by Scott Muniz | Nov 3, 2022 | Security, Technology
This article is contributed. See the original author and article here.
Apple has released a security update to address vulnerabilities in Xcode. A remote attacker could exploit one of these vulnerabilities to take control of an affected system.
The Cybersecurity and Infrastructure Security Agency (CISA) encourages users and administrators to review the Apple security page for Xcode 14.1 and apply the necessary update.
by Scott Muniz | Nov 3, 2022 | Security, Technology
This article is contributed. See the original author and article here.
CISA has released three (3) Industrial Control Systems (ICS) advisories on November 3, 2022. These advisories provide timely information about current security issues, vulnerabilities, and exploits surrounding ICS.
CISA encourages users and administrators to review the newly released ICS advisories for technical details and mitigations:
• ICSA-22-307-01 ETIC RAS
• ICSA-22-307-02 Nokia ASIK 5G AirScale System Module
• ICSA-22-307-03 Delta Industrial Automation DIALink
by Scott Muniz | Nov 3, 2022 | Security
This article was originally posted by the FTC. See the original article here.
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.
by Scott Muniz | Nov 2, 2022 | Security
This article was originally posted by the FTC. See the original article here.
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.
by Scott Muniz | Nov 1, 2022 | Security, Technology
This article is contributed. See the original author and article here.
OpenSSL has released a security advisory to address two vulnerabilities, CVE-2022-3602 and CVE-2022-3786, affecting OpenSSL versions 3.0.0 through 3.0.6.
Both CVE-2022-3602 and CVE-2022-3786 can cause a denial of service. According to OpenSSL, a cyber threat actor leveraging CVE-2022-3786, “can craft a malicious email address to overflow four attacker-controlled bytes on the stack. This buffer overflow could result in a crash (causing a denial of service) or potentially remote code execution,” allowing them to take control of an affected system.
CISA encourages users and administrators to review the OpenSSL advisory, blog, OpenSSL 3.0.7 announcement, and upgrade to OpenSSL 3.0.7. For additional information on affected products, see the 2022 OpenSSL vulnerability – CVE-2022-3602 GitHub repository, jointly maintained by the Netherland’s National Cyber Security Centrum (NCSC-NL) and CISA.
by Contributed | Nov 1, 2022 | Technology
This article is contributed. See the original author and article here.
Yammer is committed to strengthening the alignment of Yammer to Microsoft 365. This means we will no longer support tenants having more than one home Yammer network. This change will ensure Yammer networks have the same organizational boundaries as their corresponding M365 tenants. Integrating Yammer more fully into the Microsoft 365 ecosystem has been a multi-year effort and new networks created since October 2018 have not permitted this 1:Many configuration. Similarly, new Yammer networks provisioned after January 2020 have been created in Native Mode. In September 2022, the enforcement of Native Mode was announced. Automated network consolidation is an important prerequisite to reaching Native Mode and gaining access to broader safety, security, and compliance features. This will start on 5/1/2023 and continue through 5/1/2024.
Start the consolidation process
If you have secondary Yammer networks, you will lose access to all your secondary Yammer networks once you consolidate. Users from your secondary Yammer networks will be migrated to your primary network, but groups (communities) and data will be lost. In advance of this change, we strongly recommend that customers perform a full data export of their networks. You can read more about exporting data from your network here.
It is strongly advised that customers perform this network consolidation themselves. This will allow you to choose the time of the consolidation and allow the administrator to choose which primary domain will be associated with the remaining network.
Customers are encouraged to initiate network consolidation any time before or after 5/1/2023.
If you would like to self-initiate your network consolidation:
- There is a guide to network consolidation available to walk you through the process. A network administrator can run the network migration tool from within Yammer.
If you would like Microsoft to initiate your network consolidation:
- You are not required to take any action. Microsoft will notify you via the M365 Message Center of your scheduled consolidation date and default primary network and domain. The network with the highest total message count will be the default primary network.
- If you would like a different default primary network, contact Microsoft 365 support to log an exception.
If you need to postpone or schedule network consolidation around blackout dates:
- Contact Microsoft 365 support to log an exception.
What happens next?
Post consolidation of the networks into 1:1 alignment with Microsoft 365, they will be upgraded to Native Mode. This provides access to the latest features in Yammer and ensures that customers are covered by the Microsoft 365 compliance features.
You can read more about our plans to ensure alignment to Native Mode here.
Need more help?
There are Microsoft partners that can help you migrate data from your secondary networks. Please reach out to your Microsoft Account Team or contact a partner for more information.
FAQ
Q: We know which network we want to be our primary network. How can we make sure that our networks are automatically consolidated to that specific network?
A: Please contact support to specify your desired primary network and domain.
Q: We do not want our networks consolidated. What can we do?
A: Please contact support to request an exception, which will include sharing business justifications, when the consolidation can proceed, and your plan to unblock it. This is not a permanent exception.
Q: We consolidated our networks, but we want to reverse the process so we can have a different primary network. Is that possible?
A: No. Network consolidation is an irreversible process.
Step-by-step instructions for network consolidation
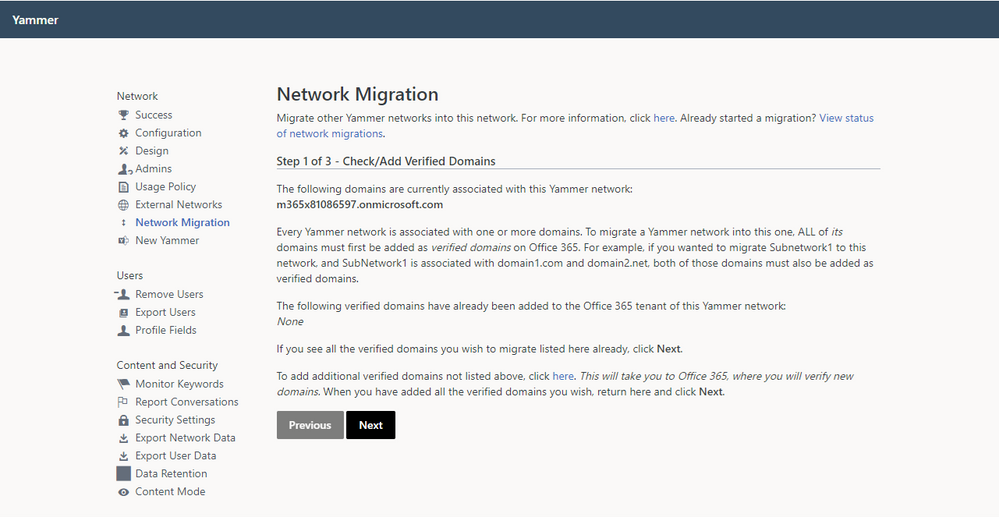
- As a network admin, visit the Network Migration page within the Yammer network admin settings of the primary network you want to keep. Make sure that all of the domains you wish to consolidate are listed. If they are not listed, you can follow the link to add and verify additional domains.

2. Choose the network you wish to consolidate, and click Next.
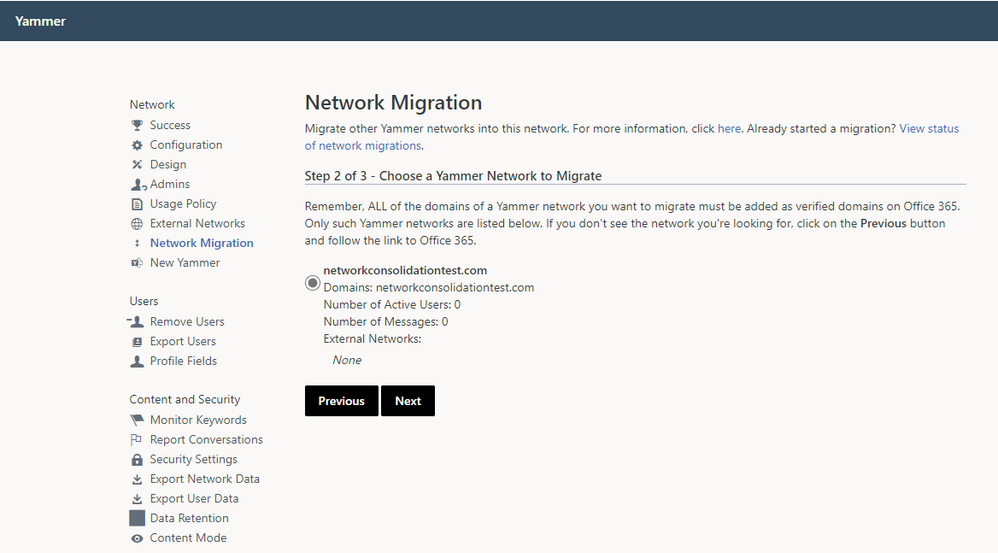
3. Validate that you are ready to consolidate the selected network and have performed any desired data export prior to consolidation.
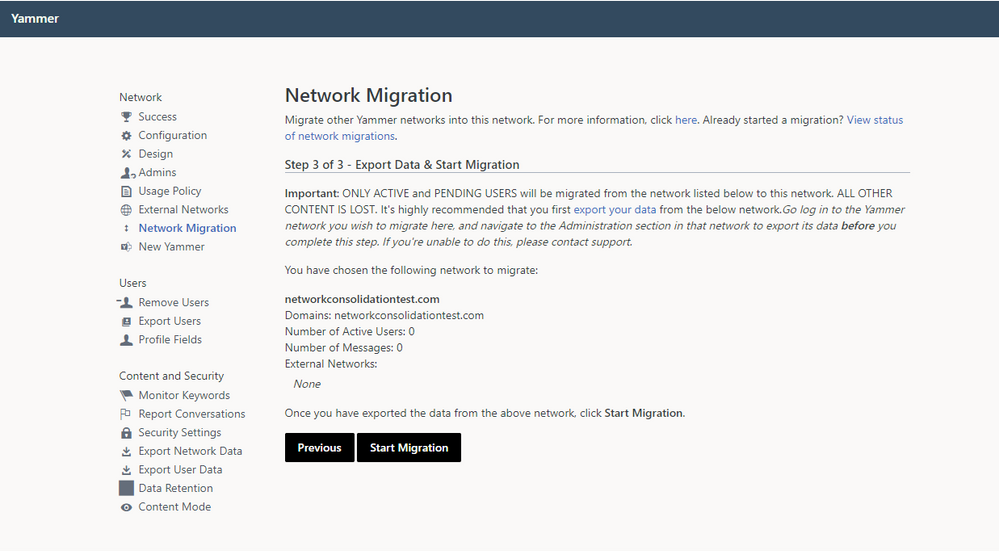
4. Follow the instructions to initiate network consolidation.
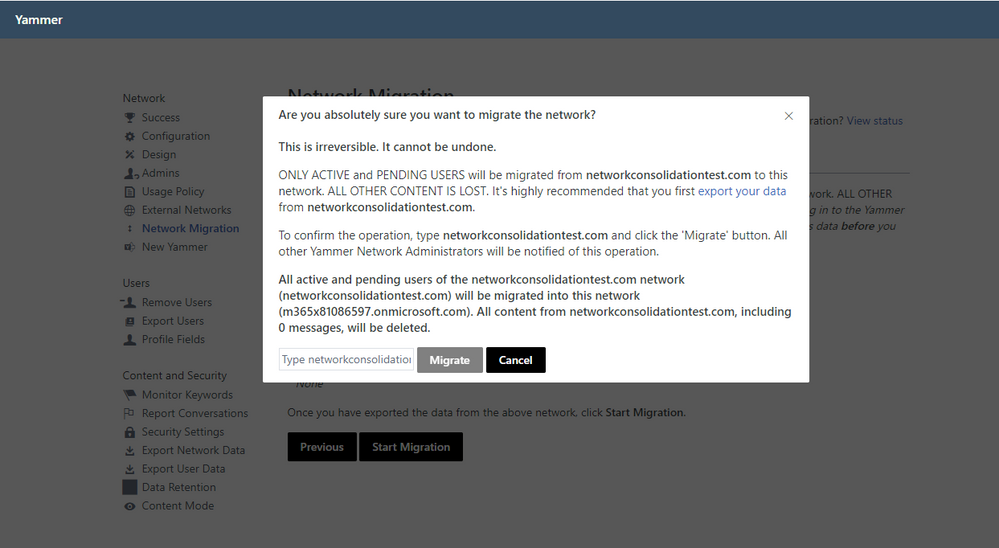
5. You can view the status of your network consolidation on the Network Migration page.
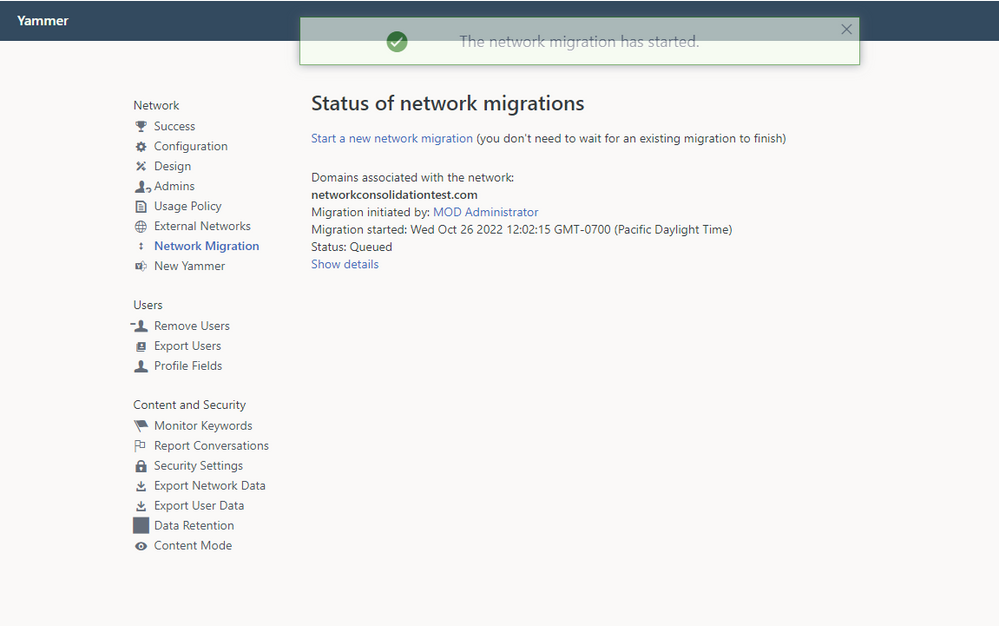
6. When the consolidation is complete, the status will update.
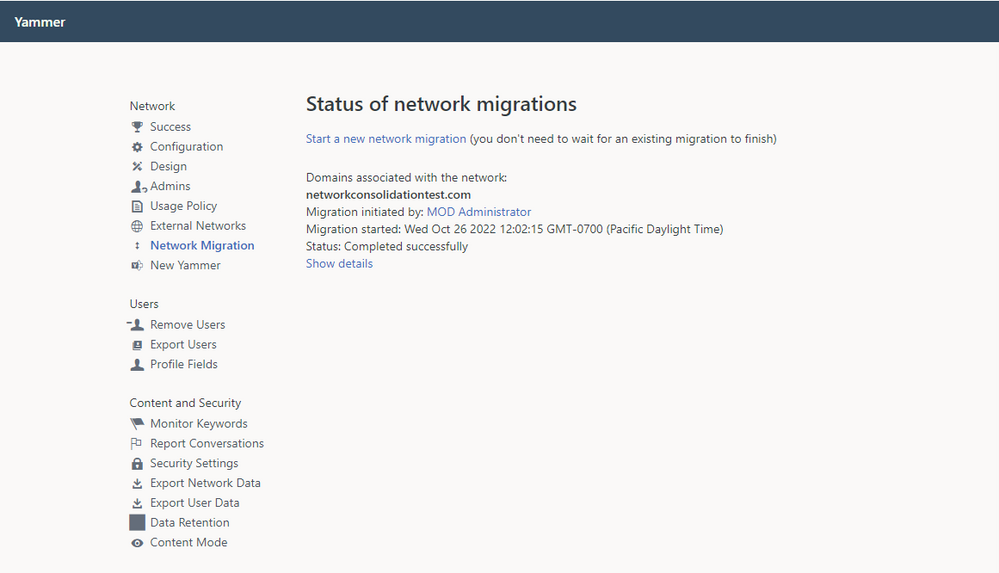
7. Repeat this process until you only have one network associated with your tenant. Congratulations! You are now ready to migrate to Native Mode.
by Scott Muniz | Nov 1, 2022 | Security, Technology
This article is contributed. See the original author and article here.
Today, CISA officially upgraded to Traffic Light Protocol (TLP) 2.0, which facilitates greater information sharing and collaboration. CISA made this upgrade in accordance with the recommendation from the Forum of Incident Response and Security Teams to upgrade to TLP 2.0 by January 2023.
Key TLP 2.0 updates:
- TLP 2.0 changes TLP:WHITE to TLP:CLEAR.
- TLP 2.0 adds the designation TLP:AMBER+STRICT, which instructs the recipient to keep the information strictly within their organization only.
Note: CISA’s Automated Indicator Sharing (AIS) capability will not update from TLP 1.0 to TLP 2.0 until March 2023. This exception includes AIS’s use of the following open standards: the Structured Threat Information Expression (STIX™) for cyber threat indicators and defensive measures information and the Trusted Automated Exchange of Intelligence Information (TAXII™) for machine-to-machine communications.
CISA encourage all individuals and organizations in the cybersecurity community to adopt TLP 2.0. For more information, see CISA’s TLP webpage, www.cisa.gov/tlp and FIRST’s TLP webpage, https://www.first.org/tlp/.
by Scott Muniz | Nov 1, 2022 | Security, Technology
This article is contributed. See the original author and article here.
CISA released one Industrial Control Systems (ICS) advisory on November 1, 2022. This advisory provides timely information about current security issues, vulnerabilities, and exploits surrounding ICS.
CISA encourages users and administrators to review the newly released ICS advisory for technical details and mitigations:

by Contributed | Oct 31, 2022 | Technology
This article is contributed. See the original author and article here.
Microsoft partners like Rubrik and Standss deliver transact-capable offers, which allow you to purchase directly from Azure Marketplace. Learn about these offers below:

|
Rubrik for Microsoft 365: Safeguard your enterprise data from insider threats or ransomware with Rubrik’s air-gapped, immutable, access-controlled backups, while continuously monitoring and remediating data risks. Rubrik Zero Trust Data Security for Microsoft 365 offers unprecedented simplicity and performance for search and restore operations for Microsoft Exchange Online, OneDrive, SharePoint, and Teams.
|

|
SendGuard for Outlook (Microsoft 365): Prevent accidental data disclosure and improve your compliance posture with SendGuard for Outlook. The software scans, detects, warns or blocks potentially sensitive, confidential or non-compliant emails and prevents them from reaching unintended recipients. It prompts Microsoft Outlook users to review and confirm both attachments and recipients before an email with confidential information can be sent.
.
|
by Scott Muniz | Oct 31, 2022 | Security, Technology
This article is contributed. See the original author and article here.
CISA has released two fact sheets to highlight threats against accounts and systems using certain forms of multifactor authentication (MFA). CISA strongly urges all organizations to implement phishing-resistant MFA to protect against phishing and other known cyber threats. If an organization using mobile push-notification-based MFA is unable to implement phishing-resistant MFA, CISA recommends using number matching to mitigate MFA fatigue. Although number matching is not as strong as phishing-resistant MFA, it is one of best interim mitigation for organizations who may not immediately be able to implement phishing-resistant MFA.
CISA recommends users and organizations see CISA fact sheets Implementing Phishing-Resistant MFA and Implementing Number Matching in MFA Applications. Visit CISA.gov/MFA for more information on MFA, including an infographic of the hierarchy of MFA options.


Recent Comments