Cisco Releases Security Updates for Multiple Products
This article is contributed. See the original author and article here.
This article is contributed. See the original author and article here.

This article was originally posted by the FTC. See the original article here.
 Over the past year, the Coronavirus created financial problems for many people. Maybe you’re one of them. As you work to regain your financial footing, scammers will continue to try to steer you off course. Here are a few ways to spot, stop, and report payment scams.
Over the past year, the Coronavirus created financial problems for many people. Maybe you’re one of them. As you work to regain your financial footing, scammers will continue to try to steer you off course. Here are a few ways to spot, stop, and report payment scams.
Learn more about the financial impact of the Coronavirus. If you or someone you know lost money to a scammer, check out some quick steps to try and recover it. And if you’ve spotted a scam, tell the FTC at ReportFraud.ftc.gov.
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.
Microsoft Mesh is a new service that allows your enterprise and your social media to go far together, allowing users and customers to interconnect using a web-enabled mesh. This new internet-based service combines the advantages of social networking and collaboration together with business tools like enterprise mobility management, collaboration, and task management for a really multi-dimensional experience on the internet. Microsoft Mesh also enables groups to work together not just inside the scope of a project but also when creating tasks shared. It follows that group real-time and productivity tasks can be handled in exactly the same fashion across multiple network devices.
Multi-user capabilities extend beyond networking. Microsoft Mesh offers rich editing and publishing experiences for e-commerce, publishing, collaboration, and publishing of all documents in addition to data. A multi-user network can include anywhere from 1 individual to several hundred consumers based on the size of your network. Since Microsoft Mesh is cross platform and cross apparatus capable, it delivers a special opportunity to leverage the capabilities of numerous devices and browsers across your corporate network without any additional investments in software or connection.
For companies looking for a new way to connect with their clients and strengthen their business ties, the usage of Microsoft Mesh is a clear way for moving your company ahead. Employing this cross-platform social network you can achieve a highly targeted audience over several devices while at the exact same time increasing your revenue. The price and complexity of integrating this system in your company should be no problem at all, letting you construct your organization and reach your goals easily. Mesh is a powerful tool and needs to be leveraged for the current generation of mobile computing.

This article was originally posted by the FTC. See the original article here.
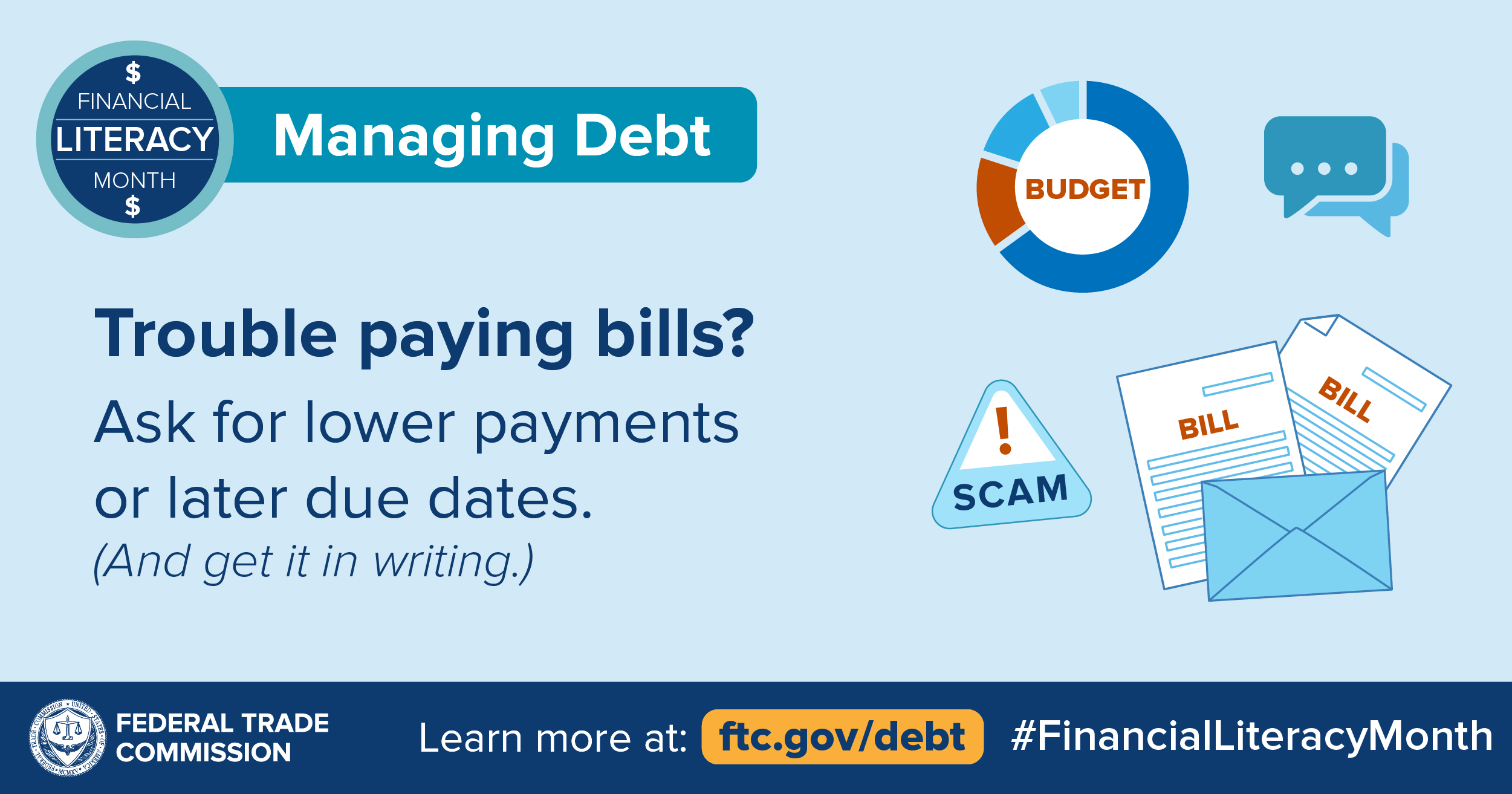
COVID-19 has thrown the economy into a tailspin. As people have been laid off, furloughed, or are working fewer hours, bills can pile up. This week, for Financial Literacy Month, we’re looking at ways to manage — and today, it’s all about dealing with debt. Here are some ideas to start regaining your financial footing when you have more month than money.
If you come across debt relief scams like these, we want to hear about it. Tell the FTC at ReportFraud.ftc.gov.
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.
This article is contributed. See the original author and article here.
SAP systems running outdated or misconfigured software are exposed to increased risks of malicious attacks. SAP applications help organizations manage critical business processes—such as enterprise resource planning, product lifecycle management, customer relationship management, and supply chain management.
On April 6 2021, security researchers from Onapsis, in coordination with SAP, released an alert detailing observed threat actor activity and techniques that could lead to full control of unsecured SAP applications. Impacted organizations could experience:
CISA recommends operators of SAP systems review the Onapsis Alert Active Cyberattacks on Mission-Critical SAP Applications for more information and apply necessary updates and mitigations.
See CISA’s previous alerts on SAP:
Recent Comments