by Contributed | Jun 10, 2022 | Technology
This article is contributed. See the original author and article here.
Establishing trust around the integrity of data stored in database systems has been a longstanding problem for all organizations that manage financial, medical, or other sensitive data. Ledger is a new feature in Azure SQL and SQL Server that incorporates blockchain crypto technologies into the RDBMS to ensure the data stored in a database is tamper evident. In this session of Data Exposed with Anna Hoffman and Pieter Vanhove, we will cover the basic concepts of Ledger and how it works, Ledger tables, and digest management, and database verification.
Resources:
Ledger Whitepaper
by Scott Muniz | Jun 10, 2022 | Security, Technology
This article is contributed. See the original author and article here.
Google has released Chrome version 102.0.5005.115 for Windows, Mac, and Linux. This version addresses vulnerabilities that an attacker could exploit to take control of an affected system.
CISA encourages users and administrators to review the Chrome Release Note and apply the necessary update.
by Contributed | Jun 9, 2022 | Technology
This article is contributed. See the original author and article here.
Establishing trust around the integrity of data stored in database systems has been a longstanding problem for all organizations that manage financial, medical, or other sensitive data. Ledger is a new feature in Azure SQL and SQL Server that incorporates blockchain crypto technologies into the RDBMS to ensure the data stored in a database is tamper evident. In this session of Data Exposed with Anna Hoffman and Pieter Vanhove, we will cover the basic concepts of Ledger and how it works, Ledger tables, and digest management, and database verification.
Watch on Data Exposed
Resources:
Ledger Whitepaper
View/share our latest episodes on Microsoft Docs and YouTube!
by Scott Muniz | Jun 9, 2022 | Security, Technology
This article is contributed. See the original author and article here.
CISA has added three new vulnerabilities to its Known Exploited Vulnerabilities Catalog, based on evidence of active exploitation. These types of vulnerabilities are a frequent attack vector for malicious cyber actors and pose significant risk to the federal enterprise. Note: to view the newly added vulnerabilities in the catalog, click on the arrow in the “Date Added to Catalog” column, which will sort by descending dates.
Binding Operational Directive (BOD) 22-01: Reducing the Significant Risk of Known Exploited Vulnerabilities established the Known Exploited Vulnerabilities Catalog as a living list of known CVEs that carry significant risk to the federal enterprise. BOD 22-01 requires FCEB agencies to remediate identified vulnerabilities by the due date to protect FCEB networks against active threats. See the BOD 22-01 Fact Sheet for more information.
Although BOD 22-01 only applies to FCEB agencies, CISA strongly urges all organizations to reduce their exposure to cyberattacks by prioritizing timely remediation of Catalog vulnerabilities as part of their vulnerability management practice. CISA will continue to add vulnerabilities to the Catalog that meet the specified criteria.
by Contributed | Jun 8, 2022 | Technology
This article is contributed. See the original author and article here.
There is no shortage of incident response frameworks in the security industry. While the processes may vary, there is relatively universal agreement on requirements to remediate an incident and conduct lessons learned. Remediation falls towards the end of the incident response cycle because security teams must fully analyze the incident to understand several dynamics:
- Who is the attacker?
- When did the incident occur?
- Which user, asset, or data are being targeted?
- Which attack techniques were leveraged?
- Which of our defenses detected it?
- Is this the full scope of the compromise, or are more factors involved?
Security teams respond after understanding these and several organizationally aligned information requirements. The incident is closed when there is confidence the attacker was expelled from the environment and respective actions completed. The difference between a young Security Operations Center (SOC) and a mature one often lies in the way incident response teams conducts lessons learned. This process evolves from a “rinse and repeat” type approach to proactive threat modeling. Proactive threat modeling is critical to understanding where the attacker maneuvered through a network. The MITRE ATT&CK® framework allows security teams to understand the methods attackers employ against networks. Recently MITRE Engenuity published the NIST SP 800-53 Controls to ATT&CK Mappings which provides an actionable approach to implementing defenses based in the NIST SP 800-53 controls framework.
 Microsoft Sentinel: Threat Analysis & Response Solution
Microsoft Sentinel: Threat Analysis & Response Solution
The Microsoft Sentinel: Threat Analysis & Response Solution takes this a step further with (2) new Workbooks designed to support development of threat hunting programs and dynamic threat modeling designed to identify, respond, harden, and remediate against threats. Microsoft Defender for Cloud is a Cloud Workload Protection Platform (CWPP) and Cloud Security Posture Management (CSPM) which provides powerful coupling with Microsoft Sentinel. Where Microsoft Sentinel provides incident response capabilities, Microsoft Defender for Cloud provides remediation actions aligned to respective regulatory compliance initiatives. Once the incident is fully remediated and cloud weaknesses are addressed there is also the ability to evaluate analytics coverage with the Microsoft Sentinel MITRE ATT&CK® blade. Check out the demo to see how.
Solution Benefits
- Proactive threat modeling (red vs. blue)
- Quantifiable framework for building threat hunting programs
- Monitoring & alerting of security coverage, threat vectors, and blind spots
- Response via security orchestration automation and response (SOAR) playbooks
- Remediation with cloud security posture management (CSPM)
- Compliance alignment to NIST SP 800-53 controls
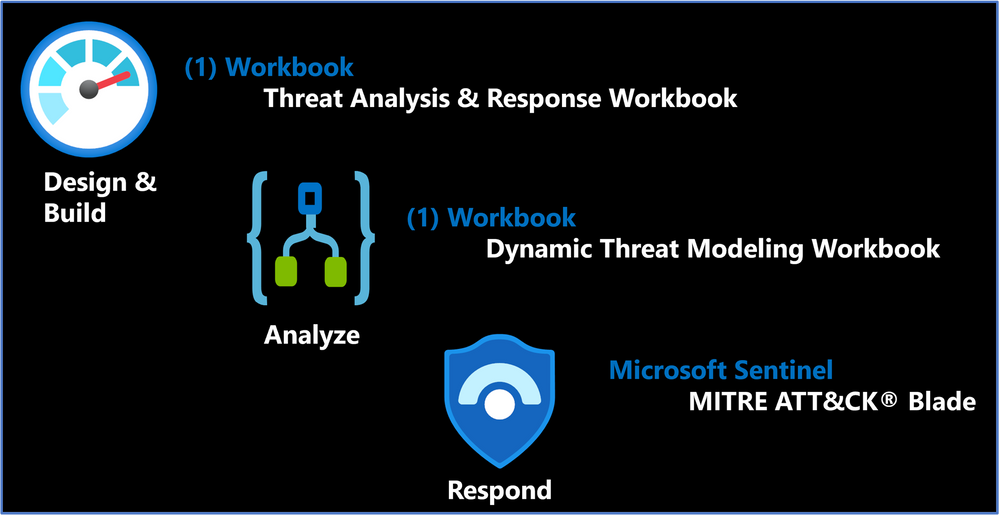 Solution Content & Workflows
Solution Content & Workflows
Solution Overview
Threat Analysis & Response Workbook
Designed by the Microsoft Threat Intelligence Center, the Threat Analysis & Response Workbook provides the foundation for building threat hunting programs. This workbook features recommended steps for getting started including resources for deploying analytics rules and hunting queries. Data Source Statistics provides an overview of which logs are ingested from respective sources which provides a starting point for determining utility of respective analytics rules. The Microsoft Sentinel GitHub section provides an overview of available analytics by alignment to respective tactics/techniques. MITRE ATT&CK Navigator Heatmap provides an assessment of coverage by tactic and technique areas which is valuable for evaluating the efficiency of organizational threat hunting programs.
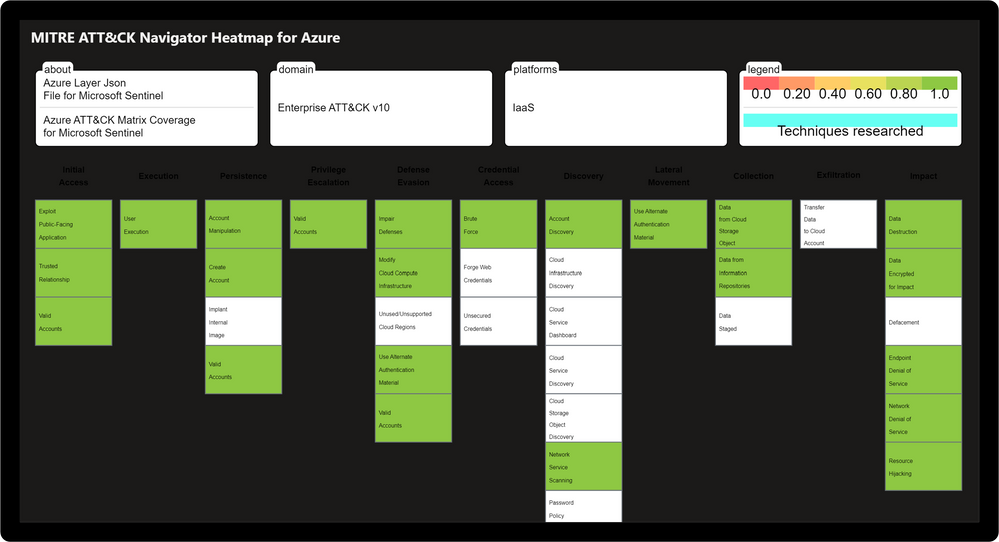 Threat Analysis & Response Workbook
Threat Analysis & Response Workbook
Dynamic Threat Analysis & Response Workbook
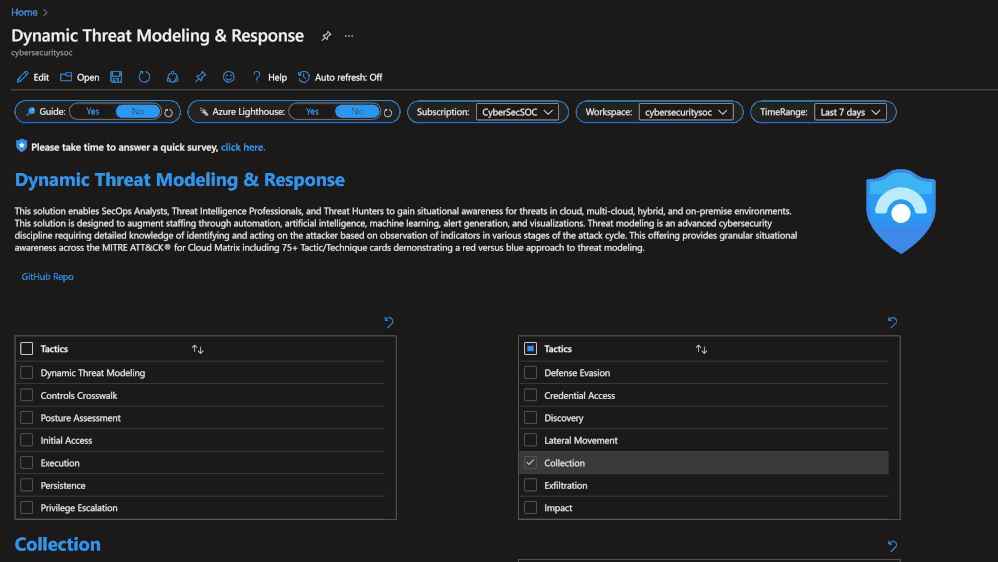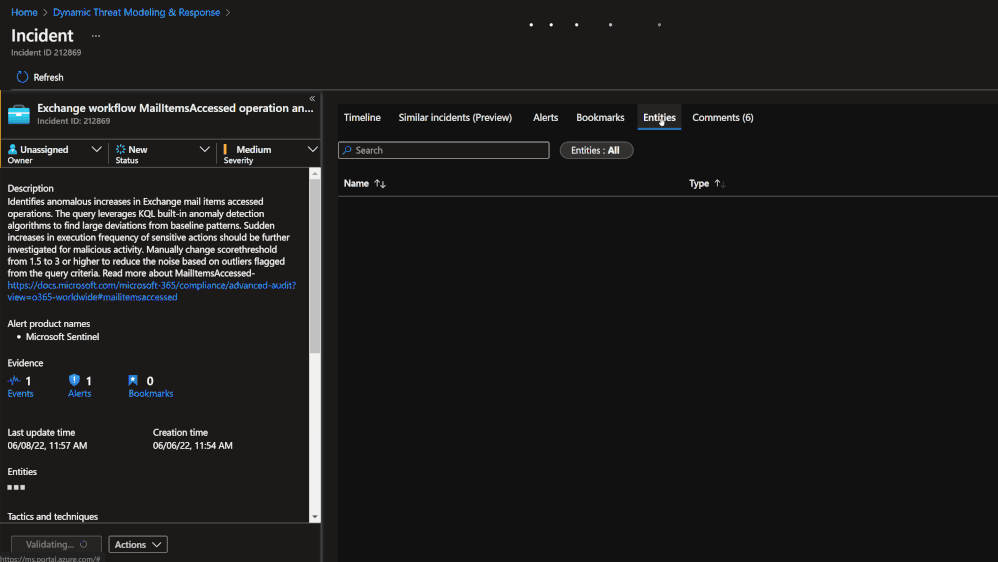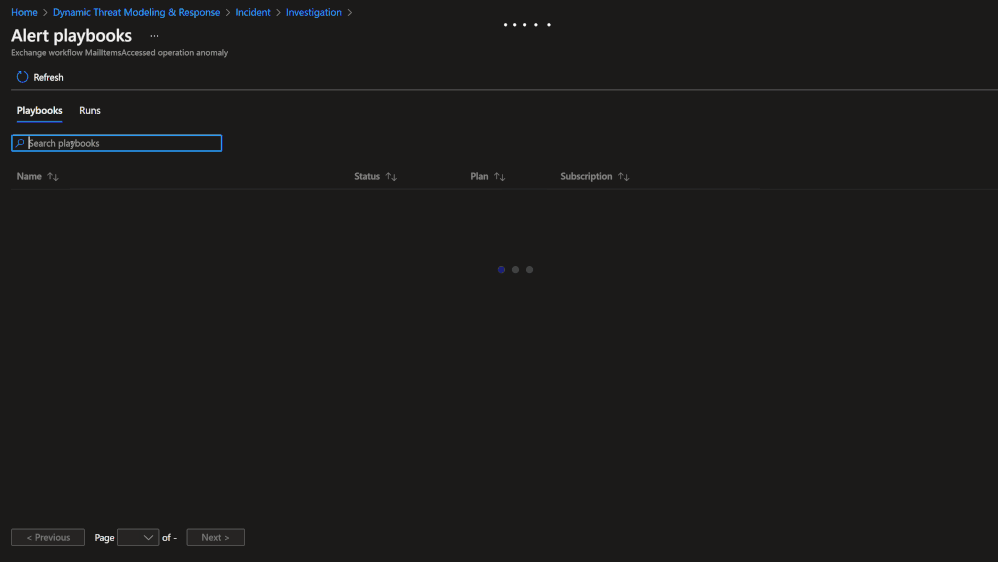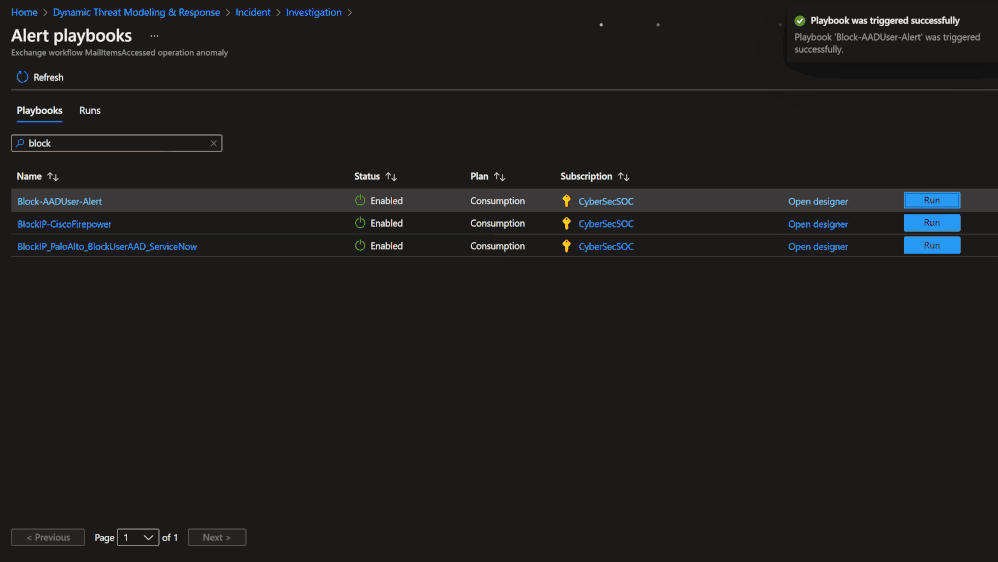
The Dynamic Threat Analysis & Response Workbook dynamically assesses attacks to your on-premises, cloud, and multi-cloud workloads. Attackers are categorized by the MITRE ATT&CK for Cloud Matrix and evaluated against Microsoft Sentinel observed Analytics and Incidents. This provides pivots to evaluate attacks against specific users, assets, attacking IPs, countries, assigned analyst, and detecting product. Each tactic provides a respective control area comprised of technique control cards.
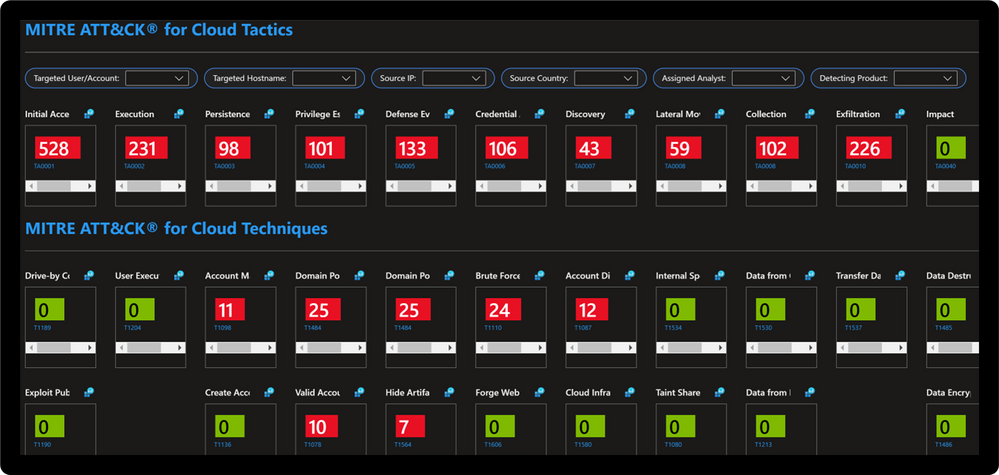 Dynamic Threat Modeling & Response Workbook
Dynamic Threat Modeling & Response Workbook
Technique Control Cards provide details of establishing coverage, evaluation of observed attacks, and defense recommendations aligned to NIST SP 800-53 controls. Observed attacks are addressed via Microsoft Sentinel Incidents for Investigation, Playbooks for Response, MITRE ATT&CK blade for Coverage, and Microsoft Defender for Cloud for Remediations.
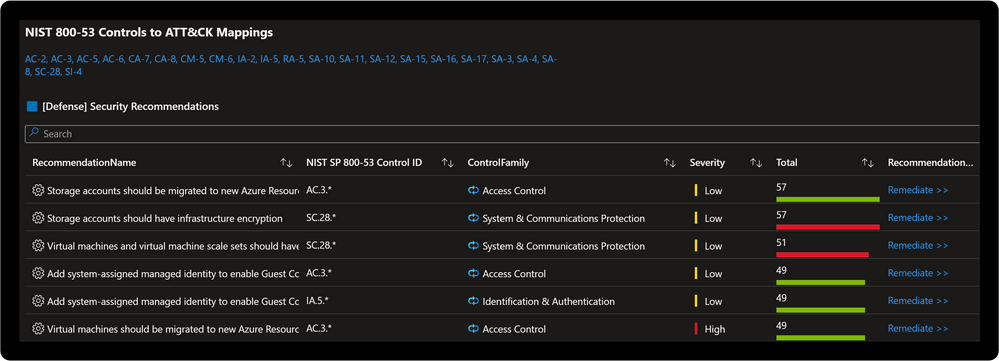 Improve posture by implementing NIST SP 800-53 control recommendations with Microsoft Defender for Cloud
Improve posture by implementing NIST SP 800-53 control recommendations with Microsoft Defender for Cloud
Microsoft Sentinel: MITRE ATT&CK Blade
MITRE ATT&CK is a publicly accessible knowledge base of tactics and techniques that are commonly used by attackers and is created and maintained by observing real-world observations. Many organizations use the MITRE ATT&CK knowledge base to develop specific threat models and methodologies that are used to verify security status in their environments. Microsoft Sentinel analyzes ingested data, not only to detect threats and help you investigate, but also to visualize the nature and coverage of your organization’s security status.
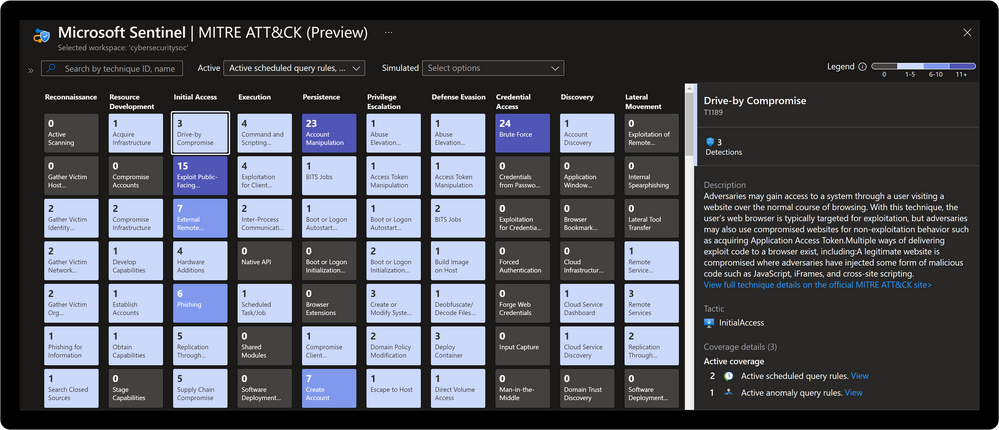 Microsoft Sentinel: MITRE ATT&CK Blade
Microsoft Sentinel: MITRE ATT&CK Blade
Get Started Today
Learn more about threat hunting with Microsoft Security
Understand security coverage by the MITRE ATT&CK® framework
Joint forces – MS Sentinel and the MITRE framework
MITRE ATT&CK® mappings released for built-in Azure security controls
This solution demonstrates best practice guidance, but Microsoft does not guarantee nor imply compliance. All requirements, tactics, validations, and controls are governed by respective organizations. This solution provides visibility and situational awareness for security capabilities delivered with Microsoft technologies in predominantly cloud-based environments. Customer experience will vary by user and some panels may require additional configurations for operation. Recommendations do not imply coverage of respective controls as they are often one of several courses of action for approaching requirements which is unique to each customer. Recommendations should be considered a starting point for planning full or partial coverage of respective requirements.


Recent Comments