by Contributed | Jun 2, 2024 | Technology
This article is contributed. See the original author and article here.
Spotlight on AI in your DevOps Lifecycle
Explore the transformative power of artificial intelligence in DevOps with our comprehensive series, “Spotlight on AI in Your DevOps Lifecycle.” This series delves into the integration of AI into every stage of the DevOps process, providing invaluable insights and practical guidance. Whether you’re a seasoned professional or new to the field, these episodes will equip you with the knowledge to leverage AI effectively in your development and operations lifecycle.
Speakers


Sessions: Register Now. https://aka.ms/DevOpsAISeries
DevOps in the era of Generative AI: Foundations of LLMOps
With the advent of generative AI, the development life cycle of intelligent applications has undergone a significant change. This shift from classical ML to LLMs-based solutions leads to implications not only on how we build applications but also in how we test, evaluate, deploy, and monitor them. The introduction of LLMOps is an important development that requires understanding the foundations of this new approach to DevOps.
The session “DevOps in the era of Generative AI: Foundations of LLMOps” will explore the basics of LLMOps, providing examples of tools and practices available in the Azure ecosystem. This talk will be held on June 12th, 2024, from 4:00 PM to 5:00 PM (UTC).
Register Now. https://aka.ms/DevOpsAISeries
Continuous Integration and Continuous Delivery (CI/CD) for AI
The session “Continuous Integration and Continuous Delivery (CI/CD) for AI” will focus on MLOps for machine learning and AI projects. This talk will cover how to set up CI/CD and collaborate with others using GitHub. It will also discuss version control, automated testing, and deployment strategies.
The session will take place on June 20th, 2024, from 6:00 PM to 7:00 PM (UTC).
Register Now. https://aka.ms/DevOpsAISeries
Monitoring, Logging, and AI Model Performance
Building an AI application does not stop at deployment. The core of any AI application is the AI model that performs certain tasks and provides predictions to users. However, AI models and their responses change over time, and our applications need to adapt to these changes in a scalable and automated way.
The session “Monitoring, Logging, and AI Model Performance” will explore how to use tools to monitor the performance of AI models and adapt to changes in a scalable way. This talk will be held on June 26th, 2024, from 4:00 PM to 5:00 PM (UTC).
Register Now. https://aka.ms/DevOpsAISeries
Scaling and Maintaining Your Applications on Azure
Azure is a popular cloud platform that provides many benefits for running AI applications. This session will focus on the practical aspects of running your applications on Azure, with a special emphasis on leveraging Azure OpenAI and Python FastAPI. The talk will cover best practices for scaling your applications to meet demand and maintaining their health and performance.
The session will be held on July 3rd, 2024, from 4:00 PM to 5:00 PM (UTC).
Register Now. https://aka.ms/DevOpsAISeries
Security, Ethics, and Governance in AI
AI brings many exciting new features into the tech landscape, but it also introduces new security risks and challenges. In this session, we will learn about the best practices and tools for securing AI-enabled applications and addressing ethical and governance issues related to AI.
The session will take place on July 10th, 2024, from 4:00 PM to 5:00 PM (UTC).
Register Now. https://aka.ms/DevOpsAISeries
by Contributed | Jun 1, 2024 | Technology
This article is contributed. See the original author and article here.
Navigating the Future with Microsoft Copilot: A Guide for Technical Students
Introduction
Copilot learning hub
Copilot is an AI assistant powered by language models, which offers innovative solutions across the Microsoft Cloud. Find what you, a technical professional, need to enhance your productivity, creativity, and data accessibility, and make the most of the enterprise-grade data security and privacy features for your organization.

As a technical student, you’re always on the lookout for tools that can enhance your productivity and creativity.
Enter Microsoft Copilot, your AI-powered assistant that’s revolutionizing the way we interact with technology. In this blog post, we’ll explore how Copilot can be a game-changer for your learning and development.
Understanding Copilot Microsoft Copilot is more than just an AI assistant; it’s a suite of solutions integrated across the Microsoft Cloud. It’s designed to boost your productivity by providing enterprise-grade data security and privacy features. Whether you’re coding, creating content, or analyzing data, Copilot is there to streamline your workflow.
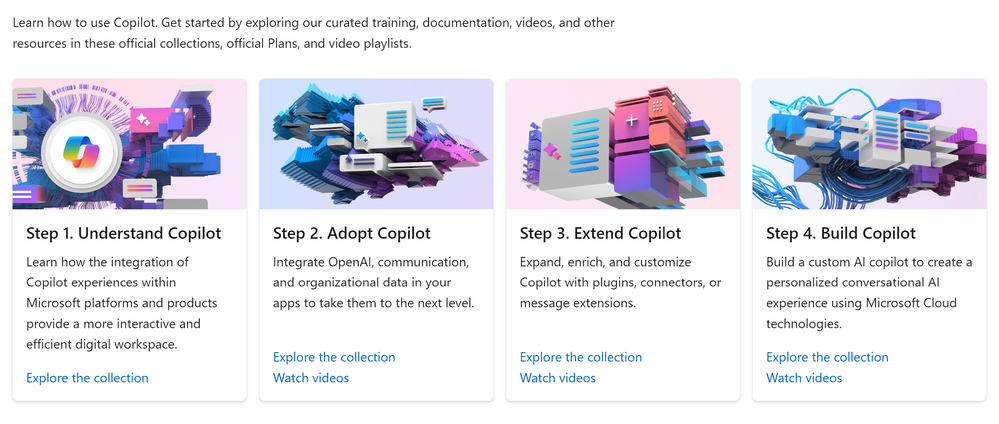
Getting Started with Copilot To get started, dive into the wealth of resources available on the official Copilot page. From curated training and documentation to informative videos and playlists, there’s a treasure trove of knowledge waiting for you.
Customizing Your Experience One of the most exciting aspects of Copilot is its flexibility. You can expand and enrich your Copilot experience with plugins, connectors, or message extensions. Even better, you can build a custom AI copilot using Microsoft Cloud technologies to create a personalized conversational AI experience.
Empowering Your Education Copilot isn’t just a tool; it’s a partner in your educational journey. It can assist you in implementing cloud infrastructure, solving technical business problems, and maximizing the value of data assets through visualization and reporting tools.
The Copilot Challenge Ready to put your skills to the test? Immerse yourself in cutting-edge AI technology and earn a badge by completing one of the unique, AI-focused challenges available until June 21, 2024. These challenges offer interactive events, expert-led sessions, and training assets to help you succeed.

Conclusion Microsoft Copilot is more than just an assistant; it’s a catalyst for innovation and productivity. As a technical student, embracing Copilot can help you stay ahead of the curve and unlock a new era of growth. So, what are you waiting for?
Let Copilot guide you through the exciting world of AI and cloud technologies. Learn how to use Microsoft Copilot | Microsoft Learn
by Contributed | May 31, 2024 | Technology
This article is contributed. See the original author and article here.
Whenever you run load tests on your endpoints in Azure Load Testing, there might be a situation where your endpoints require an access token. We have seen that before load testing these endpoints, most users generate an access token and store it in the Azure Key Vault. They then pass this token as a variable in the Header of the request as a bearer token to authenticate at the endpoint. But there might be a few problems with this approach:
- Sometime has elapsed between the act of storing the token in the key vault and the start of execution of the test. There can be a case where the token might expire during the test run and the request at the endpoints start throwing errors.
- Only one static token is stored in the key vault and is used for all the requests. When we are load testing with multiple Virtual Users, we want a situation where all users have a unique access token while making the requests, as it will mimic a real-life scenario. Currently scaling is there, but the authenticity is lost.
- Most access tokens have a lifetime of around 60-75 minutes on an average. When we are running load tests for longer durations (E.g.- Soak Tests), it is almost certain that the access token will get expired during the execution of the test. We would like to have some sort of control where the service intelligently identifies when a token is going to get expired, and renews it, so that the test can carry on as usual.
This blog covers how you can create a JMeter Test plan, where you can implement a mechanism to generate and refresh access tokens which are unique for every user and run it at scale in Azure Load Testing.
PREREQUISITES
CREATING THE TEST PLAN IN THE JMETER GUI

Create a Test Plan in JMeter. Add your variables in the “User defined variable section.” If you are testing an Azure endpoint, you may need to use the GetSecret function to store the client_ID, client_secret, tenant_ID etc. Proceed to the config elements and add a HTTP Cookie Manager and HTTP Cache Manager. Make sure to select the option to clear cache and cookies on each iteration.
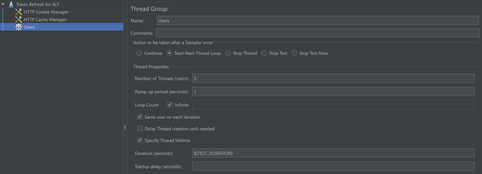
Create a Thread Group and provide the required inputs. Enable the “Start Next Thread Loop” Option. Set the Loop Count to infinite and set the test duration.
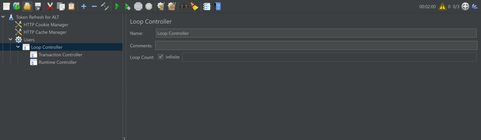
Inside the Thread Group, create a Loop Controller and set the loop count to infinite. Further, inside the loop controller, add two more controllers: The transaction controller, which will generate the token and the runtime controller, which will refresh the token.
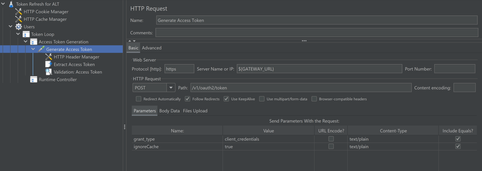
Inside the Transaction Controller, add an HTTP Sampler and setup a POST request to the token endpoint to fetch the access token. Set “grant type” as “client credentials” and “ignore Cache” as “true”. Add a HTTP Header Manager to the sampler and add the Content-Type as “application/x-www-form-urlencoded” and set the Authorization depending upon the configuration done at the token endpoint.
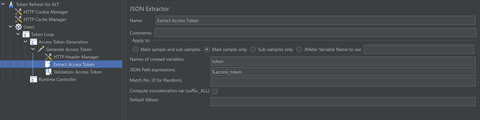
Add a JSON extractor to extract the access token and set it in a variable which will be used going forward.
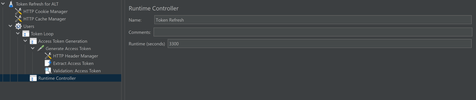
Proceed to the runtime controller. In the Runtime section, specify the time after which you want the token to be refreshed. Usually token lasts for 60 minutes. Make sure to include some buffer time before token expiry. You can also extract the expiry time of the token, store it in a variable and pass it here.
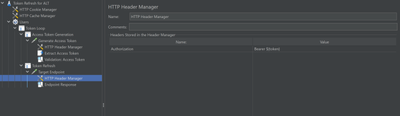
Add another HTTP Sampler, this time sending a GET request to the target endpoint. In the HTTP Header Manager, set Authorization to Bearer ${token}.
Add some listeners like View Results tree, Summary Report etc to analyse the results locally. Results should look something like this.
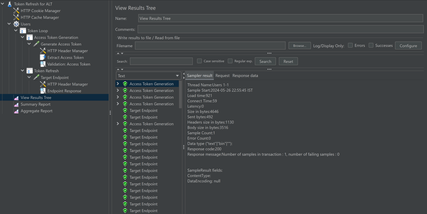
Now the JMeter script is complete and can be used in Azure Load Testing to run it at scale.
Creating and Running the Load Test
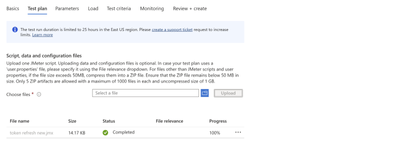
- Upload the JMeter Script in the Test plan tab.
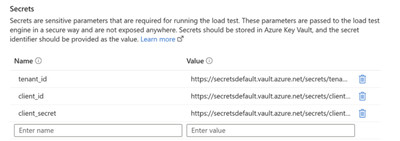
- Configure the Secrets section under the Parameters tab. Now, we are all set to launch the test.
CONCLUSION
Now you can run your load tests for an even longer duration without having to worry about the expiry of access tokens.
Try this this out and let us know if this works for you. Please use the comments section or use our feedback forum.
HAPPY LOAD TESTING!!
by Contributed | May 30, 2024 | Technology
This article is contributed. See the original author and article here.
Introduction
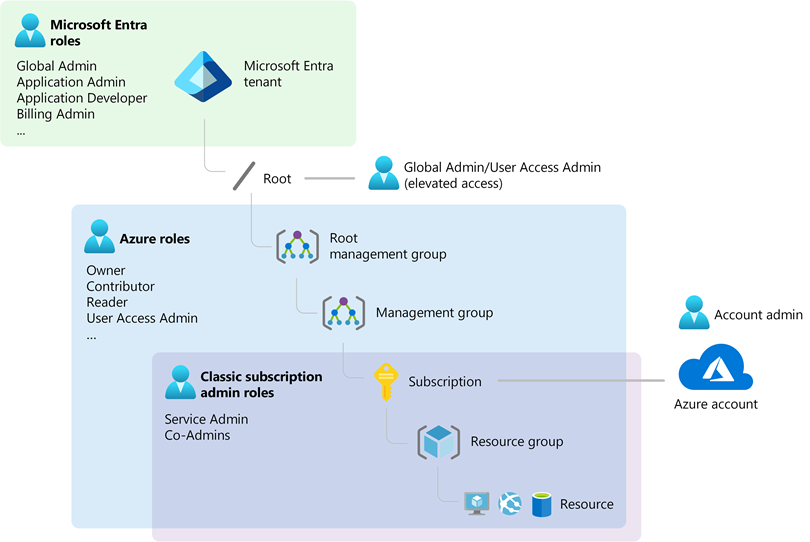
As a startup or an new customer exploring Microsoft Azure, you may find the terminology around identity and access management a bit perplexing. Terms like Tenant, Subscription, and Microsoft Entra ID, are crucial to understanding how to effectively manage and secure your Azure environment. This blog post aims to demystify these concepts and provide a clear, concise understanding of how they interrelate.

What is Microsoft Entra ID (Former Azure Active Directory)?
Microsoft Entra ID is the new name for Azure Active Directory (AAD), Microsoft’s cloud-based identity and access management service. It plays a crucial role in managing user, group, and application access to Azure services. Here’s a breakdown:
- Identity Management: Entra ID handles both authentication (verifying identity) and authorization (granting access) for Azure resources.
- Cloud-Based: Unlike traditional Active Directory, which is designed for on-premises environments, Entra ID operates entirely in the cloud, making it ideal for modern, cloud-first organizations.
Key Features:
- User and Group Management: You can create users and groups within your Entra ID tenant. These identities can be synchronized with your existing on-premises Active Directory using Entra Connect.
- Single Sign-On (SSO): Provides a seamless sign-on experience across multiple applications and services.
What is an Azure Tenant?
An Azure Tenant represents a dedicated instance of Microsoft Entra ID for your organization. It is essentially your organization’s space in the Azure cloud where you manage your identities and access.
Key Points:
- Created Automatically: When you sign up for Azure or any Microsoft cloud service, a tenant is automatically created.
- Domain Representation: By default, your tenant will have a domain like
yourcompany.onmicrosoft.com, which can be customized to use your own domain. (You can also add and replace your on.microsoft.com fallback domain)
What is an Azure Subscription?
An Azure Subscription is a logical container used to provision and manage Azure resources. It is closely tied to billing and acts as a boundary for resource management and deployment.
Key Characteristics:
- Resource Management: All Azure resources (e.g., virtual machines, databases) are associated with a subscription.
- Billing: Each subscription has its own billing cycle and payment terms, allowing you to manage costs effectively.
- Scalability: Best practice is to have separate subscriptions for production and non-production environments to manage permissions and scalability efficiently.
Relation to Tenant:
How They Work Together
Automatic Creation of Emtra ID Tenant:
- When you create an Azure subscription, an Entra ID tenant is automatically provisioned. This tenant manages identities and access within your subscription.
Authentication and Authorization:
- Azure subscriptions rely on Entra ID to authenticate and authorize users, services, and devices, ensuring that only authenticated identities can access Azure resources.
Role-Based Access Control (RBAC):
Multi-Subscription Management:
- A single Entra ID tenant can manage multiple subscriptions, enabling the same set of users and groups to access different environments. However, each subscription is associated with only one tenant.
Practical Tips for Startups
Benefit from the Azure setup Guide:
- Before you start building and deploying solutions by using Azure services, you need to prepare your environment. In this guide, we introduce features that help you organize resources, control costs, and secure and manage your organization. You can access it directly from the Azure Portal too.
Start with a Clear Structure:
- Separate Subscriptions: Use separate subscriptions for production and non-production environments to ensure better management and segregation of resources.
- Define Roles: Clearly define and assign Azure Roles and Entra ID Roles to manage permissions effectively.
Synchronize Identities:
- If you have an existing on-premises AD, use Entra Connect to synchronize identities with Entra ID, ensuring seamless access management.
Plan for Scalability:
- Design your subscription architecture to accommodate growth. Consider factors like billing, resource limits, and administrative boundaries.
Use Enterprise Scale Landing Zones:
- Implement recommended modular design to ensure your Azure environment can scale efficiently with your business needs.
Follow the links below if you are familiar with AWS and would like to understand how to map AWS concepts to Azure:
Conclusion
Understanding Microsoft Entra ID, Azure Subscriptions, and Tenants is essential for effective Azure governance. These concepts form the backbone of identity and access management in Azure, ensuring secure, scalable, and efficient management of your cloud resources. As your startup grows, mastering these basics will help you optimize your Azure environment, supporting your journey towards innovation and success.
For more detailed information, always refer to the latest Microsoft Azure documentation and best practices.
by Contributed | May 29, 2024 | Technology
This article is contributed. See the original author and article here.
Zero Trust has become the industry standard for safeguarding your entire digital estate. Central to Zero Trust is securing identity and access, which is essential for protecting resources, enforcing security policies, and ensuring compliance in today’s dynamic digital landscape.
With Microsoft Entra, we help our customers create a trust fabric that securely connects any trustworthy identity with anything, anywhere. Driven by the adoption of multicloud strategies in the era of AI, customers are encountering more challenges in securing access, not just across multiple public and private clouds, but also for business apps and on-premises resources. Unlike securing access for humans or within a single environment, where customers have established methods to address challenges, securing access anywhere is more complicated due to the dynamic nature of today’s digital estate and tools to address emerging challenges need further development. To support our customers, we unveiled our vision for securing access in any cloud at this year’s RSA conference. Today, we’re excited to dive deeper into our future investment aimed at securing access to cloud resources from any identity across diverse cloud environments.
Managing multicloud complexity in a rapidly evolving digital environment
Organizations are grappling with substantial challenges in navigating cloud access complexities, often citing issues like fragmented role-based access control (RBAC) systems, and compliance violations. These challenges are compounded by the growing use of cloud services from various cloud service providers. There have been links to several notable breaches attributed to over-permissioned identities. Our customer engagements reveal that organizations are currently using 7 to 8 products, including privileged access management (PAM) and identity governance and administration (IGA) solutions to tackle multicloud access challenges. Despite their efforts, such as toggling across multiple solutions and increasing their workforce, many organizations still struggle to achieve full visibility into their cloud access.
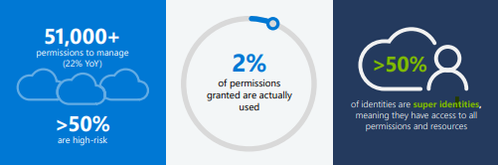
Our 2024 State of Multicloud Security Risk Report underscores these ongoing challenges arising from over-permissioned human and workload identities. Analysis of past year usage data from Microsoft Entra Permissions Management confirms that the complexities in multicloud environments primarily stem from rapid identity growth and over-provisioned permissions (learn more), including:
- Over 51,000 permissions that can be granted to identities – 50% of which are identified as high-risk permissions.
- Only 2% of those 51,000 permissions were used.
- Of the 209M identities discovered, more than 50% are identified as super identities that have all permissions to access all resources.
 Figure 1: 2024 State of Multicloud Security Risk key findings
Figure 1: 2024 State of Multicloud Security Risk key findings
Introducing our vision for cloud access management: Building a converged platform
Today, I’m excited to expand on our vision for cloud access management.
As businesses expand, organizations inevitably face challenges of overprovisioning at various levels. Initially, this manifests as granting more access to accommodate growing teams and workloads and can lead to overlapping access privileges. To address these issues, organizations must proactively identify vulnerabilities in identities and permissions and respond swiftly and, eventually, automatically. There’s a pressing need for a new solution that empowers all identities to access resources in any cloud securely while adhering to least-privileged permissions.
To address this critical need, we’re developing a converged platform that encompasses a comprehensive set of capabilities. This upcoming platform is designed to streamline the journey from risk discovery to remediation for secure access to any cloud resource whenever deviations occur, offering:
- Visibility: Gain insights into all identities and permissions assigned and used and detect risky permissions.
- Risk remediation: Remediate risky permissions with recommendations.
- Granular controls: Grant the right privileges for role-specific durations.
- Automated governance: Implement continuous compliance through automated policies.
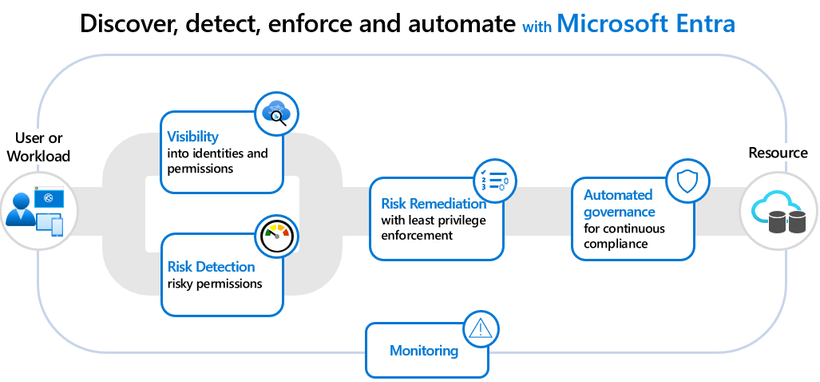 Figure 2: How to secure access from any identity across multiple clouds
Figure 2: How to secure access from any identity across multiple clouds
Our journey to secure access to resources in any cloud is advancing by building upon our industry-leading Microsoft Entra products:
- Permissions Management (CIEM) for delivering visibility into identities, permissions, and usage.
- Privileged Identity Management (PAM) for enforcing least-privileged controls for both human and workload identities.
- ID Governance (IGA) for automating identity lifecycle and access workflows regardless of origin or usage.
- Workload ID (IAM for workloads) for offering customized authorization policies for workload identities.
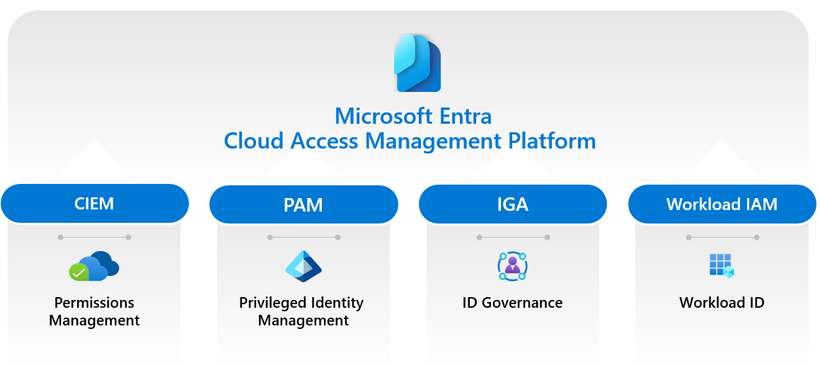 Figure 3: Convergence of four critical areas
Figure 3: Convergence of four critical areas
Additionally, as part of our continuous Copilot journey, we’re leveraging AI/ML to enhance all the technologies within the cloud access management platform. This enables organizations to uncover risks that are otherwise challenging to detect manually, identify the most significant risks, propose impactful remediations, and recommend usage-based custom roles and policies for any identity as the platform adoption grows. It will help simplify cloud access management and provide more effective ways to secure cloud environments for organizations.
Our commitment
At Microsoft, we’re committed to bringing this vision to life for our customers through the advancement and innovation of our newly converged platform, designed to secure access to resources in any cloud. Additionally, this vision extends to securing access to resources anywhere, including on-premises and business apps. Our goal is to help our customers enhance their security for any access to any resource in the era of AI and robust workload identities.
We look forward to collaborating with the community to realize this vision, empowering every organization to implement least-privileged access and permissions across all identities in multicloud and hybrid environments. We’ll keep you posted on our progress towards this vision. Until our next update, we invite you to explore our products that form the foundation of our cloud access management vision. Learn more about Microsoft Entra ID Governance and Permissions Management.
Thank you,
Joseph Dadzie
Partner Director of Product Management
LinkedIn
Twitter
Read more on this topic
Learn more about Microsoft Entra
Prevent identity attacks, ensure least privilege access, unify access controls, and improve the experience for users with comprehensive identity and network access solutions across on-premises and clouds.


Recent Comments