by Scott Muniz | Sep 3, 2021 | Security, Technology
This article is contributed. See the original author and article here.
CISA has released a new CISA Insights, Risk Considerations for Managed Service Provider Customers (MSPs), which provides Managed Service Provider (MSP) customers a framework for reducing risk.
This framework is designed for government and private sector organizations of all sizes, and it suggests considerations for IT management planning, best practices, and tools for reducing overall risk. This resource divides guidance across these areas: (1) senior executives and boards of directors (strategic decision-making); (2) procurement professionals (operational decision-making); and (3) network administrators, systems administrators, and front-line cybersecurity staff (tactical decision-making).
Read CISA’s latest blog, visit: CISA.gov/blog/2021/09/02/going-beyond-assessing-security-practices-it- service-providers.
To view this CISA Insights, please visit: CISA.gov/publication/risk-considerations-msp-customers. For additional supply chain risk management information or resources, visit CISA.gov/ict-supply-chain-library.
by Scott Muniz | Sep 3, 2021 | Security, Technology
This article is contributed. See the original author and article here.
On August 25, 2021, Atlassian released security updates to address a remote code execution vulnerability (CVE-2021-26084) affecting Confluence Server and Data Center. Recently, CVE-2021-26084 has been detected in exploits in the wild. A remote attacker could exploit this vulnerability to take control of an affected system.
CISA urges users and administrators to review Atlassian Security Advisory 2021-08-25 and immediately apply the necessary updates.

by Scott Muniz | Sep 3, 2021 | Security
This article was originally posted by the FTC. See the original article here.
Whether you’re starting to assess the damage from Hurricane Ida, the recent flooding in Tennessee, the wildfires in the West, or another natural disaster, coping with the aftermath is never easy. But when scammers target people just trying to recover, it can be even worse. Here are ways to help you avoid common post-disaster scams.
- Be skeptical of anyone promising immediate clean-up and debris removal. Some may quote outrageous prices, demand payment up-front, or lack the skills needed.
- Check them out. Before you pay, ask for IDs, licenses, and proof of insurance. Don’t believe any promises that aren’t in writing.
- Never pay by wire transfer, gift card, cryptocurrency, or in cash. And never make the final payment until the work is done and you’re satisfied.
- Guard your personal information. Only scammers will say they’re a government official and then demand money or your credit card, bank account, or Social Security number.
- Know that FEMA doesn’t charge application fees. If someone wants money to help you qualify for FEMA funds, that’s probably a scam.
- Be wise to rental listing scams. Steer clear of people who tell you to wire money or ask for security deposits or rent before you’ve met or signed a lease.
- Spot disaster-related charity scams. Scammers will often try to make a quick profit from the misfortune of others. Check out the FTC’s advice on donating wisely and avoiding charity scams.
Please share this 8.5 x 11 infographic, Picking Up the Pieces after a Disaster, and social media image in your community. 
Bookmark Dealing with Weather Emergencies. If a weather event or disaster affects you, come back for more tips on recovery and information about your rights. Like all our materials, the site is mobile-friendly, so you’ll have ready access to information when and where you need it.
Suspect a scam? Report it to the FTC at ReportFraud.ftc.gov. Want information on the latest frauds and scams we’re seeing? Sign up for our consumer alerts.
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.
by Contributed | Sep 2, 2021 | Technology
This article is contributed. See the original author and article here.
Commercial organizations can now explore and validate Windows 11 and Windows 10, version 21H2 that will be released later this year.
Today, we released Windows 11 and the Windows 10, version 21H2 feature update for commercial preview. Organizations enrolled in the Windows Insider Program for Business can access these builds through all standard channels, including Windows Update, Windows Server Update Services (WSUS), Azure Marketplace, and the Windows Insider Program ISO download page. Along with commercial pre-release availability, we are also offering free support for commercial organizations running these builds. This means you can test these releases—and your preferred deployment methods—while remaining supported prior to general availability.
Access commercial previews using Windows Update or Windows Update for Business
Commercial devices configured for the Windows Insider Program Release Preview Channel via the Windows Update Settings page or via Windows Update for Business policy will automatically be offered Windows 11 as an optional upgrade provided that the device(s) meet the hardware requirements and have taken the September 1, 2021 optional cumulative update (KB5005101). If you do not wish to upgrade a device to Windows 11, simply select “Stay on Windows 10 for now”, at which point Windows 10, version 21H2 will be offered instead. Commercial devices in the Release Preview Channel that do not meet the hardware requirements necessary to support Windows 11 will be offered Windows 10, version 21H2 automatically instead.
Both previews are completely optional. You can choose to remain on your current version of Windows and continue to receive preview builds of quality updates for that version.
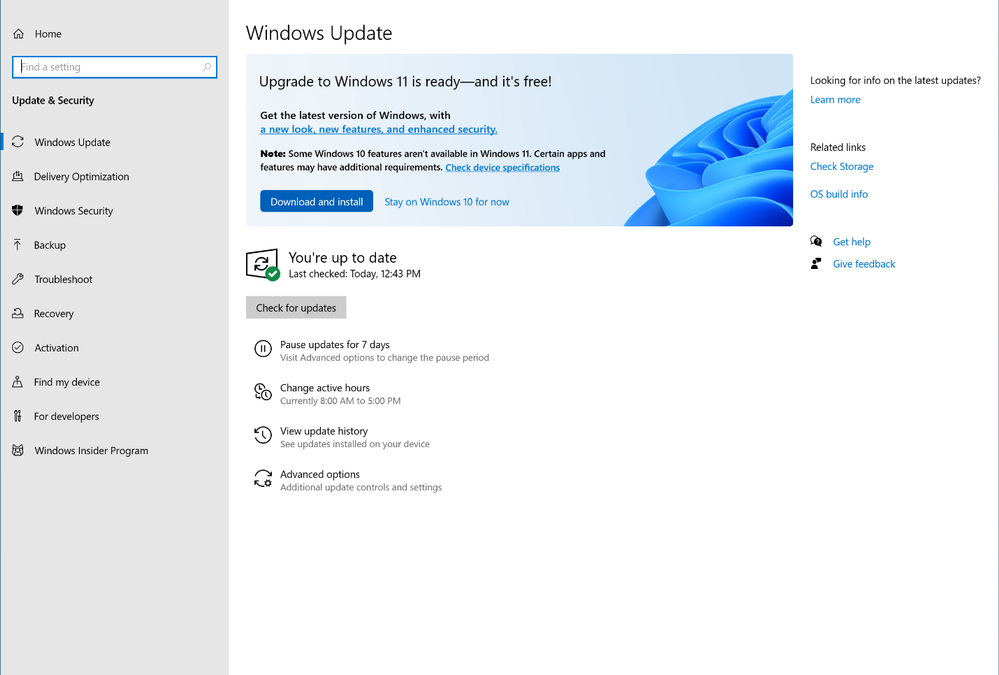
 The Windows Update interface showing that upgrade to Windows 11 is ready and free.
The Windows Update interface showing that upgrade to Windows 11 is ready and free.
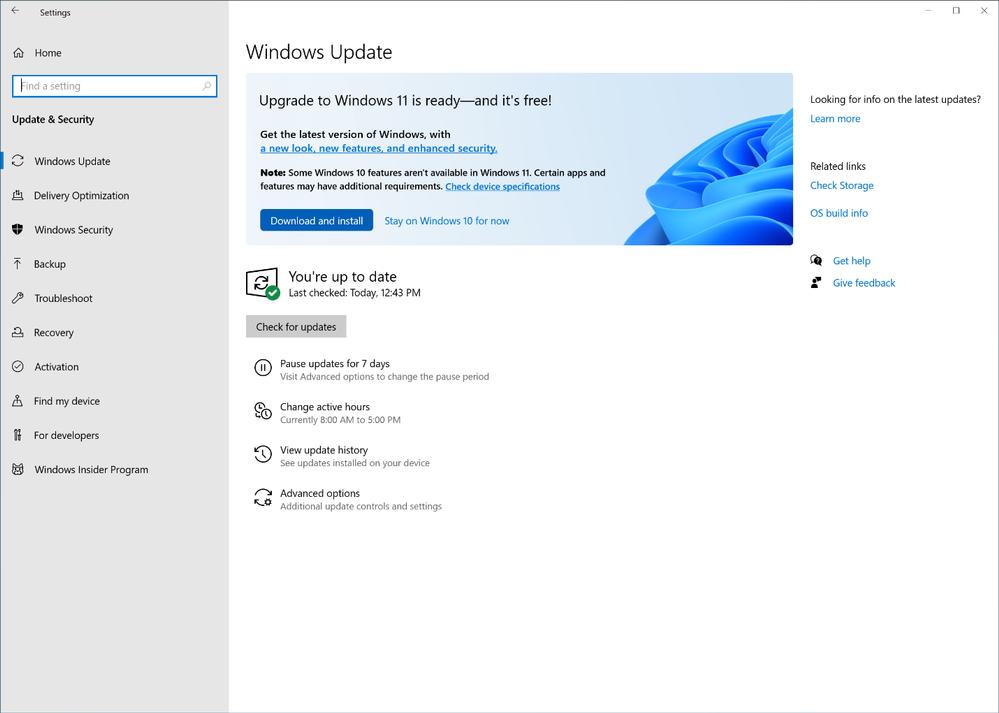
 The Windows Update view in Settings, showing as up to date
The Windows Update view in Settings, showing as up to date
If you are using MEM Intune, simply set “Servicing channel” to “Windows Insider – Release Preview”:
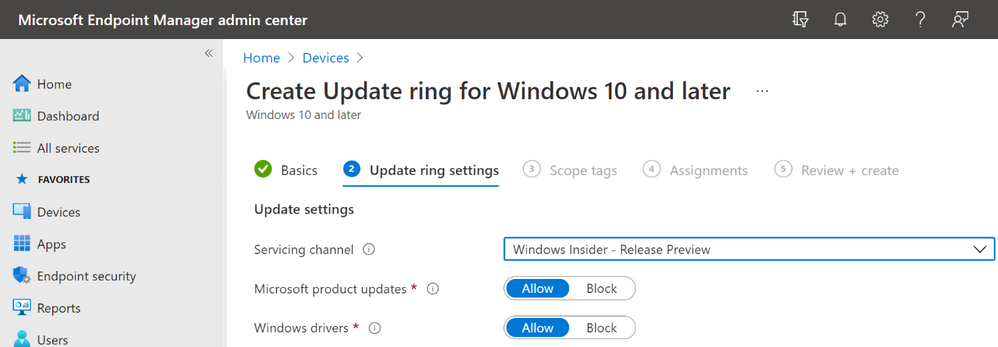 Setting Servicing channel to Windows Insider – Release Preview
Setting Servicing channel to Windows Insider – Release Preview
Note: We consider a device a commercial device if: a) it is not running Windows 10 Home edition; b) it is being managed by an IT administrator (whether via Microsoft Endpoint Manager or other endpoint management solution); or c) it has a volume license key or commercial ID, or is joined to a domain.
|
Access commercial previews using Windows Server Update Service (WSUS)
Both Windows 11 and Windows 10, version 21H2 are now available in the “Windows Insider Pre-release” category in WSUS and Microsoft Endpoint Manager (MEM) Configuration Manager. If you do not see them offered, simply sync the category and you will see them.
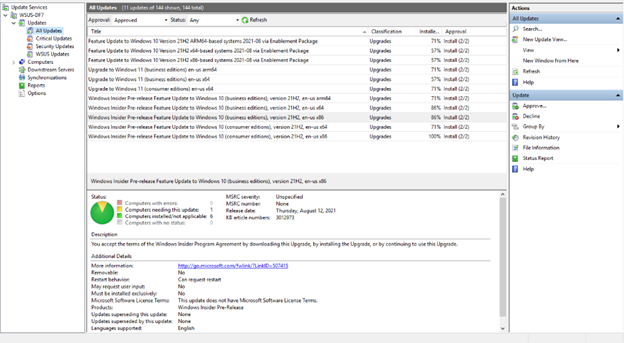 Windows 11 and Windows 10, version 21H2 are now available
Windows 11 and Windows 10, version 21H2 are now available
To access the Windows 11 preview build, devices must first take the September 1, 2021 optional cumulative update (KB 5005101). If a device is configured to send diagnostic data, but does not meet the hardware requirements, the Windows 11 upgrade will be marked as inapplicable in WSUS.
To access the Windows 10, version 21H2 preview build, devices running Windows 10, version 2004, version 20H2, or version 21H1 can leverage the enablement package path to update to version 21H2. Devices running versions prior to Windows 10, version 2004 will first need to do a full OS swap to receive Windows 10, version 21H2.
Access commercial previews from the Windows Insider Program ISO Download page
Simply go to the Windows Insider Program ISO Downloads site and select either the Windows 11 ISO (listed under Dev Channel and Beta Channel) or the Windows 10, version 21H2 ISO (listed under the Release Preview Channel).
Note: A clean installation will utilize your existing Windows 10 license keys or activate using Azure AD. No net new Windows 11 keys are required.
|
Access commercial previews through Azure Marketplace
On Azure Marketplace, we have added a new Windows 11 Preview offering with various images. For Windows 10, version 21H2, simply check out the Windows 10 Preview offering.
 Windows 11 Preview
Windows 11 Preview
Supporting your preview experience
Regardless of how you choose to deploy the release previews of either Windows 11 or Windows 10, version 21H2, we will keep you supported! If you encounter an issue, please report it to feedback hub or reach out to us directly through our free support offering for commercial organizations.
Microsoft is committed to ensuring your applications work on the latest versions of our software. Windows 11 has been built with compatibility in mind. Our promise states that apps that worked on Windows 7, 8.1, and 10 will work on Windows 11. If you experience a compatibility issue when deploying Windows 11 or Windows 10, version 21H2, you can utilize App Assure with Microsoft FastTrack to help remediate your application issues. App Assure will help troubleshoot the issue, determine the root cause, and fix the application. It is available at no additional cost for eligible customers with 150+ seats.
With that, we encourage you to go explore these releases, and don’t forget to reach out to me, @ariaupdated, on Twitter or message me on Tech Community with any feedback on how we can improve the Windows Insider Program for Business and our pre-release commercial offerings!
by Scott Muniz | Sep 2, 2021 | Security, Technology
This article is contributed. See the original author and article here.
Cisco has released security updates to address a critical vulnerability affecting Cisco Enterprise Network Function Virtualization Infrastructure Software (NFVIS) Release 4.5.1. A remote attacker could exploit this vulnerability to take control of an affected system. For updates addressing lower severity vulnerabilities, see the Cisco Security Advisories page.
CISA encourages users and administrators to review Cisco advisory cisco-sa-nfvis-g2DMVVh and apply the necessary update.









Recent Comments