Microsoft is named a Leader for Field Service Management
This article is contributed. See the original author and article here.
The past year has cultivated many personal and professional changes. No person or industry has been untouched. Even field service has embraced seismic changes as a result of the ongoing global pandemic. For many field service organizations, being dispatched to the customer’s location to diagnose and resolve an issue became more complex than ever before. In response, a shift began within field service to less hands-on, more remote, and more dynamic and proactive service operations.
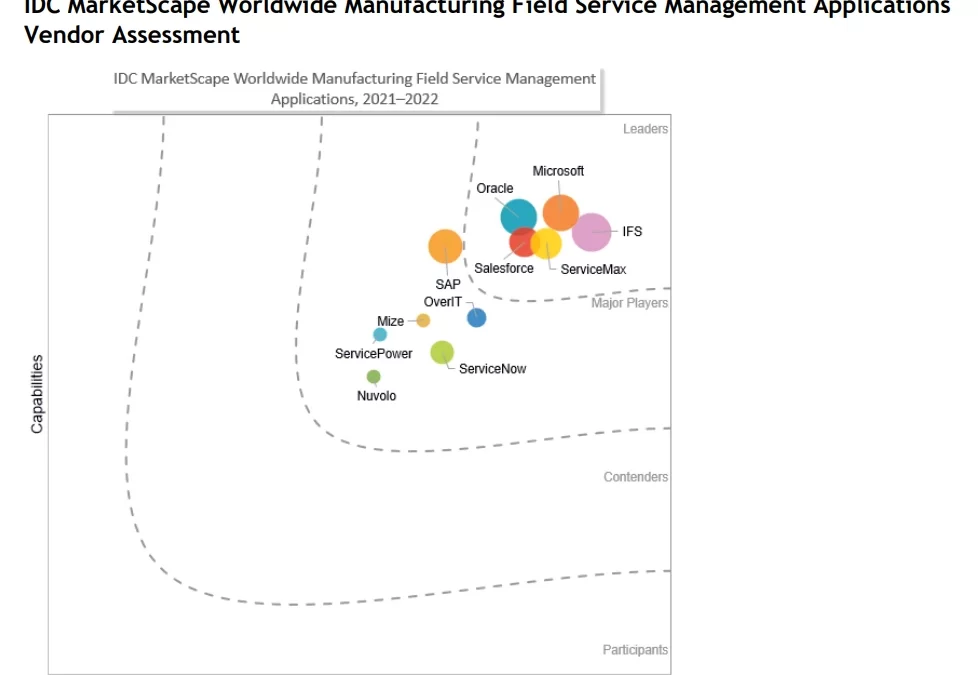
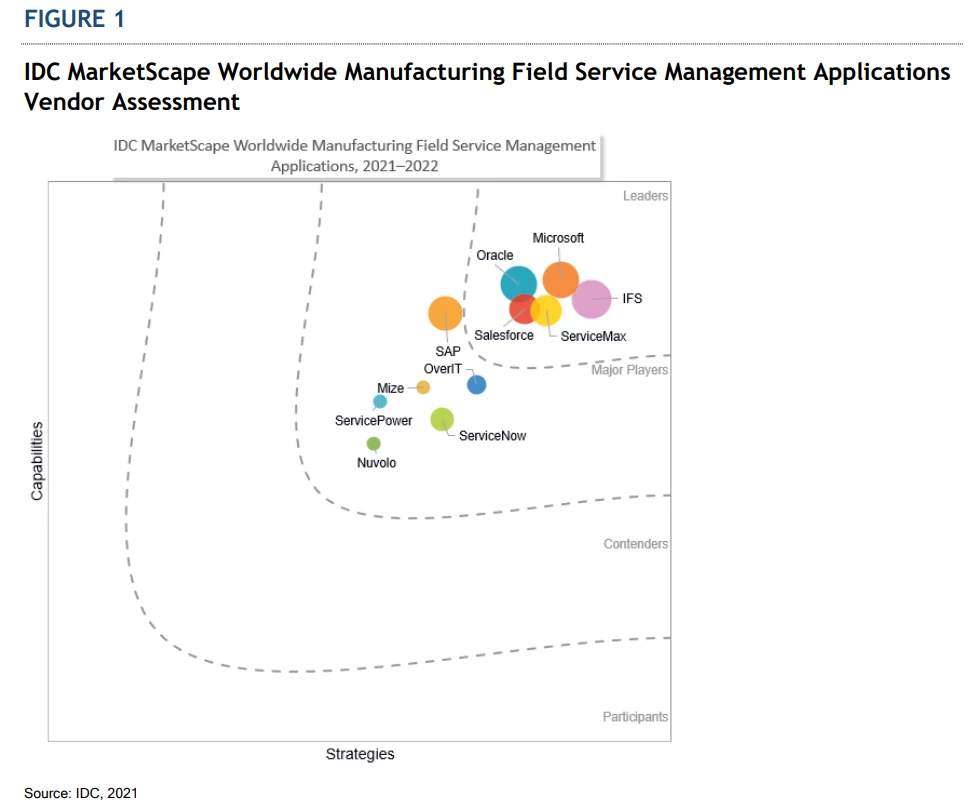
Yes, change is inevitable, and this transformative tidal wave of change within the field service arena has been for the betterfor the service organization, its personnel, and the customers it supports. It is with great pride I share with you our position as a Leader within the IDC MarketScape for the Worldwide Manufacturing Field Service Management Applications Vendor Assessment 2021-2022.
We believe this placement recognizes Microsoft’s continuous investment and authority across our service solution and cloud functionality.
Noted capabilities
IDC MarketScape objectively noted the strengths, challenges, and considerations of each vendor. For Microsoft, the IDC MarketScape noted one of our strengths as “The ability to deliver specific capabilities to support the market is critical to rapid adoption and ROI. Customer references also noted that Microsoft’s integration with other enterprise applications and technical capabilities of the application helped speed deployment and achieve value quickly.”
IDC MarketScape also noted “Microsoft’s primary challenge with regard to field service management is with regard to industry-specific innovations. Microsoft has established a culture of innovation around many of its products and highlights service-specific offerings, which demonstrate the future of field service collaboration and execution. However, manufacturers and some service organizations lag behind those in other industries, and companies like Microsoft will need to provide both transformative offerings and incremental innovations that closely align with the risk aversion of the specific subvertical industry.” Fortunately, Microsoft caters to everyone from the intrepid to the risk-averse with both transformative offerings and incremental innovations that closely align with the customer’s palatable level of risk.
The study advised “Manufacturers and service organizations should consider Microsoft when they are looking for an integrated field service product offering that can seamlessly integrate IoT data, remote collaboration, AI, and AR/mixed reality capabilities to enable more predictive and proactive service outcomes. The ability to collaborate in real time and have on-demand insights is transforming the way field service and support can be conducted. Microsoft is helping manufacturers that are on this journey around servitization and the convergence of AI, IoT, and AR in the field.”
And the transformation is occurring in real-time. Take for example, Burckhardt Compression, a global leader in manufacturing and servicing, headquartered in Switzerland. The company builds and services massive compressors weighing up to 240 tons, creating pressure three times higher than at the deepest point in the ocean. This high pressure transforms gas to a liquid state so it has less volume and is transported easier. If the compressor fails, the liquid turns back to gas and the build-up of pressure can be critical for the ship and the crew.
Because maintenance is so critical, Burckhardt Compression had to send a service engineer to wherever the compressor was locatedwhich was time-consuming, resource-intensive, and simply not scalable. To provide support at any location, Burckhardt Compression adopted Microsoft Dynamics 365 Field Service for field service management and Dynamics 365 Remote Assist, a mixed reality application. Now remote service engineers have access to real-time service data and can support the ship’s technicians by engaging in on-demand video chat, providing instruction augmented with a schematic overlay, and creating markups onscreen over the actual compressor. And a case is automatically created in Dynamics 365 Field Service when a call is initiated by Dynamics 365 Remote Assist, and a recording of the repair work is saved.
Burckhardt Compression is serving customers faster by eliminating travel time and sharing expert knowledge across the globe in a matter of minutes increasing trust, safety, and business continuity. Now the company is looking to expand to add non-Burckhardt compressors to its service roster, thereby expanding its market presence and generating additional revenue. Burckhardt Compression is just one of many manufacturing and servicing organizations that have reaped value by deploying Dynamics 365 Field Service and harnessing its capabilities to build stronger, more collaborative, and proactive service delivery.
The bottom line
Many service organizations consist of dispatchers answering service calls, putting customers on hold, asking the same questions repeatedly, while searching for the next available technician to dispatch. This process is inefficient, costly, and unsatisfying to the customer.
The world of field service is changing. Today, service organizations are evolving into profit centers, redefining business models, and creating powerful and fulfilling customer experiencesall supported by leading edge solutions like Dynamics 365 Field Service.
We’re excited to be positioned as an IDC MarketScape Leader and are committed to bringing you the best and most featured field service application available. Depend on the multidimensional capabilities of Dynamics 365 Field Service to help you better personalize customer engagements, improve employee effectiveness, and optimize service operations now and tomorrow.
This is where innovation meets what’s possible.
Read the IDC MarketScape: Worldwide Manufacturing Field Service Management Applications 2021-2022 Vendor Assessment excerpt.
Learn more about Dynamics 365 Field Service.
The post Microsoft is named a Leader for Field Service Management appeared first on Microsoft Dynamics 365 Blog.
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.

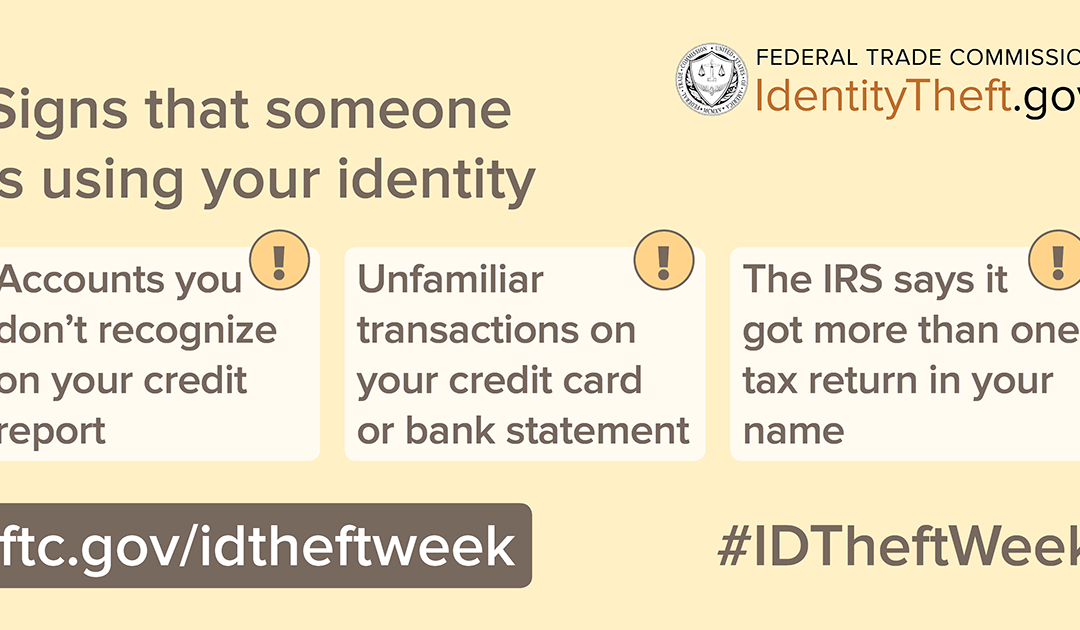
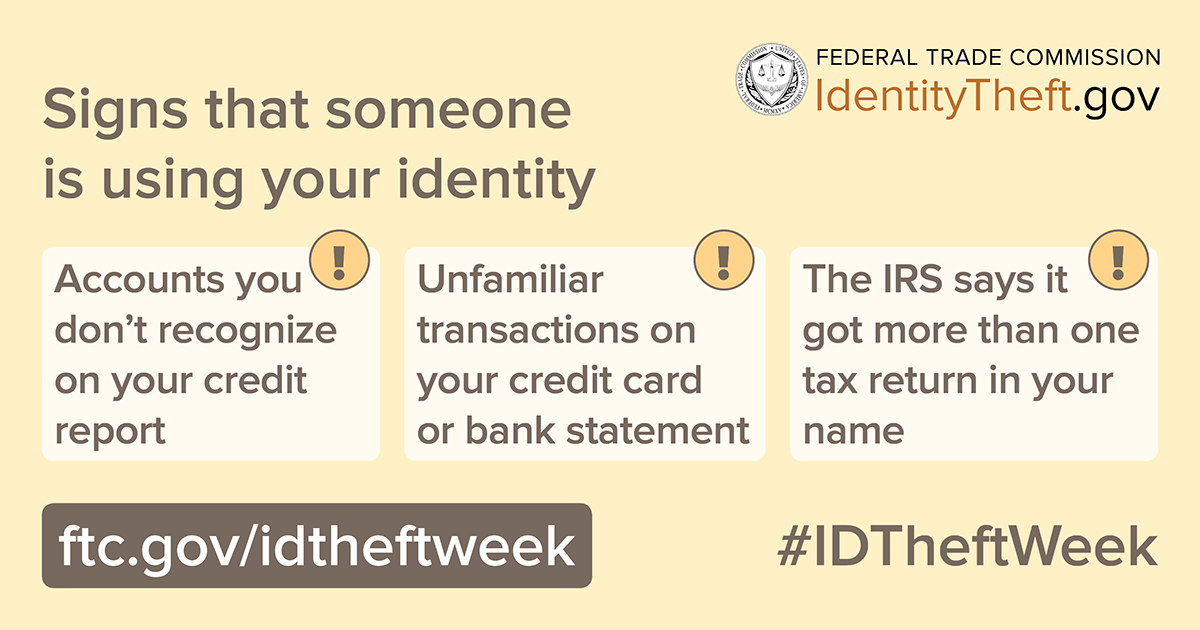


 It’s the second day of Identity Theft Awareness Week and today we’re talking about steps that can help reduce your risk of identity theft.
It’s the second day of Identity Theft Awareness Week and today we’re talking about steps that can help reduce your risk of identity theft.
Recent Comments