252.28.12. This is the IP to be shared with the Vendors or 3rd Party Software providers such that it can be whitelisted and calls can be made to the function via this public static IP.












Recent Comments