by Scott Muniz | Oct 25, 2021 | Security, Technology
This article is contributed. See the original author and article here.
| auvesy — versiondog |
A specific function code receives a raw pointer supplied by the user and deallocates this pointer. The user can then control what memory regions will be freed and cause use-after-free condition. |
2021-10-22 |
not yet calculated |
CVE-2021-38467
CONFIRM |
adobe — connect
|
Adobe Connect version 11.2.2 (and earlier) is affected by a Deserialization of Untrusted Data vulnerability to achieve arbitrary method invocation when AMF messages are deserialized on an Adobe Connect server. An attacker can leverage this to execute remote code execution on the server. |
2021-10-21 |
not yet calculated |
CVE-2021-40719
MISC |
ancom — wlan_controllers
|
ANCOM WLAN Controller (Wireless Series & Hotspot) WLC-1000 & WLC-4006 was discovered to contain multiple cross-site scripting (XSS) vulnerabilities in the /authen/start/ module via the userid and password parameters. |
2021-10-22 |
not yet calculated |
CVE-2020-23055
MISC |
aplioxio — pdf_shapingup
|
Aplioxio PDF ShapingUp 5.0.0.139 contains a buffer overflow which allows attackers to cause a denial of service (DoS) via a crafted PDF file. |
2021-10-22 |
not yet calculated |
CVE-2020-28969
MISC |
| apple — multiple_products |
This issue was addressed with improved checks. This issue is fixed in iOS 14.8 and iPadOS 14.8, macOS Big Sur 11.6, Security Update 2021-005 Catalina, tvOS 15, iOS 15 and iPadOS 15, watchOS 8. Processing a maliciously crafted dfont file may lead to arbitrary code execution. |
2021-10-19 |
not yet calculated |
CVE-2021-30842
MISC
MISC
MISC
MISC
MISC
MISC |
| apple — multiple_products |
This issue was addressed with improved checks. This issue is fixed in watchOS 8, macOS Big Sur 11.6, Security Update 2021-005 Catalina, tvOS 15, iOS 15 and iPadOS 15, iTunes 12.12 for Windows. Processing a maliciously crafted image may lead to arbitrary code execution. |
2021-10-19 |
not yet calculated |
CVE-2021-30847
MISC
MISC
MISC
MISC
MISC
MISC |
apple — multiple_products
|
This issue was addressed with improved checks. This issue is fixed in iOS 14.8 and iPadOS 14.8, macOS Big Sur 11.6, Security Update 2021-005 Catalina, tvOS 15, iOS 15 and iPadOS 15, watchOS 8. Processing a maliciously crafted dfont file may lead to arbitrary code execution. |
2021-10-19 |
not yet calculated |
CVE-2021-30843
MISC
MISC
MISC
MISC
MISC
MISC |
apple — multiple_products
|
This issue was addressed with improved checks. This issue is fixed in iOS 14.8 and iPadOS 14.8, macOS Big Sur 11.6, Security Update 2021-005 Catalina, tvOS 15, iOS 15 and iPadOS 15, watchOS 8. Processing a maliciously crafted dfont file may lead to arbitrary code execution. |
2021-10-19 |
not yet calculated |
CVE-2021-30841
MISC
MISC
MISC
MISC
MISC
MISC |
apple — multiple_products
|
A memory corruption issue was addressed with improved memory handling. This issue is fixed in iOS 14.8 and iPadOS 14.8, Safari 15, iOS 15 and iPadOS 15. Processing maliciously crafted web content may lead to code execution. |
2021-10-19 |
not yet calculated |
CVE-2021-30848
MISC
MISC
MISC |
apple — multiple_products
|
Multiple memory corruption issues were addressed with improved memory handling. This issue is fixed in iOS 14.8 and iPadOS 14.8, watchOS 8, Safari 15, tvOS 15, iOS 15 and iPadOS 15, iTunes 12.12 for Windows. Processing maliciously crafted web content may lead to arbitrary code execution. |
2021-10-19 |
not yet calculated |
CVE-2021-30849
MISC
MISC
MISC
MISC
MISC
MISC |
apple — multiple_products
|
An access issue was addressed with improved access restrictions. This issue is fixed in Security Update 2021-005 Catalina, macOS Big Sur 11.6, tvOS 15. A user may gain access to protected parts of the file system. |
2021-10-19 |
not yet calculated |
CVE-2021-30850
MISC
MISC
MISC |
apple — multiple_products
|
This issue was addressed with improved checks. This issue is fixed in Security Update 2021-005 Catalina, iTunes 12.12 for Windows, tvOS 15, iOS 15 and iPadOS 15, watchOS 8. Processing a maliciously crafted image may lead to arbitrary code execution. |
2021-10-19 |
not yet calculated |
CVE-2021-30835
MISC
MISC
MISC
MISC
MISC |
arista — eos_and_cloudeos
|
On systems running Arista EOS and CloudEOS with the affected release version, when using shared secret profiles the password configured for use by BiDirectional Forwarding Detection (BFD) will be leaked when displaying output over eAPI or other JSON outputs to other authenticated users on the device. The affected EOS Versions are: all releases in 4.22.x train, 4.23.9 and below releases in the 4.23.x train, 4.24.7 and below releases in the 4.24.x train, 4.25.4 and below releases in the 4.25.x train, 4.26.1 and below releases in the 4.26.x train |
2021-10-21 |
not yet calculated |
CVE-2021-28496
MISC |
arris — surfboard_sb8200
|
The administration web interface for the Arris Surfboard SB8200 lacks any protections against cross-site request forgery attacks. This means that an attacker could make configuration changes (such as changing the administrative password) without the consent of the user. |
2021-10-21 |
not yet calculated |
CVE-2021-20120
MISC |
atlassian — jira_server
|
Affected versions of Atlassian Jira Server and Data Center allow remote attackers to modify various resources via a Cross-Site Request Forgery (CSRF) vulnerability, following an Information Disclosure vulnerability in the referrer headers which discloses a user’s CSRF token. The affected versions are before version 8.5.10, and from version 8.6.0 before 8.13.2. |
2021-10-21 |
not yet calculated |
CVE-2021-39126
MISC |
atlassian — jira_server
|
Affected versions of Atlassian Jira Server and Data Center allow anonymous remote attackers to the query component JQL endpoint via a Broken Access Control vulnerability (BAC) vulnerability. The affected versions are before version 8.5.10, and from version 8.6.0 before 8.13.1. |
2021-10-21 |
not yet calculated |
CVE-2021-39127
MISC |
automated_logic — webctrl/webctrl
|
The login portal for the Automated Logic WebCTRL/WebCTRL OEM web application contains a vulnerability that allows for reflected XSS attacks due to the operatorlocale GET parameter not being sanitized. This issue impacts versions 6.5 and below. This issue works by passing in a basic XSS payload to a vulnerable GET parameter that is reflected in the output without sanitization. |
2021-10-22 |
not yet calculated |
CVE-2021-31682
MISC
MISC |
| auvesy — versiondog |
Many API function codes receive raw pointers remotely from the user and trust these pointers as valid in-bound memory regions. An attacker can manipulate API functions by writing arbitrary data into the resolved address of a raw pointer. |
2021-10-22 |
not yet calculated |
CVE-2021-38479
CONFIRM |
| auvesy — versiondog |
Some API functions permit by-design writing or copying data into a given buffer. Since the client controls these parameters, an attacker could rewrite the memory in any location of the affected product. |
2021-10-22 |
not yet calculated |
CVE-2021-38449
CONFIRM |
| auvesy — versiondog |
There are multiple API function codes that permit data writing to any file, which may allow an attacker to modify existing files or create new files. |
2021-10-22 |
not yet calculated |
CVE-2021-38471
CONFIRM |
| auvesy — versiondog |
The affected product’s code base doesn’t properly control arguments for specific functions, which could lead to a stack overflow. |
2021-10-22 |
not yet calculated |
CVE-2021-38473
CONFIRM |
| auvesy — versiondog |
The affected product’s proprietary protocol CSC allows for calling numerous function codes. In order to call those function codes, the user must supply parameters. There is no sanitation on the value of the offset, which allows the client to specify any offset and read out-of-bounds data. |
2021-10-22 |
not yet calculated |
CVE-2021-38451
CONFIRM |
| auvesy — versiondog |
The webinstaller is a Golang web server executable that enables the generation of an Auvesy image agent. Resource consumption can be achieved by generating large amounts of installations, which are then saved without limitation in the temp folder of the webinstaller executable. |
2021-10-22 |
not yet calculated |
CVE-2021-38465
CONFIRM |
auvesy — versiondog
|
Some API functions allow interaction with the registry, which includes reading values as well as data modification. |
2021-10-22 |
not yet calculated |
CVE-2021-38453
CONFIRM |
auvesy — versiondog
|
Many of the services used by the affected product do not specify full paths for the DLLs they are loading. An attacker can exploit the uncontrolled search path by implanting their own DLL near the affected product’s binaries, thus hijacking the loaded DLL. |
2021-10-22 |
not yet calculated |
CVE-2021-38469
CONFIRM |
auvesy — versiondog
|
The affected product’s OS Service does not verify any given parameter. A user can supply any type of parameter that will be passed to inner calls without checking the type of the parameter or the value. |
2021-10-22 |
not yet calculated |
CVE-2021-38455
CONFIRM |
auvesy — versiondog
|
The server permits communication without any authentication procedure, allowing the attacker to initiate a session with the server without providing any form of authentication. |
2021-10-22 |
not yet calculated |
CVE-2021-38457
CONFIRM |
auvesy — versiondog
|
There are multiple API function codes that permit reading and writing data to or from files and directories, which could lead to the manipulation and/or the deletion of files. |
2021-10-22 |
not yet calculated |
CVE-2021-38477
CONFIRM |
auvesy — versiondog
|
The database connection to the server is performed by calling a specific API, which could allow an unprivileged user to gain SYSDBA permissions. |
2021-10-22 |
not yet calculated |
CVE-2021-38475
CONFIRM |
auvesy — versiondog
|
The affected product uses a hard-coded blowfish key for encryption/decryption processes. The key can be easily extracted from binaries. |
2021-10-22 |
not yet calculated |
CVE-2021-38461
CONFIRM |
auvesy — versiondog
|
The affected product does not properly control the allocation of resources. A user may be able to allocate unlimited memory buffers using API functions. |
2021-10-22 |
not yet calculated |
CVE-2021-38463
CONFIRM |
auvesy — versiondog
|
The data of a network capture of the initial handshake phase can be used to authenticate at a SYSDBA level. If a specific .exe is not restarted often, it is possible to access the needed handshake packets between admin/client connections. Using the SYSDBA permission, an attacker can change user passwords or delete the database. |
2021-10-22 |
not yet calculated |
CVE-2021-38459
CONFIRM |
auvesy — versiondog
|
The scheduler service running on a specific TCP port enables the user to start and stop jobs. There is no sanitation of the supplied JOB ID provided to the function. An attacker may send a malicious payload that can enable the user to execute another SQL expression by sending a specific string. |
2021-10-22 |
not yet calculated |
CVE-2021-38481
CONFIRM |
babel — locale
|
Babel.Locale in Babel before 2.9.1 allows attackers to load arbitrary locale .dat files (containing serialized Python objects) via directory traversal, leading to code execution. |
2021-10-20 |
not yet calculated |
CVE-2021-42771
MISC
MISC
MISC
MLIST |
bqe — billquick_web_suite
|
BQE BillQuick Web Suite 2018 through 2021 before 22.0.9.1 allows SQL injection for unauthenticated remote code execution, as exploited in the wild in October 2021 for ransomware installation. SQL injection can, for example, use the txtID (aka username) parameter. Successful exploitation can include the ability to execute arbitrary code as MSSQLSERVER$ via xp_cmdshell. |
2021-10-22 |
not yet calculated |
CVE-2021-42258
MISC |
browsers — harmony_browse_and_sandblast)agent
|
The Harmony Browse and the SandBlast Agent for Browsers installers must have admin privileges to execute some steps during the installation. Because the MS Installer allows regular users to repair their installation, an attacker running an installer before 90.08.7405 can start the installation repair and place a specially crafted binary in the repair folder, which runs with the admin privileges. |
2021-10-22 |
not yet calculated |
CVE-2021-30359
MISC
MISC |
| cameleon — cms |
In Camaleon CMS, versions 2.0.1 to 2.6.0 are vulnerable to an Uncaught Exception. The app’s media upload feature crashes permanently when an attacker with a low privileged access uploads a specially crafted .svg file |
2021-10-20 |
not yet calculated |
CVE-2021-25971
MISC
MISC |
| cameleon — cms |
Camaleon CMS 0.1.7 to 2.6.0 doesn’t terminate the active session of the users, even after the admin changes the user’s password. A user that was already logged in, will still have access to the application even after the password was changed. |
2021-10-20 |
not yet calculated |
CVE-2021-25970
MISC
MISC |
cameleon — cms
|
In “Camaleon CMS” application, versions 0.0.1 to 2.6.0 are vulnerable to stored XSS, that allows unprivileged application users to store malicious scripts in the comments section of the post. These scripts are executed in a victim’s browser when they open the page containing the malicious comment. |
2021-10-20 |
not yet calculated |
CVE-2021-25969
MISC
MISC |
cameleon — cms
|
In Camaleon CMS, versions 2.1.2.0 to 2.6.0, are vulnerable to Server-Side Request Forgery (SSRF) in the media upload feature, which allows admin users to fetch media files from external URLs but fails to validate URLs referencing to localhost or other internal servers. This allows attackers to read files stored in the internal server. |
2021-10-20 |
not yet calculated |
CVE-2021-25972
MISC
MISC |
catalyst_it_ltd — mahara_cms
|
Catalyst IT Ltd Mahara CMS v19.10.2 was discovered to contain multiple cross-site scripting (XSS) vulnerabilities in the component groupfiles.php via the Number (Nombre) and Description (Descripción) parameters. |
2021-10-22 |
not yet calculated |
CVE-2020-23052
MISC |
chicehn_tech — cms
|
Chichen Tech CMS v1.0 was discovered to contain multiple SQL injection vulnerabilities in the file product_list.php via the id and cid parameters. |
2021-10-22 |
not yet calculated |
CVE-2020-28960
MISC |
cisco — identity_services_engine
|
Multiple vulnerabilities in the web-based management interface of Cisco Identity Services Engine (ISE) Software could allow an attacker to conduct a cross-site scripting (XSS) attack against a user of the interface. For more information about these vulnerabilities, see the Details section of this advisory. |
2021-10-21 |
not yet calculated |
CVE-2021-34738
CISCO |
cisco — identity_services_engine
|
A vulnerability in the web-based management interface of Cisco Identity Services Engine (ISE) could allow an authenticated, remote attacker with administrative read-only privileges to download files that should be restricted. This vulnerability is due to incorrect permissions settings on an affected device. An attacker could exploit this vulnerability by sending a crafted HTTP request to the device. A successful exploit could allow the attacker to download files that should be restricted. |
2021-10-21 |
not yet calculated |
CVE-2021-40123
CISCO |
cisco — identity_services_engine
|
Multiple vulnerabilities in the web-based management interface of Cisco Identity Services Engine (ISE) Software could allow an attacker to conduct a cross-site scripting (XSS) attack against a user of the interface. For more information about these vulnerabilities, see the Details section of this advisory. |
2021-10-21 |
not yet calculated |
CVE-2021-40121
CISCO |
cisco — integrated_management_controller
|
A vulnerability in the web-based management interface of Cisco Integrated Management Controller (IMC) Software could allow an unauthenticated, remote attacker to cause the web-based management interface to unexpectedly restart. The vulnerability is due to insufficient input validation on the web-based management interface. An attacker could exploit this vulnerability by sending a crafted HTTP request to an affected device. A successful exploit could allow the attacker to cause the interface to restart, resulting in a denial of service (DoS) condition. |
2021-10-21 |
not yet calculated |
CVE-2021-34736
CISCO |
cisco — ios_xe_sd-wan_software
|
A vulnerability in the CLI of Cisco IOS XE SD-WAN Software could allow an authenticated, local attacker to execute arbitrary commands with root privileges. The vulnerability is due to insufficient input validation by the system CLI. An attacker could exploit this vulnerability by authenticating to an affected device and submitting crafted input to the system CLI. A successful exploit could allow the attacker to execute commands on the underlying operating system with root privileges. |
2021-10-21 |
not yet calculated |
CVE-2021-1529
CISCO |
cisco — meeting_server
|
A vulnerability in an API of the Call Bridge feature of Cisco Meeting Server could allow an unauthenticated, remote attacker to cause a denial of service (DoS) condition. This vulnerability is due to improper handling of large series of message requests. An attacker could exploit this vulnerability by sending a series of messages to the vulnerable API. A successful exploit could allow the attacker to cause the affected device to reload, dropping all ongoing calls and resulting in a DoS condition. |
2021-10-21 |
not yet calculated |
CVE-2021-40122
CISCO |
cisco — telepresence_management_suite
|
A vulnerability in the web-based management interface of Cisco TelePresence Management Suite (TMS) Software could allow an authenticated, remote attacker to conduct a cross-site scripting (XSS) attack against a user of the interface. This vulnerability is due to insufficient input validation by the web-based management interface. An attacker could exploit this vulnerability by inserting malicious data in a specific data field in the interface. A successful exploit could allow the attacker to execute arbitrary script code in the context of the affected interface or access sensitive, browser-based information. |
2021-10-21 |
not yet calculated |
CVE-2021-34760
CISCO |
cisco — tetration
|
A vulnerability in the web-based management interface of Cisco Tetration could allow an authenticated, remote attacker to perform a stored cross-site scripting (XSS) attack on an affected system. This vulnerability exists because the web-based management interface does not sufficiently validate user-supplied input. An attacker could exploit this vulnerability by injecting malicious code into specific pages of the interface. A successful exploit could allow the attacker to execute arbitrary script code in the context of the affected interface or access sensitive, browser-based information. To exploit this vulnerability, the attacker would need valid administrative credentials. |
2021-10-21 |
not yet calculated |
CVE-2021-34789
CISCO |
cisco — webex_software
|
A vulnerability in the application integration feature of Cisco Webex Software could allow an unauthenticated, remote attacker to authorize an external application to integrate with and access a user’s account without that user’s express consent. This vulnerability is due to improper validation of cross-site request forgery (CSRF) tokens. An attacker could exploit this vulnerability by convincing a targeted user who is currently authenticated to Cisco Webex Software to follow a link designed to pass malicious input to the Cisco Webex Software application authorization interface. A successful exploit could allow the attacker to cause Cisco Webex Software to authorize an application on the user’s behalf without the express consent of the user, possibly allowing external applications to read data from that user’s profile. |
2021-10-21 |
not yet calculated |
CVE-2021-34743
CISCO |
civetweb — civetweb
|
The CivetWeb web library does not validate uploaded filepaths when running on an OS other than Windows, when using the built-in HTTP form-based file upload mechanism, via the mg_handle_form_request API. Web applications that use the file upload form handler, and use parts of the user-controlled filename in the output path, are susceptible to directory traversal |
2021-10-21 |
not yet calculated |
CVE-2020-27304
MISC
MISC |
cosmos — sdk
|
The Cosmos-SDK is a framework for building blockchain applications in Golang. Affected versions of the SDK were vulnerable to a consensus halt due to non-deterministic behaviour in a ValidateBasic method in the x/authz module. The MsgGrant of the x/authz module contains a Grant field which includes a user-defined expiration time for when the authorization grant expires. In Grant.ValidateBasic(), that time is compared to the node’s local clock time. Any chain running an affected version of the SDK with the authz module enabled could be halted by anyone with the ability to send transactions on that chain. Recovery would require applying the patch and rolling back the latest block. Users are advised to update to version 0.44.2. |
2021-10-20 |
not yet calculated |
CVE-2021-41135
MISC
CONFIRM
MISC |
csdn — app_4
|
Cross-Site Scripting (XSS) vulnerability exists in Csdn APP 4.10.0, which can be exploited by attackers to obtain sensitive information such as user cookies. |
2021-10-22 |
not yet calculated |
CVE-2021-41747
MISC
MISC |
| dedecms — dedecms |
DedeCMS v7.5 SP2 was discovered to contain multiple cross-site scripting (XSS) vulnerabilities in the component sys_admin_user_edit.php via the `filename`, `mid`, `userid`, and `templet’ parameters. |
2021-10-22 |
not yet calculated |
CVE-2020-36496
MISC |
| dedecms — dedecms |
DedeCMS v7.5 SP2 was discovered to contain multiple cross-site scripting (XSS) vulnerabilities in the component mychannel_edit.php via the `filename`, `mid`, `userid`, and `templet’ parameters. |
2021-10-22 |
not yet calculated |
CVE-2020-36494
MISC |
| dedecms — dedecms |
DedeCMS v7.5 SP2 was discovered to contain multiple cross-site scripting (XSS) vulnerabilities in the component select_media.php via the `activepath`, `keyword`, `tag`, `fmdo=x&filename`, `CKEditor` and `CKEditorFuncNum` parameters. |
2021-10-22 |
not yet calculated |
CVE-2020-36492
MISC |
dedecms — dedecms
|
DedeCMS v7.5 SP2 was discovered to contain multiple cross-site scripting (XSS) vulnerabilities in the component makehtml_homepage.php via the `filename`, `mid`, `userid`, and `templet’ parameters. |
2021-10-22 |
not yet calculated |
CVE-2020-36497
MISC |
dedecms — dedecms
|
DedeCMS v7.5 SP2 was discovered to contain multiple cross-site scripting (XSS) vulnerabilities in the component file_manage_view.php via the `filename`, `mid`, `userid`, and `templet’ parameters. |
2021-10-22 |
not yet calculated |
CVE-2020-36495
MISC |
dedecms — dedecms
|
DedeCMS v7.5 SP2 was discovered to contain multiple cross-site scripting (XSS) vulnerabilities in the component media_main.php via the `activepath`, `keyword`, `tag`, `fmdo=x&filename`, `CKEditor` and `CKEditorFuncNum` parameters. |
2021-10-22 |
not yet calculated |
CVE-2020-36493
MISC |
dedecms — dedecms
|
DedeCMS v7.5 SP2 was discovered to contain multiple cross-site scripting (XSS) vulnerabilities in the component tpl.php via the `filename`, `mid`, `userid`, and `templet’ parameters. |
2021-10-22 |
not yet calculated |
CVE-2020-23046
MISC |
dedecms — dedecms
|
DedeCMS v7.5 SP2 was discovered to contain multiple cross-site scripting (XSS) vulnerabilities in the component file_pic_view.php via the `activepath`, `keyword`, `tag`, `fmdo=x&filename`, `CKEditor` and `CKEditorFuncNum` parameters. |
2021-10-22 |
not yet calculated |
CVE-2020-23044
MISC |
dedecms — dedecms
|
DedeCMS v7.5 SP2 was discovered to contain multiple cross-site scripting (XSS) vulnerabilities in the component tags_main.php via the `activepath`, `keyword`, `tag`, `fmdo=x&filename`, `CKEditor` and `CKEditorFuncNum` parameters. |
2021-10-22 |
not yet calculated |
CVE-2020-36491
MISC |
dedecms — dedecms
|
DedeCMS v7.5 SP2 was discovered to contain multiple cross-site scripting (XSS) vulnerabilities in the component file_manage_view.php via the `activepath`, `keyword`, `tag`, `fmdo=x&filename`, `CKEditor` and `CKEditorFuncNum` parameters. |
2021-10-22 |
not yet calculated |
CVE-2020-36490
MISC |
discourse — discourse
|
Discourse is an open source platform for community discussion. In affected versions maliciously crafted requests could lead to remote code execution. This resulted from a lack of validation in subscribe_url values. This issue is patched in the latest stable, beta and tests-passed versions of Discourse. To workaround the issue without updating, requests with a path starting /webhooks/aws path could be blocked at an upstream proxy. |
2021-10-20 |
not yet calculated |
CVE-2021-41163
CONFIRM
MISC |
draytek — vigorap_1000c
|
Draytek VigorAP 1000C contains a stored cross-site scripting (XSS) vulnerability in the RADIUS Setting – RADIUS Server Configuration module. This vulnerability allows attackers to execute arbitrary web scripts or HTML via a crafted payload in the username input field. |
2021-10-22 |
not yet calculated |
CVE-2020-28968
MISC |
dropouts_technoligies_llp — air_share
|
Dropouts Technologies LLP Air Share v1.2 was discovered to contain a cross-site scripting (XSS) vulnerability in the devicename parameter. This vulnerability allows attackers to execute arbitrary web scripts or HTML via a crafted payload in the devicename information. |
2021-10-22 |
not yet calculated |
CVE-2020-36489
MISC |
dropouts_technologies_llp — air_share
|
Dropouts Technologies LLP Air Share v1.2 was discovered to contain a cross-site scripting (XSS) vulnerability in the path parameter of the `list` and `download` exception-handling. This vulnerability allows attackers to execute arbitrary web scripts or HTML via a crafted GET request. |
2021-10-22 |
not yet calculated |
CVE-2020-23041
MISC |
| dropouts_technologies_llp — super_backup |
Dropouts Technologies LLP Super Backup v2.0.5 was discovered to contain a cross-site scripting (XSS) vulnerability in the path parameter of the `list` and `download` module. This vulnerability allows attackers to execute arbitrary web scripts or HTML via a crafted GET request. |
2021-10-22 |
not yet calculated |
CVE-2020-23042
MISC |
droupouts_technologies_llp — super_backup
|
Dropouts Technologies LLP Super Backup v2.0.5 was discovered to contain an issue in the path parameter of the `list` and `download` module which allows attackers to perform a directory traversal via a change to the path variable to request the local list command. |
2021-10-22 |
not yet calculated |
CVE-2020-23061
MISC |
elabftw — elabftw
|
eLabFTW is an open source electronic lab notebook manager for research teams. In versions of eLabFTW before 4.1.0, it allows attackers to bypass a brute-force protection mechanism by using many different forged PHPSESSID values in HTTP Cookie header. This issue has been addressed by implementing brute force login protection, as recommended by Owasp with Device Cookies. This mechanism will not impact users and will effectively thwart any brute-force attempts at guessing passwords. The only correct way to address this is to upgrade to version 4.1.0. Adding rate limitation upstream of the eLabFTW service is of course a valid option, with or without upgrading. |
2021-10-22 |
not yet calculated |
CVE-2021-41171
CONFIRM
MISC
MISC
MISC
MISC |
| emerson — wirelesshart_gateway |
The affected product is vulnerable to improper input validation in the restore file. This enables an attacker to provide malicious config files to replace any file on disk. |
2021-10-22 |
not yet calculated |
CVE-2021-38485
CONFIRM |
| etherum — etherum |
The Proof-of-Stake (PoS) Ethereum consensus protocol through 2021-10-19 allows an adversary to leverage network delay to cause a denial of service (indefinite stalling of consensus decisions). |
2021-10-20 |
not yet calculated |
CVE-2021-42765
MISC |
etherum — etherum
|
The Proof-of-Stake (PoS) Ethereum consensus protocol through 2021-10-19 allows an adversary to cause a denial of service (long-range consensus chain reorganizations), even when this adversary has little stake and cannot influence network message propagation. This can cause a protocol stall, or an increase in the profits of individual validators. |
2021-10-20 |
not yet calculated |
CVE-2021-42766
MISC |
etherum — etherum
|
The Proof-of-Stake (PoS) Ethereum consensus protocol through 2021-10-19 allows an adversary to cause a denial of service (delayed consensus decisions), and also increase the profits of individual validators, via short-range reorganizations of the underlying consensus chain. |
2021-10-20 |
not yet calculated |
CVE-2021-42764
MISC |
flashget — flashget
|
FlashGet v1.9.6 was discovered to contain a buffer overflow in the ‘current path directory’ function. This vulnerability allows attackers to elevate local process privileges via overwriting the registers. |
2021-10-22 |
not yet calculated |
CVE-2020-28967
MISC |
folder_lock — folder_lock
|
Folder Lock v3.4.5 was discovered to contain a stored cross-site scripting (XSS) vulnerability in the Create Folder function under the ‘create’ module. This vulnerability allows attackers to execute arbitrary web scripts or HTML via a crafted payload as a path or folder name. |
2021-10-22 |
not yet calculated |
CVE-2020-23039
MISC |
fork_cms — content_management_system
|
Fork CMS Content Management System v5.8.0 was discovered to contain a cross-site scripting (XSS) vulnerability in the `Displayname` field when using the `Add`, `Edit` or `Register’ functions. This vulnerability allows attackers to execute arbitrary web scripts or HTML. |
2021-10-22 |
not yet calculated |
CVE-2020-23049
MISC |
foxlor — foxlor
|
Multiple cross-site scripting (XSS) vulnerabilities in the Customer Add module of Foxlor v0.10.16 allows attackers to execute arbitrary web scripts or HTML via a crafted payload entered into the name, firstname, or username input fields. |
2021-10-22 |
not yet calculated |
CVE-2020-28957
MISC |
freebsd — freebsd
|
FreeBSD’s crontab calculates the MD5 sum of the previous and new cronjob to determine if any changes have been made before copying the new version in. In particular, it uses the MD5File() function, which takes a pathname as an argument, and is called with euid 0. A race condition in this process may lead to an arbitrary MD5 comparison regardless of the read permissions. |
2021-10-19 |
not yet calculated |
CVE-2011-1075
MISC
MISC |
freerdp — freerdp
|
FreeRDP is a free implementation of the Remote Desktop Protocol (RDP), released under the Apache license. In affected versions a malicious server might trigger out of bound writes in a connected client. Connections using GDI or SurfaceCommands to send graphics updates to the client might send `0` width/height or out of bound rectangles to trigger out of bound writes. With `0` width or heigth the memory allocation will be `0` but the missing bounds checks allow writing to the pointer at this (not allocated) region. This issue has been patched in FreeRDP 2.4.1. |
2021-10-21 |
not yet calculated |
CVE-2021-41160
CONFIRM |
freerdp — freerdp
|
FreeRDP is a free implementation of the Remote Desktop Protocol (RDP), released under the Apache license. All FreeRDP clients prior to version 2.4.1 using gateway connections (`/gt:rpc`) fail to validate input data. A malicious gateway might allow client memory to be written out of bounds. This issue has been resolved in version 2.4.1. If you are unable to update then use `/gt:http` rather than /gt:rdp connections if possible or use a direct connection without a gateway. |
2021-10-21 |
not yet calculated |
CVE-2021-41159
CONFIRM |
gjson — gjson
|
GJSON before 1.9.3 allows a ReDoS (regular expression denial of service) attack. |
2021-10-22 |
not yet calculated |
CVE-2021-42836
MISC
MISC
MISC
MISC
MISC |
| gnu — mailman |
GNU Mailman before 2.1.35 may allow remote Privilege Escalation. A certain csrf_token value is derived from the admin password, and may be useful in conducting a brute-force attack against that password. |
2021-10-21 |
not yet calculated |
CVE-2021-42096
CONFIRM
CONFIRM
MLIST
DEBIAN |
gnu — mailman
|
GNU Mailman before 2.1.35 may allow remote Privilege Escalation. A csrf_token value is not specific to a single user account. An attacker can obtain a value within the context of an unprivileged user account, and then use that value in a CSRF attack against an admin (e.g., for account takeover). |
2021-10-21 |
not yet calculated |
CVE-2021-42097
CONFIRM
CONFIRM
MLIST
DEBIAN |
| google — android |
In RW_SetActivatedTagType of rw_main.cc, there is possible memory corruption due to a race condition. This could lead to remote code execution with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-9 Android-10 Android-11 Android-8.1Android ID: A-192472262 |
2021-10-22 |
not yet calculated |
CVE-2021-0870
MISC |
| google — android |
In runDumpHeap of ActivityManagerShellCommand.java, there is a possible deletion of system files due to a confused deputy. This could lead to local escalation of privilege with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-9 Android-10 Android-11 Android-8.1Android ID: A-183262161 |
2021-10-22 |
not yet calculated |
CVE-2021-0708
MISC |
| google — android |
In sanitizeSbn of NotificationManagerService.java, there is a possible way to keep service running in foreground and keep granted permissions due to Bypass of Background Service Restrictions. This could lead to local escalation of privilege with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-11 Android-10Android ID: A-185388103 |
2021-10-22 |
not yet calculated |
CVE-2021-0705
MISC |
| google — android |
In SecondStageMain of init.cpp, there is a possible use after free due to incorrect shared_ptr usage. This could lead to local escalation of privilege if the attacker has physical access to the device, with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-11Android ID: A-184569329 |
2021-10-22 |
not yet calculated |
CVE-2021-0703
MISC |
| google — android |
In VectorDrawable::VectorDrawable of VectorDrawable.java, there is a possible way to introduce a memory corruption due to sharing of not thread-safe objects. This could lead to local escalation of privilege with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-8.1 Android-9 Android-10 Android-11Android ID: A-185178568 |
2021-10-22 |
not yet calculated |
CVE-2021-0652
MISC |
google — android
|
In multiple methods of AAudioService, there is a possible use-after-free due to a race condition. This could lead to local escalation of privilege with User execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-10 Android-11Android ID: A-153358911 |
2021-10-22 |
not yet calculated |
CVE-2021-0483
MISC |
google — android
|
In getAllSubInfoList of SubscriptionController.java, there is a possible way to retrieve a long term identifier without the correct permissions due to a missing permission check. This could lead to local information disclosure with User execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-11 Android-10Android ID: A-183612370 |
2021-10-22 |
not yet calculated |
CVE-2021-0643
MISC |
google — android
|
In loadLabel of PackageItemInfo.java, there is a possible way to DoS a device by having a long label in an app due to incorrect input validation. This could lead to local denial of service with no additional execution privileges needed. User interaction is needed for exploitation.Product: AndroidVersions: Android-11 Android-9 Android-10Android ID: A-67013844 |
2021-10-22 |
not yet calculated |
CVE-2021-0651
MISC |
google — android
|
In startListening of PluginManagerImpl.java, there is a possible way to disable arbitrary app components due to a missing permission check. This could lead to local denial of service with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-9 Android-10 Android-11 Android-8.1Android ID: A-193444889 |
2021-10-22 |
not yet calculated |
CVE-2021-0706
MISC |
google — android
|
In RevertActiveSessions of apexd.cpp, there is a possible way to share the wrong file due to an unintentional MediaStore downgrade. This could lead to local information disclosure with no additional execution privileges needed. User interaction is needed for exploitation.Product: AndroidVersions: Android-11Android ID: A-193932765 |
2021-10-22 |
not yet calculated |
CVE-2021-0702
MISC |
hcl — traveler_companion
|
“HCL Traveler Companion is vulnerable to an iOS weak cryptographic process vulnerability via the included MobileIron AppConnect SDK” |
2021-10-21 |
not yet calculated |
CVE-2020-14263
MISC |
hcl_software — connections
|
“HCL Connections Security Update for Reflected Cross-Site Scripting (XSS) Vulnerability” |
2021-10-21 |
not yet calculated |
CVE-2021-27746
MISC |
| hyland — alfresco |
An issue was discovered in Hyland org.alfresco:alfresco-content-services through 6.2.2.18 and org.alfresco:alfresco-transform-services through 1.3. A crafted HTML file, once uploaded, could trigger an unexpected request by the transformation engine. The response to the request is not available to the attacker, i.e., this is blind SSRF. |
2021-10-21 |
not yet calculated |
CVE-2021-41792
MISC
MISC |
hyland — alfresco
|
An issue was discovered in Hyland org.alfresco:share through 7.0.0.2 and org.alfresco:community-share through 7.0. An evasion of the XSS filter for HTML input validation in the Alfresco Share User Interface leads to stored XSS that could be exploited by an attacker (given that he has privileges on the content collaboration features). |
2021-10-21 |
not yet calculated |
CVE-2021-41791
MISC
MISC |
hyland — alfresco
|
An issue was discovered in Hyland org.alfresco:alfresco-content-services through 7.0.1.2. Script Action execution allows executing scripts uploaded outside of the Data Dictionary. This could allow a logged-in attacker to execute arbitrary code inside a sandboxed environment. |
2021-10-21 |
not yet calculated |
CVE-2021-41790
MISC
MISC |
ibm — business_automation_workflow
|
IBM Business Automation Workflow 18.0, 19.0, 20.0, and 21.0 is vulnerable to cross-site scripting. This vulnerability allows users to embed arbitrary JavaScript code in the Web UI thus altering the intended functionality potentially leading to credentials disclosure within a trusted session. IBM X-Force ID: 204833. |
2021-10-22 |
not yet calculated |
CVE-2021-29835
CONFIRM
XF |
ibm — flash_system_900
|
IBM Flash System 900 could allow an authenticated attacker to obtain sensitive information and cause a denial of service due to a restricted shell escape vulnerability. IBM X-Force ID: 206229. |
2021-10-21 |
not yet calculated |
CVE-2021-29873
CONFIRM
CONFIRM
XF |
ibm — qradar_advisor
|
IBM QRadar Advisor 2.5 through 2.6.1 is vulnerable to cross-site scripting. This vulnerability allows users to embed arbitrary JavaScript code in the Web UI thus altering the intended functionality potentially leading to credentials disclosure within a trusted session. IBM X-Force ID: 209566. |
2021-10-20 |
not yet calculated |
CVE-2021-38896
CONFIRM
XF |
ibm — standards_processing_engine
|
IBM Standards Processing Engine (IBM Transformation Extender Advanced 9.0 and 10.0) does not set the secure attribute on authorization tokens or session cookies. Attackers may be able to get the cookie values by sending a http:// link to a user or by planting this link in a site the user goes to. The cookie will be sent to the insecure link and the attacker can then obtain the cookie value by snooping the traffic. IBM X-Force ID: 207090. |
2021-10-21 |
not yet calculated |
CVE-2021-29883
CONFIRM
XF |
inhand_networks — ir615_routers
|
InHand Networks IR615 Router’s Versions 2.3.0.r4724 and 2.3.0.r4870 are vulnerable to an attacker using a traceroute tool to inject commands into the device. This may allow the attacker to remotely run commands on behalf of the device. |
2021-10-19 |
not yet calculated |
CVE-2021-38478
MISC |
internet_download_manager — internet_download_manager
|
Internet Download Manager 6.37.11.1 was discovered to contain a stack buffer overflow in the Search function. This vulnerability allows attackers to escalate local process privileges via unspecified vectors. |
2021-10-22 |
not yet calculated |
CVE-2020-28964
MISC |
internet_download_manager — internet_download_manager
|
Internet Download Manager 6.37.11.1 was discovered to contain a stack buffer overflow in the Export/Import function. This vulnerability allows attackers to escalate local process privileges via a crafted ef2 file. |
2021-10-22 |
not yet calculated |
CVE-2020-23060
MISC |
juniper — 128_technology_session_smart_router
|
The usage of an internal HTTP header created an authentication bypass vulnerability (CWE-287), allowing an attacker to view internal files, change settings, manipulate services and execute arbitrary code. This issue affects all Juniper Networks 128 Technology Session Smart Router versions prior to 4.5.11, and all versions of 5.0 up to and including 5.0.1. |
2021-10-19 |
not yet calculated |
CVE-2021-31349
CONFIRM |
| juniper — ctpview_server |
The Juniper Networks CTPView server is not enforcing HTTP Strict Transport Security (HSTS). HSTS is an optional response header which allows servers to indicate that content from the requested domain will only be served over HTTPS. The lack of HSTS may leave the system vulnerable to downgrade attacks, SSL-stripping man-in-the-middle attacks, and weakens cookie-hijacking protections. This issue affects Juniper Networks CTPView: 7.3 versions prior to 7.3R7; 9.1 versions prior to 9.1R3. |
2021-10-19 |
not yet calculated |
CVE-2021-0296
CONFIRM |
juniper — jboss_application_server
|
A configuration weakness in the JBoss Application Server (AppSvr) component of Juniper Networks SRC Series allows a remote attacker to send a specially crafted query to cause the web server to delete files which may allow the attacker to disrupt the integrity and availability of the system. |
2021-10-19 |
not yet calculated |
CVE-2021-31381
CONFIRM |
juniper — jboss_application_server
|
A configuration weakness in the JBoss Application Server (AppSvr) component of Juniper Networks SRC Series allows a remote attacker to send a specially crafted query to cause the web server to disclose sensitive information in the HTTP response which allows the attacker to obtain sensitive information. |
2021-10-19 |
not yet calculated |
CVE-2021-31380
CONFIRM |
| juniper — junos_os |
An Uncontrolled Resource Consumption vulnerability in Juniper Networks Junos OS on EX2300, EX3400 and EX4300 Series platforms allows an adjacent attacker sending a stream of layer 2 frames will trigger an Aggregated Ethernet (AE) interface to go down and thereby causing a Denial of Service (DoS). By continuously sending a stream of specific layer 2 frames an attacker will sustain the Denial of Service (DoS) condition. This issue affects: Juniper Networks Junos OS EX4300 Series All versions prior to 15.1R7-S7; 16.1 versions prior to 16.1R7-S8; 17.1 versions prior to 17.1R2-S12; 17.2 versions prior to 17.2R3-S4; 17.3 versions prior to 17.3R3-S8; 17.4 versions prior to 17.4R2-S10, 17.4R3-S2; 18.1 versions prior to 18.1R3-S10; 18.2 versions prior to 18.2R2-S7, 18.2R3-S3; 18.3 versions prior to 18.3R2-S4, 18.3R3-S2; 18.4 versions prior to 18.4R1-S7, 18.4R2-S4, 18.4R3-S1; 19.1 versions prior to 19.1R1-S5, 19.1R2-S1, 19.1R3; 19.2 versions prior to 19.2R1-S5, 19.2R2; 19.3 versions prior to 19.3R2-S2, 19.3R3; 19.4 versions prior to 19.4R1-S2, 19.4R2. Juniper Networks Junos OS EX3400 and EX4300-MP Series All versions prior to 18.1R3-S12; 18.2 versions prior to 18.2R3-S7; 18.3 versions prior to 18.3R3-S4; 18.4 versions prior to 18.4R2-S9, 18.4R3-S7; 19.1 versions prior to 19.1R2-S3, 19.1R3-S4; 19.2 versions prior to 19.2R3-S1; 19.3 versions prior to 19.3R3-S1; 19.4 versions prior to 19.4R3-S1; 20.1 versions prior to 20.1R3; 20.2 versions prior to 20.2R3; 20.3 versions prior to 20.3R2. Juniper Networks Junos OS EX2300 Series All versions prior to 18.3R3-S5; 18.4 versions prior to 18.4R2-S9, 18.4R3-S9; 19.1 versions prior to 19.1R2-S3, 19.1R3-S6; 19.2 versions prior to 19.2R1-S7, 19.2R3-S3; 19.3 versions prior to 19.3R2-S7, 19.3R3-S3; 19.4 versions prior to 19.4R3-S5; 20.1 versions prior to 20.1R2-S2, 20.1R3-S1; 20.2 versions prior to 20.2R3-S2; 20.3 versions prior to 20.3R3-S1; 20.4 versions prior to 20.4R2-S1, 20.4R3; 21.1 versions prior to 21.1R2. |
2021-10-19 |
not yet calculated |
CVE-2021-31365
CONFIRM |
| juniper — junos_os |
An Improper Input Validation vulnerability in J-Web of Juniper Networks Junos OS allows a locally authenticated J-Web attacker to escalate their privileges to root over the target device. This issue affects: Juniper Networks Junos OS All versions prior to 18.3R3-S5; 18.4 versions prior to 18.4R3-S9; 19.1 versions prior to 19.1R3-S6; 19.2 versions prior to 19.2R3-S3; 19.3 versions prior to 19.3R3-S3; 19.4 versions prior to 19.4R3-S5; 20.1 versions prior to 20.1R3-S1; 20.2 versions prior to 20.2R3-S2; 20.3 versions prior to 20.3R3-S1; 20.4 versions prior to 20.4R3; 21.1 versions prior to 21.1R2, 21.1R3; 21.2 versions prior to 21.2R1-S1, 21.2R2; |
2021-10-19 |
not yet calculated |
CVE-2021-31372
CONFIRM |
| juniper — junos_os |
Juniper Networks Junos OS uses the 128.0.0.0/2 subnet for internal communications between the RE and PFEs. It was discovered that packets utilizing these IP addresses may egress an QFX5110 switch, leaking configuration information such as heartbeats, kernel versions, etc. out to the Internet, leading to an information exposure vulnerability. This issue affects: Juniper Networks Junos OS on QFX5110 Series: All versions prior to 17.3R3-S12; 18.1 versions prior to 18.1R3-S13; 18.3 versions prior to 18.3R3-S5; 19.1 versions prior to 19.1R3-S6; 19.2 versions prior to 19.2R1-S7, 19.2R3-S3; 19.3 versions prior to 19.3R2-S6, 19.3R3-S3; 19.4 versions prior to 19.4R1-S4, 19.4R3-S5; 20.1 versions prior to 20.1R2-S2, 20.1R3-S1; 20.2 versions prior to 20.2R3-S2; 20.3 versions prior to 20.3R3-S1; 20.4 versions prior to 20.4R2-S1, 20.4R3; 21.1 versions prior to 21.1R1-S1, 21.1R2; |
2021-10-19 |
not yet calculated |
CVE-2021-31371
CONFIRM |
| juniper — junos_os |
An improper privilege management vulnerability in the Juniper Networks Junos OS and Junos OS Evolved command-line interpreter (CLI) allows a low-privileged user to overwrite local files as root, possibly leading to a system integrity issue or Denial of Service (DoS). Depending on the files overwritten, exploitation of this vulnerability could lead to a sustained Denial of Service (DoS) condition, requiring manual user intervention to recover. This issue affects: Juniper Networks Junos OS: All versions, including the following supported releases: 15.1 versions prior to 15.1R7-S10; 17.4 versions prior to 17.4R3-S5; 18.3 versions prior to 18.3R3-S5; 18.4 versions prior to 18.4R3-S9; 19.1 versions prior to 19.1R3-S6; 19.2 versions prior to 19.2R1-S7, 19.2R3-S3; 19.3 versions prior to 19.3R2-S6, 19.3R3-S3; 19.4 versions prior to 19.4R3-S6; 20.1 versions prior to 20.1R2-S2, 20.1R3-S1; 20.2 versions prior to 20.2R3-S2; 20.3 versions prior to 20.3R3; 20.4 versions prior to 20.4R2-S1, 20.4R3; 21.1 versions prior to 21.1R1-S1, 21.1R2. Juniper Networks Junos OS Evolved: All versions prior to 20.4R2-S3-EVO; All versions of 21.1-EVO. |
2021-10-19 |
not yet calculated |
CVE-2021-31360
CONFIRM |
| juniper — junos_os |
A persistent Cross-Site Scripting (XSS) vulnerability in Juniper Networks Junos OS on SRX Series, J-Web interface may allow a remote authenticated user to inject persistent and malicious scripts. An attacker can exploit this vulnerability to steal sensitive data and credentials from a web administration session, or hijack another user’s active session to perform administrative actions. This issue affects: Juniper Networks Junos OS on SRX Series: 18.2 versions prior to 18.2R3-S8; 18.3 versions prior to 18.3R3-S5; 18.4 versions prior to 18.4R3-S8; 19.1 versions prior to 19.1R3-S5; 19.2 versions prior to 19.2R1-S7, 19.2R3-S3; 19.3 versions prior to 19.3R2-S6, 19.3R3-S3; 19.4 versions prior to 19.4R1-S4, 19.4R2-S4, 19.4R3-S3; 20.1 versions prior to 20.1R2-S2, 20.1R3; 20.2 versions prior to 20.2R3-S1; 20.3 versions prior to 20.3R2-S1, 20.3R3. |
2021-10-19 |
not yet calculated |
CVE-2021-31373
CONFIRM |
| juniper — junos_os |
An Incorrect Permission Assignment for Critical Resource vulnerability of a certain file in the filesystem of Junos OS allows a local authenticated attacker to cause routing process daemon (RPD) to crash and restart, causing a Denial of Service (DoS). Repeated actions by the attacker will create a sustained Denial of Service (DoS) condition. This issue affects: Juniper Networks Junos OS: 15.1 versions prior to 15.1R7-S9; 17.3 versions prior to 17.3R3-S12; 17.4 versions prior to 17.4R2-S13, 17.4R3-S5; 18.1 versions prior to 18.1R3-S13; 18.2 versions prior to 18.2R3-S8; 18.3 versions prior to 18.3R3-S5; 18.4 versions prior to 18.4R2-S8, 18.4R3-S7; 19.1 versions prior to 19.1R2-S3, 19.1R3-S5; 19.2 versions prior to 19.2R3-S2; 19.3 versions prior to 19.3R2-S6, 19.3R3-S2; 19.4 versions prior to 19.4R1-S4, 19.4R2-S4, 19.4R3-S2; 20.1 versions prior to 20.1R2-S2, 20.1R3; 20.2 versions prior to 20.2R2-S3, 20.2R3; 20.3 versions prior to 20.3R3; 20.4 versions prior to 20.4R1-S1, 20.4R2. |
2021-10-19 |
not yet calculated |
CVE-2021-31377
CONFIRM |
| juniper — junos_os |
An Incorrect Behavior Order vulnerability in the MAP-E automatic tunneling mechanism of Juniper Networks Junos OS allows an attacker to send certain malformed IPv4 or IPv6 packets to cause a Denial of Service (DoS) to the PFE on the device which is disabled as a result of the processing of these packets. Continued receipt and processing of these malformed IPv4 or IPv6 packets will create a sustained Denial of Service (DoS) condition. This issue only affects MPC 7/8/9/10/11 cards, when MAP-E IP reassembly is enabled on these cards. An indicator of compromise is the output: FPC [“FPC ID” # e.g. “0”] PFE #{PFE ID # e.g. “1”] : Fabric Disabled Example: FPC 0 PFE #1 : Fabric Disabled when using the command: show chassis fabric fpcs An example of a healthy result of the command use would be: user@device-re1> show chassis fabric fpcs Fabric management FPC state: FPC 0 PFE #0 Plane 0: Plane enabled Plane 1: Plane enabled Plane 2: Plane enabled Plane 3: Plane enabled Plane 4: Plane enabled Plane 5: Plane enabled Plane 6: Plane enabled Plane 7: Plane enabled This issue affects: Juniper Networks Junos OS on MX Series with MPC 7/8/9/10/11 cards, when MAP-E IP reassembly is enabled on these cards. 17.2 version 17.2R1 and later versions; 17.3 versions prior to 17.3R3-S9; 17.4 versions prior to 17.4R2-S12, 17.4R3-S3; 18.1 versions prior to 18.1R3-S11; 18.2 versions prior to 18.2R2-S6, 18.2R3-S3; 18.3 versions prior to 18.3R2-S4, 18.3R3-S1; 18.4 versions prior to 18.4R1-S8, 18.4R2-S5, 18.4R3; 19.1 versions prior to 19.1R1-S6, 19.1R2-S2, 19.1R3; 19.2 versions prior to 19.2R1-S5, 19.2R2; 19.3 versions prior to 19.3R2-S5, 19.3R3. This issue does not affect Juniper Networks Junos OS versions prior to 17.2R1. |
2021-10-19 |
not yet calculated |
CVE-2021-31379
CONFIRM
MISC |
| juniper — junos_os |
An Information Exposure vulnerability in Juniper Networks SRC Series devices configured for NETCONF over SSH permits the negotiation of weak ciphers, which could allow a remote attacker to obtain sensitive information. A remote attacker with read and write access to network data could exploit this vulnerability to display plaintext bits from a block of ciphertext and obtain sensitive information. This issue affects all Juniper Networks SRC Series versions prior to 4.13.0-R6. |
2021-10-19 |
not yet calculated |
CVE-2021-31352
CONFIRM |
| juniper — junos_os |
A Race Condition in the ‘show chassis pic’ command in Juniper Networks Junos OS Evolved may allow an attacker to crash the port interface concentrator daemon (picd) process on the FPC, if the command is executed coincident with other system events outside the attacker’s control, leading to a Denial of Service (DoS) condition. Continued execution of the CLI command, under precise conditions, could create a sustained Denial of Service (DoS) condition. This issue affects all Juniper Networks Junos OS Evolved versions prior to 20.1R2-EVO on PTX10003 and PTX10008 platforms. Junos OS is not affected by this vulnerability. |
2021-10-19 |
not yet calculated |
CVE-2021-0298
CONFIRM |
| juniper — junos_os |
An Improper Handling of Exceptional Conditions vulnerability in Juniper Networks Junos OS and Junos OS Evolved allows an attacker to inject a specific BGP update, causing the routing protocol daemon (RPD) to crash and restart, leading to a Denial of Service (DoS). Continued receipt and processing of the BGP update will create a sustained Denial of Service (DoS) condition. This issue affects very specific versions of Juniper Networks Junos OS: 19.3R3-S2; 19.4R3-S3; 20.2 versions 20.2R2-S3 and later, prior to 20.2R3-S2; 20.3 versions 20.3R2 and later, prior to 20.3R3; 20.4 versions 20.4R2 and later, prior to 20.4R3; 21.1 versions prior to 21.1R2. Juniper Networks Junos OS 20.1 is not affected by this issue. This issue also affects Juniper Networks Junos OS Evolved: All versions prior to 20.4R2-S3-EVO, 20.4R3-EVO; 21.1-EVO versions prior to 21.1R2-EVO; 21.2-EVO versions prior to 21.2R2-EVO. |
2021-10-19 |
not yet calculated |
CVE-2021-31353
CONFIRM |
| juniper — junos_os |
On Juniper Networks Junos OS and Junos OS Evolved devices processing a specially crafted BGP UPDATE or KEEPALIVE message can lead to a routing process daemon (RPD) crash and restart, causing a Denial of Service (DoS). Continued receipt and processing of this message will create a sustained Denial of Service (DoS) condition. This issue affects both IBGP and EBGP deployments over IPv4 or IPv6. This issue affects: Juniper Networks Junos OS: 17.3 versions prior to 17.3R3-S11; 17.4 versions prior to 17.4R2-S13, 17.4R3-S4; 18.1 versions prior to 18.1R3-S12; 18.2 versions prior to 18.2R2-S8, 18.2R3-S7; 18.3 versions prior to 18.3R3-S4; 18.4 versions prior to 18.4R1-S8, 18.4R2-S7, 18.4R3-S7; 19.1 versions prior to 19.1R1-S6, 19.1R2-S2, 19.1R3-S4; 19.2 versions prior to 19.2R1-S6, 19.2R3-S1; 19.3 versions prior to 19.3R2-S5, 19.3R3-S1; 19.4 versions prior to 19.4R1-S4, 19.4R1-S4, 19.4R2-S3, 19.4R3-S1; 20.1 versions prior to 20.1R2; 20.2 versions prior to 20.2R2; 20.3 versions prior to 20.3R1-S1, 20.3R2. Juniper Networks Junos OS Evolved: 20.3 versions prior to 20.3R2-EVO. |
2021-10-19 |
not yet calculated |
CVE-2021-31374
CONFIRM |
| juniper — junos_os |
An Improper Input Validation vulnerability in routing process daemon (RPD) of Juniper Networks Junos OS devices configured with BGP origin validation using Resource Public Key Infrastructure (RPKI), allows an attacker to send a specific BGP update which may cause RPKI policy-checks to be bypassed. This, in turn, may allow a spoofed advertisement to be accepted or propagated. This issue affects: Juniper Networks Junos OS 12.3 versions prior to 12.3R12-S18; 15.1 versions prior to 15.1R7-S9; 17.2 versions prior to 17.2R3-S3; 17.3 versions prior to 17.3R3-S7; 17.4 versions prior to 17.4R2-S9, 17.4R3; 18.1 versions prior to 18.1R3-S13; 18.2 versions prior to 18.2R3-S3; 18.3 versions prior to 18.3R3-S1; 18.4 versions prior to 18.4R3; 19.1 versions prior to 19.1R2; 19.2 versions prior to 19.2R2; 19.3 versions prior to 19.3R2. |
2021-10-19 |
not yet calculated |
CVE-2021-31375
CONFIRM |
| juniper — junos_os |
An Improper Input Validation vulnerability in Packet Forwarding Engine manager (FXPC) process of Juniper Networks Junos OS allows an attacker to cause a Denial of Service (DoS) by sending specific DHCPv6 packets to the device and crashing the FXPC service. Continued receipt and processing of this specific packet will create a sustained Denial of Service (DoS) condition. This issue affects only the following platforms in ACX Series: ACX500, ACX1000, ACX1100, ACX2100, ACX2200, ACX4000, ACX5048, ACX5096 devices. Other ACX platforms are not affected from this issue. This issue affects Juniper Networks Junos OS on ACX500, ACX1000, ACX1100, ACX2100, ACX2200, ACX4000, ACX5048, ACX5096: 18.4 version 18.4R3-S7 and later versions prior to 18.4R3-S8. This issue does not affect: Juniper Networks Junos OS 18.4 versions prior to 18.4R3-S7 on ACX500, ACX1000, ACX1100, ACX2100, ACX2200, ACX4000, ACX5048, ACX5096. |
2021-10-19 |
not yet calculated |
CVE-2021-31376
CONFIRM |
| juniper — junos_os |
A Protection Mechanism Failure vulnerability in RPD (routing protocol daemon) of Juniper Networks Junos OS and Junos OS Evolved allows an adjacent unauthenticated attacker to cause established IS-IS adjacencies to go down by sending a spoofed hello PDU leading to a Denial of Service (DoS) condition. Continued receipted of these spoofed PDUs will create a sustained Denial of Service (DoS) condition. This issue affects: Juniper Networks Junos OS All versions prior to 18.2R3-S8; 18.3 versions prior to 18.3R3-S5; 18.4 versions prior to 18.4R3-S9; 19.1 versions prior to 19.1R3-S7; 19.2 versions prior to 19.2R1-S7, 19.2R3-S3; 19.3 versions prior to 19.3R2-S6, 19.3R3-S2; 19.4 versions prior to 19.4R3-S3; 20.1 versions prior to 20.1R3; 20.2 versions prior to 20.2R3; 20.3 versions prior to 20.3R3; 20.4 versions prior to 20.4R2. Juniper Networks Junos OS Evolved All versions prior to 20.4R2-EVO; 21.1 versions prior to 21.1R2-EVO. |
2021-10-19 |
not yet calculated |
CVE-2021-31362
CONFIRM |
| juniper — junos_os |
A Protection Mechanism Failure vulnerability in the J-Web HTTP service of Juniper Networks Junos OS allows a remote unauthenticated attacker to perform Person-in-the-Middle (PitM) attacks against the device. This issue affects: Juniper Networks Junos OS 12.3 versions prior to 12.3R12-S20; 15.1 versions prior to 15.1R7-S11; 18.3 versions prior to 18.3R3-S6; 18.4 versions prior to 18.4R3-S10; 19.1 versions prior to 19.1R3-S7; 19.2 versions prior to 19.2R3-S4; 19.3 versions prior to 19.3R3-S4; 19.4 versions prior to 19.4R3-S6; 20.1 versions prior to 20.1R3-S2; 20.2 versions prior to 20.2R3-S3; 20.3 versions prior to 20.3R3-S1; 20.4 versions prior to 20.4R3; 21.1 versions prior to 21.1R3; 21.2 versions prior to 21.2R2. |
2021-10-19 |
not yet calculated |
CVE-2021-31386
CONFIRM |
| juniper — junos_os |
An Improper Limitation of a Pathname to a Restricted Directory (‘Path Traversal’) vulnerability in J-Web of Juniper Networks Junos OS allows any low-privileged authenticated attacker to elevate their privileges to root. This issue affects: Juniper Networks Junos OS 12.3 versions prior to 12.3R12-S19; 15.1 versions prior to 15.1R7-S10; 18.3 versions prior to 18.3R3-S5; 18.4 versions prior to 18.4R3-S9; 19.1 versions prior to 19.1R3-S6; 19.2 versions prior to 19.2R1-S7, 19.2R3-S3; 19.3 versions prior to 19.3R3-S3; 19.4 versions prior to 19.4R3-S5; 20.1 versions prior to 20.1R2-S2, 20.1R3-S1; 20.2 versions prior to 20.2R3-S2; 20.3 versions prior to 20.3R3; 20.4 versions prior to 20.4R2-S1, 20.4R3; 21.1 versions prior to 21.1R1-S1, 21.1R2. |
2021-10-19 |
not yet calculated |
CVE-2021-31385
CONFIRM |
juniper — junos_os
|
A command injection vulnerability in sftp command processing on Juniper Networks Junos OS Evolved allows an attacker with authenticated CLI access to be able to bypass configured access protections to execute arbitrary shell commands within the context of the current user. The vulnerability allows an attacker to bypass command authorization restrictions assigned to their specific user account and execute commands that are available to the privilege level for which the user is assigned. For example, a user that is in the super-user login class, but restricted to executing specific CLI commands could exploit the vulnerability to execute any other command available to an unrestricted admin user. This vulnerability does not increase the privilege level of the user, but rather bypasses any CLI command restrictions by allowing full access to the shell. This issue affects Juniper Networks Junos OS Evolved: All versions prior to 20.4R2-S2-EVO; 21.1 versions prior to 21.1R2-EVO; 21.2 versions prior to 21.2R1-S1-EVO, 21.2R2-EVO. |
2021-10-19 |
not yet calculated |
CVE-2021-31358
CONFIRM |
juniper — junos_os
|
An Improper Check for Unusual or Exceptional Conditions in packet processing on the MS-MPC/MS-MIC utilized by Juniper Networks Junos OS allows a malicious attacker to send a specific packet, triggering the MS-MPC/MS-MIC to reset, causing a Denial of Service (DoS). Continued receipt and processing of this packet will create a sustained Denial of Service (DoS) condition. This issue only affects specific versions of Juniper Networks Junos OS on MX Series: 17.3R3-S11; 17.4R2-S13; 17.4R3 prior to 17.4R3-S5; 18.1R3-S12; 18.2R2-S8, 18.2R3-S7, 18.2R3-S8; 18.3R3-S4; 18.4R3-S7; 19.1R3-S4, 19.1R3-S5; 19.2R1-S6; 19.3R3-S2; 19.4R2-S4, 19.4R2-S5; 19.4R3-S2; 20.1R2-S1; 20.2R2-S2, 20.2R2-S3, 20.2R3; 20.3R2, 20.3R2-S1; 20.4R1, 20.4R1-S1, 20.4R2; 21.1R1; This issue does not affect any version of Juniper Networks Junos OS prior to 15.1X49-D240; |
2021-10-19 |
not yet calculated |
CVE-2021-31351
CONFIRM |
juniper — junos_os
|
A local privilege escalation vulnerability in Juniper Networks Junos OS and Junos OS Evolved allows a local, low-privileged user to cause the Juniper DHCP daemon (jdhcpd) process to crash, resulting in a Denial of Service (DoS), or execute arbitrary commands as root. Continued processing of malicious input will repeatedly crash the system and sustain the Denial of Service (DoS) condition. This issue affects: Juniper Networks Junos OS: All versions, including the following supported releases: 15.1 versions prior to 15.1R7-S10; 17.4 versions prior to 17.4R3-S5; 18.3 versions prior to 18.3R3-S5; 18.4 versions prior to 18.4R3-S9; 19.1 versions prior to 19.1R3-S6; 19.2 versions prior to 19.2R1-S7, 19.2R3-S3; 19.3 versions prior to 19.3R2-S6, 19.3R3-S3; 19.4 versions prior to 19.4R3-S6; 20.1 versions prior to 20.1R2-S2, 20.1R3-S1; 20.2 versions prior to 20.2R3-S2; 20.3 versions prior to 20.3R3; 20.4 versions prior to 20.4R2-S1, 20.4R3; 21.1 versions prior to 21.1R1-S1, 21.1R2. Juniper Networks Junos OS Evolved: All versions prior to 20.4R2-S3-EVO; All versions of 21.1-EVO. |
2021-10-19 |
not yet calculated |
CVE-2021-31359
CONFIRM |
juniper — junos_os
|
An Improper Privilege Management vulnerability in the gRPC framework, used by the Juniper Extension Toolkit (JET) API on Juniper Networks Junos OS and Junos OS Evolved, allows a network-based, low-privileged authenticated attacker to perform operations as root, leading to complete compromise of the targeted system. The issue is caused by the JET service daemon (jsd) process authenticating the user, then passing configuration operations directly to the management daemon (mgd) process, which runs as root. This issue affects Juniper Networks Junos OS: 18.4 versions prior to 18.4R1-S8, 18.4R2-S8, 18.4R3-S8; 19.1 versions prior to 19.1R2-S3, 19.1R3-S5; 19.2 versions prior to 19.2R1-S7, 19.2R3-S2; 19.3 versions prior to 19.3R2-S6, 19.3R3-S2; 19.4 versions prior to 19.4R1-S4, 19.4R2-S4, 19.4R3-S3; 20.1 versions prior to 20.1R2-S2, 20.1R3; 20.2 versions prior to 20.2R2-S3, 20.2R3; 20.3 versions prior to 20.3R2-S1, 20.3R3; 20.4 versions prior to 20.4R2. This issue does not affect Juniper Networks Junos OS versions prior to 18.4R1. Juniper Networks Junos OS Evolved: All versions prior to 20.4R2-EVO; 21.1-EVO versions prior to 21.1R2-EVO. |
2021-10-19 |
not yet calculated |
CVE-2021-31350
CONFIRM |
juniper — junos_os
|
A command injection vulnerability in tcpdump command processing on Juniper Networks Junos OS Evolved allows an attacker with authenticated CLI access to be able to bypass configured access protections to execute arbitrary shell commands within the context of the current user. The vulnerability allows an attacker to bypass command authorization restrictions assigned to their specific user account and execute commands that are available to the privilege level for which the user is assigned. For example, a user that is in the super-user login class, but restricted to executing specific CLI commands could exploit the vulnerability to execute any other command available to an unrestricted admin user. This vulnerability does not increase the privilege level of the user, but rather bypasses any CLI command restrictions by allowing full access to the shell. This issue affects Juniper Networks Junos OS Evolved: All versions prior to 20.3R2-S1-EVO; 20.4 versions prior to 20.4R2-S2-EVO; 21.1 versions prior to 21.1R2-EVO; 21.2 versions prior to 21.2R1-S1-EVO, 21.2R2-EVO. |
2021-10-19 |
not yet calculated |
CVE-2021-31357
CONFIRM |
juniper — junos_os
|
A command injection vulnerability in command processing on Juniper Networks Junos OS Evolved allows an attacker with authenticated CLI access to be able to bypass configured access protections to execute arbitrary shell commands within the context of the current user. The vulnerability allows an attacker to bypass command authorization restrictions assigned to their specific user account and execute commands that are available to the privilege level for which the user is assigned. For example, a user that is in the super-user login class, but restricted to executing specific CLI commands could exploit the vulnerability to execute any other command available to an unrestricted admin user. This vulnerability does not increase the privilege level of the user, but rather bypasses any CLI command restrictions by allowing full access to the shell. This issue affects Juniper Networks Junos OS Evolved: All versions prior to 20.4R3-S1-EVO; All versions of 21.1-EVO and 21.2-EVO. |
2021-10-19 |
not yet calculated |
CVE-2021-31356
CONFIRM |
juniper — junos_os
|
An Improper Check for Unusual or Exceptional Conditions vulnerability combined with Improper Handling of Exceptional Conditions in Juniper Networks Junos OS on QFX Series and PTX Series allows an unauthenticated network based attacker to cause increased FPC CPU utilization by sending specific IP packets which are being VXLAN encapsulated leading to a partial Denial of Service (DoS). Continued receipted of these specific traffic will create a sustained Denial of Service (DoS) condition. This issue affects: Juniper Networks Junos OS on QFX Series: All versions prior to 17.3R3-S11; 17.4 versions prior to 17.4R2-S13, 17.4R3-S4; 18.1 versions prior to 18.1R3-S12; 18.2 versions prior to 18.2R2-S8, 18.2R3-S7; 18.3 versions prior to 18.3R3-S4; 18.4 versions prior to 18.4R1-S8, 18.4R2-S7, 18.4R3-S7; 19.1 versions prior to 19.1R1-S6, 19.1R2-S2, 19.1R3-S4; 19.2 versions prior to 19.2R1-S6, 19.2R3-S2; 19.3 versions prior to 19.3R3-S1; 19.4 versions prior to 19.4R2-S3, 19.4R3-S1; 20.1 versions prior to 20.1R2, 20.1R3; 20.2 versions prior to 20.2R2, 20.2R3; 20.3 versions prior to 20.3R1-S1, 20.3R2. Juniper Networks Junos OS on PTX Series: All versions prior to 18.4R3-S9; 19.1 versions prior to 19.1R3-S6; 19.2 versions prior to 19.2R1-S7, 19.2R3-S3; 19.3 versions prior to 19.3R2-S6, 19.3R3-S3; 19.4 versions prior to 19.4R1-S4, 19.4R3-S5; 20.1 versions prior to 20.1R2-S2, 20.1R3; 20.2 versions prior to 20.2R3-S1; 20.3 versions prior to 20.3R2-S1, 20.3R3; 20.4 versions prior to 20.4R2-S1, 20.4R3; 21.1 versions prior to 21.1R1-S1, 21.1R2. |
2021-10-19 |
not yet calculated |
CVE-2021-31361
CONFIRM |
juniper — junos_os
|
Due to a Missing Authorization weakness and Insufficient Granularity of Access Control in a specific device configuration, a vulnerability exists in Juniper Networks Junos OS on SRX Series whereby an attacker who attempts to access J-Web administrative interfaces can successfully do so from any device interface regardless of the web-management configuration and filter rules which may otherwise protect access to J-Web. This issue affects: Juniper Networks Junos OS SRX Series 20.4 version 20.4R1 and later versions prior to 20.4R2-S1, 20.4R3; 21.1 versions prior to 21.1R1-S1, 21.1R2. This issue does not affect Juniper Networks Junos OS versions prior to 20.4R1. |
2021-10-19 |
not yet calculated |
CVE-2021-31384
MISC |
juniper — junos_os
|
In an MPLS P2MP environment a Loop with Unreachable Exit Condition vulnerability in the routing protocol daemon (RPD) of Juniper Networks Junos OS and Junos OS Evolved allows an unauthenticated adjacent attacker to cause high load on RPD which in turn may lead to routing protocol flaps. If a system with sensor-based-stats enabled receives a specific LDP FEC this can lead to the above condition. Continued receipted of such an LDP FEC will create a sustained Denial of Service (DoS) condition. This issue affects: Juniper Networks Junos OS 19.2 version 19.2R2 and later versions prior to 19.2R3-S3; 19.3 versions prior to 19.3R2-S6, 19.3R3-S2; 19.4 versions prior to 19.4R1-S4, 19.4R2-S4, 19.4R3-S2; 20.1 versions prior to 20.1R2-S1, 20.1R3; 20.2 versions prior to 20.2R2-S1, 20.2R3; 20.3 versions prior to 20.3R1-S2, 20.3R2. This issue does not affect Juniper Networks Junos OS versions prior to 19.2R2. Juniper Networks Junos OS Evolved All versions prior to 20.1R2-S3-EVO; 20.3 versions prior to 20.3R1-S2-EVO. |
2021-10-19 |
not yet calculated |
CVE-2021-31363
CONFIRM |
juniper — junos_os
|
An Improper Check for Unusual or Exceptional Conditions vulnerability combined with a Race Condition in the flow daemon (flowd) of Juniper Networks Junos OS on SRX300 Series, SRX500 Series, SRX1500, and SRX5000 Series with SPC2 allows an unauthenticated network based attacker sending specific traffic to cause a crash of the flowd/srxpfe process, responsible for traffic forwarding in SRX, which will cause a Denial of Service (DoS). Continued receipt and processing of this specific traffic will create a sustained Denial of Service (DoS) condition. This issue can only occur when specific packets are trying to create the same session and logging for session-close is configured as a policy action. Affected platforms are: SRX300 Series, SRX500 Series, SRX1500, and SRX5000 Series with SPC2. Not affected platforms are: SRX4000 Series, SRX5000 Series with SPC3, and vSRX Series. This issue affects Juniper Networks Junos OS SRX300 Series, SRX500 Series, SRX1500, and SRX5000 Series with SPC2: All versions prior to 17.4R3-S5; 18.3 versions prior to 18.3R3-S5; 18.4 versions prior to 18.4R3-S9; 19.1 versions prior to 19.1R3-S6; 19.2 versions prior to 19.2R1-S7, 19.2R3-S2; 19.3 versions prior to 19.3R2-S6, 19.3R3-S2; 19.4 versions prior to 19.4R1-S4, 19.4R3-S3; 20.1 versions prior to 20.1R2-S2, 20.1R3; 20.2 versions prior to 20.2R3; 20.3 versions prior to 20.3R2-S1, 20.3R3; 20.4 versions prior to 20.4R2. |
2021-10-19 |
not yet calculated |
CVE-2021-31364
CONFIRM |
juniper — junos_os
|
An Unchecked Return Value vulnerability in the authd (authentication daemon) of Juniper Networks Junos OS on MX Series configured for subscriber management / BBE allows an adjacent attacker to cause a crash by sending a specific username. This impacts authentication, authorization, and accounting (AAA) services on the MX devices and leads to a Denial of Service (DoS) condition. Continued receipted of these PPP login request will create a sustained Denial of Service (DoS) condition. This issue affects: Juniper Networks Junos OS 15.1 versions prior to 15.1R7-S9; 17.3 versions prior to 17.3R3-S12; 17.4 versions prior to 17.4R3-S5; 18.1 versions prior to 18.1R3-S13; 18.2 versions prior to 18.2R3-S8; 18.3 versions prior to 18.3R3-S5; 18.4 versions prior to 18.4R3-S9; 19.1 versions prior to 19.1R3-S6; 19.2 versions prior to 19.2R1-S7, 19.2R3-S3; 19.3 versions prior to 19.3R2-S6, 19.3R3-S3; 19.4 versions prior to 19.4R3-S3; 20.1 versions prior to 20.1R3; 20.2 versions prior to 20.2R3-S1; 20.3 versions prior to 20.3R3; 20.4 versions prior to 20.4R3; 21.1 versions prior to 21.1R2. |
2021-10-19 |
not yet calculated |
CVE-2021-31366
CONFIRM |
juniper — junos_os
|
A Missing Release of Memory after Effective Lifetime vulnerability in the Packet Forwarding Engine (PFE) of Juniper Networks Junos OS on PTX Series allows an adjacent attacker to cause a Denial of Service (DoS) by sending genuine BGP flowspec packets which cause an FPC heap memory leak. Once having run out of memory the FPC will crash and restart along with a core dump. Continued receipted of these packets will create a sustained Denial of Service (DoS) condition. This issue affects: Juniper Networks Junos OS All versions prior to 18.4R3-S9; 19.1 versions prior to 19.1R3-S7; 19.2 versions prior to 19.2R1-S7, 19.2R3-S3; 19.3 versions prior to 19.3R2-S6, 19.3R3-S3; 19.4 versions prior to 19.4R1-S4, 19.4R3-S6; 20.1 versions prior to 20.1R2-S2, 20.1R3; 20.2 versions prior to 20.2R3-S1; 20.3 versions prior to 20.3R3; 20.4 versions prior to 20.4R3; 21.1 versions prior to 21.1R2. Juniper Networks Junos Evolved is not affected. |
2021-10-19 |
not yet calculated |
CVE-2021-31367
CONFIRM |
juniper — junos_os
|
An Uncontrolled Resource Consumption vulnerability in the kernel of Juniper Networks JUNOS OS allows an unauthenticated network based attacker to cause 100% CPU load and the device to become unresponsive by sending a flood of traffic to the out-of-band management ethernet port. Continued receipted of a flood will create a sustained Denial of Service (DoS) condition. Once the flood subsides the system will recover by itself. An indication that the system is affected by this issue would be that kernel and netisr process are shown to be using a lot of CPU cycles like in the following example output: user@host> show system processes extensive … PID USERNAME PRI NICE SIZE RES STATE C TIME WCPU COMMAND 16 root -72 – 0K 304K WAIT 1 839:40 88.96% intr{swi1: netisr 0} 0 root 97 – 0K 160K RUN 1 732:43 87.99% kernel{bcm560xgmac0 que} This issue affects Juniper Networks JUNOS OS on EX2300 Series, EX3400 Series, and ACX710: All versions prior to 18.1R3-S13; 18.2 versions prior to 18.2R3-S8; 18.3 versions prior to 18.3R3-S5; 18.4 versions prior to 18.4R2-S8, 18.4R3-S9; 19.1 versions prior to 19.1R3-S5; 19.2 versions prior to 19.2R1-S7, 19.2R3-S3; 19.3 versions prior to 19.3R2-S6, 19.3R3-S2; 19.4 versions prior to 19.4R1-S4, 19.4R3-S3; 20.1 versions prior to 20.1R2-S2, 20.1R3; 20.2 versions prior to 20.2R3; 20.3 versions prior to 20.3R2-S1, 20.3R3; 20.4 versions prior to 20.4R2. |
2021-10-19 |
not yet calculated |
CVE-2021-31368
CONFIRM |
juniper — junos_os
|
On MX Series platforms with MS-MPC/MS-MIC, an Allocation of Resources Without Limits or Throttling vulnerability in Juniper Networks Junos OS allows an unauthenticated network attacker to cause a partial Denial of Service (DoS) with a high rate of specific traffic. If a Class of Service (CoS) rule is attached to the service-set and a high rate of specific traffic is processed by this service-set, for some of the other traffic which has services applied and is being processed by this MS-MPC/MS-MIC drops will be observed. Continued receipted of this high rate of specific traffic will create a sustained Denial of Service (DoS) condition. This issue affects: Juniper Networks Junos OS on MX Series with MS-MPC/MS-MIC: All versions prior to 17.4R3-S5; 18.3 versions prior to 18.3R3-S5; 18.4 versions prior to 18.4R3-S9; 19.1 versions prior to 19.1R3-S6; 19.2 versions prior to 19.2R1-S7, 19.2R3-S3; 19.3 versions prior to 19.3R2-S7, 19.3R3-S3; 19.4 versions prior to 19.4R3-S5; 20.1 versions prior to 20.1R2-S2, 20.1R3-S1; 20.2 versions prior to 20.2R3-S2; 20.3 versions prior to 20.3R3; 20.4 versions prior to 20.4R2-S1, 20.4R3; 21.1 versions prior to 21.1R1-S1, 21.1R2. |
2021-10-19 |
not yet calculated |
CVE-2021-31369
CONFIRM |
juniper — junos_os
|
An Incomplete List of Disallowed Inputs vulnerability in Packet Forwarding Engine (PFE) of Juniper Networks Junos OS on QFX5000 Series and EX4600 Series allows an adjacent unauthenticated attacker which sends a high rate of specific multicast traffic to cause control traffic received from the network to be dropped. This will impact control protocols (including but not limited to routing-protocols) and lead to a Denial of Service (DoS). Continued receipt of this specific multicast traffic will create a sustained Denial of Service (DoS) condition. This issue affects Juniper Networks Junos OS on QFX5000 and EX4600 Series: All versions prior to 17.3R3-S12; 17.4 versions prior to 17.4R3-S5; 18.3 versions prior to 18.3R3-S5; 18.4 versions prior to 18.4R3-S9; 19.1 versions prior to 19.1R3-S6; 19.2 versions prior to 19.2R1-S7, 19.2R3-S3; 19.3 versions prior to 19.3R2-S6, 19.3R3-S3; 19.4 versions prior to 19.4R1-S4, 19.4R3-S3; 20.1 versions prior to 20.1R2-S2, 20.1R3-S1; 20.2 versions prior to 20.2R3-S2; 20.3 versions prior to 20.3R3; 20.4 versions prior to 20.4R2-S2, 20.4R3; 21.1 versions prior to 21.1R1-S1, 21.1R2. |
2021-10-19 |
not yet calculated |
CVE-2021-31370
CONFIRM |
juniper — junos_os
|
A persistent cross-site scripting (XSS) vulnerability in the captive portal graphical user interface of Juniper Networks Junos OS may allow a remote authenticated user to inject web script or HTML and steal sensitive data and credentials from a web administration session, possibly tricking a follow-on administrative user to perform administrative actions on the device. This issue affects Juniper Networks Junos OS: All versions, including the following supported releases: 12.3X48 versions prior to 12.3X48-D105; 15.1X49 versions prior to 15.1X49-D220; 18.3 versions prior to 18.3R3-S5; 18.4 versions prior to 18.4R3-S9; 19.1 versions prior to 19.1R3-S7; 19.2 versions prior to 19.2R3-S3; 19.3 versions prior to 19.3R3-S4; 19.4 versions prior to 19.4R3-S6; 20.1 versions prior to 20.1R3; 20.2 versions prior to 20.2R1-S1, 20.2R2; 20.3 versions prior to 20.3R2; 20.4 versions prior to 20.4R2; 21.1 versions prior to 21.1R2. |
2021-10-19 |
not yet calculated |
CVE-2021-31355
CONFIRM |
juniper — junos_os
|
A vulnerability in the processing of TCP MD5 authentication in Juniper Networks Junos OS Evolved may allow a BGP or LDP session configured with MD5 authentication to succeed, even if the peer does not have TCP MD5 authentication enabled. This could lead to untrusted or unauthorized sessions being established, resulting in an impact on confidentiality or stability of the network. This issue affects Juniper Networks Junos OS Evolved: All versions prior to 20.3R2-S1-EVO; 20.4 versions prior to 20.4R2-EVO; 21.1 versions prior to 21.1R2-EVO. Juniper Networks Junos OS is not affected by this issue. |
2021-10-19 |
not yet calculated |
CVE-2021-0297
CONFIRM |
juniper — junos_os
|
An Improper Handling of Exceptional Conditions vulnerability in the processing of a transit or directly received malformed IPv6 packet in Juniper Networks Junos OS results in a kernel crash, causing the device to restart, leading to a Denial of Service (DoS). Continued receipt and processing of this packet will create a sustained Denial of Service (DoS) condition. This issue only affects systems with IPv6 configured. Devices with only IPv4 configured are not vulnerable to this issue. This issue affects Juniper Networks Junos OS: 19.4 versions prior to 19.4R3; 20.1 versions prior to 20.1R2; 20.2 versions prior to 20.2R1-S1, 20.2R2. This issue does not affect Juniper Networks Junos OS versions prior to 19.4R1. |
2021-10-19 |
not yet calculated |
CVE-2021-0299
CONFIRM |
juniper — junos_os
|
In broadband environments, including but not limited to Enhanced Subscriber Management, (CHAP, PPP, DHCP, etc.), on Juniper Networks Junos OS devices where RADIUS servers are configured for managing subscriber access and a subscriber is logged in and then requests to logout, the subscriber may be forced into a “Terminating” state by an attacker who is able to send spoofed messages appearing to originate from trusted RADIUS server(s) destined to the device in response to the subscriber’s request. These spoofed messages cause the Junos OS General Authentication Service (authd) daemon to force the broadband subscriber into this “Terminating” state which the subscriber will not recover from thereby causing a Denial of Service (DoS) to the endpoint device. Once in the “Terminating” state, the endpoint subscriber will no longer be able to access the network. Restarting the authd daemon on the Junos OS device will temporarily clear the subscribers out of the “Terminating” state. As long as the attacker continues to send these spoofed packets and subscribers request to be logged out, the subscribers will be returned to the “Terminating” state thereby creating a persistent Denial of Service to the subscriber. An indicator of compromise may be seen by displaying the output of “show subscribers summary”. The presence of subscribers in the “Terminating” state may indicate the issue is occurring. This issue affects: Juniper Networks Junos OS 17.3 versions prior to 17.3R3-S12; 17.4 versions prior to 17.4R3-S5; 18.1 versions prior to 18.1R3-S13; 18.2 versions prior to 18.2R3-S8; 18.3 versions prior to 18.3R3-S5; 18.4 versions prior to 18.4R2-S8, 18.4R3-S9; 19.1 versions prior to 19.1R3-S6; 19.2 versions prior to 19.2R1-S7, 19.2R3-S3; 19.3 versions prior to 19.3R2-S6, 19.3R3-S3; 19.4 versions prior to 19.4R1-S4, 19.4R1-S4, 19.4R3-S3; 20.1 versions prior to 20.1R3; 20.2 versions prior to 20.2R3-S1; 20.3 versions prior to 20.3R3; 20.4 versions prior to 20.4R3; 21.1 versions prior to 21.1R2. This issue does not affect: Juniper Networks Junos OS 12.3 version 12.3R1 and later versions; 15.1 version 15.1R1 and later versions. |
2021-10-19 |
not yet calculated |
CVE-2021-31378
MISC
CONFIRM |
juniper — junos_os
|
On PTX1000 System, PTX10002-60C System, after upgrading to an affected release, a Race Condition vulnerability between the chassis daemon (chassisd) and firewall process (dfwd) of Juniper Networks Junos OS, may update the device’s interfaces with incorrect firewall filters. This issue only occurs when upgrading the device to an affected version of Junos OS. Interfaces intended to have protections may have no protections assigned to them. Interfaces with one type of protection pattern may have alternate protections assigned to them. Interfaces intended to have no protections may have protections assigned to them. These firewall rule misassignments may allow genuine traffic intended to be stopped at the interface to propagate further, potentially causing disruptions in services by propagating unwanted traffic. An attacker may be able to take advantage of these misassignments. This issue affects Juniper Networks Junos OS on PTX1000 System: 17.2 versions 17.2R1 and later versions prior to 17.3 versions prior to 17.3R3-S12; 17.4 versions prior to 17.4R3-S5; 18.1 versions prior to 18.1R3-S13; 18.2 versions prior to 18.2R3-S8; 18.3 versions prior to 18.3R3-S5; 18.4 versions prior to 18.4R1-S8, 18.4R2-S8, 18.4R3-S8; 19.1 versions prior to 19.1R3-S5; 19.2 versions prior to 19.2R3-S2; 19.3 versions prior to 19.3R2-S6, 19.3R3-S3; 19.4 versions prior to 19.4R2-S4, 19.4R3-S3; 20.1 versions prior to 20.1R3; 20.2 versions prior to 20.2R2-S3, 20.2R3; 20.3 versions prior to 20.3R2-S1, 20.3R3; 20.4 versions prior to 20.4R1-S1, 20.4R2. This issue does not affect Juniper Networks Junos OS prior to version 17.2R1 on PTX1000 System. This issue affects Juniper Networks Junos OS on PTX10002-60C System: 18.2 versions 18.2R1 and later versions prior to 18.4 versions prior to 18.4R3-S9; 19.1 versions later than 19.1R1 prior to 19.4 versions prior to 19.4R2-S5, 19.4R3-S5; 20.1 versions prior to 20.1R3-S1; 20.2 versions prior to 20.2R3-S2; 20.3 versions prior to 20.3R3-S1; 20.4 versions 20.4R1 and later versions prior to 21.1 versions prior to 21.1R2; 21.2 versions 21.2R1 and later versions prior to 21.3 versions prior to 21.3R2. This issue does not affect Juniper Networks Junos OS prior to version 18.2R1 on PTX10002-60C System. This issue impacts all filter families (inet, inet6, etc.) and all loopback filters. It does not rely upon the location where a filter is set, impacting both logical and physical interfaces. |
2021-10-19 |
not yet calculated |
CVE-2021-31382
CONFIRM
MISC |
juniper — junos_os
|
In Point to MultiPoint (P2MP) scenarios within established sessions between network or adjacent neighbors the improper use of a source to destination copy write operation combined with a Stack-based Buffer Overflow on certain specific packets processed by the routing protocol daemon (RPD) of Juniper Networks Junos OS and Junos OS Evolved sent by a remote unauthenticated network attacker causes the RPD to crash causing a Denial of Service (DoS). Continued receipt and processing of these packets will create a sustained Denial of Service (DoS) condition. This issue affects: Juniper Networks Junos OS 19.2 versions prior to 19.2R3-S2; 19.3 versions prior to 19.3R2-S6, 19.3R3-S2; 19.4 versions prior to 19.4R1-S4, 19.4R2-S4, 19.4R3-S3; 20.1 versions prior to 20.1R2-S2, 20.1R3; 20.2 versions prior to 20.2R2-S3, 20.2R3; 20.3 versions prior to 20.3R2. This issue does not affect Juniper Networks Junos OS versions prior to 19.2R1. Juniper Networks Junos OS Evolved 20.1 versions prior to 20.1R3-EVO; 20.2 versions prior to 20.2R3-EVO; 20.3 versions prior to 20.3R2-EVO. |
2021-10-19 |
not yet calculated |
CVE-2021-31383
CONFIRM |
juniper — junos_os
|
An Out Of Bounds (OOB) access vulnerability in the handling of responses by a Juniper Agile License (JAL) Client in Juniper Networks Junos OS and Junos OS Evolved, configured in Network Mode (to use Juniper Agile License Manager) may allow an attacker to cause a partial Denial of Service (DoS), or lead to remote code execution (RCE). The vulnerability exists in the packet parsing logic on the client that processes the response from the server using a custom protocol. An attacker with control of a JAL License Manager, or with access to the local broadcast domain, may be able to spoof a new JAL License Manager and/or craft a response to the Junos OS License Client, leading to exploitation of this vulnerability. This issue only affects Junos systems configured in Network Mode. Systems that are configured in Standalone Mode (the default mode of operation for all systems) are not vulnerable to this issue. This issue affects: Juniper Networks Junos OS: 19.2 versions prior to 19.2R3-S3; 19.3 versions prior to 19.3R3-S3; 20.1 versions prior to 20.1R2-S2, 20.1R3-S1; 20.2 versions prior to 20.2R3-S2; 20.3 versions prior to 20.3R3; 20.4 versions prior to 20.4R3; 21.1 versions prior to 21.1R2. Juniper Networks Junos OS Evolved: version 20.1R1-EVO and later versions, prior to 21.2R2-EVO. This issue does not affect Juniper Networks Junos OS versions prior to 19.2R1. |
2021-10-19 |
not yet calculated |
CVE-2021-31354
CONFIRM |
kiwi — cattools_installation_wizard
|
As a result of an unquoted service path vulnerability present in the Kiwi CatTools Installation Wizard, a local attacker could gain escalated privileges by inserting an executable into the path of the affected service or uninstall entry. |
2021-10-22 |
not yet calculated |
CVE-2021-35230
MISC |
libmobi — libmobi
|
libmobi is vulnerable to Use of Out-of-range Pointer Offset |
2021-10-19 |
not yet calculated |
CVE-2021-3889
CONFIRM
MISC |
libmobi — libmobi
|
libmobi is vulnerable to Use of Out-of-range Pointer Offset |
2021-10-19 |
not yet calculated |
CVE-2021-3888
MISC
CONFIRM |
linux — linux_kernel
|
dp_link_settings_write in drivers/gpu/drm/amd/display/amdgpu_dm/amdgpu_dm_debugfs.c in the Linux kernel through 5.14.14 allows a heap-based buffer overflow by an attacker who can write a string to the AMD GPU display drivers debug filesystem. There are no checks on size within parse_write_buffer_into_params when it uses the size of copy_from_user to copy a userspace buffer into a 40-byte heap buffer. |
2021-10-21 |
not yet calculated |
CVE-2021-42327
MISC
MISC |
linux — linux_kernel
|
The firewire subsystem in the Linux kernel through 5.14.13 has a buffer overflow related to drivers/media/firewire/firedtv-avc.c and drivers/media/firewire/firedtv-ci.c, because avc_ca_pmt mishandles bounds checking. |
2021-10-20 |
not yet calculated |
CVE-2021-42739
MISC
MISC |
macrob7 — macs_framework_content_management_system
|
Macrob7 Macs Framework Content Management System – 1.14f was discovered to contain a SQL injection vulnerability via the ‘roleId’ parameter of the `editRole` and `deletUser` modules. |
2021-10-22 |
not yet calculated |
CVE-2020-23045
MISC |
macrob7 — macs_framework_content_management_system
|
Macrob7 Macs Framework Content Management System – 1.14f contains a cross-site scripting (XSS) vulnerability in the account reset function, which allows attackers to execute arbitrary web scripts or HTML via a crafted payload in the e-mail input field. |
2021-10-22 |
not yet calculated |
CVE-2020-36498
MISC |
macrob7 — macs_framework_content_management_system
|
Macrob7 Macs Framework Content Management System – 1.14f was discovered to contain a cross-site scripting (XSS) vulnerability in the search input field of the search module. |
2021-10-22 |
not yet calculated |
CVE-2020-23047
MISC |
mcafee — epolicy_orchestrator
|
Stored Cross-Site Scripting vulnerability in McAfee ePolicy Orchestrator (ePO) prior to 5.10 Update 11 allows ePO administrators to inject arbitrary web script or HTML via multiple parameters where the administrator’s entries were not correctly sanitized. |
2021-10-22 |
not yet calculated |
CVE-2021-31834
CONFIRM |
mcafee — epolicy_orchestrator
|
Cross-Site Scripting vulnerability in McAfee ePolicy Orchestrator (ePO) prior to 5.10 Update 11 allows ePO administrators to inject arbitrary web script or HTML via a specific parameter where the administrator’s entries were not correctly sanitized. |
2021-10-22 |
not yet calculated |
CVE-2021-31835
CONFIRM |
media_navi_inc — smacom
|
MEDIA NAVI Inc SMACom v1.2 was discovered to contain an insecure session validation vulnerability in the session handling of the `password` authentication parameter of the wifi photo transfer module. This vulnerability allows attackers with network access privileges or on public wifi networks to read the authentication credentials and follow-up requests containing the user password via a man in the middle attack. |
2021-10-22 |
not yet calculated |
CVE-2020-23036
MISC |
microsoft — surface_pro_3
|
Microsoft Surface Pro 3 Security Feature Bypass Vulnerability |
2021-10-20 |
not yet calculated |
CVE-2021-42299
MISC |
modern-async — modern-async
|
modern-async is an open source JavaScript tooling library for asynchronous operations using async/await and promises. In affected versions a bug affecting two of the functions in this library: forEachSeries and forEachLimit. They should limit the concurrency of some actions but, in practice, they don’t. Any code calling these functions will be written thinking they would limit the concurrency but they won’t. This could lead to potential security issues in other projects. The problem has been patched in 1.0.4. There is no workaround. |
2021-10-20 |
not yet calculated |
CVE-2021-41167
MISC
MISC
CONFIRM |
nong_ge — file_explorer
|
An issue in the authentication mechanism in Nong Ge File Explorer v1.4 unauthenticated allows to access sensitive data. |
2021-10-22 |
not yet calculated |
CVE-2020-23058
MISC |
nsk — user_agent_string_switcher_service
|
A cross-site scripting (XSS) vulnerability in NSK User Agent String Switcher Service v0.3.5 allows attackers to execute arbitrary web scripts or HTML via a crafted payload in the user agent input field. |
2021-10-22 |
not yet calculated |
CVE-2020-23054
MISC |
openpower — openpower
|
An issue was discovered in OpenPOWER 2.6 firmware. unpack_timestamp() calls le32_to_cpu() for endian conversion of a uint16_t “year” value, resulting in a type mismatch that can truncate a higher integer value to a smaller one, and bypass a timestamp check. The fix is to use the right endian conversion function. |
2021-10-22 |
not yet calculated |
CVE-2021-36357
MISC |
oracle — communications
|
Vulnerability in the Oracle Communications Interactive Session Recorder product of Oracle Communications (component: Provision API). The supported version that is affected is 6.4. Easily exploitable vulnerability allows unauthenticated attacker with network access via HTTP to compromise Oracle Communications Interactive Session Recorder. While the vulnerability is in Oracle Communications Interactive Session Recorder, attacks may significantly impact additional products. Successful attacks of this vulnerability can result in unauthorized update, insert or delete access to some of Oracle Communications Interactive Session Recorder accessible data as well as unauthorized read access to a subset of Oracle Communications Interactive Session Recorder accessible data and unauthorized ability to cause a partial denial of service (partial DOS) of Oracle Communications Interactive Session Recorder. CVSS 3.1 Base Score 8.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:L/I:L/A:L). |
2021-10-20 |
not yet calculated |
CVE-2021-2461
MISC |
oracle — communications
|
Vulnerability in the Oracle Communications Session Border Controller product of Oracle Communications (component: Routing). Supported versions that are affected are 8.4 and 9.0. Easily exploitable vulnerability allows high privileged attacker with network access via HTTP to compromise Oracle Communications Session Border Controller. While the vulnerability is in Oracle Communications Session Border Controller, attacks may significantly impact additional products. Successful attacks of this vulnerability can result in unauthorized access to critical data or complete access to all Oracle Communications Session Border Controller accessible data. CVSS 3.1 Base Score 6.8 (Confidentiality impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:C/C:H/I:N/A:N). |
2021-10-20 |
not yet calculated |
CVE-2021-2414
MISC |
oracle — communications
|
Vulnerability in the Oracle Communications Session Border Controller product of Oracle Communications (component: Routing). Supported versions that are affected are 8.4 and 9.0. Easily exploitable vulnerability allows high privileged attacker with network access via HTTP to compromise Oracle Communications Session Border Controller. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of Oracle Communications Session Border Controller. CVSS 3.1 Base Score 4.9 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-2416
MISC |
oracle — database_server
|
Vulnerability in the RDBMS Security component of Oracle Database Server. Supported versions that are affected are 12.2.0.1, 19c and 21c. Easily exploitable vulnerability allows high privileged attacker having DBA privilege with network access via Oracle Net to compromise RDBMS Security. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of RDBMS Security as well as unauthorized update, insert or delete access to some of RDBMS Security accessible data. CVSS 3.1 Base Score 5.5 (Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:L/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-35551
MISC |
oracle — database_server
|
Vulnerability in the Oracle LogMiner component of Oracle Database Server. Supported versions that are affected are 12.1.0.2, 12.2.0.1 and 19c. Easily exploitable vulnerability allows high privileged attacker having DBA privilege with network access via Oracle Net to compromise Oracle LogMiner. Successful attacks of this vulnerability can result in unauthorized creation, deletion or modification access to critical data or all Oracle LogMiner accessible data as well as unauthorized read access to a subset of Oracle LogMiner accessible data and unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of Oracle LogMiner. CVSS 3.1 Base Score 6.7 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:L/I:H/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-2332
MISC |
oracle — database_server
|
Vulnerability in the Core RDBMS component of Oracle Database Server. Supported versions that are affected are 12.1.0.2, 12.2.0.1, 19c and 21c. Easily exploitable vulnerability allows low privileged attacker having Create Table privilege with network access via Oracle Net to compromise Core RDBMS. Successful attacks of this vulnerability can result in unauthorized ability to cause a partial denial of service (partial DOS) of Core RDBMS. CVSS 3.1 Base Score 4.3 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:N/I:N/A:L). |
2021-10-20 |
not yet calculated |
CVE-2021-35558
MISC |
oracle — database_server
|
Vulnerability in the Oracle Database Enterprise Edition Unified Audit component of Oracle Database Server. Supported versions that are affected are 12.1.0.2, 12.2.0.1 and 19c. Easily exploitable vulnerability allows high privileged attacker having Local Logon privilege with network access via Oracle Net to compromise Oracle Database Enterprise Edition Unified Audit. Successful attacks of this vulnerability can result in unauthorized update, insert or delete access to some of Oracle Database Enterprise Edition Unified Audit accessible data. CVSS 3.1 Base Score 2.7 (Integrity impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:L/A:N). |
2021-10-20 |
not yet calculated |
CVE-2021-35576
MISC |
oracle — database_server
|
Vulnerability in the Zero Downtime DB Migration to Cloud component of Oracle Database Server. The supported version that is affected is 21c. Easily exploitable vulnerability allows high privileged attacker having Local Logon privilege with logon to the infrastructure where Zero Downtime DB Migration to Cloud executes to compromise Zero Downtime DB Migration to Cloud. While the vulnerability is in Zero Downtime DB Migration to Cloud, attacks may significantly impact additional products. Successful attacks of this vulnerability can result in takeover of Zero Downtime DB Migration to Cloud. CVSS 3.1 Base Score 8.2 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:L/AC:L/PR:H/UI:N/S:C/C:H/I:H/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-35599
MISC |
oracle — database_server
|
Vulnerability in the Java VM component of Oracle Database Server. Supported versions that are affected are 12.1.0.2, 12.2.0.1, 19c and 21c. Difficult to exploit vulnerability allows low privileged attacker having Create Procedure privilege with network access via Oracle Net to compromise Java VM. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of Java VM. CVSS 3.1 Base Score 7.1 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:H/PR:L/UI:R/S:U/C:H/I:H/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-35619
MISC |
oracle — database_server
|
Vulnerability in the Core RDBMS component of Oracle Database Server. Supported versions that are affected are 12.1.0.2, 12.2.0.1, 19c and 21c. Easily exploitable vulnerability allows low privileged attacker having Create Table privilege with network access via Oracle Net to compromise Core RDBMS. Successful attacks of this vulnerability can result in unauthorized ability to cause a partial denial of service (partial DOS) of Core RDBMS. CVSS 3.1 Base Score 4.3 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:N/I:N/A:L). |
2021-10-20 |
not yet calculated |
CVE-2021-35557
MISC |
oracle — e-buiness_suite
|
Vulnerability in the Oracle Applications Framework product of Oracle E-Business Suite (component: Session Management). Supported versions that are affected are 12.1.3 and 12.2.3-12.2.10. Easily exploitable vulnerability allows unauthenticated attacker with network access via HTTP to compromise Oracle Applications Framework. Successful attacks of this vulnerability can result in unauthorized ability to cause a partial denial of service (partial DOS) of Oracle Applications Framework. CVSS 3.1 Base Score 5.3 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:L). |
2021-10-20 |
not yet calculated |
CVE-2021-2477
MISC |
| oracle — e-business_suite |
Vulnerability in the Oracle Universal Work Queue product of Oracle E-Business Suite (component: Work Provider Site Level Administration). Supported versions that are affected are 12.1.1-12.1.3 and 12.2.3-12.2.10. Easily exploitable vulnerability allows low privileged attacker with network access via HTTP to compromise Oracle Universal Work Queue. Successful attacks of this vulnerability can result in unauthorized creation, deletion or modification access to critical data or all Oracle Universal Work Queue accessible data as well as unauthorized access to critical data or complete access to all Oracle Universal Work Queue accessible data. CVSS 3.1 Base Score 8.1 (Confidentiality and Integrity impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:N). |
2021-10-20 |
not yet calculated |
CVE-2021-35562
MISC |
oracle — e-business_suite
|
Vulnerability in the Oracle Applications Manager product of Oracle E-Business Suite (component: Diagnostics). Supported versions that are affected are 12.1.3 and 12.2.3-12.2.10. Easily exploitable vulnerability allows high privileged attacker with network access via HTTP to compromise Oracle Applications Manager. Successful attacks of this vulnerability can result in unauthorized access to critical data or complete access to all Oracle Applications Manager accessible data. CVSS 3.1 Base Score 4.9 (Confidentiality impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:N/A:N). |
2021-10-20 |
not yet calculated |
CVE-2021-35569
MISC |
oracle — e-business_suite
|
Vulnerability in the Oracle Applications Manager product of Oracle E-Business Suite (component: View Reports). Supported versions that are affected are 12.1.3 and 12.2.3-12.2.10. Easily exploitable vulnerability allows low privileged attacker with network access via HTTP to compromise Oracle Applications Manager. Successful attacks require human interaction from a person other than the attacker and while the vulnerability is in Oracle Applications Manager, attacks may significantly impact additional products. Successful attacks of this vulnerability can result in unauthorized update, insert or delete access to some of Oracle Applications Manager accessible data as well as unauthorized read access to a subset of Oracle Applications Manager accessible data and unauthorized ability to cause a partial denial of service (partial DOS) of Oracle Applications Manager. CVSS 3.1 Base Score 6.5 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:L). |
2021-10-20 |
not yet calculated |
CVE-2021-35582
MISC |
oracle — e-business_suite
|
Vulnerability in the Oracle Shipping Execution product of Oracle E-Business Suite (component: Workflow Events). Supported versions that are affected are 12.2.6-12.2.10. Easily exploitable vulnerability allows low privileged attacker with network access via HTTP to compromise Oracle Shipping Execution. Successful attacks of this vulnerability can result in unauthorized creation, deletion or modification access to critical data or all Oracle Shipping Execution accessible data as well as unauthorized access to critical data or complete access to all Oracle Shipping Execution accessible data. CVSS 3.1 Base Score 8.1 (Confidentiality and Integrity impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:N). |
2021-10-20 |
not yet calculated |
CVE-2021-35563
MISC |
oracle — e-business_suite
|
Vulnerability in the Oracle Applications Manager product of Oracle E-Business Suite (component: Diagnostics). Supported versions that are affected are 12.1.3 and 12.2.3-12.2.10. Easily exploitable vulnerability allows low privileged attacker with network access via HTTP to compromise Oracle Applications Manager. Successful attacks of this vulnerability can result in unauthorized creation, deletion or modification access to critical data or all Oracle Applications Manager accessible data as well as unauthorized access to critical data or complete access to all Oracle Applications Manager accessible data. CVSS 3.1 Base Score 8.1 (Confidentiality and Integrity impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:N). |
2021-10-20 |
not yet calculated |
CVE-2021-35566
MISC |
oracle — e-business_suite
|
Vulnerability in the Oracle Mobile Field Service product of Oracle E-Business Suite (component: Admin UI). Supported versions that are affected are 12.1.1-12.1.3 and 12.2.3-12.2.10. Easily exploitable vulnerability allows low privileged attacker with network access via HTTP to compromise Oracle Mobile Field Service. Successful attacks of this vulnerability can result in unauthorized creation, deletion or modification access to critical data or all Oracle Mobile Field Service accessible data as well as unauthorized access to critical data or complete access to all Oracle Mobile Field Service accessible data. CVSS 3.1 Base Score 8.1 (Confidentiality and Integrity impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:N). |
2021-10-20 |
not yet calculated |
CVE-2021-35570
MISC |
oracle — e-business_suite
|
Vulnerability in the Oracle Deal Management product of Oracle E-Business Suite (component: Miscellaneous). Supported versions that are affected are 12.1.1-12.1.3. Easily exploitable vulnerability allows low privileged attacker with network access via HTTP to compromise Oracle Deal Management. Successful attacks of this vulnerability can result in unauthorized creation, deletion or modification access to critical data or all Oracle Deal Management accessible data as well as unauthorized access to critical data or complete access to all Oracle Deal Management accessible data. CVSS 3.1 Base Score 8.1 (Confidentiality and Integrity impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:N). |
2021-10-20 |
not yet calculated |
CVE-2021-35536
MISC |
oracle — e-business_suite
|
Vulnerability in the Oracle Applications Manager product of Oracle E-Business Suite (component: View Reports). Supported versions that are affected are 12.1.3 and 12.2.3-12.2.10. Easily exploitable vulnerability allows unauthenticated attacker with network access via HTTP to compromise Oracle Applications Manager. Successful attacks require human interaction from a person other than the attacker and while the vulnerability is in Oracle Applications Manager, attacks may significantly impact additional products. Successful attacks of this vulnerability can result in unauthorized update, insert or delete access to some of Oracle Applications Manager accessible data. CVSS 3.1 Base Score 4.7 (Integrity impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:N/I:L/A:N). |
2021-10-20 |
not yet calculated |
CVE-2021-35581
MISC |
oracle — e-business_suite
|
Vulnerability in the Oracle Applications Manager product of Oracle E-Business Suite (component: View Reports). Supported versions that are affected are 12.1.3 and 12.2.3-12.2.10. Easily exploitable vulnerability allows unauthenticated attacker with network access via HTTP to compromise Oracle Applications Manager. Successful attacks require human interaction from a person other than the attacker and while the vulnerability is in Oracle Applications Manager, attacks may significantly impact additional products. Successful attacks of this vulnerability can result in unauthorized update, insert or delete access to some of Oracle Applications Manager accessible data as well as unauthorized read access to a subset of Oracle Applications Manager accessible data. CVSS 3.1 Base Score 6.1 (Confidentiality and Integrity impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N). |
2021-10-20 |
not yet calculated |
CVE-2021-35580
MISC |
oracle — e-business_suite
|
Vulnerability in the Oracle Trade Management product of Oracle E-Business Suite (component: Quotes). Supported versions that are affected are 12.1.1-12.1.3. Easily exploitable vulnerability allows low privileged attacker with network access via HTTP to compromise Oracle Trade Management. Successful attacks of this vulnerability can result in unauthorized creation, deletion or modification access to critical data or all Oracle Trade Management accessible data as well as unauthorized access to critical data or complete access to all Oracle Trade Management accessible data. CVSS 3.1 Base Score 8.1 (Confidentiality and Integrity impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:N). |
2021-10-20 |
not yet calculated |
CVE-2021-2485
MISC |
oracle — e-business_suite
|
Vulnerability in the Oracle Payables product of Oracle E-Business Suite (component: Invoice Approvals). Supported versions that are affected are 12.1.1-12.1.3. Easily exploitable vulnerability allows low privileged attacker with network access via HTTP to compromise Oracle Payables. Successful attacks of this vulnerability can result in unauthorized creation, deletion or modification access to critical data or all Oracle Payables accessible data as well as unauthorized access to critical data or complete access to all Oracle Payables accessible data. CVSS 3.1 Base Score 8.1 (Confidentiality and Integrity impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:N). |
2021-10-20 |
not yet calculated |
CVE-2021-2482
MISC |
oracle — e-business_suite
|
Vulnerability in the Oracle Sales Offline product of Oracle E-Business Suite (component: Offline Template). Supported versions that are affected are 12.1.1-12.1.3 and 12.2.3-12.2.10. Easily exploitable vulnerability allows low privileged attacker with network access via HTTP to compromise Oracle Sales Offline. Successful attacks of this vulnerability can result in unauthorized ability to cause a partial denial of service (partial DOS) of Oracle Sales Offline. CVSS 3.1 Base Score 4.3 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:N/I:N/A:L). |
2021-10-20 |
not yet calculated |
CVE-2021-35611
MISC
MISC |
oracle — e-business_suite
|
Vulnerability in the Oracle Web Analytics product of Oracle E-Business Suite (component: Admin). Supported versions that are affected are 12.1.1-12.1.3. Easily exploitable vulnerability allows low privileged attacker with network access via HTTP to compromise Oracle Web Analytics. Successful attacks of this vulnerability can result in unauthorized creation, deletion or modification access to critical data or all Oracle Web Analytics accessible data as well as unauthorized access to critical data or complete access to all Oracle Web Analytics accessible data. CVSS 3.1 Base Score 8.1 (Confidentiality and Integrity impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:N). |
2021-10-20 |
not yet calculated |
CVE-2021-2474
MISC |
oracle — e-business_suite
|
Vulnerability in the Oracle Incentive Compensation product of Oracle E-Business Suite (component: User Interface). Supported versions that are affected are 12.1.1-12.1.3. Easily exploitable vulnerability allows low privileged attacker with network access via HTTP to compromise Oracle Incentive Compensation. Successful attacks of this vulnerability can result in unauthorized creation, deletion or modification access to critical data or all Oracle Incentive Compensation accessible data as well as unauthorized access to critical data or complete access to all Oracle Incentive Compensation accessible data. CVSS 3.1 Base Score 8.1 (Confidentiality and Integrity impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:N). |
2021-10-20 |
not yet calculated |
CVE-2021-35585
MISC |
oracle — e-business_suite
|
Vulnerability in the Oracle Trade Management product of Oracle E-Business Suite (component: Quotes). Supported versions that are affected are 12.1.1-12.1.3 and 12.2.3-12.2.10. Easily exploitable vulnerability allows unauthenticated attacker with network access via HTTP to compromise Oracle Trade Management. Successful attacks of this vulnerability can result in unauthorized read access to a subset of Oracle Trade Management accessible data. CVSS 3.1 Base Score 5.3 (Confidentiality impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:L/I:N/A:N). |
2021-10-20 |
not yet calculated |
CVE-2021-35554
MISC |
oracle — e-business_suite
|
Vulnerability in the Oracle Content Manager product of Oracle E-Business Suite (component: Content Item Manager). Supported versions that are affected are 12.1.1-12.1.3. Easily exploitable vulnerability allows low privileged attacker with network access via HTTP to compromise Oracle Content Manager. Successful attacks of this vulnerability can result in unauthorized creation, deletion or modification access to critical data or all Oracle Content Manager accessible data as well as unauthorized access to critical data or complete access to all Oracle Content Manager accessible data. CVSS 3.1 Base Score 8.1 (Confidentiality and Integrity impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:N). |
2021-10-20 |
not yet calculated |
CVE-2021-2483
MISC |
oracle — e-business_suite
|
Vulnerability in the Oracle Operations Intelligence product of Oracle E-Business Suite (component: BIS Operations Intelligence). Supported versions that are affected are 12.1.1-12.1.3. Easily exploitable vulnerability allows low privileged attacker with network access via HTTP to compromise Oracle Operations Intelligence. Successful attacks of this vulnerability can result in unauthorized creation, deletion or modification access to critical data or all Oracle Operations Intelligence accessible data as well as unauthorized access to critical data or complete access to all Oracle Operations Intelligence accessible data. CVSS 3.1 Base Score 8.1 (Confidentiality and Integrity impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:N). |
2021-10-20 |
not yet calculated |
CVE-2021-2484
MISC |
oracle — enterprise_manager
|
Vulnerability in the Enterprise Manager Base Platform product of Oracle Enterprise Manager (component: Policy Framework). Supported versions that are affected are 13.4.0.0 and 13.5.0.0. Easily exploitable vulnerability allows low privileged attacker with network access via HTTP to compromise Enterprise Manager Base Platform. Successful attacks of this vulnerability can result in takeover of Enterprise Manager Base Platform. CVSS 3.1 Base Score 8.8 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-2137
MISC |
| oracle — essbase |
Vulnerability in the Essbase Administration Services product of Oracle Essbase (component: EAS Console). The supported version that is affected is Prior to 11.1.2.4.046. Easily exploitable vulnerability allows low privileged attacker with network access via HTTP to compromise Essbase Administration Services. While the vulnerability is in Essbase Administration Services, attacks may significantly impact additional products. Successful attacks of this vulnerability can result in unauthorized access to critical data or complete access to all Essbase Administration Services accessible data as well as unauthorized update, insert or delete access to some of Essbase Administration Services accessible data. CVSS 3.1 Base Score 8.5 (Confidentiality and Integrity impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:C/C:H/I:L/A:N). |
2021-10-20 |
not yet calculated |
CVE-2021-35651
MISC |
| oracle — essbase |
Vulnerability in the Essbase Administration Services product of Oracle Essbase (component: EAS Console). The supported version that is affected is Prior to 11.1.2.4.046. Easily exploitable vulnerability allows unauthenticated attacker with network access via HTTP to compromise Essbase Administration Services. While the vulnerability is in Essbase Administration Services, attacks may significantly impact additional products. Successful attacks of this vulnerability can result in takeover of Essbase Administration Services. CVSS 3.1 Base Score 10.0 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-35652
MISC |
| oracle — essbase |
Vulnerability in the Essbase Administration Services product of Oracle Essbase (component: EAS Console). The supported version that is affected is Prior to 11.1.2.4.046. Easily exploitable vulnerability allows low privileged attacker with network access via HTTP to compromise Essbase Administration Services. While the vulnerability is in Essbase Administration Services, attacks may significantly impact additional products. Successful attacks of this vulnerability can result in unauthorized access to critical data or complete access to all Essbase Administration Services accessible data. CVSS 3.1 Base Score 7.7 (Confidentiality impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:C/C:H/I:N/A:N). |
2021-10-20 |
not yet calculated |
CVE-2021-35653
MISC |
oracle — essbase
|
Vulnerability in the Essbase Administration Services product of Oracle Essbase (component: EAS Console). The supported version that is affected is Prior to 11.1.2.4.046. Easily exploitable vulnerability allows unauthenticated attacker with network access via HTTP to compromise Essbase Administration Services. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of Essbase Administration Services. CVSS 3.1 Base Score 7.5 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-35654
MISC |
oracle — essbase
|
Vulnerability in the Essbase Administration Services product of Oracle Essbase (component: EAS Console). The supported version that is affected is Prior to 11.1.2.4.046. Easily exploitable vulnerability allows unauthenticated attacker with network access via HTTP to compromise Essbase Administration Services. Successful attacks of this vulnerability can result in unauthorized read access to a subset of Essbase Administration Services accessible data. CVSS 3.1 Base Score 5.3 (Confidentiality impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:L/I:N/A:N). |
2021-10-20 |
not yet calculated |
CVE-2021-35655
MISC |
| oracle — fusion |
Vulnerability in the Oracle Outside In Technology product of Oracle Fusion Middleware (component: Outside In Filters). The supported version that is affected is 8.5.5. Easily exploitable vulnerability allows unauthenticated attacker with network access via HTTP to compromise Oracle Outside In Technology. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of Oracle Outside In Technology. Note: Outside In Technology is a suite of software development kits (SDKs). The protocol and CVSS Base Score depend on the software that uses Outside In Technology. The CVSS score assumes that the software passes data received over a network directly to Outside In Technology, but if data is not received over a network the CVSS score may be lower. CVSS 3.1 Base Score 7.5 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-35659
MISC |
| oracle — fusion |
Vulnerability in the Oracle Outside In Technology product of Oracle Fusion Middleware (component: Outside In Filters). The supported version that is affected is 8.5.5. Easily exploitable vulnerability allows unauthenticated attacker with network access via HTTP to compromise Oracle Outside In Technology. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of Oracle Outside In Technology. Note: Outside In Technology is a suite of software development kits (SDKs). The protocol and CVSS Base Score depend on the software that uses Outside In Technology. The CVSS score assumes that the software passes data received over a network directly to Outside In Technology, but if data is not received over a network the CVSS score may be lower. CVSS 3.1 Base Score 7.5 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-35656
MISC |
| oracle — fusion |
Vulnerability in the Oracle Outside In Technology product of Oracle Fusion Middleware (component: Outside In Filters). The supported version that is affected is 8.5.5. Easily exploitable vulnerability allows unauthenticated attacker with network access via HTTP to compromise Oracle Outside In Technology. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of Oracle Outside In Technology. Note: Outside In Technology is a suite of software development kits (SDKs). The protocol and CVSS Base Score depend on the software that uses Outside In Technology. The CVSS score assumes that the software passes data received over a network directly to Outside In Technology, but if data is not received over a network the CVSS score may be lower. CVSS 3.1 Base Score 7.5 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-35660
MISC |
| oracle — fusion |
Vulnerability in the Oracle Outside In Technology product of Oracle Fusion Middleware (component: Outside In Filters). The supported version that is affected is 8.5.5. Easily exploitable vulnerability allows unauthenticated attacker with network access via HTTP to compromise Oracle Outside In Technology. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of Oracle Outside In Technology. Note: Outside In Technology is a suite of software development kits (SDKs). The protocol and CVSS Base Score depend on the software that uses Outside In Technology. The CVSS score assumes that the software passes data received over a network directly to Outside In Technology, but if data is not received over a network the CVSS score may be lower. CVSS 3.1 Base Score 7.5 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-35658
MISC |
oracle — fusion
|
Vulnerability in the Oracle Outside In Technology product of Oracle Fusion Middleware (component: Outside In Filters). The supported version that is affected is 8.5.5. Easily exploitable vulnerability allows unauthenticated attacker with network access via HTTP to compromise Oracle Outside In Technology. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of Oracle Outside In Technology. Note: Outside In Technology is a suite of software development kits (SDKs). The protocol and CVSS Base Score depend on the software that uses Outside In Technology. The CVSS score assumes that the software passes data received over a network directly to Outside In Technology, but if data is not received over a network the CVSS score may be lower. CVSS 3.1 Base Score 7.5 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-35574
MISC |
oracle — fusion
|
Vulnerability in the Oracle Outside In Technology product of Oracle Fusion Middleware (component: Outside In Filters). The supported version that is affected is 8.5.5. Easily exploitable vulnerability allows unauthenticated attacker with network access via HTTP to compromise Oracle Outside In Technology. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of Oracle Outside In Technology. Note: Outside In Technology is a suite of software development kits (SDKs). The protocol and CVSS Base Score depend on the software that uses Outside In Technology. The CVSS score assumes that the software passes data received over a network directly to Outside In Technology, but if data is not received over a network the CVSS score may be lower. CVSS 3.1 Base Score 7.5 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-35572
MISC |
oracle — fusion
|
Vulnerability in the Oracle Outside In Technology product of Oracle Fusion Middleware (component: Outside In Filters). The supported version that is affected is 8.5.5. Easily exploitable vulnerability allows unauthenticated attacker with network access via HTTP to compromise Oracle Outside In Technology. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of Oracle Outside In Technology. Note: Outside In Technology is a suite of software development kits (SDKs). The protocol and CVSS Base Score depend on the software that uses Outside In Technology. The CVSS score assumes that the software passes data received over a network directly to Outside In Technology, but if data is not received over a network the CVSS score may be lower. CVSS 3.1 Base Score 7.5 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-35657
MISC |
oracle — fusion
|
Vulnerability in the Oracle Outside In Technology product of Oracle Fusion Middleware (component: Outside In Filters). The supported version that is affected is 8.5.5. Easily exploitable vulnerability allows unauthenticated attacker with network access via HTTP to compromise Oracle Outside In Technology. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of Oracle Outside In Technology. Note: Outside In Technology is a suite of software development kits (SDKs). The protocol and CVSS Base Score depend on the software that uses Outside In Technology. The CVSS score assumes that the software passes data received over a network directly to Outside In Technology, but if data is not received over a network the CVSS score may be lower. CVSS 3.1 Base Score 7.5 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-35573
MISC |
oracle — fusion
|
Vulnerability in the Oracle HTTP Server product of Oracle Fusion Middleware (component: Web Listener). The supported version that is affected is 11.1.1.9.0. Difficult to exploit vulnerability allows unauthenticated attacker with network access via HTTP to compromise Oracle HTTP Server. Successful attacks of this vulnerability can result in unauthorized update, insert or delete access to some of Oracle HTTP Server accessible data. CVSS 3.1 Base Score 3.7 (Integrity impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:N/I:L/A:N). |
2021-10-20 |
not yet calculated |
CVE-2021-2480
MISC |
oracle — fusion
|
Vulnerability in the Oracle HTTP Server product of Oracle Fusion Middleware (component: OSSL Module). The supported version that is affected is 11.1.1.9.0. Difficult to exploit vulnerability allows unauthenticated attacker with network access via HTTPS to compromise Oracle HTTP Server. Successful attacks of this vulnerability can result in unauthorized access to critical data or complete access to all Oracle HTTP Server accessible data. CVSS 3.1 Base Score 5.9 (Confidentiality impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:N/A:N). |
2021-10-20 |
not yet calculated |
CVE-2021-35666
MISC |
oracle — fusion
|
Vulnerability in the Oracle Outside In Technology product of Oracle Fusion Middleware (component: Outside In Filters). The supported version that is affected is 8.5.5. Easily exploitable vulnerability allows unauthenticated attacker with network access via HTTP to compromise Oracle Outside In Technology. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of Oracle Outside In Technology. Note: Outside In Technology is a suite of software development kits (SDKs). The protocol and CVSS Base Score depend on the software that uses Outside In Technology. The CVSS score assumes that the software passes data received over a network directly to Outside In Technology, but if data is not received over a network the CVSS score may be lower. CVSS 3.1 Base Score 7.5 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-35662
MISC |
oracle — fusion
|
Vulnerability in the Oracle Outside In Technology product of Oracle Fusion Middleware (component: Outside In Filters). The supported version that is affected is 8.5.5. Easily exploitable vulnerability allows unauthenticated attacker with network access via HTTP to compromise Oracle Outside In Technology. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of Oracle Outside In Technology. Note: Outside In Technology is a suite of software development kits (SDKs). The protocol and CVSS Base Score depend on the software that uses Outside In Technology. The CVSS score assumes that the software passes data received over a network directly to Outside In Technology, but if data is not received over a network the CVSS score may be lower. CVSS 3.1 Base Score 7.5 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-35661
MISC |
oracle — hyperion
|
Vulnerability in the Hyperion Financial Reporting product of Oracle Hyperion (component: Repository). The supported version that is affected is 11.2.6.0. Easily exploitable vulnerability allows unauthenticated attacker with network access via HTTP to compromise Hyperion Financial Reporting. Successful attacks require human interaction from a person other than the attacker and while the vulnerability is in Hyperion Financial Reporting, attacks may significantly impact additional products. Successful attacks of this vulnerability can result in unauthorized update, insert or delete access to some of Hyperion Financial Reporting accessible data as well as unauthorized read access to a subset of Hyperion Financial Reporting accessible data. CVSS 3.1 Base Score 6.1 (Confidentiality and Integrity impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N). |
2021-10-20 |
not yet calculated |
CVE-2021-35665
MISC |
| oracle — java_se |
Vulnerability in the Java SE, Oracle GraalVM Enterprise Edition product of Oracle Java SE (component: ImageIO). Supported versions that are affected are Java SE: 7u311, 8u301, 11.0.12, 17; Oracle GraalVM Enterprise Edition: 20.3.3 and 21.2.0. Easily exploitable vulnerability allows unauthenticated attacker with network access via multiple protocols to compromise Java SE, Oracle GraalVM Enterprise Edition. Successful attacks of this vulnerability can result in unauthorized ability to cause a partial denial of service (partial DOS) of Java SE, Oracle GraalVM Enterprise Edition. Note: This vulnerability applies to Java deployments, typically in clients running sandboxed Java Web Start applications or sandboxed Java applets, that load and run untrusted code (e.g., code that comes from the internet) and rely on the Java sandbox for security. This vulnerability can also be exploited by using APIs in the specified Component, e.g., through a web service which supplies data to the APIs. CVSS 3.1 Base Score 5.3 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:L). |
2021-10-20 |
not yet calculated |
CVE-2021-35586
MISC
CONFIRM |
oracle — java_se
|
Vulnerability in the Java SE, Oracle GraalVM Enterprise Edition product of Oracle Java SE (component: Utility). Supported versions that are affected are Java SE: 7u311, 8u301, 11.0.12, 17; Oracle GraalVM Enterprise Edition: 20.3.3 and 21.2.0. Easily exploitable vulnerability allows unauthenticated attacker with network access via multiple protocols to compromise Java SE, Oracle GraalVM Enterprise Edition. Successful attacks of this vulnerability can result in unauthorized ability to cause a partial denial of service (partial DOS) of Java SE, Oracle GraalVM Enterprise Edition. Note: This vulnerability applies to Java deployments, typically in clients running sandboxed Java Web Start applications or sandboxed Java applets, that load and run untrusted code (e.g., code that comes from the internet) and rely on the Java sandbox for security. This vulnerability can also be exploited by using APIs in the specified Component, e.g., through a web service which supplies data to the APIs. CVSS 3.1 Base Score 5.3 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:L). |
2021-10-20 |
not yet calculated |
CVE-2021-35561
MISC
CONFIRM |
oracle — java_se
|
Vulnerability in the Java SE, Oracle GraalVM Enterprise Edition product of Oracle Java SE (component: JSSE). Supported versions that are affected are Java SE: 8u301, 11.0.12, 17; Oracle GraalVM Enterprise Edition: 20.3.3 and 21.2.0. Easily exploitable vulnerability allows unauthenticated attacker with network access via TLS to compromise Java SE, Oracle GraalVM Enterprise Edition. Successful attacks of this vulnerability can result in unauthorized ability to cause a partial denial of service (partial DOS) of Java SE, Oracle GraalVM Enterprise Edition. Note: This vulnerability can only be exploited by supplying data to APIs in the specified Component without using Untrusted Java Web Start applications or Untrusted Java applets, such as through a web service. CVSS 3.1 Base Score 5.3 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:L). |
2021-10-20 |
not yet calculated |
CVE-2021-35578
MISC
CONFIRM |
oracle — java_se
|
Vulnerability in the Java SE, Oracle GraalVM Enterprise Edition product of Oracle Java SE (component: Hotspot). Supported versions that are affected are Java SE: 7u311, 8u301; Oracle GraalVM Enterprise Edition: 20.3.3 and 21.2.0. Difficult to exploit vulnerability allows unauthenticated attacker with network access via multiple protocols to compromise Java SE, Oracle GraalVM Enterprise Edition. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in unauthorized ability to cause a partial denial of service (partial DOS) of Java SE, Oracle GraalVM Enterprise Edition. Note: This vulnerability applies to Java deployments, typically in clients running sandboxed Java Web Start applications or sandboxed Java applets, that load and run untrusted code (e.g., code that comes from the internet) and rely on the Java sandbox for security. This vulnerability can also be exploited by using APIs in the specified Component, e.g., through a web service which supplies data to the APIs. CVSS 3.1 Base Score 3.1 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:H/PR:N/UI:R/S:U/C:N/I:N/A:L). |
2021-10-20 |
not yet calculated |
CVE-2021-35588
MISC
CONFIRM |
oracle — java_se
|
Vulnerability in the Java SE, Oracle GraalVM Enterprise Edition product of Oracle Java SE (component: JSSE). Supported versions that are affected are Java SE: 7u311, 8u301, 11.0.12; Oracle GraalVM Enterprise Edition: 20.3.3 and 21.2.0. Easily exploitable vulnerability allows unauthenticated attacker with network access via TLS to compromise Java SE, Oracle GraalVM Enterprise Edition. Successful attacks of this vulnerability can result in unauthorized ability to cause a partial denial of service (partial DOS) of Java SE, Oracle GraalVM Enterprise Edition. Note: This vulnerability can only be exploited by supplying data to APIs in the specified Component without using Untrusted Java Web Start applications or Untrusted Java applets, such as through a web service. CVSS 3.1 Base Score 5.3 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:L). |
2021-10-20 |
not yet calculated |
CVE-2021-35565
MISC
CONFIRM |
oracle — java_se
|
Vulnerability in the Java SE, Oracle GraalVM Enterprise Edition product of Oracle Java SE (component: Keytool). Supported versions that are affected are Java SE: 7u311, 8u301, 11.0.12, 17; Oracle GraalVM Enterprise Edition: 20.3.3 and 21.2.0. Easily exploitable vulnerability allows unauthenticated attacker with network access via multiple protocols to compromise Java SE, Oracle GraalVM Enterprise Edition. Successful attacks of this vulnerability can result in unauthorized update, insert or delete access to some of Java SE, Oracle GraalVM Enterprise Edition accessible data. Note: This vulnerability applies to Java deployments, typically in clients running sandboxed Java Web Start applications or sandboxed Java applets, that load and run untrusted code (e.g., code that comes from the internet) and rely on the Java sandbox for security. This vulnerability can also be exploited by using APIs in the specified Component, e.g., through a web service which supplies data to the APIs. CVSS 3.1 Base Score 5.3 (Integrity impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:L/A:N). |
2021-10-20 |
not yet calculated |
CVE-2021-35564
MISC
CONFIRM |
oracle — java_se
|
Vulnerability in the Java SE, Oracle GraalVM Enterprise Edition product of Oracle Java SE (component: JSSE). Supported versions that are affected are Java SE: 7u311, 8u301, 11.0.12, 17; Oracle GraalVM Enterprise Edition: 20.3.3 and 21.2.0. Difficult to exploit vulnerability allows unauthenticated attacker with network access via TLS to compromise Java SE, Oracle GraalVM Enterprise Edition. Successful attacks of this vulnerability can result in unauthorized read access to a subset of Java SE, Oracle GraalVM Enterprise Edition accessible data. Note: This vulnerability applies to Java deployments, typically in clients running sandboxed Java Web Start applications or sandboxed Java applets, that load and run untrusted code (e.g., code that comes from the internet) and rely on the Java sandbox for security. This vulnerability can also be exploited by using APIs in the specified Component, e.g., through a web service which supplies data to the APIs. CVSS 3.1 Base Score 3.7 (Confidentiality impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:L/I:N/A:N). |
2021-10-20 |
not yet calculated |
CVE-2021-35603
MISC
CONFIRM |
oracle — java_se
|
Vulnerability in the Java SE, Oracle GraalVM Enterprise Edition product of Oracle Java SE (component: Libraries). Supported versions that are affected are Java SE: 8u301, 11.0.12, 17; Oracle GraalVM Enterprise Edition: 20.3.3 and 21.2.0. Easily exploitable vulnerability allows low privileged attacker with network access via Kerberos to compromise Java SE, Oracle GraalVM Enterprise Edition. Successful attacks require human interaction from a person other than the attacker and while the vulnerability is in Java SE, Oracle GraalVM Enterprise Edition, attacks may significantly impact additional products. Successful attacks of this vulnerability can result in unauthorized access to critical data or complete access to all Java SE, Oracle GraalVM Enterprise Edition accessible data. Note: This vulnerability applies to Java deployments, typically in clients running sandboxed Java Web Start applications or sandboxed Java applets, that load and run untrusted code (e.g., code that comes from the internet) and rely on the Java sandbox for security. This vulnerability can also be exploited by using APIs in the specified Component, e.g., through a web service which supplies data to the APIs. CVSS 3.1 Base Score 6.8 (Confidentiality impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:H/I:N/A:N). |
2021-10-20 |
not yet calculated |
CVE-2021-35567
MISC
CONFIRM |
oracle — java_se
|
Vulnerability in the Java SE product of Oracle Java SE (component: Deployment). The supported version that is affected is Java SE: 8u301. Difficult to exploit vulnerability allows unauthenticated attacker with network access via multiple protocols to compromise Java SE. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of Java SE. Note: This vulnerability applies to Java deployments, typically in clients running sandboxed Java Web Start applications or sandboxed Java applets, that load and run untrusted code (e.g., code that comes from the internet) and rely on the Java sandbox for security. This vulnerability does not apply to Java deployments, typically in servers, that load and run only trusted code (e.g., code installed by an administrator). CVSS 3.1 Base Score 7.5 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:H/PR:N/UI:R/S:U/C:H/I:H/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-35560
MISC
CONFIRM |
oracle — java_se
|
Vulnerability in the Java SE, Oracle GraalVM Enterprise Edition product of Oracle Java SE (component: Swing). Supported versions that are affected are Java SE: 7u311, 8u301, 11.0.12, 17; Oracle GraalVM Enterprise Edition: 20.3.3 and 21.2.0. Easily exploitable vulnerability allows unauthenticated attacker with network access via multiple protocols to compromise Java SE, Oracle GraalVM Enterprise Edition. Successful attacks of this vulnerability can result in unauthorized ability to cause a partial denial of service (partial DOS) of Java SE, Oracle GraalVM Enterprise Edition. Note: This vulnerability applies to Java deployments, typically in clients running sandboxed Java Web Start applications or sandboxed Java applets, that load and run untrusted code (e.g., code that comes from the internet) and rely on the Java sandbox for security. This vulnerability can also be exploited by using APIs in the specified Component, e.g., through a web service which supplies data to the APIs. CVSS 3.1 Base Score 5.3 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:L). |
2021-10-20 |
not yet calculated |
CVE-2021-35559
MISC
CONFIRM |
oracle — java_se
|
Vulnerability in the Java SE, Oracle GraalVM Enterprise Edition product of Oracle Java SE (component: JSSE). Supported versions that are affected are Java SE: 7u311, 8u301, 11.0.12; Oracle GraalVM Enterprise Edition: 20.3.3 and 21.2.0. Difficult to exploit vulnerability allows unauthenticated attacker with network access via TLS to compromise Java SE, Oracle GraalVM Enterprise Edition. Successful attacks of this vulnerability can result in unauthorized access to critical data or complete access to all Java SE, Oracle GraalVM Enterprise Edition accessible data. Note: This vulnerability applies to Java deployments, typically in clients running sandboxed Java Web Start applications or sandboxed Java applets, that load and run untrusted code (e.g., code that comes from the internet) and rely on the Java sandbox for security. This vulnerability can also be exploited by using APIs in the specified Component, e.g., through a web service which supplies data to the APIs. CVSS 3.1 Base Score 5.9 (Confidentiality impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:N/A:N). |
2021-10-20 |
not yet calculated |
CVE-2021-35550
MISC
CONFIRM |
oracle — java_se
|
Vulnerability in the Java SE, Oracle GraalVM Enterprise Edition product of Oracle Java SE (component: Swing). Supported versions that are affected are Java SE: 7u311, 8u301, 11.0.12, 17; Oracle GraalVM Enterprise Edition: 20.3.3 and 21.2.0. Easily exploitable vulnerability allows unauthenticated attacker with network access via multiple protocols to compromise Java SE, Oracle GraalVM Enterprise Edition. Successful attacks of this vulnerability can result in unauthorized ability to cause a partial denial of service (partial DOS) of Java SE, Oracle GraalVM Enterprise Edition. Note: This vulnerability applies to Java deployments, typically in clients running sandboxed Java Web Start applications or sandboxed Java applets, that load and run untrusted code (e.g., code that comes from the internet) and rely on the Java sandbox for security. This vulnerability does not apply to Java deployments, typically in servers, that load and run only trusted code (e.g., code installed by an administrator). CVSS 3.1 Base Score 5.3 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:L). |
2021-10-20 |
not yet calculated |
CVE-2021-35556
MISC
CONFIRM |
| oracle — mysql |
Vulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.5.23 and prior, 7.6.19 and prior and 8.0.26 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-35592
MISC
MISC
CONFIRM |
| oracle — mysql |
Vulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: ndbcluster/plugin DDL). Supported versions that are affected are 8.0.26 and prior. Easily exploitable vulnerability allows low privileged attacker with network access via multiple protocols to compromise MySQL Cluster. Successful attacks of this vulnerability can result in unauthorized ability to cause a partial denial of service (partial DOS) of MySQL Cluster. CVSS 3.1 Base Score 4.3 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:N/I:N/A:L). |
2021-10-20 |
not yet calculated |
CVE-2021-35584
MISC
CONFIRM |
| oracle — mysql |
Vulnerability in the MySQL Server product of Oracle MySQL (component: Server: Windows). Supported versions that are affected are 8.0.25 and prior. Easily exploitable vulnerability allows unauthenticated attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 7.5 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-35583
MISC
CONFIRM |
| oracle — mysql |
Vulnerability in the MySQL Server product of Oracle MySQL (component: Server: Optimizer). Supported versions that are affected are 8.0.26 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server as well as unauthorized update, insert or delete access to some of MySQL Server accessible data. CVSS 3.1 Base Score 5.5 (Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:L/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-35612
MISC
CONFIRM |
| oracle — mysql |
Vulnerability in the MySQL Server product of Oracle MySQL (component: Server: Optimizer). Supported versions that are affected are 8.0.26 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 4.9 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-35575
MISC
CONFIRM |
| oracle — mysql |
Vulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.33 and prior, 7.5.23 and prior, 7.6.19 and prior and 8.0.26 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-35593
MISC
MISC
CONFIRM |
| oracle — mysql |
Vulnerability in the MySQL Server product of Oracle MySQL (component: Server: Error Handling). Supported versions that are affected are 8.0.26 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 4.9 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-35596
MISC
CONFIRM |
| oracle — mysql |
Vulnerability in the MySQL Client product of Oracle MySQL (component: C API). Supported versions that are affected are 8.0.26 and prior. Easily exploitable vulnerability allows low privileged attacker with network access via multiple protocols to compromise MySQL Client. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Client. CVSS 3.1 Base Score 6.5 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:N/I:N/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-35597
MISC
CONFIRM |
| oracle — mysql |
Vulnerability in the MySQL Server product of Oracle MySQL (component: Server: Group Replication Plugin). Supported versions that are affected are 8.0.26 and prior. Difficult to exploit vulnerability allows low privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 5.3 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:H/PR:L/UI:N/S:U/C:N/I:N/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-35608
MISC
CONFIRM |
| oracle — mysql |
Vulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.33 and prior, 7.5.23 and prior, 7.6.19 and prior and 8.0.26 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-35590
MISC
MISC
CONFIRM |
oracle — mysql
|
Vulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.33 and prior, 7.5.23 and prior, 7.6.19 and prior and 8.0.26 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-35594
MISC
MISC
CONFIRM |
oracle — mysql
|
Vulnerability in the MySQL Server product of Oracle MySQL (component: InnoDB). Supported versions that are affected are 5.7.35 and prior and 8.0.26 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server as well as unauthorized update, insert or delete access to some of MySQL Server accessible data. CVSS 3.1 Base Score 5.5 (Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:L/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-35604
MISC
CONFIRM |
oracle — mysql
|
Vulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.33 and prior, 7.5.23 and prior, 7.6.19 and prior and 8.0.26 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-35598
MISC
MISC
CONFIRM |
oracle — mysql
|
Vulnerability in the MySQL Server product of Oracle MySQL (component: Server: Optimizer). Supported versions that are affected are 8.0.26 and prior. Easily exploitable vulnerability allows low privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server as well as unauthorized update, insert or delete access to some of MySQL Server accessible data. CVSS 3.1 Base Score 7.1 (Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:N/I:L/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-35610
MISC
CONFIRM |
oracle — mysql
|
Vulnerability in the MySQL Server product of Oracle MySQL (component: Server: DML). Supported versions that are affected are 8.0.26 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 4.9 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-35591
MISC
CONFIRM |
oracle — mysql
|
Vulnerability in the MySQL Server product of Oracle MySQL (component: Server: DML). Supported versions that are affected are 8.0.26 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 4.9 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-2478
MISC
CONFIRM |
oracle — mysql
|
Vulnerability in the MySQL Connectors product of Oracle MySQL (component: Connector/J). Supported versions that are affected are 8.0.26 and prior. Difficult to exploit vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Connectors. Successful attacks of this vulnerability can result in unauthorized access to critical data or complete access to all MySQL Connectors accessible data and unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Connectors. CVSS 3.1 Base Score 5.9 (Confidentiality and Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:H/PR:H/UI:N/S:U/C:H/I:N/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-2471
MISC |
oracle — mysql
|
Vulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 8.0.26 and prior. Difficult to exploit vulnerability allows unauthenticated attacker with network access via multiple protocols to compromise MySQL Cluster. Successful attacks of this vulnerability can result in unauthorized ability to cause a partial denial of service (partial DOS) of MySQL Cluster. CVSS 3.1 Base Score 3.7 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:N/I:N/A:L). |
2021-10-20 |
not yet calculated |
CVE-2021-35613
MISC
CONFIRM |
oracle — mysql
|
Vulnerability in the MySQL Server product of Oracle MySQL (component: Server: Options). Supported versions that are affected are 8.0.26 and prior. Difficult to exploit vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server as well as unauthorized update, insert or delete access to some of MySQL Server accessible data. CVSS 3.1 Base Score 5.0 (Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:H/PR:H/UI:N/S:U/C:N/I:L/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-35602
MISC
CONFIRM |
oracle — mysql
|
Vulnerability in the MySQL Server product of Oracle MySQL (component: Server: DML). Supported versions that are affected are 8.0.26 and prior. Easily exploitable vulnerability allows low privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 6.5 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:N/I:N/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-35607
MISC
CONFIRM |
oracle — mysql
|
Vulnerability in the MySQL Server product of Oracle MySQL (component: Server: Replication). Supported versions that are affected are 8.0.26 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 4.9 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-35546
MISC
CONFIRM |
oracle — mysql
|
Vulnerability in the MySQL Server product of Oracle MySQL (component: Server: Optimizer). Supported versions that are affected are 8.0.26 and prior. Easily exploitable vulnerability allows low privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 6.5 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:N/I:N/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-2481
MISC
CONFIRM |
oracle — mysql
|
Vulnerability in the MySQL Server product of Oracle MySQL (component: Server: Optimizer). Supported versions that are affected are 8.0.26 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via MySQL Protcol to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 4.9 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-35577
MISC
CONFIRM |
oracle — mysql
|
Vulnerability in the MySQL Server product of Oracle MySQL (component: Server: DML). Supported versions that are affected are 8.0.25 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 4.9 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-35537
MISC
CONFIRM |
oracle — mysql
|
Vulnerability in the MySQL Server product of Oracle MySQL (component: Server: DML). Supported versions that are affected are 8.0.26 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 4.9 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-2479
MISC
CONFIRM |
| oracle — mysql_server |
Vulnerability in the MySQL Server product of Oracle MySQL (component: Server: Optimizer). Supported versions that are affected are 8.0.26 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 4.9 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-35638
MISC
CONFIRM |
| oracle — mysql_server |
Vulnerability in the MySQL Server product of Oracle MySQL (component: Server: Optimizer). Supported versions that are affected are 8.0.26 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 4.9 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-35644
MISC
CONFIRM |
| oracle — mysql_server |
Vulnerability in the MySQL Server product of Oracle MySQL (component: Server: PS). Supported versions that are affected are 8.0.26 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 4.9 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-35637
MISC
CONFIRM |
| oracle — mysql_server |
Vulnerability in the MySQL Server product of Oracle MySQL (component: Server: Data Dictionary). Supported versions that are affected are 8.0.26 and prior. Easily exploitable vulnerability allows high privileged attacker with logon to the infrastructure where MySQL Server executes to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 4.4 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:L/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-35632
MISC
CONFIRM |
| oracle — mysql_server |
Vulnerability in the MySQL Server product of Oracle MySQL (component: Server: Optimizer). Supported versions that are affected are 8.0.26 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 4.9 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-35634
MISC
CONFIRM |
| oracle — mysql_server |
Vulnerability in the MySQL Server product of Oracle MySQL (component: Server: Optimizer). Supported versions that are affected are 8.0.26 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 4.9 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-35642
MISC
CONFIRM |
| oracle — mysql_server |
Vulnerability in the MySQL Server product of Oracle MySQL (component: Server: Optimizer). Supported versions that are affected are 8.0.25 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 4.9 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-35629
MISC
CONFIRM |
| oracle — mysql_server |
Vulnerability in the MySQL Server product of Oracle MySQL (component: Server: Optimizer). Supported versions that are affected are 8.0.26 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 4.9 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-35643
MISC
CONFIRM |
| oracle — mysql_server |
Vulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 7.4.33 and prior, 7.5.23 and prior, 7.6.19 and prior and 8.0.26 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in takeover of MySQL Cluster. CVSS 3.1 Base Score 6.3 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-35621
MISC
MISC
CONFIRM |
| oracle — mysql_server |
Vulnerability in the MySQL Server product of Oracle MySQL (component: Server: Optimizer). Supported versions that are affected are 8.0.26 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 4.9 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-35645
MISC
CONFIRM |
| oracle — mysql_server |
Vulnerability in the MySQL Server product of Oracle MySQL (component: Server: GIS). Supported versions that are affected are 8.0.26 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 4.9 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-35631
MISC
CONFIRM |
| oracle — mysql_server |
Vulnerability in the MySQL Server product of Oracle MySQL (component: Server: Optimizer). Supported versions that are affected are 8.0.26 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 4.9 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-35636
MISC
CONFIRM |
| oracle — mysql_server |
Vulnerability in the MySQL Server product of Oracle MySQL (component: Server: Security: Encryption). Supported versions that are affected are 8.0.26 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 4.9 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-35622
MISC
CONFIRM |
| oracle — mysql_server |
Vulnerability in the MySQL Server product of Oracle MySQL (component: Server: Security: Roles). Supported versions that are affected are 8.0.26 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized read access to a subset of MySQL Server accessible data. CVSS 3.1 Base Score 2.7 (Confidentiality impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:L/I:N/A:N). |
2021-10-20 |
not yet calculated |
CVE-2021-35623
MISC
CONFIRM |
| oracle — mysql_server |
Vulnerability in the MySQL Server product of Oracle MySQL (component: Server: Security: Privileges). Supported versions that are affected are 5.7.35 and prior and 8.0.26 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized creation, deletion or modification access to critical data or all MySQL Server accessible data. CVSS 3.1 Base Score 4.9 (Integrity impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:H/A:N). |
2021-10-20 |
not yet calculated |
CVE-2021-35624
MISC
CONFIRM |
| oracle — mysql_server |
Vulnerability in the MySQL Server product of Oracle MySQL (component: Server: Stored Procedure). Supported versions that are affected are 8.0.26 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 4.9 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-35639
MISC
CONFIRM |
oracle — mysql_server
|
Vulnerability in the MySQL Server product of Oracle MySQL (component: Server: Security: Privileges). Supported versions that are affected are 8.0.26 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized read access to a subset of MySQL Server accessible data. CVSS 3.1 Base Score 2.7 (Confidentiality impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:L/I:N/A:N). |
2021-10-20 |
not yet calculated |
CVE-2021-35625
MISC
CONFIRM |
oracle — mysql_server
|
Vulnerability in the MySQL Server product of Oracle MySQL (component: Server: Optimizer). Supported versions that are affected are 8.0.26 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 4.9 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-35628
MISC
CONFIRM |
oracle — mysql_server
|
Vulnerability in the MySQL Cluster product of Oracle MySQL (component: Cluster: General). Supported versions that are affected are 8.0.26 and prior. Difficult to exploit vulnerability allows high privileged attacker with access to the physical communication segment attached to the hardware where the MySQL Cluster executes to compromise MySQL Cluster. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in unauthorized ability to cause a partial denial of service (partial DOS) of MySQL Cluster. CVSS 3.1 Base Score 1.8 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:H/PR:H/UI:R/S:U/C:N/I:N/A:L). |
2021-10-20 |
not yet calculated |
CVE-2021-35618
MISC
CONFIRM |
oracle — mysql_server
|
Vulnerability in the MySQL Server product of Oracle MySQL (component: Server: Optimizer). Supported versions that are affected are 8.0.26 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 4.9 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-35626
MISC
CONFIRM |
oracle — mysql_server
|
Vulnerability in the MySQL Server product of Oracle MySQL (component: Server: Optimizer). Supported versions that are affected are 8.0.26 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 4.9 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-35641
MISC
CONFIRM |
oracle — mysql_server
|
Vulnerability in the MySQL Server product of Oracle MySQL (component: Server: Options). Supported versions that are affected are 8.0.26 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized creation, deletion or modification access to critical data or all MySQL Server accessible data. CVSS 3.1 Base Score 4.9 (Integrity impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:H/A:N). |
2021-10-20 |
not yet calculated |
CVE-2021-35630
MISC
CONFIRM |
oracle — mysql_server
|
Vulnerability in the MySQL Server product of Oracle MySQL (component: Server: DDL). Supported versions that are affected are 8.0.26 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized update, insert or delete access to some of MySQL Server accessible data. CVSS 3.1 Base Score 2.7 (Integrity impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:L/A:N). |
2021-10-20 |
not yet calculated |
CVE-2021-35640
MISC
CONFIRM |
oracle — mysql_server
|
Vulnerability in the MySQL Server product of Oracle MySQL (component: Server: Logging). Supported versions that are affected are 8.0.26 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a partial denial of service (partial DOS) of MySQL Server. CVSS 3.1 Base Score 2.7 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:L). |
2021-10-20 |
not yet calculated |
CVE-2021-35633
MISC
CONFIRM |
oracle — mysql_server
|
Vulnerability in the MySQL Server product of Oracle MySQL (component: Server: Optimizer). Supported versions that are affected are 8.0.26 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 4.9 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-35635
MISC
CONFIRM |
oracle — mysql_server
|
Vulnerability in the MySQL Server product of Oracle MySQL (component: Server: Optimizer). Supported versions that are affected are 8.0.26 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 4.9 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-35646
MISC
CONFIRM |
oracle — mysql_server
|
Vulnerability in the MySQL Server product of Oracle MySQL (component: Server: Optimizer). Supported versions that are affected are 8.0.26 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 4.9 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-35647
MISC
CONFIRM |
oracle — mysql_server
|
Vulnerability in the MySQL Server product of Oracle MySQL (component: Server: FTS). Supported versions that are affected are 8.0.26 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 4.9 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-35648
MISC
CONFIRM |
oracle — mysql_server
|
Vulnerability in the MySQL Server product of Oracle MySQL (component: Server: Optimizer). Supported versions that are affected are 8.0.26 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 4.9 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-35627
MISC
CONFIRM |
| oracle — peoplesoft |
Vulnerability in the PeopleSoft Enterprise CS Student Records product of Oracle PeopleSoft (component: Class Search). The supported version that is affected is 9.2. Easily exploitable vulnerability allows low privileged attacker with network access via HTTP to compromise PeopleSoft Enterprise CS Student Records. Successful attacks require human interaction from a person other than the attacker and while the vulnerability is in PeopleSoft Enterprise CS Student Records, attacks may significantly impact additional products. Successful attacks of this vulnerability can result in unauthorized update, insert or delete access to some of PeopleSoft Enterprise CS Student Records accessible data as well as unauthorized read access to a subset of PeopleSoft Enterprise CS Student Records accessible data. CVSS 3.1 Base Score 5.4 (Confidentiality and Integrity impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N). |
2021-10-20 |
not yet calculated |
CVE-2021-35553
MISC |
| oracle — peoplesoft |
Vulnerability in the PeopleSoft Enterprise PeopleTools product of Oracle PeopleSoft (component: Business Interlink). Supported versions that are affected are 8.57, 8.58 and 8.59. Easily exploitable vulnerability allows unauthenticated attacker with network access via HTTP to compromise PeopleSoft Enterprise PeopleTools. Successful attacks require human interaction from a person other than the attacker and while the vulnerability is in PeopleSoft Enterprise PeopleTools, attacks may significantly impact additional products. Successful attacks of this vulnerability can result in unauthorized update, insert or delete access to some of PeopleSoft Enterprise PeopleTools accessible data as well as unauthorized read access to a subset of PeopleSoft Enterprise PeopleTools accessible data. CVSS 3.1 Base Score 6.1 (Confidentiality and Integrity impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N). |
2021-10-20 |
not yet calculated |
CVE-2021-35595
MISC |
| oracle — peoplesoft |
Vulnerability in the PeopleSoft Enterprise CS Campus Community product of Oracle PeopleSoft (component: Notification Framework). Supported versions that are affected are 9.0 and 9.2. Easily exploitable vulnerability allows low privileged attacker with access to the physical communication segment attached to the hardware where the PeopleSoft Enterprise CS Campus Community executes to compromise PeopleSoft Enterprise CS Campus Community. Successful attacks of this vulnerability can result in unauthorized access to critical data or complete access to all PeopleSoft Enterprise CS Campus Community accessible data. CVSS 3.1 Base Score 5.7 (Confidentiality impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:L/PR:L/UI:N/S:U/C:H/I:N/A:N). |
2021-10-20 |
not yet calculated |
CVE-2021-35606
MISC |
oracle — peoplesoft
|
Vulnerability in the PeopleSoft Enterprise SCM product of Oracle PeopleSoft (component: Supplier Portal). The supported version that is affected is 9.2. Easily exploitable vulnerability allows low privileged attacker with network access via HTTP to compromise PeopleSoft Enterprise SCM. Successful attacks require human interaction from a person other than the attacker and while the vulnerability is in PeopleSoft Enterprise SCM, attacks may significantly impact additional products. Successful attacks of this vulnerability can result in unauthorized update, insert or delete access to some of PeopleSoft Enterprise SCM accessible data as well as unauthorized read access to a subset of PeopleSoft Enterprise SCM accessible data. CVSS 3.1 Base Score 5.4 (Confidentiality and Integrity impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N). |
2021-10-20 |
not yet calculated |
CVE-2021-35541
MISC |
oracle — peoplesoft
|
Vulnerability in the PeopleSoft Enterprise CC Common Application Objects product of Oracle PeopleSoft (component: Activity Guide Composer). The supported version that is affected is 9.2. Easily exploitable vulnerability allows low privileged attacker with network access via HTTP to compromise PeopleSoft Enterprise CC Common Application Objects. Successful attacks of this vulnerability can result in unauthorized creation, deletion or modification access to critical data or all PeopleSoft Enterprise CC Common Application Objects accessible data as well as unauthorized access to critical data or complete access to all PeopleSoft Enterprise CC Common Application Objects accessible data. CVSS 3.1 Base Score 8.1 (Confidentiality and Integrity impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:N). |
2021-10-20 |
not yet calculated |
CVE-2021-35543
MISC |
oracle — peoplesoft
|
Vulnerability in the PeopleSoft Enterprise PeopleTools product of Oracle PeopleSoft (component: SQR). Supported versions that are affected are 8.57, 8.58 and 8.59. Easily exploitable vulnerability allows low privileged attacker with network access via HTTP to compromise PeopleSoft Enterprise PeopleTools. Successful attacks of this vulnerability can result in unauthorized access to critical data or complete access to all PeopleSoft Enterprise PeopleTools accessible data. CVSS 3.1 Base Score 6.5 (Confidentiality impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:N/A:N). |
2021-10-20 |
not yet calculated |
CVE-2021-35609
MISC |
oracle — peoplesoft
|
Vulnerability in the PeopleSoft Enterprise CS SA Integration Pack product of Oracle PeopleSoft (component: Students Administration). Supported versions that are affected are 9.0 and 9.2. Easily exploitable vulnerability allows low privileged attacker with access to the physical communication segment attached to the hardware where the PeopleSoft Enterprise CS SA Integration Pack executes to compromise PeopleSoft Enterprise CS SA Integration Pack. Successful attacks of this vulnerability can result in unauthorized access to critical data or complete access to all PeopleSoft Enterprise CS SA Integration Pack accessible data. CVSS 3.1 Base Score 5.7 (Confidentiality impacts). CVSS Vector: (CVSS:3.1/AV:A/AC:L/PR:L/UI:N/S:U/C:H/I:N/A:N). |
2021-10-20 |
not yet calculated |
CVE-2021-35601
MISC |
oracle — peoplesoft
|
Vulnerability in the PeopleSoft Enterprise CS Academic Advisement product of Oracle PeopleSoft (component: Advising Notes). The supported version that is affected is 9.2. Easily exploitable vulnerability allows low privileged attacker with network access via HTTP to compromise PeopleSoft Enterprise CS Academic Advisement. Successful attacks of this vulnerability can result in unauthorized update, insert or delete access to some of PeopleSoft Enterprise CS Academic Advisement accessible data as well as unauthorized read access to a subset of PeopleSoft Enterprise CS Academic Advisement accessible data. CVSS 3.1 Base Score 5.4 (Confidentiality and Integrity impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:L/I:L/A:N). |
2021-10-20 |
not yet calculated |
CVE-2021-35571
MISC |
oracle — peoplesoft
|
Vulnerability in the PeopleSoft Enterprise PeopleTools product of Oracle PeopleSoft (component: Rich Text Editor). Supported versions that are affected are 8.57, 8.58 and 8.59. Easily exploitable vulnerability allows unauthenticated attacker with network access via HTTP to compromise PeopleSoft Enterprise PeopleTools. Successful attacks require human interaction from a person other than the attacker and while the vulnerability is in PeopleSoft Enterprise PeopleTools, attacks may significantly impact additional products. Successful attacks of this vulnerability can result in unauthorized update, insert or delete access to some of PeopleSoft Enterprise PeopleTools accessible data as well as unauthorized read access to a subset of PeopleSoft Enterprise PeopleTools accessible data. CVSS 3.1 Base Score 6.1 (Confidentiality and Integrity impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N). |
2021-10-20 |
not yet calculated |
CVE-2021-35568
MISC |
oracle — solarias
|
Vulnerability in the Oracle Solaris product of Oracle Systems (component: Utility). The supported version that is affected is 11. Easily exploitable vulnerability allows low privileged attacker with logon to the infrastructure where Oracle Solaris executes to compromise Oracle Solaris. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in unauthorized update, insert or delete access to some of Oracle Solaris accessible data and unauthorized ability to cause a partial denial of service (partial DOS) of Oracle Solaris. CVSS 3.1 Base Score 3.9 (Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:L/AC:L/PR:L/UI:R/S:U/C:N/I:L/A:L). |
2021-10-20 |
not yet calculated |
CVE-2021-35549
MISC |
oracle — solaris
|
Vulnerability in the Oracle Solaris product of Oracle Systems (component: Filesystem). The supported version that is affected is 11. Easily exploitable vulnerability allows low privileged attacker with logon to the infrastructure where Oracle Solaris executes to compromise Oracle Solaris. While the vulnerability is in Oracle Solaris, attacks may significantly impact additional products. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of Oracle Solaris. CVSS 3.1 Base Score 6.5 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:C/C:N/I:N/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-35539
MISC |
oracle — solaris
|
Vulnerability in the Oracle Solaris product of Oracle Systems (component: Device drivers). The supported version that is affected is 11. Easily exploitable vulnerability allows high privileged attacker with logon to the infrastructure where Oracle Solaris executes to compromise Oracle Solaris. While the vulnerability is in Oracle Solaris, attacks may significantly impact additional products. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of Oracle Solaris. CVSS 3.1 Base Score 6.0 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:L/AC:L/PR:H/UI:N/S:C/C:N/I:N/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-35589
MISC |
oracle — supply_chain
|
Vulnerability in the Oracle Transportation Management product of Oracle Supply Chain (component: Authentication). The supported version that is affected is 6.4.3. Easily exploitable vulnerability allows unauthenticated attacker with network access via HTTP to compromise Oracle Transportation Management. Successful attacks of this vulnerability can result in unauthorized read access to a subset of Oracle Transportation Management accessible data. CVSS 3.1 Base Score 5.3 (Confidentiality impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:L/I:N/A:N). |
2021-10-20 |
not yet calculated |
CVE-2021-2476
MISC |
oracle — supply_chain
|
Vulnerability in the Oracle Transportation Management product of Oracle Supply Chain (component: UI Infrastructure). The supported version that is affected is 6.4.3. Easily exploitable vulnerability allows low privileged attacker with network access via HTTP to compromise Oracle Transportation Management. Successful attacks of this vulnerability can result in unauthorized update, insert or delete access to some of Oracle Transportation Management accessible data as well as unauthorized read access to a subset of Oracle Transportation Management accessible data. CVSS 3.1 Base Score 5.4 (Confidentiality and Integrity impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:L/I:L/A:N). |
2021-10-20 |
not yet calculated |
CVE-2021-35616
MISC |
oracle — virtualization
|
Vulnerability in the Oracle Secure Global Desktop product of Oracle Virtualization (component: Server). The supported version that is affected is 5.6. Easily exploitable vulnerability allows low privileged attacker with network access via multiple protocols to compromise Oracle Secure Global Desktop. Successful attacks of this vulnerability can result in unauthorized read access to a subset of Oracle Secure Global Desktop accessible data and unauthorized ability to cause a partial denial of service (partial DOS) of Oracle Secure Global Desktop. CVSS 3.1 Base Score 5.4 (Confidentiality and Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:L/I:N/A:L). |
2021-10-20 |
not yet calculated |
CVE-2021-35649
MISC |
oracle — virtualization
|
Vulnerability in the Oracle Secure Global Desktop product of Oracle Virtualization (component: Client). The supported version that is affected is 5.6. Easily exploitable vulnerability allows low privileged attacker with network access via multiple protocols to compromise Oracle Secure Global Desktop. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in unauthorized read access to a subset of Oracle Secure Global Desktop accessible data and unauthorized ability to cause a partial denial of service (partial DOS) of Oracle Secure Global Desktop. CVSS 3.1 Base Score 4.6 (Confidentiality and Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:U/C:L/I:N/A:L). |
2021-10-20 |
not yet calculated |
CVE-2021-35650
MISC |
oracle — vm_virtualbox
|
Vulnerability in the Oracle VM VirtualBox product of Oracle Virtualization (component: Core). The supported version that is affected is Prior to 6.1.28. Easily exploitable vulnerability allows high privileged attacker with logon to the infrastructure where Oracle VM VirtualBox executes to compromise Oracle VM VirtualBox. While the vulnerability is in Oracle VM VirtualBox, attacks may significantly impact additional products. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of Oracle VM VirtualBox and unauthorized read access to a subset of Oracle VM VirtualBox accessible data. CVSS 3.1 Base Score 6.7 (Confidentiality and Availability impacts). CVSS Vector: (CVSS:3.1/AV:L/AC:L/PR:H/UI:N/S:C/C:L/I:N/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-35545
MISC |
oracle — vm_virtualbox
|
Vulnerability in the Oracle VM VirtualBox product of Oracle Virtualization (component: Core). The supported version that is affected is Prior to 6.1.28. Easily exploitable vulnerability allows high privileged attacker with logon to the infrastructure where Oracle VM VirtualBox executes to compromise Oracle VM VirtualBox. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of Oracle VM VirtualBox. CVSS 3.1 Base Score 4.4 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:L/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-35542
MISC |
oracle — vm_virtualbox
|
Vulnerability in the Oracle VM VirtualBox product of Oracle Virtualization (component: Core). The supported version that is affected is Prior to 6.1.28. Easily exploitable vulnerability allows high privileged attacker with logon to the infrastructure where Oracle VM VirtualBox executes to compromise Oracle VM VirtualBox. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of Oracle VM VirtualBox. CVSS 3.1 Base Score 4.4 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:L/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-2475
MISC |
oracle — vm_virtualbox
|
Vulnerability in the Oracle VM VirtualBox product of Oracle Virtualization (component: Core). The supported version that is affected is Prior to 6.1.28. Easily exploitable vulnerability allows low privileged attacker with logon to the infrastructure where Oracle VM VirtualBox executes to compromise Oracle VM VirtualBox. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of Oracle VM VirtualBox. CVSS 3.1 Base Score 5.5 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:U/C:N/I:N/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-35540
MISC |
oracle — vm_virtualbox
|
Vulnerability in the Oracle VM VirtualBox product of Oracle Virtualization (component: Core). The supported version that is affected is Prior to 6.1.28. Easily exploitable vulnerability allows low privileged attacker with logon to the infrastructure where Oracle VM VirtualBox executes to compromise Oracle VM VirtualBox. Successful attacks of this vulnerability can result in takeover of Oracle VM VirtualBox. Note: This vulnerability does not apply to Windows systems. CVSS 3.1 Base Score 7.8 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-35538
MISC |
oracle — weblogic_server
|
Vulnerability in the Oracle WebLogic Server product of Oracle Fusion Middleware (component: Coherence Container). Supported versions that are affected are 12.1.3.0.0, 12.2.1.3.0, 12.2.1.4.0 and 14.1.1.0.0. Easily exploitable vulnerability allows unauthenticated attacker with network access via IIOP to compromise Oracle WebLogic Server. Successful attacks of this vulnerability can result in takeover of Oracle WebLogic Server. CVSS 3.1 Base Score 9.8 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-35617
MISC |
oracle — weblogic_server
|
Vulnerability in the Oracle WebLogic Server product of Oracle Fusion Middleware (component: Core). Supported versions that are affected are 10.3.6.0.0, 12.1.3.0.0, 12.2.1.3.0, 12.2.1.4.0 and 14.1.1.0.0. Easily exploitable vulnerability allows unauthenticated attacker with network access via T3 to compromise Oracle WebLogic Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of Oracle WebLogic Server. CVSS 3.1 Base Score 7.5 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H). |
2021-10-20 |
not yet calculated |
CVE-2021-35620
MISC |
oracle — weblogic_server
|
Vulnerability in the Oracle WebLogic Server product of Oracle Fusion Middleware (component: Diagnostics). Supported versions that are affected are 12.2.1.3.0, 12.2.1.4.0 and 14.1.1.0.0. Easily exploitable vulnerability allows unauthenticated attacker with network access via HTTP to compromise Oracle WebLogic Server. Successful attacks of this vulnerability can result in unauthorized update, insert or delete access to some of Oracle WebLogic Server accessible data. CVSS 3.1 Base Score 5.3 (Integrity impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:L/A:N). |
2021-10-20 |
not yet calculated |
CVE-2021-35552
MISC |
orion — platform
|
Each authenticated Orion Platform user in a MSP (Managed Service Provider) environment can view and browse all NetPath Services from all that MSP’s customers. This can lead to any user having a limited insight into other customer’s infrastructure and potential data cross-contamination. |
2021-10-21 |
not yet calculated |
CVE-2021-35225
MISC
MISC
MISC |
package — x-assign
|
This affects all versions of package x-assign. The global proto object can be polluted using the __proto__ object. |
2021-10-20 |
not yet calculated |
CVE-2021-23452
MISC
MISC |
passcovery_co_ltd — zip_password_recovery
|
Passcovery Co. Ltd ZIP Password Recovery v3.70.69.0 was discovered to contain a buffer overflow via the decompress function. |
2021-10-22 |
not yet calculated |
CVE-2020-28963
MISC |
perfex — cms
|
Perfex CRM v2.4.4 was discovered to contain a stored cross-site scripting (XSS) vulnerability in the component ./clients/client via the company name parameter. |
2021-10-22 |
not yet calculated |
CVE-2020-28961
MISC |
php — simple_payroll_system
|
The Simple Payroll System with Dynamic Tax Bracket in PHP using SQLite Free Source Code (by: oretnom23 ) is vulnerable from remote SQL-Injection-Bypass-Authentication for the admin account. The parameter (username) from the login form is not protected correctly and there is no security and escaping from malicious payloads. |
2021-10-22 |
not yet calculated |
CVE-2021-42169
MISC |
phpgurukul — user_registration_and_user_management_system
|
Phpgurukul User Registration & User Management System v2.0 was discovered to contain multiple stored cross-site scripting (XSS) vulnerabilities via the firstname and lastname parameters of the registration form & loginsystem input fields. |
2021-10-22 |
not yet calculated |
CVE-2020-23051
MISC |
portable_ltd — playable
|
Portable Ltd Playable v9.18 contains a code injection vulnerability in the filename parameter, which allows attackers to execute arbitrary web scripts or HTML via a crafted POST request. |
2021-10-22 |
not yet calculated |
CVE-2020-23037
MISC |
portable_ltd — playable
|
Portable Ltd Playable v9.18 was discovered to contain an arbitrary file upload vulnerability in the filename parameter of the upload module. This vulnerability allows attackers to execute arbitrary code via a crafted JPEG file. |
2021-10-22 |
not yet calculated |
CVE-2020-36485
MISC |
qutebrowser — qutebrowser
|
qutebrowser is an open source keyboard-focused browser with a minimal GUI. Starting with qutebrowser v1.7.0, the Windows installer for qutebrowser registers a `qutebrowserurl:` URL handler. With certain applications, opening a specially crafted `qutebrowserurl:…` URL can lead to execution of qutebrowser commands, which in turn allows arbitrary code execution via commands such as `:spawn` or `:debug-pyeval`. Only Windows installs where qutebrowser is registered as URL handler are affected. The issue has been fixed in qutebrowser v2.4.0. The fix also adds additional hardening for potential similar issues on Linux (by adding the new –untrusted-args flag to the .desktop file), though no such vulnerabilities are known. |
2021-10-21 |
not yet calculated |
CVE-2021-41146
CONFIRM
MISC |
rabbitmq — plugin
|
The HTTP interface was enabled for RabbitMQ Plugin in ARM 2020.2.6 and the ability to configure HTTPS was not available. |
2021-10-21 |
not yet calculated |
CVE-2021-35227
MISC
MISC |
rasa — rasa
|
Rasa is an open source machine learning framework to automate text-and voice-based conversations. In affected versions a vulnerability exists in the functionality that loads a trained model `tar.gz` file which allows a malicious actor to craft a `model.tar.gz` file which can overwrite or replace bot files in the bot directory. The vulnerability is fixed in Rasa 2.8.10. For users unable to update ensure that users do not upload untrusted model files, and restrict CLI or API endpoint access where a malicious actor could target a deployed Rasa instance. |
2021-10-21 |
not yet calculated |
CVE-2021-41127
CONFIRM
MISC |
rasa_x — rasa_x
|
Rasa X before 0.42.4 allows Directory Traversal during archive extraction. In the functionality that allows a user to load a trained model archive, an attacker has arbitrary write capability within specific directories via a crafted archive file. |
2021-10-22 |
not yet calculated |
CVE-2021-42556
MISC
CONFIRM |
revisor — video_management_system
|
Revisor Video Management System (VMS) before 2.0.0 has a directory traversal vulnerability. Successful exploitation could allow an attacker to traverse the file system to access files or directories that are outside of restricted directory on the remote server. This could lead to the disclosure of sensitive data on the vulnerable server. |
2021-10-19 |
not yet calculated |
CVE-2021-42261
MISC
MISC |
seedms — content_management_system
|
SeedDMS Content Management System v6.0.7 contains a persistent cross-site scripting (XSS) vulnerability in the component AddEvent.php via the name and comment parameters. |
2021-10-22 |
not yet calculated |
CVE-2020-23048
MISC |
shell-quote — shell-quote
|
The shell-quote package before 1.7.3 for Node.js allows command injection. An attacker can inject unescaped shell metacharacters through a regex designed to support Windows drive letters. If the output of this package is passed to a real shell as a quoted argument to a command with exec(), an attacker can inject arbitrary commands. This is because the Windows drive letter regex character class is {A-z] instead of the correct {A-Za-z]. Several shell metacharacters exist in the space between capital letter Z and lower case letter a, such as the backtick character. |
2021-10-21 |
not yet calculated |
CVE-2021-42740
CONFIRM
MISC
CONFIRM |
showdoc — showdoc
|
ShowDoc 2.8.3 ihas a file upload vulnerability, where attackers can use the vulnerability to obtain server permissions. |
2021-10-22 |
not yet calculated |
CVE-2021-41745
MISC
MISC |
sky_file — ftp_server
|
An issue in the FTP server of Sky File v2.1.0 allows attackers to perform directory traversal via `/null//` path commands. |
2021-10-22 |
not yet calculated |
CVE-2020-36488
MISC |
sky_file — sky_file
|
Sky File v2.1.0 contains a directory traversal vulnerability in the FTP server which allows attackers to access sensitive data and files via ‘null’ path commands. |
2021-10-22 |
not yet calculated |
CVE-2020-23040
MISC |
snapdragon — auto
|
Improper handling of sensor HAL structure in absence of sensor can lead to use after free in Snapdragon Auto |
2021-10-20 |
not yet calculated |
CVE-2021-30315
CONFIRM |
| snapdragon — multiple_products |
Improper validation of kernel buffer address while copying information back to user buffer can lead to kernel memory information exposure to user space in Snapdragon Auto, Snapdragon Compute, Snapdragon Consumer IOT, Snapdragon Industrial IOT, Snapdragon Mobile, Snapdragon Voice & Music, Snapdragon Wearables |
2021-10-20 |
not yet calculated |
CVE-2021-1969
CONFIRM |
| snapdragon — multiple_products |
Possible memory corruption due to lack of bound check of input index in Snapdragon Auto, Snapdragon Compute, Snapdragon Connectivity, Snapdragon Consumer IOT, Snapdragon Industrial IOT, Snapdragon IoT, Snapdragon Mobile, Snapdragon Voice & Music, Snapdragon Wearables |
2021-10-20 |
not yet calculated |
CVE-2021-1959
CONFIRM |
| snapdragon — multiple_products |
Possible buffer over read due to lack of data length check in QVR Service configuration in Snapdragon Auto, Snapdragon Compute, Snapdragon Connectivity, Snapdragon Consumer IOT, Snapdragon Industrial IOT, Snapdragon Wearables |
2021-10-20 |
not yet calculated |
CVE-2021-1985
CONFIRM |
| snapdragon — multiple_products |
Possible stack buffer overflow due to lack of check on the maximum number of post NAN discovery attributes while processing a NAN Match event in Snapdragon Auto, Snapdragon Compute, Snapdragon Connectivity, Snapdragon Consumer IOT, Snapdragon Industrial IOT, Snapdragon Mobile, Snapdragon Voice & Music, Snapdragon Wearables |
2021-10-20 |
not yet calculated |
CVE-2021-1967
CONFIRM |
| snapdragon — multiple_products |
Possible buffer overflow due to lack of length check of source and destination buffer before copying in Snapdragon Auto, Snapdragon Compute, Snapdragon Consumer IOT, Snapdragon Industrial IOT, Snapdragon Mobile, Snapdragon Voice & Music |
2021-10-20 |
not yet calculated |
CVE-2021-1966
CONFIRM |
| snapdragon — multiple_products |
Possible buffer over read due to lack of length check while parsing beacon IE response in Snapdragon Auto, Snapdragon Compute, Snapdragon Connectivity, Snapdragon Consumer Electronics Connectivity, Snapdragon Consumer IOT, Snapdragon Industrial IOT, Snapdragon Mobile, Snapdragon Voice & Music, Snapdragon Wired Infrastructure and Networking |
2021-10-20 |
not yet calculated |
CVE-2021-1980
CONFIRM |
| snapdragon — multiple_products |
Null pointer dereference can occur due to lack of null check for user provided input in Snapdragon Auto, Snapdragon Compute, Snapdragon Connectivity, Snapdragon Consumer IOT, Snapdragon Industrial IOT, Snapdragon Wearables |
2021-10-20 |
not yet calculated |
CVE-2021-1936
CONFIRM |
| snapdragon — multiple_products |
Possible out of bound memory access due to improper boundary check while creating HSYNC fence in Snapdragon Auto, Snapdragon Connectivity, Snapdragon Consumer IOT, Snapdragon Industrial IOT, Snapdragon Mobile, Snapdragon Wearables |
2021-10-20 |
not yet calculated |
CVE-2021-30316
CONFIRM |
| snapdragon — multiple_products |
Possible buffer out of bound read can occur due to improper validation of TBTT count and length while parsing the beacon response in Snapdragon Compute, Snapdragon Connectivity, Snapdragon Consumer Electronics Connectivity |
2021-10-20 |
not yet calculated |
CVE-2021-30304
CONFIRM |
| snapdragon — multiple_products |
Improper authentication of sub-frames of a multicast AMSDU frame can lead to information disclosure in Snapdragon Auto, Snapdragon Compute, Snapdragon Connectivity, Snapdragon Consumer IOT, Snapdragon Industrial IOT, Snapdragon Mobile, Snapdragon Voice & Music, Snapdragon Wearables, Snapdragon Wired Infrastructure and Networking |
2021-10-20 |
not yet calculated |
CVE-2021-30312
CONFIRM |
| snapdragon — multiple_products |
Possible stack overflow due to improper length check of TLV while copying the TLV to a local stack variable in Snapdragon Auto, Snapdragon Compute, Snapdragon Connectivity, Snapdragon Consumer Electronics Connectivity, Snapdragon Consumer IOT, Snapdragon Industrial IOT, Snapdragon IoT, Snapdragon Mobile, Snapdragon Voice & Music, Snapdragon Wired Infrastructure and Networking |
2021-10-20 |
not yet calculated |
CVE-2021-30288
CONFIRM |
snapdragon — multiple_products
|
Improper access control in trusted application environment can cause unauthorized access to CDSP or ADSP VM memory with either privilege in Snapdragon Auto, Snapdragon Compute, Snapdragon Connectivity, Snapdragon Consumer IOT, Snapdragon Industrial IOT, Snapdragon Mobile, Snapdragon Wired Infrastructure and Networking |
2021-10-20 |
not yet calculated |
CVE-2021-1932
CONFIRM |
snapdragon — multiple_products
|
Null pointer dereference can occur due to memory allocation failure in DIAG in Snapdragon Auto, Snapdragon Compute, Snapdragon Connectivity, Snapdragon Industrial IOT, Snapdragon Wearables |
2021-10-20 |
not yet calculated |
CVE-2021-1917
CONFIRM |
snapdragon — multiple_products
|
Possible integer overflow due to improper length check while updating grace period and count record in Snapdragon Auto, Snapdragon Compute, Snapdragon Connectivity, Snapdragon Industrial IOT, Snapdragon Mobile, Snapdragon Wired Infrastructure and Networking |
2021-10-20 |
not yet calculated |
CVE-2021-1913
CONFIRM |
snapdragon — multiple_products
|
Possible buffer overflow due to Improper validation of received CF-ACK and CF-Poll data frames in Snapdragon Auto, Snapdragon Connectivity, Snapdragon Consumer Electronics Connectivity, Snapdragon Consumer IOT, Snapdragon Industrial IOT, Snapdragon IoT, Snapdragon Mobile, Snapdragon Voice & Music |
2021-10-20 |
not yet calculated |
CVE-2021-30310
CONFIRM |
snapdragon — multiple_products
|
Possible buffer over read due to improper buffer allocation for file length passed from user space in Snapdragon Auto, Snapdragon Connectivity, Snapdragon Industrial IOT, Snapdragon Mobile |
2021-10-20 |
not yet calculated |
CVE-2021-30306
CONFIRM |
snapdragon — multiple_products
|
Improper validation of kernel buffer address while copying information back to user buffer can lead to kernel memory information exposure to user space in Snapdragon Auto, Snapdragon Compute, Snapdragon Consumer IOT, Snapdragon Industrial IOT, Snapdragon Mobile, Snapdragon Voice & Music, Snapdragon Wearables |
2021-10-20 |
not yet calculated |
CVE-2021-1968
CONFIRM |
snapdragon — multiple_products
|
Possible stack overflow due to improper validation of camera name length before copying the name in VR Service in Snapdragon Compute, Snapdragon Connectivity, Snapdragon Consumer IOT, Snapdragon Industrial IOT |
2021-10-20 |
not yet calculated |
CVE-2021-30256
CONFIRM |
snapdragon — multiple_products
|
Possible buffer over read due to improper validation of frame length while processing AEAD decryption during ASSOC response in Snapdragon Auto, Snapdragon Compute, Snapdragon Connectivity, Snapdragon Consumer Electronics Connectivity, Snapdragon Consumer IOT, Snapdragon Industrial IOT, Snapdragon IoT, Snapdragon Mobile, Snapdragon Voice & Music |
2021-10-20 |
not yet calculated |
CVE-2021-1977
CONFIRM |
snapdragon — multiple_products
|
Possible out of bound access due to lack of validation of page offset before page is inserted in Snapdragon Auto, Snapdragon Connectivity, Snapdragon Industrial IOT, Snapdragon Mobile |
2021-10-20 |
not yet calculated |
CVE-2021-30305
CONFIRM |
snapdragon — multiple_products
|
Possible buffer overflow due to improper validation of index value while processing the plugin block in Snapdragon Auto, Snapdragon Compute, Snapdragon Connectivity, Snapdragon Consumer IOT, Snapdragon Industrial IOT, Snapdragon Wearables |
2021-10-20 |
not yet calculated |
CVE-2021-1984
CONFIRM |
snapdragon — multiple_products
|
Improper authentication of EAP WAPI EAPOL frames from unauthenticated user can lead to information disclosure in Snapdragon Compute, Snapdragon Connectivity, Snapdragon Consumer Electronics Connectivity, Snapdragon Consumer IOT, Snapdragon Industrial IOT, Snapdragon Mobile, Snapdragon Wired Infrastructure and Networking |
2021-10-20 |
not yet calculated |
CVE-2021-30302
CONFIRM |
snapdragon — multiple_products
|
Possible out of bound read due to improper validation of packet length while handling data transfer in VR service in Snapdragon Auto, Snapdragon Compute, Snapdragon Connectivity, Snapdragon Consumer IOT, Snapdragon Industrial IOT, Snapdragon Wearables |
2021-10-20 |
not yet calculated |
CVE-2021-30297
CONFIRM |
snapdragon — multiple_products
|
Possible memory corruption due to lack of validation of client data used for memory allocation in Snapdragon Auto, Snapdragon Compute, Snapdragon Connectivity, Snapdragon Consumer IOT, Snapdragon Industrial IOT, Snapdragon Wearables |
2021-10-20 |
not yet calculated |
CVE-2021-30292
CONFIRM |
snapdragon — multiple_products
|
Possible memory corruption due to lack of validation of client data used for memory allocation in Snapdragon Auto, Snapdragon Compute, Snapdragon Connectivity, Snapdragon Consumer IOT, Snapdragon Industrial IOT, Snapdragon Wearables |
2021-10-20 |
not yet calculated |
CVE-2021-30291
CONFIRM |
snapdragon — multiple_products
|
Possible integer overflow due to improper check of batch count value while sanitizer is enabled in Snapdragon Auto, Snapdragon Compute, Snapdragon Connectivity, Snapdragon Consumer IOT, Snapdragon Industrial IOT, Snapdragon Voice & Music, Snapdragon Wearables |
2021-10-20 |
not yet calculated |
CVE-2021-1949
CONFIRM |
snapdragon — multiple_products
|
Possible buffer overflow due to improper size calculation of payload received in VR service in Snapdragon Auto, Snapdragon Compute, Snapdragon Connectivity, Snapdragon Consumer IOT, Snapdragon Industrial IOT, Snapdragon Wearables |
2021-10-20 |
not yet calculated |
CVE-2021-30258
CONFIRM |
snapdragon — multiple_products
|
Accepting AMSDU frames with mismatched destination and source address can lead to information disclosure in Snapdragon Auto, Snapdragon Connectivity, Snapdragon Consumer Electronics Connectivity, Snapdragon Consumer IOT, Snapdragon Industrial IOT, Snapdragon IoT, Snapdragon Mobile, Snapdragon Voice & Music, Snapdragon Wired Infrastructure and Networking |
2021-10-20 |
not yet calculated |
CVE-2020-11303
CONFIRM |
snapdragon — multiple_products
|
Possible out of bound read or write in VR service due to lack of validation of DSP selection values in Snapdragon Compute, Snapdragon Connectivity, Snapdragon Consumer IOT, Snapdragon Industrial IOT |
2021-10-20 |
not yet calculated |
CVE-2021-30257
CONFIRM |
snapdragon — multiple_products
|
Possible buffer overflow due to improper handling of negative data length while processing write request in VR service in Snapdragon Auto, Snapdragon Compute, Snapdragon Connectivity, Snapdragon Consumer IOT, Snapdragon Industrial IOT, Snapdragon Wearables |
2021-10-20 |
not yet calculated |
CVE-2021-1983
CONFIRM |
snapdragon — qnap_devices
|
A command injection vulnerability has been reported to affect QNAP device running Media Streaming add-on. If exploited, this vulnerability allow remote attackers to run arbitrary commands. We have already fixed this vulnerability in the following versions of Media Streaming add-on: QTS 5.0.0: Media Streaming add-on 500.0.0.3 ( 2021/08/20 ) and later QTS 4.5.4: Media Streaming add-on 500.0.0.3 ( 2021/08/20 ) and later QTS 4.3.6: Media Streaming add-on 430.1.8.12 ( 2021/08/20 ) and later QTS 4.3.3: Media Streaming add-on 430.1.8.12 ( 2021/09/29 ) and later QuTS-Hero 5.0.0: Media Streaming add-on 500.0.0.3 ( 2021/08/20 ) and later |
2021-10-22 |
not yet calculated |
CVE-2021-34362
MISC |
solarwinds — database_performance_analyzer
|
This vulnerability occurred due to missing input sanitization for one of the output fields that is extracted from headers on specific section of page causing a reflective cross site scripting attack. An attacker would need to perform a Man in the Middle attack in order to change header for a remote victim. |
2021-10-21 |
not yet calculated |
CVE-2021-35228
MISC
MISC |
stb — stb_image
|
An issue was discovered in stb stb_image.h 1.33 through 2.27. The HDR loader parsed truncated end-of-file RLE scanlines as an infinite sequence of zero-length runs. An attacker could potentially have caused denial of service in applications using stb_image by submitting crafted HDR files. |
2021-10-21 |
not yet calculated |
CVE-2021-42715
MISC
MISC |
stb — stb_image
|
An issue was discovered in stb stb_image.h 2.27. The PNM loader incorrectly interpreted 16-bit PGM files as 8-bit when converting to RGBA, leading to a buffer overflow when later reinterpreting the result as a 16-bit buffer. An attacker could potentially have crashed a service using stb_image, or read up to 1024 bytes of non-consecutive heap data without control over the read location. |
2021-10-21 |
not yet calculated |
CVE-2021-42716
MISC
MISC
MISC |
| sugarcrm — sugarcrm |
Multiple cross-site scripting (XSS) vulnerabilities in the Support module of SugarCRM v6.5.18 allows attackers to execute arbitrary web scripts or HTML via crafted payloads entered into the primary address state or alternate address state input fields. |
2021-10-22 |
not yet calculated |
CVE-2020-36501
MISC |
sugarcrm — sugarcrm
|
Multiple cross-site scripting (XSS) vulnerabilities in the Sales module of SugarCRM v6.5.18 allows attackers to execute arbitrary web scripts or HTML via crafted payloads entered into the primary address state or alternate address state input fields. |
2021-10-22 |
not yet calculated |
CVE-2020-28956
MISC |
sugarcrm — sugarcrm
|
SugarCRM v6.5.18 was discovered to contain a cross-site scripting (XSS) vulnerability in the Create Employee module. This vulnerability allows attackers to execute arbitrary web scripts or HTML via a crafted payload in the First Name or Last Name input fields. |
2021-10-22 |
not yet calculated |
CVE-2020-28955
MISC |
suitecrm — suitecrm
|
SuiteCRM before 7.11.19 allows remote code execution via the system settings Log File Name setting. In certain circumstances involving admin account takeover, logger_file_name can refer to an attacker-controlled PHP file under the web root, because only the all-lowercase PHP file extensions were blocked. NOTE: this issue exists because of an incomplete fix for CVE-2020-28328. |
2021-10-22 |
not yet calculated |
CVE-2021-42840
MISC
MISC
MISC
MISC |
sulu — sulu
|
Sulu is an open-source PHP content management system based on the Symfony framework. In versions before 1.6.43 are subject to stored cross site scripting attacks. HTML input into Tag names is not properly sanitized. Only admin users are allowed to create tags. Users are advised to upgrade. |
2021-10-21 |
not yet calculated |
CVE-2021-41169
CONFIRM
MISC |
sundown — sundown
|
Snudown is a reddit-specific fork of the Sundown Markdown parser used by GitHub, with Python integration added. In affected versions snudown was found to be vulnerable to denial of service attacks to its reference table implementation. References written in markdown ` [reference_name]: https://www.example.com` are inserted into a hash table which was found to have a weak hash function, meaning that an attacker can reliably generate a large number of collisions for it. This makes the hash table vulnerable to a hash-collision DoS attack, a type of algorithmic complexity attack. Further the hash table allowed for duplicate entries resulting in long retrieval times. Proofs of concept and further discussion of the hash collision issue are discussed on the snudown GHSA(https://github.com/reddit/snudown/security/advisories/GHSA-6gvv-9q92-w5f6). Users are advised to update to version 1.7.0. |
2021-10-21 |
not yet calculated |
CVE-2021-41168
CONFIRM
MISC |
swift — file_transfer_mobile
|
Swift File Transfer Mobile v1.1.2 and below was discovered to contain a cross-site scripting (XSS) vulnerability via the ‘path’ parameter of the ‘list’ and ‘download’ exception-handling. |
2021-10-22 |
not yet calculated |
CVE-2020-36486
MISC |
swift — file_transfer_mobile
|
Swift File Transfer Mobile v1.1.2 and below was discovered to contain an information disclosure vulnerability in the path parameter. This vulnerability is exploited via an error caused by including non-existent path environment variables. |
2021-10-22 |
not yet calculated |
CVE-2020-23038
MISC |
swift — file_transfer_mobile
|
Swift File Transfer Mobile v1.1.2 was discovered to contain a cross-site scripting (XSS) vulnerability via the devicename parameter which allows attackers to execute arbitrary web scripts or HTML via a crafted payload entered as the device name itself. |
2021-10-22 |
not yet calculated |
CVE-2020-36502
MISC |
synchronet — bbs
|
An issue was discovered in function scanallsubs in src/sbbs3/scansubs.cpp in Synchronet BBS, which may allow attackers to view sensitive information due to an uninitialized value. |
2021-10-19 |
not yet calculated |
CVE-2021-36512
MISC
MISC |
tao — open_source_assessment_platform
|
TAO Open Source Assessment Platform v3.3.0 RC02 was discovered to contain a cross-site scripting (XSS) vulnerability in the content parameter of the Rubric Block (Add) module. This vulnerability allows attackers to execute arbitrary web scripts or HTML via a crafted payload in the rubric name value. |
2021-10-22 |
not yet calculated |
CVE-2020-36499
MISC |
tao — open_source_assessment_platform
|
TAO Open Source Assessment Platform v3.3.0 RC02 was discovered to contain a HTML injection vulnerability in the userFirstName parameter of the user account input field. This vulnerability allows attackers to execute phishing attacks, external redirects, and arbitrary code. |
2021-10-22 |
not yet calculated |
CVE-2020-23050
MISC |
| tough — tough |
Tough provides a set of Rust libraries and tools for using and generating the update framework (TUF) repositories. The tough library, prior to 0.12.0, does not properly sanitize delegated role names when caching a repository, or when loading a repository from the filesystem. When the repository is cached or loaded, files ending with the .json extension could be overwritten with role metadata anywhere on the system. A fix is available in version 0.12.0. No workarounds to this issue are known. |
2021-10-19 |
not yet calculated |
CVE-2021-41150
CONFIRM
MISC
MISC |
tough — tough
|
Tough provides a set of Rust libraries and tools for using and generating the update framework (TUF) repositories. The tough library, prior to 0.12.0, does not properly sanitize target names when caching a repository, or when saving specific targets to an output directory. When targets are cached or saved, files could be overwritten with arbitrary content anywhere on the system. A fix is available in version 0.12.0. No workarounds to this issue are known. |
2021-10-19 |
not yet calculated |
CVE-2021-41149
CONFIRM
MISC |
tran_tu — sir_sender
|
Tran Tu Air Sender v1.0.2 was discovered to contain an arbitrary file upload vulnerability in the upload module. This vulnerability allows attackers to execute arbitrary code via a crafted file. |
2021-10-22 |
not yet calculated |
CVE-2020-23043
MISC |
trane — building_automation_controllers
|
The affected product is vulnerable to directory traversal due to mishandling of provided backup folder structure. |
2021-10-22 |
not yet calculated |
CVE-2021-42542
CONFIRM |
trane — building_automation_controllers
|
The affected product is vulnerable to a unsanitized extract folder for system configuration. A low-privileged user can leverage this logic to overwrite the settings and other key functionality. |
2021-10-22 |
not yet calculated |
CVE-2021-42540
CONFIRM |
trane — building_automation_controllers
|
The affected product is vulnerable to a missing permission validation on system backup restore, which could lead to account take over and unapproved settings change. |
2021-10-22 |
not yet calculated |
CVE-2021-42539
CONFIRM |
trane — building_automation_controllers
|
The affected product is vulnerable to a parameter injection via passphrase, which enables the attacker to supply uncontrolled input. |
2021-10-22 |
not yet calculated |
CVE-2021-42538
CONFIRM |
trane — building_automation_controllers
|
The affected product is vulnerable to a disclosure of peer username and password by allowing all users access to read global variables. |
2021-10-22 |
not yet calculated |
CVE-2021-42536
CONFIRM |
trane — building_automation_controllers
|
The affected product’s web application does not properly neutralize the input during webpage generation, which could allow an attacker to inject code in the input forms. |
2021-10-22 |
not yet calculated |
CVE-2021-42534
CONFIRM |
trend_micro — apex_one_and_worry-free_business_security
|
A null pointer vulnerability in Trend Micro Apex One and Worry-Free Business Security 10.0 SP1 could allow an attacker to crash the CGI program on affected installations. |
2021-10-21 |
not yet calculated |
CVE-2021-23139
MISC
MISC |
| trend_mirco — apex_one |
An incorrect permission assignment vulnerability in Trend Micro Apex One and Apex One as a Service could allow a local attacker to load a DLL with escalated privileges on affected installations. Please note: an attacker must first obtain the ability to execute low-privileged code on the target system in order to exploit this vulnerability. |
2021-10-21 |
not yet calculated |
CVE-2021-42011
MISC
MISC |
| trend_mirco — apex_one |
An uncontrolled search path element vulnerabilities in Trend Micro Apex One and Apex One as a Service agents could allow a local attacker to escalate privileges on affected installations. An attacker must first obtain the ability to execute low-privileged code on the target system in order to exploit this vulnerability. |
2021-10-21 |
not yet calculated |
CVE-2021-42102
MISC
MISC |
| trend_mirco — apex_one |
Unnecessary privilege vulnerabilities in Trend Micro Apex One, Apex One as a Service, Worry-Free Business Security 10.0 SP1 and Worry-Free Business Security Services could allow a local attacker to escalate privileges on affected installations. Please note: an attacker must first obtain the ability to execute low-privileged code on the target system in order to exploit this vulnerability. This vulnerability is similar to but not identical to CVE-2021-42105, 42106 and 42107. |
2021-10-21 |
not yet calculated |
CVE-2021-42104
MISC
MISC
MISC |
trend_mirco — apex_one
|
Unnecessary privilege vulnerabilities in Trend Micro Apex One, Apex One as a Service, Worry-Free Business Security 10.0 SP1 and Worry-Free Business Security Services could allow a local attacker to escalate privileges on affected installations. Please note: an attacker must first obtain the ability to execute low-privileged code on the target system in order to exploit this vulnerability. This vulnerability is similar to but not identical to CVE-2021-42104, 42105 and 42107. |
2021-10-21 |
not yet calculated |
CVE-2021-42106
MISC
MISC
MISC |
trend_mirco — apex_one
|
Unnecessary privilege vulnerabilities in the Web Console of Trend Micro Apex One, Apex One as a Service and Worry-Free Business Security 10.0 SP1 could allow a local attacker to escalate privileges on affected installations. Please note: an attacker must first obtain the ability to execute low-privileged code on the target system in order to exploit this vulnerability. |
2021-10-21 |
not yet calculated |
CVE-2021-42108
MISC
MISC
MISC |
trend_mirco — apex_one
|
Unnecessary privilege vulnerabilities in Trend Micro Apex One, Apex One as a Service, Worry-Free Business Security 10.0 SP1 and Worry-Free Business Security Services could allow a local attacker to escalate privileges on affected installations. Please note: an attacker must first obtain the ability to execute low-privileged code on the target system in order to exploit this vulnerability. This vulnerability is similar to but not identical to CVE-2021-42104, 42105 and 42106. |
2021-10-21 |
not yet calculated |
CVE-2021-42107
MISC
MISC
MISC |
trend_mirco — apex_one
|
Unnecessary privilege vulnerabilities in Trend Micro Apex One, Apex One as a Service, Worry-Free Business Security 10.0 SP1 and Worry-Free Business Security Services could allow a local attacker to escalate privileges on affected installations. Please note: an attacker must first obtain the ability to execute low-privileged code on the target system in order to exploit this vulnerability. This vulnerability is similar to but not identical to CVE-2021-42104, 42106 and 42107. |
2021-10-21 |
not yet calculated |
CVE-2021-42105
MISC
MISC
MISC |
trend_mirco — apex_one
|
A stack-based buffer overflow vulnerability in Trend Micro Apex One, Apex One as a Service and Worry-Free Business Security 10.0 SP1 could allow a local attacker to escalate privileges on affected installations. Please note: an attacker must first obtain the ability to execute low-privileged code on the target system in order to exploit this vulnerability. |
2021-10-21 |
not yet calculated |
CVE-2021-42012
MISC
MISC
MISC |
trend_mirco — apex_one
|
An uncontrolled search path element vulnerabilities in Trend Micro Apex One and Apex One as a Service could allow a local attacker to escalate privileges on affected installations. An attacker must first obtain the ability to execute low-privileged code on the target system in order to exploit this vulnerability. This vulnerability is similar but not identical to CVE-2021-42103. |
2021-10-21 |
not yet calculated |
CVE-2021-42101
MISC
MISC |
trend_mirco — apex_one
|
An uncontrolled search path element vulnerabilities in Trend Micro Apex One and Apex One as a Service could allow a local attacker to escalate privileges on affected installations. An attacker must first obtain the ability to execute low-privileged code on the target system in order to exploit this vulnerability. This vulnerability is similar but not identical to CVE-2021-42101. |
2021-10-21 |
not yet calculated |
CVE-2021-42103
MISC
MISC |
ufida — plm
|
All versions of yongyou PLM are affected by a command injection issue. UFIDA PLM (Product Life Cycle Management) is a strategic management method. It applies a series of enterprise application systems to support the entire process from conceptual design to the end of product life, and the collaborative creation, distribution, application and management of product information across organizations. Yonyou PLM uses jboss by default, and you can access the management control background without authorization An attacker can use this vulnerability to gain server permissions. |
2021-10-22 |
not yet calculated |
CVE-2021-41744
MISC |
| vmware — vrealize |
Releases prior to VMware vRealize Operations Tenant App 8.6 contain an Information Disclosure Vulnerability. |
2021-10-21 |
not yet calculated |
CVE-2021-22034
MISC |
webkitgtk — bubblewraplauncher
|
BubblewrapLauncher.cpp in WebKitGTK and WPE WebKit before 2.34.1 allows a limited sandbox bypass that allows a sandboxed process to trick host processes into thinking the sandboxed process is not confined by the sandbox, by abusing VFS syscalls that manipulate its filesystem namespace. The impact is limited to host services that create UNIX sockets that WebKit mounts inside its sandbox, and the sandboxed process remains otherwise confined. NOTE: this is similar to CVE-2021-41133. |
2021-10-20 |
not yet calculated |
CVE-2021-42762
MISC
MISC |
| wordpress — wordpress |
The Catch Themes Demo Import WordPress plugin is vulnerable to arbitrary file uploads via the import functionality found in the ~/inc/CatchThemesDemoImport.php file, in versions up to and including 1.7, due to insufficient file type validation. This makes it possible for an attacker with administrative privileges to upload malicious files that can be used to achieve remote code execution. |
2021-10-21 |
not yet calculated |
CVE-2021-39352
MISC
MISC
MISC |
| wordpress — wordpress |
The Simple Job Board WordPress plugin is vulnerable to Stored Cross-Site Scripting due to insufficient escaping on the $job_board_privacy_policy_label variable echo’d out via the ~/admin/settings/class-simple-job-board-settings-privacy.php file which allowed attackers with administrative user access to inject arbitrary web scripts, in versions up to and including 2.9.4. This affects multi-site installations where unfiltered_html is disabled for administrators, and sites where unfiltered_html is disabled. |
2021-10-21 |
not yet calculated |
CVE-2021-39328
MISC
MISC
MISC |
| wordpress — wordpress |
Version 3.3.23 of the Sassy Social Share WordPress plugin is vulnerable to PHP Object Injection via the wp_ajax_heateor_sss_import_config AJAX action due to deserialization of unvalidated user supplied inputs via the import_config function found in the ~/admin/class-sassy-social-share-admin.php file. This can be exploited by underprivileged authenticated users due to a missing capability check on the import_config function. |
2021-10-21 |
not yet calculated |
CVE-2021-39321
MISC
MISC
MISC |
wordpress — wordpress
|
The Easy Digital Downloads WordPress plugin is vulnerable to Reflected Cross-Site Scripting via the $start_date and $end_date parameters found in the ~/includes/admin/payments/class-payments-table.php file which allows attackers to inject arbitrary web scripts, in versions up to and including 2.11.2. |
2021-10-21 |
not yet calculated |
CVE-2021-39354
MISC
MISC
MISC |
wordpress — wordpress
|
Reflected Cross-Site Scripting (XSS) vulnerability in WordPress Ivory Search plugin (versions <= 4.6.6). Vulnerable parameter: &post. |
2021-10-21 |
not yet calculated |
CVE-2021-36869
CONFIRM
MISC |
wordpress — wordpress
|
The Content Staging WordPress plugin is vulnerable to Stored Cross-Site Scripting due to insufficient input validation and escaping via several parameters that are echo’d out via the ~/templates/settings.php file which allowed attackers with administrative user access to inject arbitrary web scripts, in versions up to and including 2.0.1. This affects multi-site installations where unfiltered_html is disabled for administrators, and sites where unfiltered_html is disabled. |
2021-10-21 |
not yet calculated |
CVE-2021-39356
MISC
MISC
MISC |
wordpress — wordpress
|
The Leaky Paywall WordPress plugin is vulnerable to Stored Cross-Site Scripting due to insufficient input validation and sanitization via the ~/class.php file which allowed attackers with administrative user access to inject arbitrary web scripts, in versions up to and including 4.16.5. This affects multi-site installations where unfiltered_html is disabled for administrators, and sites where unfiltered_html is disabled. |
2021-10-21 |
not yet calculated |
CVE-2021-39357
MISC
MISC
MISC |
wordpress — wordpress
|
The LearnPress WordPress plugin is vulnerable to Stored Cross-Site Scripting due to insufficient escaping on the $custom_profile parameter found in the ~/inc/admin/views/backend-user-profile.php file which allowed attackers with administrative user access to inject arbitrary web scripts, in versions up to and including 4.1.3.1. This affects multi-site installations where unfiltered_html is disabled for administrators, and sites where unfiltered_html is disabled. Please note that this is seperate from CVE-2021-24702. |
2021-10-21 |
not yet calculated |
CVE-2021-39348
MISC
MISC
MISC |
wp — mailster
|
WP Mailster 1.6.18.0 allows XSS when a victim opens a mail server’s details in the mst_servers page, for a crafted server_host, server_name, or connection_parameter parameter. |
2021-10-21 |
not yet calculated |
CVE-2021-28975
MISC
MISC |
zephyr — zephyr
|
Truncated L2CAP K-frame causes assertion failure. Zephyr versions >= 2.4.0, >= v.2.50 contain Improper Handling of Length Parameter Inconsistency (CWE-130), Reachable Assertion (CWE-617). For more information, see https://github.com/zephyrproject-rtos/zephyr/security/advisories/GHSA-fx88-6c29-vrp3 |
2021-10-19 |
not yet calculated |
CVE-2021-3454
MISC |
zephyr — zephyr
|
Disconnecting L2CAP channel right after invalid ATT request leads freeze. Zephyr versions >= 2.4.0, >= 2.5.0 contain Use After Free (CWE-416). For more information, see https://github.com/zephyrproject-rtos/zephyr/security/advisories/GHSA-7g38-3x9v-v7vp |
2021-10-19 |
not yet calculated |
CVE-2021-3455
MISC |
zoho_manageengine — applications_manager
|
An SSRF issue was discovered in Zoho ManageEngine Applications Manager build 15200. |
2021-10-21 |
not yet calculated |
CVE-2021-35512
MISC
MISC
MISC |
| zte — mf971r_product |
ZTE MF971R product has two stack-based buffer overflow vulnerabilities. An attacker could exploit the vulnerabilities to execute arbitrary code. |
2021-10-20 |
not yet calculated |
CVE-2021-21748
MISC |
zte — mf971r_product
|
ZTE MF971R product has a configuration file control vulnerability. An attacker could use this vulnerability to modify the configuration parameters of the device, causing some security functions of the device to be disabled. |
2021-10-20 |
not yet calculated |
CVE-2021-21744
MISC |
zte — mf971r_product
|
ZTE MF971R product has a CRLF injection vulnerability. An attacker could exploit the vulnerability to modify the HTTP response header information through a specially crafted HTTP request. |
2021-10-20 |
not yet calculated |
CVE-2021-21743
MISC |
zte — mf971r_product
|
ZTE MF971R product has a Referer authentication bypass vulnerability. Without CSRF verification, an attackercould use this vulnerability to perform illegal authorization operations by sending a request to the user to click. |
2021-10-20 |
not yet calculated |
CVE-2021-21745
MISC |
zte — mf971r_product
|
ZTE MF971R product has two stack-based buffer overflow vulnerabilities. An attacker could exploit the vulnerabilities to execute arbitrary code. |
2021-10-20 |
not yet calculated |
CVE-2021-21749
MISC |
zte — mf971r_product
|
ZTE MF971R product has reflective XSS vulnerability. An attacker could use the vulnerability to obtain cookie information. |
2021-10-20 |
not yet calculated |
CVE-2021-21747
MISC |
zte — mf971r_product
|
ZTE MF971R product has reflective XSS vulnerability. An attacker could use the vulnerability to obtain cookie information. |
2021-10-20 |
not yet calculated |
CVE-2021-21746
MISC |

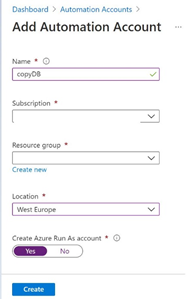
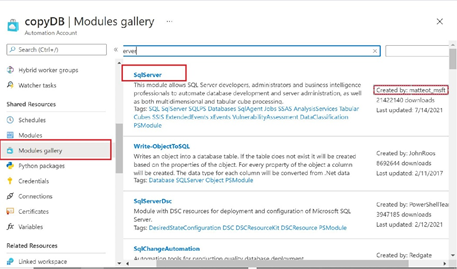
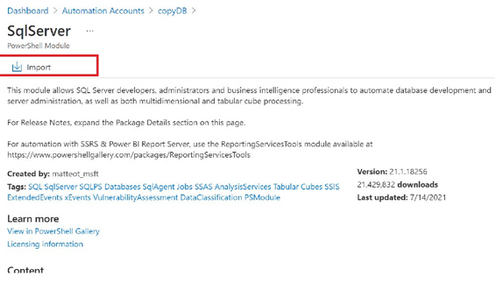
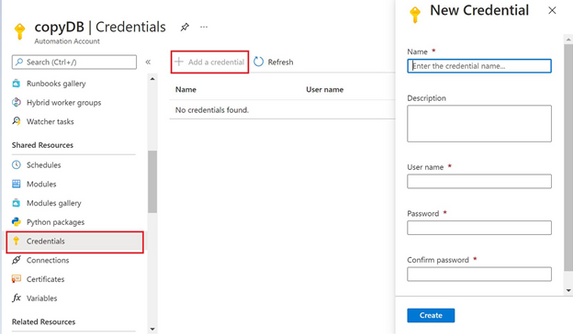
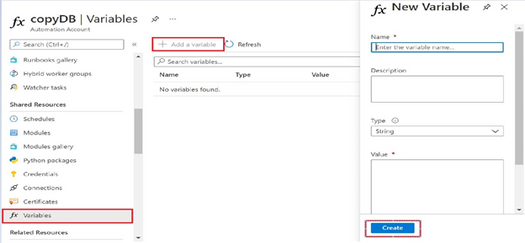
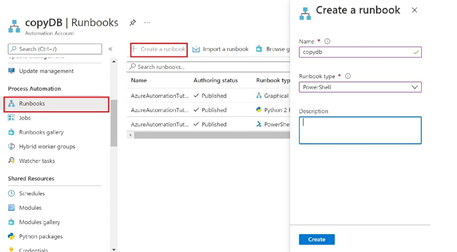
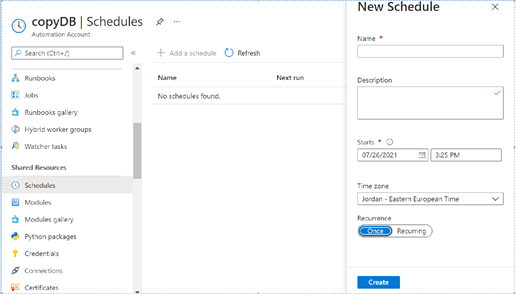
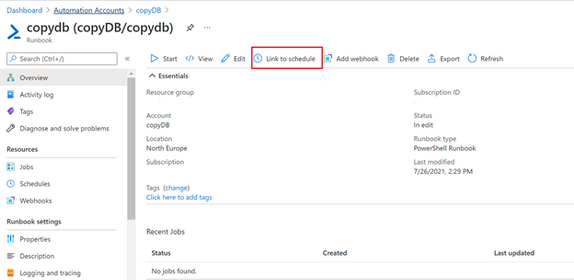
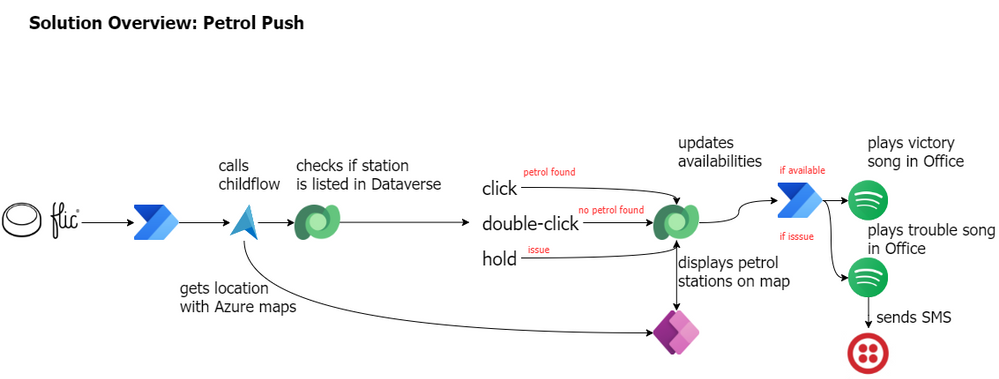

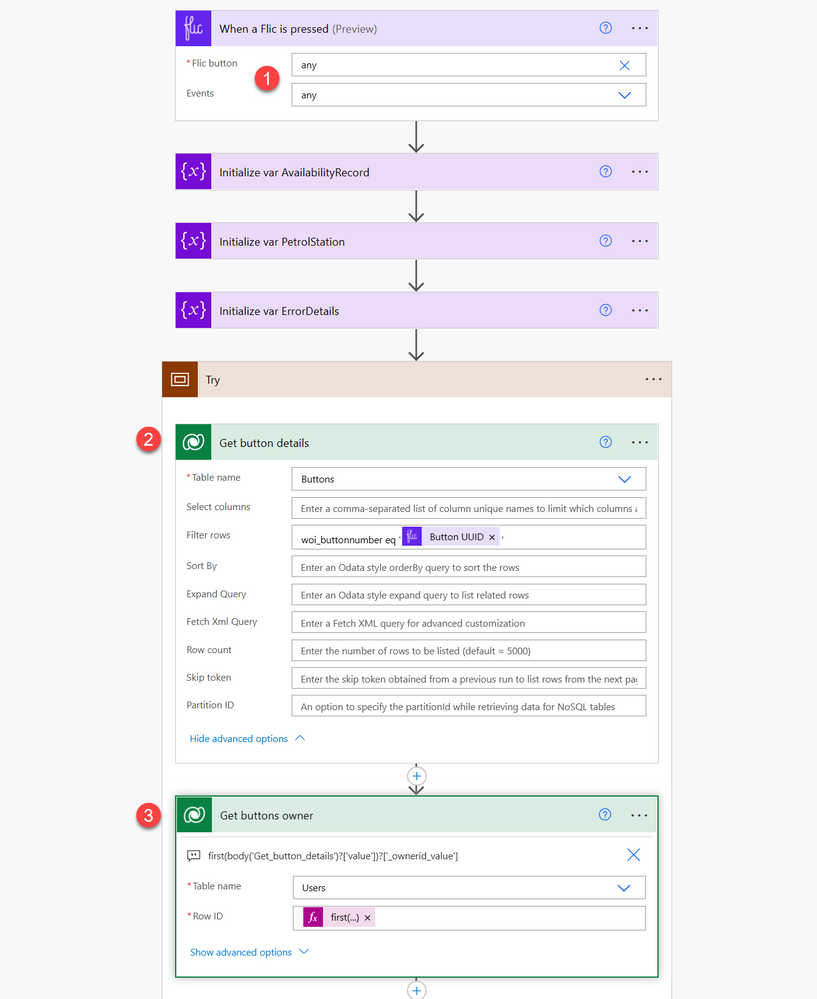
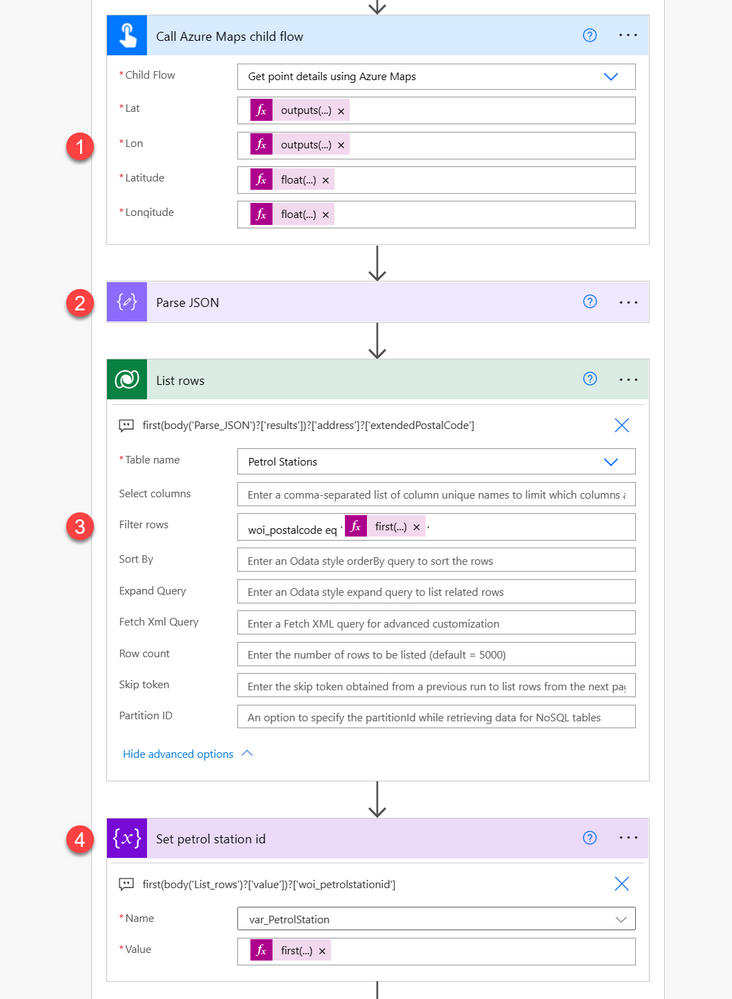
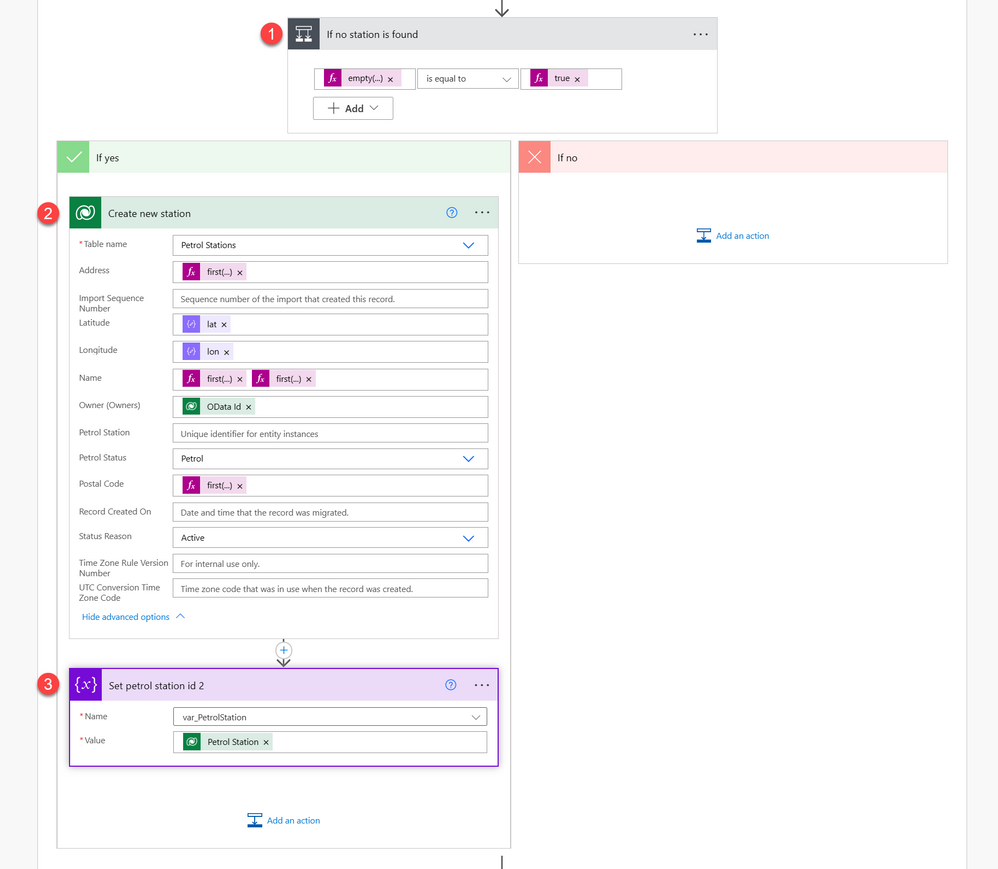
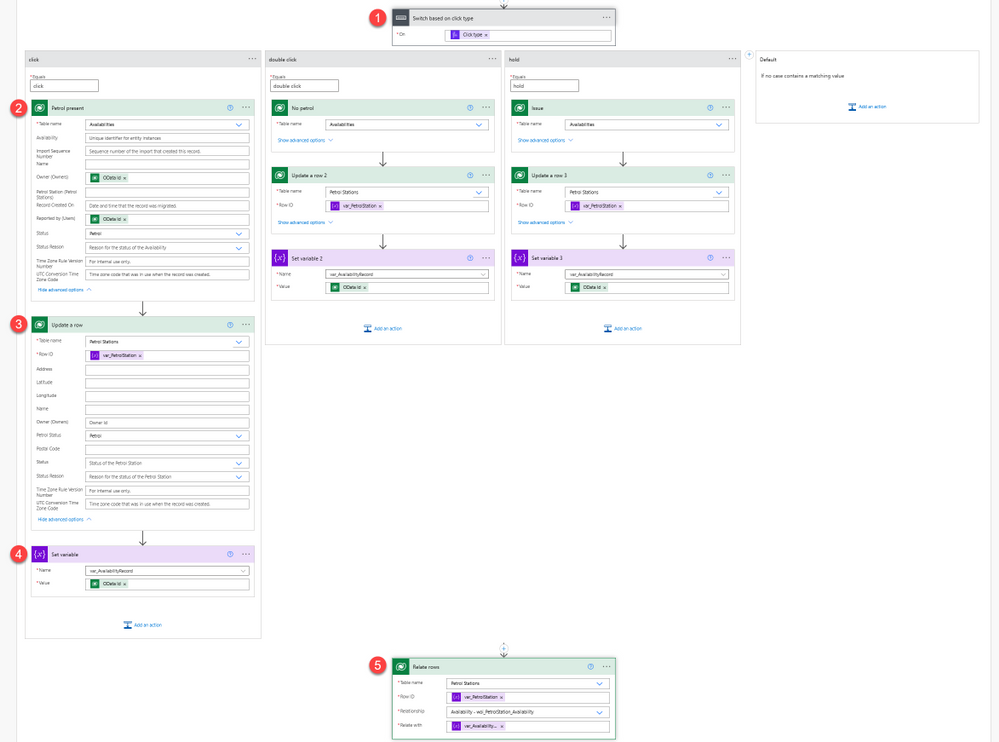
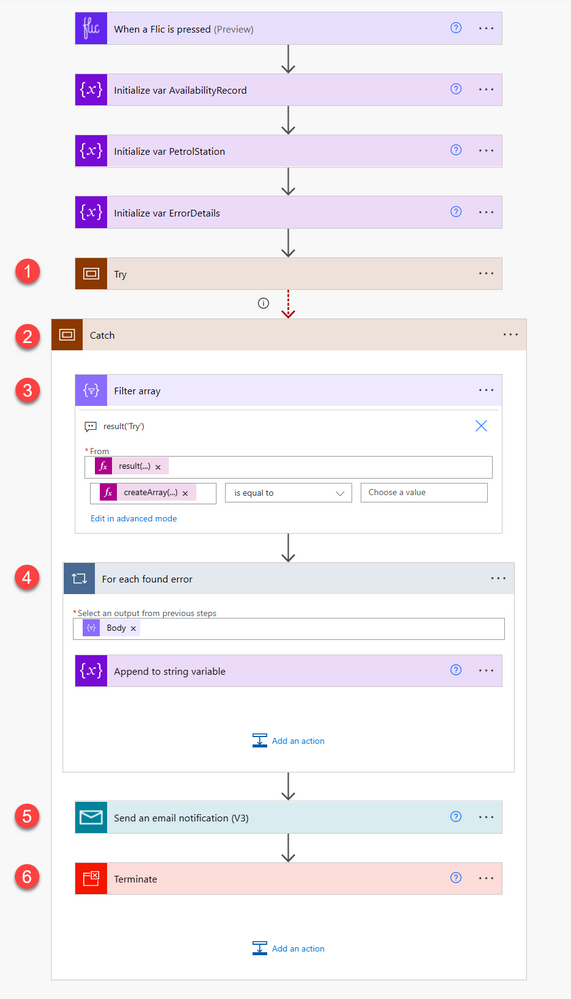
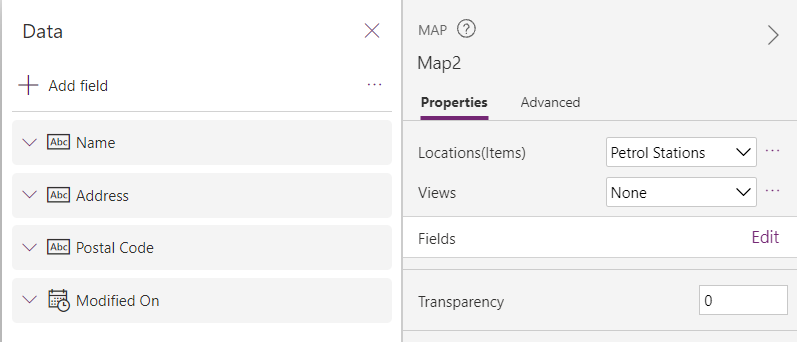
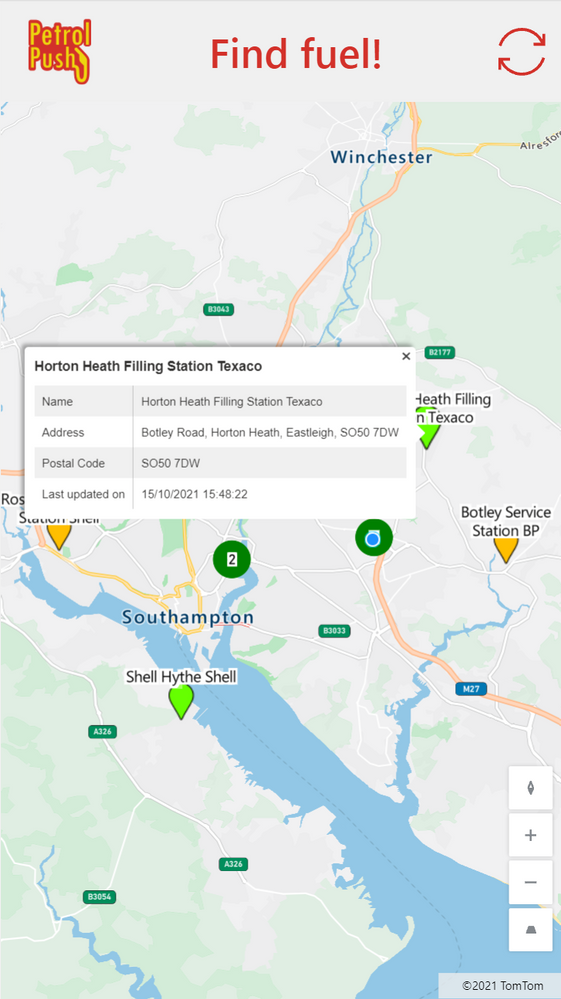


Recent Comments