As finance leaders scale to meet growing business complexity—spanning global entities, evolving regulations, and rising business performance demands—the pressure is on to do more than close the books. Today’s finance organizations must move faster, manage risk more proactively, and adapt dynamically.
That requires more than automation, it demands a new era of ERP. One where systems don’t just record and report, but act, learn, and adapt—where AI agents, embedded in everyday workflows, help finance teams manage complexity, reduce manual effort, and accelerate decision-making.
At Gartner CFO & Finance Executive Conference 2025—taking place at the Gaylord National Resort and Convention Center—we’re showcasing how Microsoft is enabling this shift. Visit our team of technical specialists at Booth #313 and attend our keynote to see how Microsoft is helping finance teams develop and implement AI strategies that align with business goals—without compromising on governance, compliance, or security.
Global-scale financial operations for the modern CFO
As organizations adapt to shifting markets—whether by entering new regions, adjusting product strategies, or responding to evolving regulations—financial operations become more complex. Finance teams are tasked with managing activity across multiple legal entities, currencies, and accounting standards, all while ensuring accuracy, compliance, and transparency. What was once the domain of large multinational companies is now a day-to-day reality for businesses of all sizes. As a result, global-scale financial operations have shifted from being a specialized need within your business systems to a core capability.
This evolving reality is creating a new baseline for finance transformation. Global-scale financial operations are no longer a niche requirement—they’re an operational necessity. Finance teams must support complex processes like consolidation, allocations, revaluation, and compliance across geographies and systems, while maintaining accuracy and transparency.
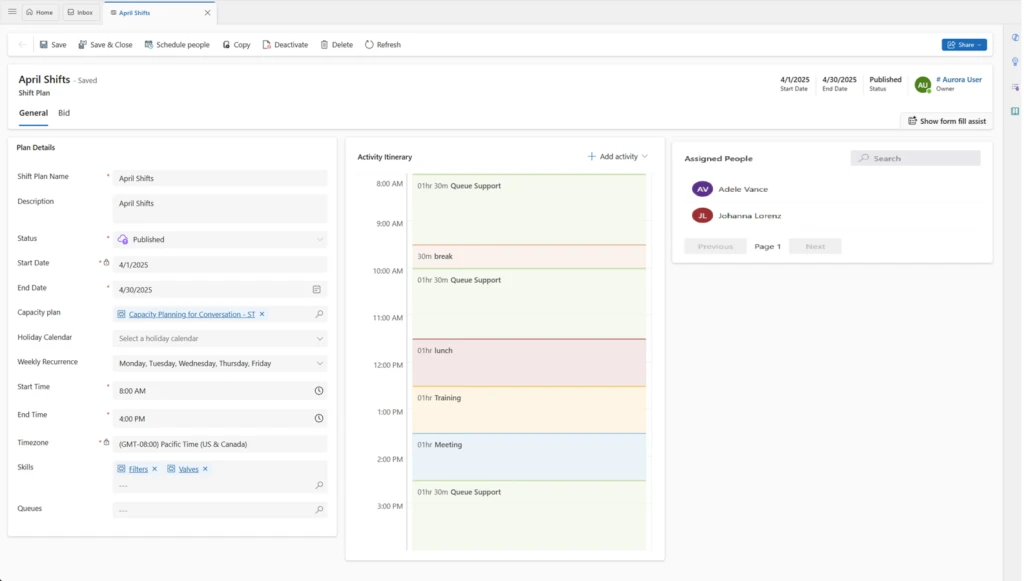
Microsoft Dynamics 365 Finance provides this foundation with capabilities that include:
- Multi-entity journal processing from a single experience.
- Multi-ledger automation to support International Financial Reporting Standards (IFRS), United States Generally Accepted Accounting Principles (US GAAP), and local standards.
- Cross-entity allocations, revaluations, and close activities.
- Shared hierarchies for business units, customers, vendors, and financial dimensions.
- Integrated consolidation and reporting across systems and geographies.
These features help finance organizations simplify complexity and operate with greater agility and precision—without increasing overhead.
Investing in the future of global-scale finance and agentic operations
As business models continue to evolve and financial complexity deepens, Microsoft is making foundational investments to support the next generation of finance operations. Our roadmap for Dynamics 365 Finance focuses on deepening multi-entity and multi-ledger capabilities, accelerating period-end close, and enabling flexible data hierarchies across legal entities, currencies, and accounting standards. Here are a few things we’re investing in:
- Multi-entity and intercompany operations are often constrained by fragmented processes and manual handoffs across legal entities. A new approach is needed to streamline activity across the organization, reduce duplication, and increase control—all without scaling up effort or cost.
- Multi-ledger accounting is becoming essential as more companies operate in jurisdictions that require parallel accounting standards. Traditional methods often rely on offline reconciliation or separate systems. We’re investing in ways to maintain compliance and transparency while reducing complexity.
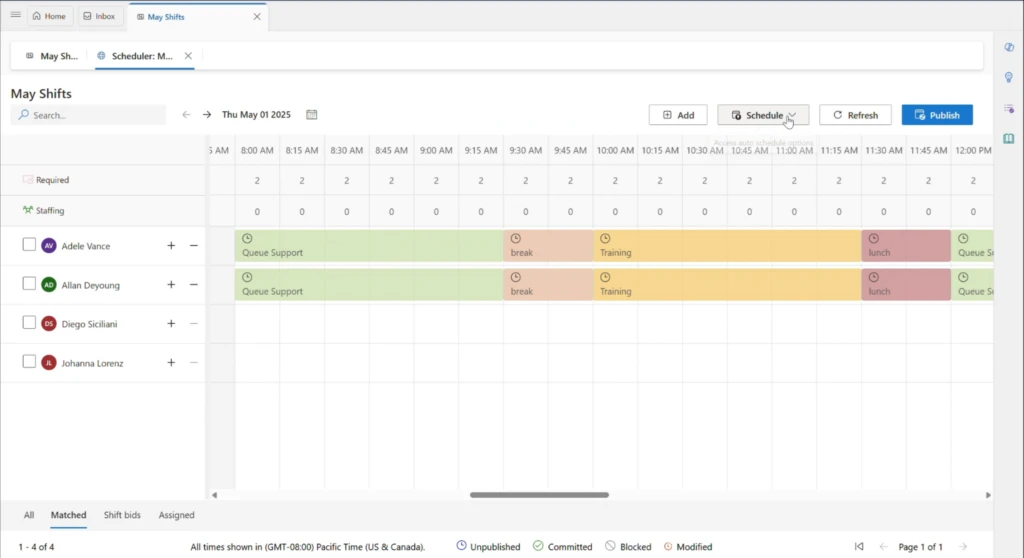
- Accelerating period-end close remains one of the most persistent challenges for finance teams. Time-consuming reconciliations, disconnected systems, and limited visibility into task status slow down the close. We’re focusing on integrated task orchestration, automation, and embedded intelligence to improve agility and confidence.
- Flexible data hierarchies are increasingly essential as organizations grow and restructure—they help introduce new business units, financial dimensions, and operational models. We’re evolving to provide more support for shared, adaptable hierarchies across entities and dimensions to improve enterprise-wide reporting, planning agility, and compliance alignment.
At the center of this is a new vision for ERP—one that supports your organization’s shift to a more autonomous enterprise. This model brings together adaptive user experiences, AI agents, and a set of modular, extensible capabilities that can be accessed across applications and workflows. Finance professionals can interact with the system in natural language, receive guided recommendations, and delegate tasks to AI-powered agents embedded directly within their daily workflows. At the same time, these systems are becoming more interoperable—able to connect data, coordinate actions, and deliver outcomes across complex organizational structures.
We’re building financial operations solutions that don’t just keep pace with change, they help you lead it.
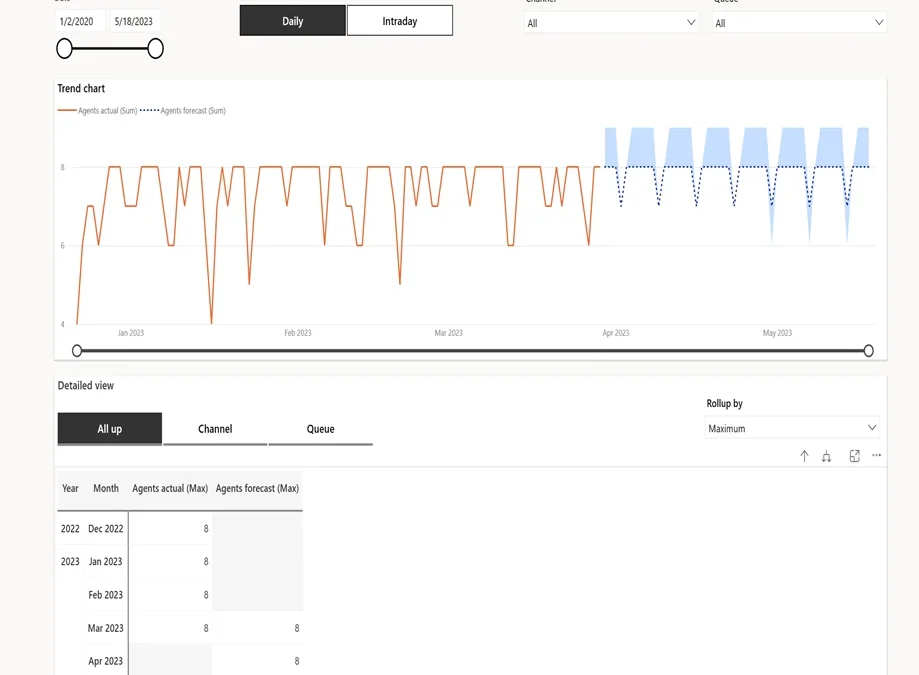
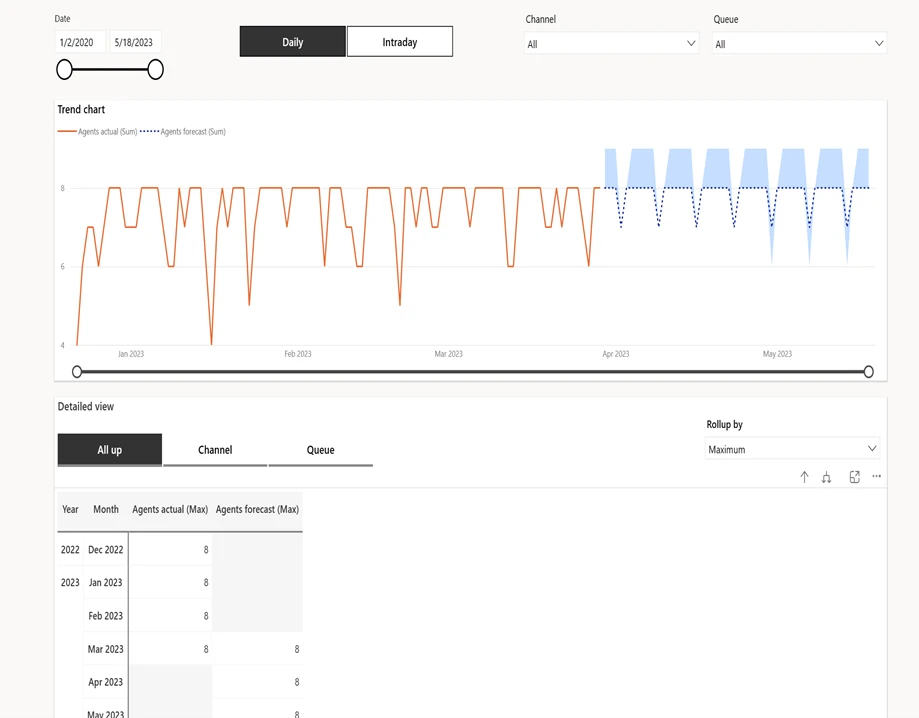
While intelligent automation has improved efficiency across finance processes, the next phase of transformation will require more than assistance. This next phase calls for intelligent systems that act with autonomy and help finance teams stay ahead of increasing demands.
Microsoft is delivering both embedded and the ability to build AI agents to support this shift:
- The Account Reconciliation Agent, embedded in Dynamics 365 Finance, helps automate transaction matching, flag discrepancies, and reduces time spent on period-end close activities. Watch the Account Reconciliation Agent here.
- The Finance Reconciliation Agent, available in Excel, enables intelligent reconciliation of data sets from across the business using familiar tools. Watch the Finance Reconciliation Agent here.
- Custom finance agents, built with Microsoft Copilot Studio, allow organizations to design their own agent experiences—supporting processes like allocation modeling, compliance validation, or internal control workflows tailored to their unique operating model.
This approach to AI implementation represents a new layer of the finance IT stack—one that not only reduces manual workload but allows you to use and create agents that work for you to enhances accuracy, accountability, and insight.
Gartner CFO & Finance Executive Conference 2025
Learn how Microsoft helps finance teams develop and implement AI strategies.
Visit Microsoft at Booth #313
If you’re attending Gartner CFO & Finance Executive Conference 2025, we invite you to connect with us in person.
At Booth #313, you can:
- See Microsoft’s first-party finance agents in action.
- Explore how Dynamics 365 is powering global-scale financial operations today.
- Learn how to build custom agents with Copilot Studio.
- Hear how Microsoft’s own finance organization is applying these tools to modernize operations.
Join us for our featured session on May 20 at 3:15 PM Eastern Time (UTC – 4) in Potomac B, available on-demand to attendees only:
- Session title: Unlocking Business Value with AI-Enabled Outcomes
- Speakers: April Olson (Dynamics 365 Finance), Cory Hrncirik (Modern Finance), Stephanie Dart (Product Marketing)
- What to expect: Learn how Microsoft is applying cutting-edge AI to transform finance operations—from reconciliation and forecasting to policy guidance and close review. We’ll share practical examples from our own finance organization, highlight new agent capabilities, and offer guidance on how to begin implementing agent-based automation in your own enterprise.
Whether your finance team supports 10 legal entities or hundreds, the tools to manage complexity, enhance insight, and drive transformation are available now.
Let us show you what’s next in financial and agentic operations, and how Microsoft can help you lead the way.
The post See what’s next in financial operations from Microsoft Dynamics 365 at Gartner CFO & Finance Executive Conference 2025 appeared first on Microsoft Dynamics 365 Blog.
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.





Recent Comments