
by Scott Muniz | Oct 25, 2021 | Security
This article was originally posted by the FTC. See the original article here.
 Every day dedicated community advocates work to improve the lives and protect the rights of people across the country. The FTC is proud of our work with the legal services community and we are excited to share the Community Advocate Center, a new resource to help you report to the FTC your clients’ experiences with fraud, scams, and bad business practices.
Every day dedicated community advocates work to improve the lives and protect the rights of people across the country. The FTC is proud of our work with the legal services community and we are excited to share the Community Advocate Center, a new resource to help you report to the FTC your clients’ experiences with fraud, scams, and bad business practices.
We know that communities thrive when we work together. We also know that scammers target specific populations including people of color, speakers of other languages, and lower-income communities. When advocates tell us people’s stories through ReportFraud.ftc.gov, the FTC can give tailored advice on next steps, including specific info about how to try to recover their money.
When you sign up for the Community Advocate Center, you’ll be joining colleagues from Legal Services Corporation, Inc. the National Legal Aid & Defender Association, the National Consumer Law Center, and the National Association of Consumer Advocates in supporting this initiative.
And please share this post and the video with your friends and colleagues and encourage them to use the Community Advocate Center on behalf of their clients.
The FTC cares about stopping scams you deal with, and preventing others from taking root. We use reports from your community to stop bad practices, get money back for your clients, and educate people about how to avoid the latest scams. Please sign up today: ReportFraud.ftc.gov/community
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.

by Scott Muniz | Oct 25, 2021 | Security, Technology
This article is contributed. See the original author and article here.

Official websites use .gov
A .gov website belongs to an official government organization in the United States.

Secure .gov websites use HTTPS A
lock ( )
) or
https:// means you’ve safely connected to the .gov website. Share sensitive information only on official, secure websites.
by Contributed | Oct 25, 2021 | Technology
This article is contributed. See the original author and article here.
Attackers are constantly evolving their phishing technique with sophisticated campaigns to subvert email protection systems like Microsoft Defender for Office 365 and make your security perimeters vulnerable. For this reason, it’s critical that SecOps professionals empower employees to be hypervigilant to such threats and report them as soon as they land in their inboxes.
Microsoft Defender for Office 365 has a fully automated detection and remediation system for emails, URLs and attachments that are reported by your employees. User and admin submissions are critical positive reinforcement signals for our machine learning based detection systems to review, triage, rapid-learn and mitigate attacks. The submission pipeline is a tightly integrated solution with automated mail-flow filters that protect your employees from similar threats.
You can learn here on how to report an email to Microsoft and manage your submissions here.
Once you report an email through the submission process, our system follows a set of actions. If you have any organizational compliance restrictions that prevents a user from reporting sensitive emails outside of your infrastructure, we recommend using the custom mailbox reporting option detailed here. This will ensure that user reported emails will come to your custom mailbox. Admins who are granted privileges to review those emails can then report them back to Microsoft.

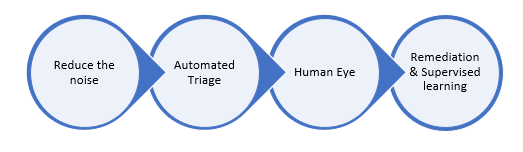
Figure 1: Behind the scenes post-submission process flow.
- Reduce the Noise: We wanted to reduce the noise from the submissions to ensure we send only clean signals for our automated triage system.
- Simulation: Your simulated messages from Attack Simulation Training or any of your 3rd party vendor will be filtered.
- Policy overrides: Wrongly classified messages due to your tenant’s ploicies or sometimes to end users’ policies are notified so that you can act at your end. From the override scenarios, we also honor your policies if they recommend detection improvements.
- Email Auth Check: We validate if the email authentication passed or failed during the email delivery.
You can learn about configuring 3rd party simulations here and learn about our secure by default strategy here.
- Automated Triage: We run our detection filters once again to identify if our systems have adapted between the time of delivery and your submission.
- All our machine learning based email filters will be run on your submissions to reclassify them in case of updated learning.
- In case of entities such as URLs and attachments in your submitted emails, we detonate them once again in our highly advanced sandbox environment to uncover the status of weaponization and assign the verdicts accordingly.
- We run a series of machine learning models exclusively on the reported submissions to identify, cluster the patterns and reclassify them in case of change in verdicts based on anomalies observed in similar submissions across our global customer base.
- We generate automated alerts on user reported phishing submissions by default and enable AIR (Automated Investigation and Response) so that these submissions will carry the verdicts from our automated triaging process. Please note that AIR is only available in MDO plan 2/E5/A5.
You can learn more about our AIR capabilities here.
- Human Eye: As the weaponization of phishing entities are dynamic, attackers constantly use multiple evasion techniques to bypass filters. That’s why a hybrid approach and human partnered machine learning based solution is the ideal method to stay on top of advanced threats and weaponization tricks.
- We prioritize submissions based on various factors such as phish severity, malware indicators, false positives, high volume anomalies, advanced pattern indicators, and whether reported by an admin or user.
- Expert graders/analysts are well trained on phish detection techniques and will be dissecting submissions through various Indicators of Compromise (IOC) and do deeper investigation on all email entities such as headers, URLs, attachments, and sender reputation to assign the right verdict on submissions.
- Graders generally deliver informed decisions as high-quality verdict signals that are being sent to the above discussed machine learning models 2(c) for continuous reinforcement learning.
- Human graded verdicts always take a higher priority and can override the verdict given by the automated triage process.
Human graders review anonymized email header and body metadata and hashed entities in a highly compliant environment that meets all the privacy guidelines from our Trust Center. You can learn more about Microsoft Trust Center here. You can also learn more about data storage here, and learn more about our data retention policies here.
- Remediation and supervised learning: The new verdict either from automated triage or human grader review will be sent for both rapid remediation and retrain our ML filters faster.
- We apply the graded labels from the automated triage system or human graders on the submitted and all related clusters belonging to this submitted pattern.
- We move all the messages from the current delivery location to the new location for all the impacted end users. For example, the system will move the messages from inbox to quarantine in case of ‘phish’ verdicts and move from Quarantine/Junk to inbox in case of ‘Good’ verdicts using our Zero-hour Auto Purge (ZAP) platform.
- We also identify IOCs by the submitted clusters and add them to our reputations to initiate instantaneous mitigation against phish and malware campaigns.
- Any new incoming mail from a similar pattern or IOC will be auto classified with the new verdict to reduce the triage load from your SecOps.
You can learn more about ZAP here.
The automated User Submission workflow is carefully designed with state-of-the-art technology to help the organizations to mitigate any False negative or False positive risks faster to reduce MTTR (Mean time to Response) for their SOC team. It also becomes important for organizations to enhance their security postures by training employees who actively participate in this phish detection submission feedback loop. Attack Simulation Training is included with Microsoft Defender for Office 365 P2 and E5 licenses and provides the necessary simulation and training capability that reduces phish vulnerabilities at the user-level. Learn more and get started using Attack Simulation Training here.
Do you have questions or feedback about Microsoft Defender for Office 365? Engage with the community and Microsoft experts in the Defender for Office 365 forum.

by Contributed | Oct 25, 2021 | Business, Microsoft 365, Technology
This article is contributed. See the original author and article here.
Hybrid work has become a part of our reality. We’ve had to rethink everything from where, when, and how we work. Navigating this new normal is both challenging and uncomfortable at times.
The post Gartner recognizes Microsoft as Leader in Unified Communications as a Service and Meetings Solutions appeared first on Microsoft 365 Blog.
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.

by Priyesh Wagh | Oct 25, 2021 | Dynamics 365, Microsoft, Technology
Here’s how you configure a Dataverse Search for a Dynamics 365 Instance from Power Platform Admin Center
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.

 Every day dedicated community advocates work to improve the lives and protect the rights of people across the country. The FTC is proud of our work with the legal services community and we are excited to share the Community Advocate Center, a new resource to help you report to the FTC your clients’ experiences with fraud, scams, and bad business practices.
Every day dedicated community advocates work to improve the lives and protect the rights of people across the country. The FTC is proud of our work with the legal services community and we are excited to share the Community Advocate Center, a new resource to help you report to the FTC your clients’ experiences with fraud, scams, and bad business practices. 



Recent Comments