
by Priyesh Wagh | Jan 12, 2022 | Dynamics 365, Microsoft, Technology
Here’s how you can correctly send a Notes attachment file from dynamics 365 CRM i.e. Dataverse to SharePoint using Power Automate
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.
by Contributed | Jan 12, 2022 | Technology
This article is contributed. See the original author and article here.
By Erin Boris, Idan Basre and Yoann Mallet
One of the latest app connectors to be added to Microsoft Defender for Cloud Apps is for Smartsheet.
As we have in the past for other protected apps, we would like to share a few examples of how to use it to secure your Smartsheet deployment.
Why Connect Smartsheet?
As with other apps, connecting Smartsheet to Defender for Cloud Apps allows you to leverage some of the built-in features of your favorite CASB, such as:
How to connect Smartsheet?
Let’s start with connecting Smartsheet.
Detailed instructions are available here, and if you prefer our video, check it out below:
Leverage Microsoft Defender for Cloud Apps with Smartsheet
The best way to get quick value from Defender for Cloud Apps when protecting Smartsheet, is to use the Advanced Hunting feature in the Microsoft 365 Defender portal.
If you have not used that portal just yet, simply visit http://security.microsoft.com and you will be redirected to it.
Once there browse to advanced hunting. This will enable you to write your own KQL queries to gather relevant information from the Defender for Cloud Apps activity logs.
Here are two relevant examples:
Scenario 1: New user invited, has an external email address
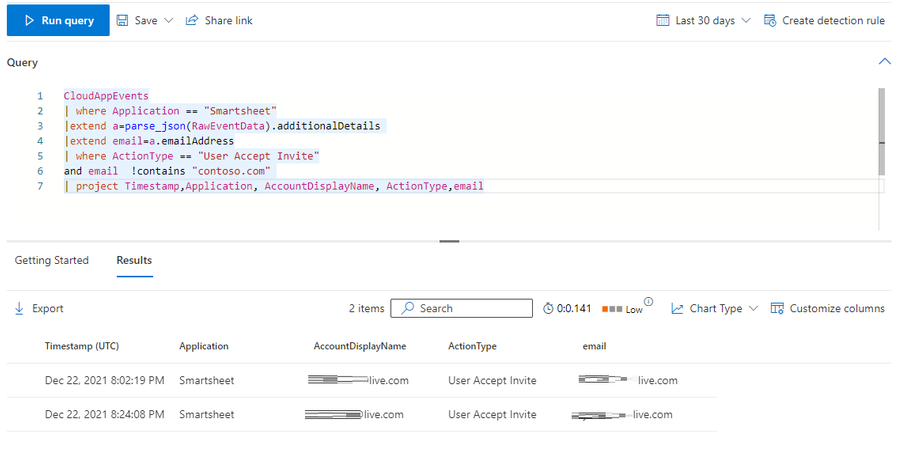
Having a new user invited to Smartsheet with an external email address may be suspicious. In order to detect this, you can leverage the following KQL Query:
CloudAppEvents
| where Application == "Smartsheet"
|extend a=parse_json(RawEventData).additionalDetails
|extend email=a.emailAddress
| where ActionType == "User Accept Invite"
and email !contains "contoso.com"
| project Timestamp,Application, AccountDisplayName, ActionType,email
Below is an example of the result of that query in Advanced Hunting:

This can potentially help you detect any attempt to exfiltrate data or identify a malicious user enabling an external account.
Another option to view all accounts with external email addresses that currently have access to Smartsheet, is from the API connector properties in Defender for Cloud Apps.
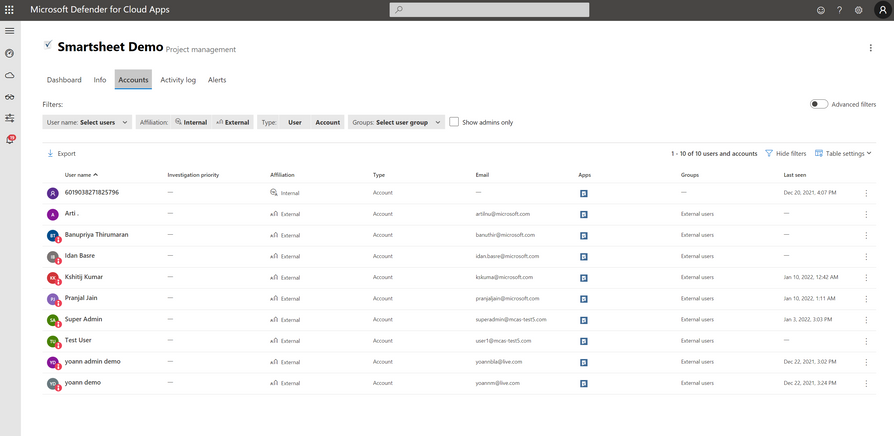
A filter can be used to see all external accounts that have accepted an invitation.
Scenario 2: File sent as attachment to external email address
When files are sent as an attachment from Smartsheet directly, to an external email address, this can be a sign of data exfiltration.
In order to identify such activities, you can leverage the following KQL Query:
CloudAppEvents
| where Application == "Smartsheet"
|extend a=parse_json(RawEventData).additionalDetails
|extend Recipient=a.recipientEmail
| where ActionType =="Sheet Send As Attachment"
and Recipient !contains "contoso.com"
| project Timestamp,Application, AccountDisplayName, ActionType,Recipient
Creating alerts from these queries
In addition to detecting these actions, Microsoft 365 Defender also allows you to create your own custom detections, and identify when these occur in near real-time, as described here.
As you can imagine, when using such powerful queries, the sky is the limit! Feel free to share any relevant KQL query you have identified for Smartsheet in the comments below.
Resources:
For more information about the features discussed in this article, please read:
Feedback
We welcome your feedback or relevant use cases and requirements for this pillar of Cloud App Security by emailing CASFeedback@microsoft.com and mentioning the area or pillar in Cloud App Security you wish to discuss.
Learn more
For further information on how your organization can benefit from Microsoft Cloud App Security, connect with us at the links below:

by Contributed | Jan 12, 2022 | Business, Microsoft 365, Technology
This article is contributed. See the original author and article here.
The two billion frontline workers, which represent 80 percent of the world’s workforce, have weathered risk, exhaustion, and ongoing disruption throughout the pandemic. From shutdowns to new safety protocols to increased workloads and dwindling inventory, the frontline is constantly facing challenges. Today we are releasing a set of technology innovations and partnerships to reduce stress on the frontline and empower the way they work and interact.
The post 3 ways technology can help rebuild your frontline workforce appeared first on Microsoft 365 Blog.
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.
by Scott Muniz | Jan 11, 2022 | Security, Technology
This article is contributed. See the original author and article here.
Adobe has released security updates to address vulnerabilities in multiple Adobe products. An attacker could exploit some of these vulnerabilities to take control of an affected system.
CISA encourages users and administrators to review the following Adobe Security Bulletins and apply the necessary updates.
Acrobat and Reader APSB22-01
Illustrator APSB22-02
Bridge APSB22-03
InCopy APSB22-04
InDesign APSB22-05

by Scott Muniz | Jan 11, 2022 | Security
This article was originally posted by the FTC. See the original article here.
As you may have heard, the U.S. Department of Education announced another extension of the flexibilities offered to federal student loan borrowers. Understanding these options can help you make more informed decisions about paying your bills and prioritizing your debts. The benefits have been extended through May 1, 2022.
You don’t need to hire a company to help you get this student loan payment relief. The program is already in place and there’s nothing you need to do to enroll. Anyone who tells you they can help you sign up for this program for a fee is a scammer.
So, just to recap, what does this mean for you if you have a federal student loan?
- This program gives temporary payment relief to borrowers with qualifying federal student loans. But some federal student loans don’t qualify – for example, older Family Federal Education Loan (FFEL) program loans or Perkins Loans that are owned by the school you attended. Contact your federal loan servicer online or by phone to find out if your loans are eligible.
- If your federal loans are covered, the U.S. Department of Education has automatically placed your loans into what’s called “administrative forbearance.” That means you can stop making payments on those loans right away, up through May 1, 2022. If your payments automatically come out of your bank account, check if any payments have been processed since March 13, 2020. If they have, you may be able to get a refund as part of administrative forbearance.
- If you want to keep making payments on your qualifying federal student loan through May 1st, the interest rate is now 0%. So any payments you make during the forbearance period may help you pay off your debt faster. If you’re on an income-based repayment program and/or a forgiveness program, you should check out Federal Student Aid’s Coronavirus page to see which option makes sense for you.
- If your federal student loans are in default, the U.S. Department of Education has stopped making collection calls, and sending letters or billing statements through May 1, 2022. And if your federal loans were in default and your employer continues to garnish your wages, you’ll get a refund.
This program only applies to federal student loans. Not sure what kinds of student loans you have? Here are two things you can do to find out:
- Get a complete list of your private and federal student loans by pulling your credit report. (In fact, you can get your report for free every week through April 20, 2022.) Read through it and find your student loans, taking note of the companies that are your lenders or loan servicers. Compare it to the full list of federal loan servicers found here.
- Confirm which of your loans are federal. Log into FSA or call the Federal Student Aid Information Center (FSAIC) at 1-800-433-3243.
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.





Recent Comments