
Join action in Data Operations in Power Automate
Here’s a quick summary on how you can use Join operation in Power Automate!
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.

Here’s a quick summary on how you can use Join operation in Power Automate!
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.
This article is contributed. See the original author and article here.
As stated in an earlier blog, Zero Trust Architecture resets the security posture of the organization to act as if hostile adversaries have both internal and external access to the network. You must assume that a breach has occurred or is imminent in a Zero Trust approach to cybersecurity. The traditional Defense in Depth strategy of protecting the perimeter of the digital estate and trusting everyone inside is no longer a sound cybersecurity premise. Identity is the new perimeter for Zero Trust Architecture and Azure Active Directory is at the core.
In the 1979 film, “When a Stranger Calls” the police are doing forensics on a series of threatening phone calls that Jill, the babysitter, keeps receiving. Finally, in the plot twist, Sergeant Sacker calls Jill back to inform her that they have traced the calls to their origin, “We’ve traced the call. It’s coming from inside the house.” Unlike Jill’s unfortunate circumstances our organizations must presume external actors have infiltrated our digital estate with a run of the house—including compromised identity and credentials.
In Verizon’s 2021 Data Breach Investigations Report, External Actors continually execute successful breaches by leveraging compromised credentials. The attacks tend to look like internal actors until forensic investigations reveal that actor is indeed an external threat that has infiltrated the digital estate. This is why one of the most foundational practices within the Identification and Authentication (IA) Domain, and arguably all of the Cybersecurity Maturity Model Certification (CMMC) framework, is IA.3.083 “Use multifactor authentication for local and network access to privileged accounts and for network access to non-privileged accounts.” After surpassing weak authentication through credential hijacking, the first stage of the breach can remain undetected for months or years while adversaries move laterally through your network.
Since the beginning of 2021, there have been more than two dozen ‘headliner’ cyber breaches—ranging from the top social networks to mobile carriers to local retailers in our communities. The principal interests of these attacks have been primarily stolen credentials and identity—email addresses, phone numbers, hashed passwords, and other Personally Identifiable Information (PII). Most often, an email address or phone number is 50% of the information needed to compromise login credentials. Combined with phishing attacks—the most prevalent attack type—adversaries have a treasure trove of identity credentials to be leveraged across a multitude of organizations.
As Alex Simons, CVP, Identity Program Management at Microsoft stated, “The only people in the world who love passwords are hackers!” Compromised credentials remain the number one method that bad actors use to gain access to your organization. In fact, Microsoft Security Research found that the risk of credential compromise could be reduced up to 99% by simply enabling Multifactor Authentication (MFA) across your enterprise.
This brings us back to adopting a Zero Trust mindset for your digital culture and estate. And yes, it is a cultural shift for everyone. By moving the digital perimeter from the network edge to identity, you no longer need to focus on whether bad actors are internal or external threats. No one accessing the network is implicitly trusted nor granted privileges beyond what is necessary for task completion. Even if an organization follows CMMC IA.3.083 mentioned above, it is imperative to control and track sessions and activities attached to a single identity.
Large, highly resourced companies are still challenged to perform this level of identity management and monitoring across their digital estate. With over 75% of the Defense Industrial Base (DIB) being small businesses, the challenge to effectively resource and standup a proactive Security Operations Center (SOC) remains a daunting task to meet the compliance requirements for CMMC Level 3 and beyond. Almost two entire CMMC domains – Audit and Accountability (AU) and Incident Response (IR) – could require one FTE for a 200-person company as an example. The only financial mitigation or offset comes through the use of technology or the use of a Managed Security Services Provider (MSSP).

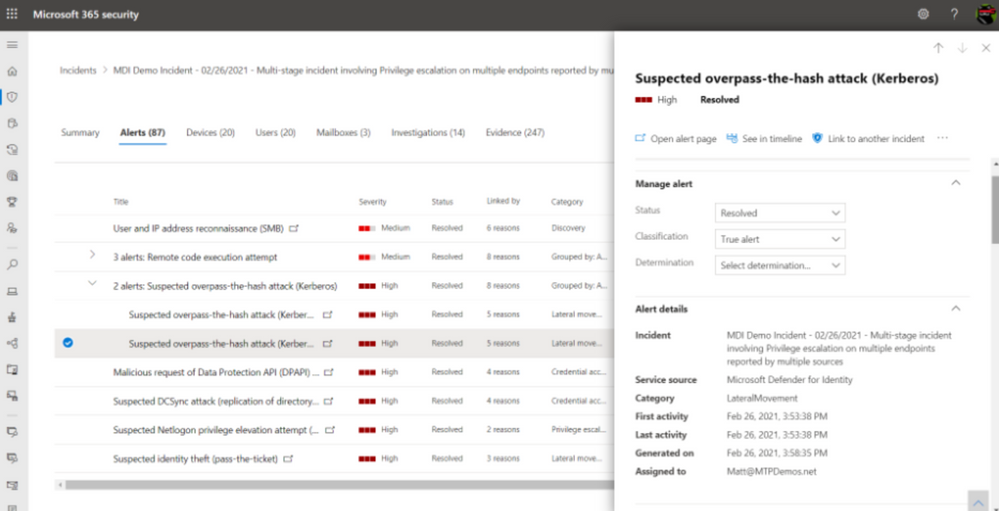
Microsoft Defender for Identity (MDI), previously known as Azure Advanced Threat Protection or Azure ATP, is one of those technologies that can help organizations protect and monitor user identities at scale. Organizations deployed on Microsoft 365 GCC or GCC High can take an identity-centric approach and evaluate user sign-in behaviors in real-time, along with device and application risk profiles. Not only can MDI ingest and analyze user activities (i.e. multiple data points around each authentication attempt and session) Microsoft will correlate suspicious user behavior with other verified malicious attacks happening across millions of other cloud environments to generate possible intelligence.
For example, if a user is attempting to login to an application from Birmingham, AL and then five minutes later the same account is attempting a second login from Lubbock, Texas on a non-standard device, this behavior needs to be flagged. Firstly, unless the user has broken the space-time barrier—and teleported 1000 miles in under five minutes—it’s unlikely that this impossible travel is authentic. Second, the device profile has changed and doesn’t represent what’s known or common for that individual. Thirdly, Microsoft Defender for Identity is using machine learning to analyze new threat patterns to determine if your organizational risk has increased or if your organization is being attacked.
The above example and capabilities align to System & Communications Protection SC.3.190 “Protect the authenticity of communications” and System & Information Integrity SI.2.216 “Monitor organizational systems… to detect attacks and indicators of potential attacks.”
Microsoft Defender for Identity gets a superset of capabilities when paired with other components of Microsoft 365 Defender, a fully functioning Extended Detection and Response (XDR) suite. By correlating data from apps, email, and endpoints, your organization gains a comprehensive view of your threat landscape and procedures to mitigate and remediate attacks. More importantly, by analyzing suspicious behaviors in real-time, your security operations team can proactively hunt for threats versus waiting for a breach to occur.
In a previous article, we laid out the differences and benefits between Microsoft’s Commercial and Government Cloud offerings. Defender for Identity is built on the FedRAMP High accredited Microsoft Azure Government Cloud and includes interoperability with Microsoft 365 GCC, GCC High, and DoD. This MDI can be licensed for users through the F5 and E5 license or standalone.
Microsoft Defender for Identity for GCC, GCC High, and DoD leverage the same underlying technologies and provides same capabilities as the commercial instance of Defender for Identity with a few exceptions:
Not only will MDI integrate with Azure Active Directory and your organization’s Microsoft 365 environment, MDI will also analyze on premises Active Directory and provide insights on where improvements can be made across a company’s entire identity estate.
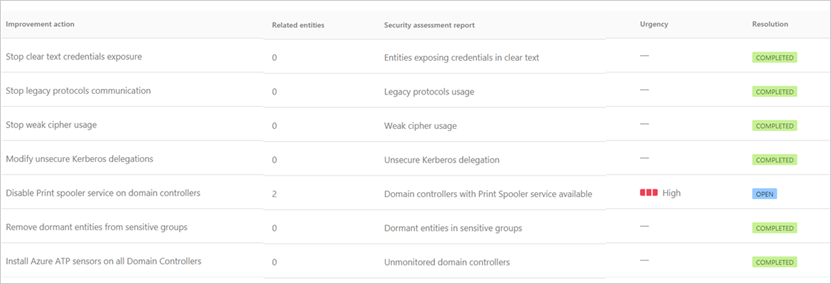
Already underway, the DIB is undertaking its most significant digital transformation with CMMC, and the Department of Homeland Security is now taking a deeper look at the program. Moreover, achieving Zero Trust Architecture is not a mutually exclusive endeavor for DIB companies. Nor is Zero Trust the latest bandwagon or industry buzzword that everyone is incorporating into their marketing. Zero Trust is a fundamental shift in our culture to not only protect our digital estate more effectively, but to also enable a higher degree of secure collaboration between organizations without boundaries.
Identity is the first step on our Zero Trust Journey. Once the Identity is fortified, we can shift to the security and protection of new devices, apps, IoT, and more. Bad actors and the threat landscape are evolving at cloud speed. These bad actors will continually attack the DIB supply chain through social engineering and pretexting to get your identity credentials—the keys to your digital estate.
In this article, there were some questions that were presented and left unanswered. However, this conversation is not done. We want you to pose questions of your own about your identity perimeter, Zero Trust Architecture, CMMC, and other security and compliance topics. The best way to get those questions asked and answered real-time is one of our upcoming events and webinars. We are expanding this conversation in the DIB community to accelerate the transformation. Let’s work together to secure our national supply chain and innovate like never before.

This article was originally posted by the FTC. See the original article here.

Did you get an email from your boss asking you for a favor? Does your boss need you to send gift cards to pay for an upcoming office party? Before you go out and pay up, ask yourself: is that really your boss? It could be a scammer trying to get your money.
Here’s how it can play out. The scammer sends you an email impersonating your boss, either using a spoofed email address, or by hacking into their account. They then make up a story about needing your help with something — an office surprise party, a company event, even a simple errand. Whatever the reason, they’ll ask you to help by paying them with gift cards, promising to pay you back later. But once you hand over the gift card number and PIN, the money is gone.
If you get an unexpected email from your boss asking for this kind of help:
Did you or someone you know pay a scammer? Find out what to do next. If you act quickly, sometimes (only sometimes) you can get your money back. But it’s worth trying.
And if you spotted this scam, report it at ReportFraud.ftc.gov.
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.
This article is contributed. See the original author and article here.
Mozilla has released security updates to address vulnerabilities in Firefox, Firefox ESR, and Thunderbird. An attacker could exploit some of these vulnerabilities to take control of an affected system.
CISA encourages users and administrators to review the Mozilla security advisories for Firefox 92, Firefox ESR 78.14, and Thunderbird 78.14.
This article is contributed. See the original author and article here.
Businesses are moving away from rigid and monolithic solutions towards agile business applications that can be deployed quickly, integrated seamlessly with other existing systems, and can collect and unify extensive amounts of data from various touchpoints unlocking siloed data. According to Forrester, siloed data inhibits organizations from creating a comprehensive profile of customer needs, a challenge for 44 percent1 of retail decision-makers.
To drive better personalization, organizations also need to create a single view of their orders across all engagement channels. Propelling this shift is the realization by business leaders that they can leverage best-of-breed applications to avoid costly and time-consuming rip and replace business processes while still achieving the same objectives.
Last month we announced the general availability of Microsoft Dynamics 365 Intelligent Order Management, a solution that enables businesses to accelerate agility by leveraging easy-to-deploy out-of-the-box connectors within a low-code or no-code environment. This month, we are pleased to share several integrations and enhancements that further expand the capabilities of Dynamics 365 Intelligent Order Management.
Learn more: Dynamics 365 Intelligent Order Management is now generally available
McKinsey2 recently interviewed 60 senior supply-chain executives from across industries and geographies. 85 percent of respondents reported that they struggled with inefficient digital technologies to address logistic disruptions, shortages of parts and materials, and sudden swings in demand caused by the COVID-19 pandemic. designed to allow businesses to rapidly scale with out-of-box, pre-built partner connectors to e-commerce platforms, fulfillment services, delivery partners, and other back-office systems. Through our growing ecosystem of partners, we provide companies with new levels of agility by seamlessly integrating with other best-of-breed solutions.
Some of the order intake systems that Intelligent Order Management offers pre-built connectors are Orderful and BigCommerce. BigCommerce is a cloud-based e-commerce SaaS platform, and Orderful is a cloud-based electronic data interchange (EDI) platform that allows enterprises to integrate EDI transactions from Orderful’s network. These new order intake sources enable more nimble operations, allowing businesses to capitalize on new opportunities faster by accepting orders from anywhere.
Another integration that we are proud to announce is with ShipStation. ShipStation is a web-based e-commerce shipping platform that helps merchants quickly generate shipping labels for their online orders. By integrating ShipStation with the Intelligent Order Management platform, users can bring all their carriers and order sources together within one unified solution.
Finally, Intelligent Order Management users can now connect to Avalara, an automated tax compliance solution that determines order tax rates based on geolocation and product classification, and also Flexe, a cloud-based platform that unifies warehouse sourcing and streamlines material handling operations.
By adding these pre-built partner connectors to Intelligent Order Management, our solution provides a foundation for businesses to build agility and resiliency into their order management processes and free themselves from legacy and inefficient digital technologies.
Learn more: Intelligent Order Management partners with leading service providers to optimize order management
Organizations can no longer afford to be rigid and reactive, and the push is for flexible, adaptable, and agile architecture. A survey conducted by McKinsey showed that highly successful agile transformations typically delivered around 30 percent gains in efficiency, customer satisfaction, employee engagement, and operational performance, making the organization 5 to 10 times faster and turbocharging innovation.
Thanks to our partnership with ShipStation, Intelligent Order Management now saves users time with the capability to print shipping labels directly from its own application.
We are also making updates to system functionality such as adding internal to external ID transformation. With internal to external ID transformation, users can establish different mappings with different providers. For example, a user can map different names for the same product or SKU from an e-commerce system, such as BigCommerce, to Intelligent Order Management. This type of internal to external ID mapping is critical because Intelligent Order Management is used in complex order environments where data is communicated between many internal and external systems.
We have also added localized Business Event definitions and Provider definition metadata to localizations. The updates to localization also extended localization beyond English to the following languages: Arabic, Danish, Dutch, German, Italian, Japanese, and Spanish.
Additionally, users will now enjoy an enriched Power BI architecture including a set of dashboards embedded into the user interface that is based on Microsoft Power BI technology. The Power BI dashboards provide longer-range insights into the order and fulfillment data that is moving through the app.
According to a recent “final mile” survey by Gartner, just 18 percent of organizations report fulfillment accuracy rates of 95 percent or better4. At Microsoft, we believe that digital solutions are a promising path to improving this key performance indicator, and our new Order insights dashboard can help companies do exactly that.
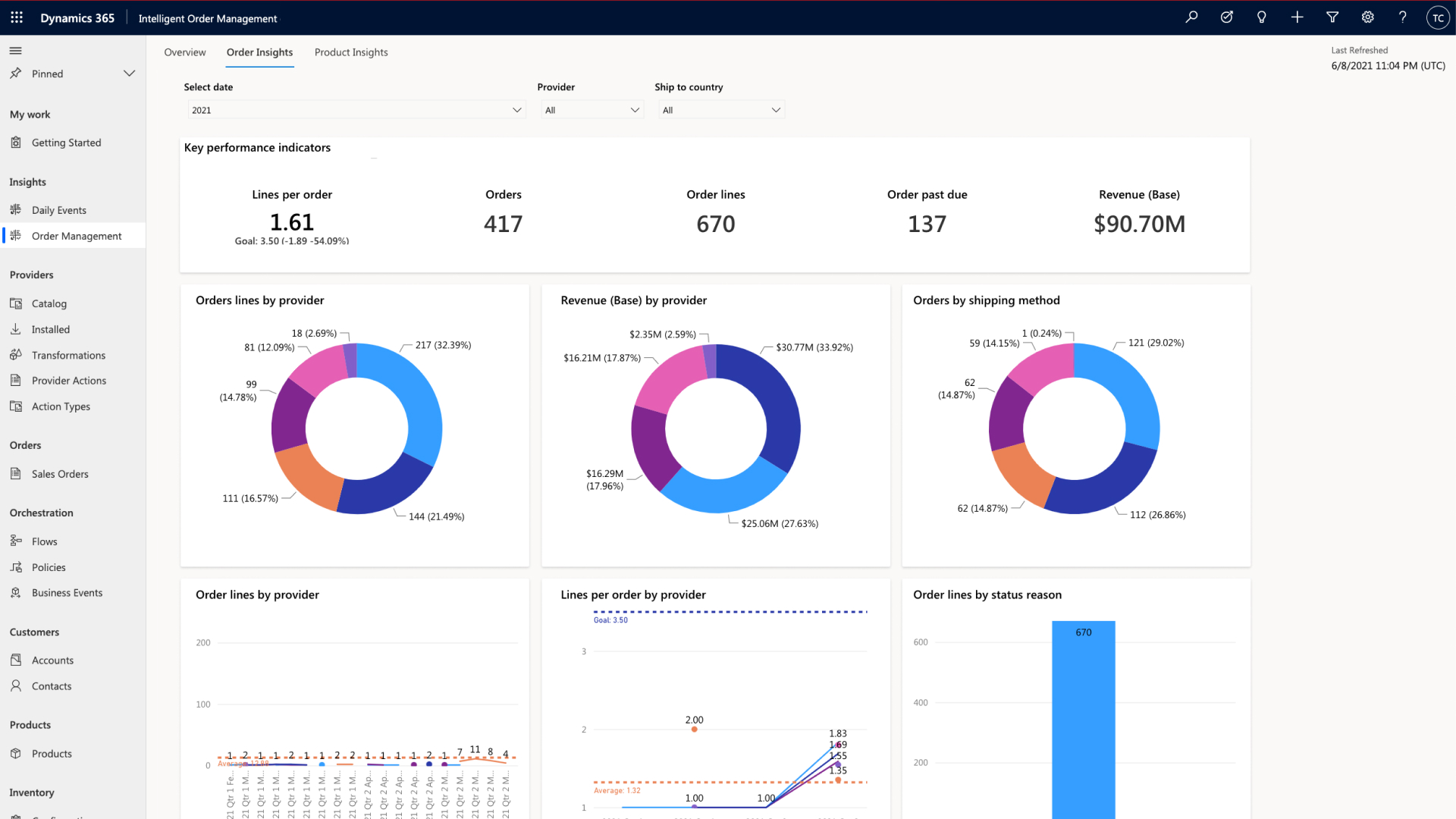
The order insights dashboard (shown above) provides in-depth visibility into aggregated order fulfillment activities flowing through Intelligent Order Management. From a single screen, users can quickly review key performance indicators such as Lines per order on average, Order count, Number of order lines, and Orders past due. Users can also see performance metrics of individual providers, and if there is an issue, they can drill down into the provider’s details to learn more.
Within the Insights menu, we have also introduced different dashboard views to provide users with the whole picture of what is happening with an order. For example, the Daily Events dashboard gives users an overview of any failed order orchestration steps, flagging them to help in the decision-making process.
Learn more in our recent webinar: Turn Order Fulfillment into a Competitive Advantage
As businesses continue to improve their ability to quickly adapt to changing demands, they must rely on flexible solutions like Dynamics 365 Intelligent Order Management that seamlessly integrate with other best-of-breed applications. By providing organizations with the ability to scale rapidly, go to market faster, and improve order accuracy with fulfillment insights, we are enabling businesses to increase organizational agility.
If you are interested in seeing how these features can work for your organization, you can get started today with a free Dynamics 365 Intelligent Order Management trial.
1A Forrester Consulting Thought Leadership Paper Commissioned by Microsoft. The Digital Commerce Imperative. January 2021.
2 McKinsey, Resetting supply chains for the next normal. July 2020 | Article. By Knut Alicke, Richa Gupta, and Vera Trautwein.
3McKinsey, The impact of agility: How to shape your organization to compete. May 25, 2021 | Survey. By By Wouter Aghina, Christopher Handscomb, Olli Salo, and Shail Thaker.
4Gartner, Top Trends in Retail Digital Transformation and Innovation for 2021. 5 February 2021. By Kelsie Marian, Miriam Burt, Max Hammond, Hanna Karki, Robert Hetu, Sandeep Unni.
GARTNER is a registered trademark and service mark of the Gartner Inc., in the U.S. and internationally and is used herein with permission. All rights reserved.
The post Dynamics 365 Intelligent Order Management accelerates adaptability appeared first on Microsoft Dynamics 365 Blog.
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.
Recent Comments