by Contributed | Jun 17, 2022 | Technology
This article is contributed. See the original author and article here.
Earlier this year, we introduced 9 new out-of-box Trainable Classifiers for sensitive business document discovery and classification. These include Finance, IT, IP, Tax, Agreements, Healthcare, Procurement, and Legal Affairs.
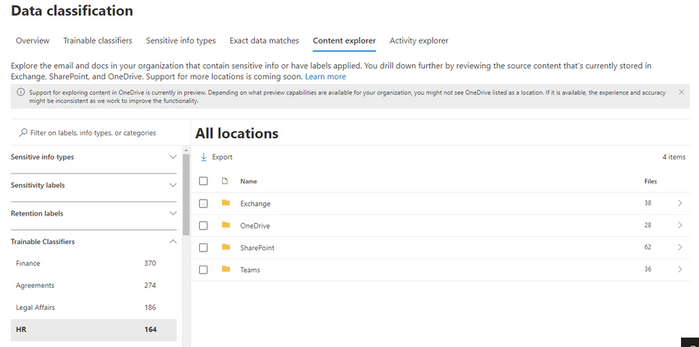
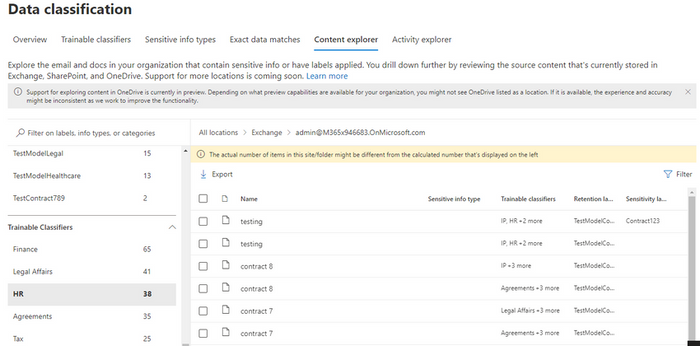
To make the discovery of your sensitive information easier, we are introducing data discovery with Trainable Classifiers in Content Explorer. This means that your sensitive documents that are classified by Trainable Classifiers can be viewed even if they are not used as conditions in an auto-labeling policy. This includes both pre-trained out-of-box models as well as custom trainable classifiers.
For each classifier, you can drill down from the location to the specific document that has been classified. If the classification is not what is expected, there is an opportunity to provide No-Match feedback so that we can further improve our classifiers. We currently have 11 out-of-box business document classifiers available for this feature with another 23 in private preview and another 30 that will be available for preview shortly.
These Trainable classifiers can be used for the discovery and classification of sensitive information across SPO and ODB by clicking on the respective classifier/category in Content Explorer.
Some of the Trainable Classifiers we plan to provide as built-in out-of-box include
- Intellectual property and trade secrets such as Project Documents, Standard Operating Procedures, Software Product Development Files, Network Design documents
- Business-critical documents such as M&A files, Business Plan, Strategic Planning Documents, Meeting Notes Statement of Work, Financial Statements, Manufacturing batch records, Customer account Files, Market research reports
- Sensitive business content as part of daily business operations such as Payroll, Invoice, Statement of Work, Financial Statements, Statement of Accounts, Employee Performance Files, Facility Permits

Customers can opt-out of this feature by raising a support ticket with this request and this feature can be turned off for their tenant.
Thanks for reading!
by Contributed | Jun 16, 2022 | Technology
This article is contributed. See the original author and article here.

Minimize handoff/huddle times between shifts with Soundbite in Microsoft Teams.
“Traditional written communications isolate and inconvenience many employees resulting in a disconnect.
With Soundbite™ for Microsoft Teams, you can show empathy and create a sense of purpose by sharing personalized short-form content with frontline workers” and clinicians. – Soundbite™ for Your Frontline Workforce
Watch the video below to see how “Dr. G.” demonstrates the use of clinician soundbites to minimize overhead and churn for already overworked clinicians.
To learn more about the use of Microsoft Teams and Soundbite leverage the resource links below. You can also reach Soundbite directly at https://soundbite.ai/ and/or contact you Microsoft account team.
Resources:
Work on the Clinician Soundbites was done by Jasmine Hoegh, Erin Spencer, and Michael Gannotti
Thanks for visiting – Michael Gannotti LinkedIn | Twitter

by Scott Muniz | Jun 16, 2022 | Security, Technology
This article is contributed. See the original author and article here.
CISA has released Trusted Internet Connections (TIC) 3.0 Cloud Use Case for public comment. TIC is a federal cybersecurity initiative intended to secure federal data, networks, and boundaries while providing visibility into agency traffic, including cloud communications.
TIC use cases provide guidance on the secure implementation and configuration of specific platforms, services, and environments, and are released on an individual basis. TIC 3.0 Cloud Use Case defines how network and multi-boundary security should be applied in cloud environments, focusing on cloud deployments for Infrastructure-as-a-Service, Platform-as-a-Service, Software-as-a-Service, and Email-as-a-Service. This is the last of the Initial Common Trusted Internet Connections Use Cases outlined in OMB Memorandum M-19-26.
CISA encourages federal government stakeholders to review Executive Assistant Director Goldstein’s blog post and TIC 3.0 Cloud Use Case and share it broadly within their networks.
by Scott Muniz | Jun 16, 2022 | Security, Technology
This article is contributed. See the original author and article here.
Cisco has released security updates to address vulnerabilities in multiple Cisco products. An attacker could exploit some of these vulnerabilities to take control of an affected system. For updates addressing lower severity vulnerabilities, see the Cisco Security Advisories page.
CISA encourages users and administrators to review the following Cisco advisories and apply the necessary updates:

by Contributed | Jun 16, 2022 | Business, Microsoft 365, Technology
This article is contributed. See the original author and article here.
We are excited to announce the general availability of Microsoft Defender for individuals—a new security app designed to keep individuals and families safer online. Available for Microsoft 365 Personal and Family subscribers starting today, Microsoft Defender helps simplify your online security through one, unified view into your family’s protections, across your personal phones and computers.
The post Introducing Microsoft Defender: A new Microsoft 365 online security app for you and your family appeared first on Microsoft 365 Blog.
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.


Recent Comments