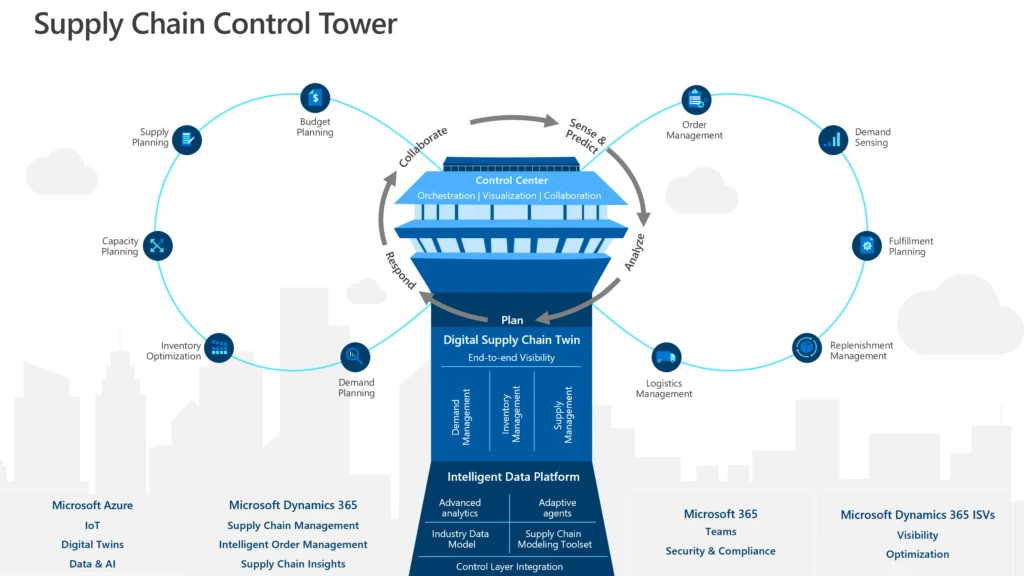
Dynamics 365 composable approach enables rapid deployment of a supply chain control tower
This article is contributed. See the original author and article here.
Delays, constraints, and disruptions are frequent challenges for global supply chains. And they are costly. According to Gartner 70 percent of supply chain leaders report that they have been constantly responding to disruptions since 2019.1 Supply chain professionals have long understood that the earlier potential disruptions and constraints are identified, the more successful the measures to adapt and overcome them can be. So, the question becomes, how do we identify disruptions and constraints at the earliest possible opportunity? The answer is real-time, end-to-end visibility across the supply chain, which is precisely what supply chain control towers provide.
While the benefits of supply chain control towers are easily understood, many organizations continue to struggle to make control towers a reality. The composable approach of Microsoft Dynamics 365 is changing this situation however, and providing organizations a path to rapid deployment of supply chain control towers. This article explains the composable approach and why it is an essential ingredient for success in supply chain control tower initiatives.
Learn more in our on-demand webinar: How to rapidly deploy a supply chain control tower with a composable approach.
The future leans towards composable solutions
The future of business applications is composable. We can see this in reports from analyst firms such as Gartner, who predict that “by 2023 organizations, that have adopted a composable approach will outpace their competition by 80 percent.”2 But, what is a composable approach? Before we delve into the composable approach and what makes it different, let’s briefly explore the evolution of enterprise resource planning (ERP) solutions as this will help us understand why composability is key to achieving end-to-end visibility.
The challenge of achieving end-to-end visibility
In the past, ERP systems were sold as one massive application. This meant that they were expensive and difficult to change. As these applications matured, vendors looked for ways to give customers greater flexibility. To provide this flexibility, business functions, like sales and supply chain, were increasingly offered as modular components such as customer relationships management (CRM) systems, warehouse management systems (WMS), transportation management systems (TMS), and supply chain management (SCM) systems. While modularity did provide flexibility, the flexibility itself created other problems, as we discuss next.
The main issue is that once business functions could select the components that best suited their needs, such as CRM or WMS, replacement and implementation of these systems often took place at different times, and systems were often from different vendors. Also, due to the possible differences in maturity levels and solution architectures of these disparate systems, they required time-consuming and expensive custom development to achieve end-to-end integration across the enterprise. And after integration, end-to-end performance was often plagued by latency, synchronization, and data unification issues. This is the situation where many companies find themselves today and it is the primary reason that achieving real-time end-to-end visibility of the supply chain has been so elusive.
Microservices are composable
Technology vendors began offering business solutions assembled application experiences built on microservices architectures in the continuing drive to improve customer applications. Whereas in the past, a specific business function, like warehouse or sales, would select the right system for their needs, such as CRM or WMS, businesses can now choose solutions tailored to individual workloads. For example, a simple order management workload could be composed by bringing together order orchestration, fulfillment, and inventory.
These microservices, such as real-time inventory and fulfillment, not only provide greater flexibility, but because they easily connect to other microservice applications and utilize API-driven messaging, data and actions can be pulled and pushed between different systemsdecreasing latency, improving synchronization, and enabling real-time end-to-end visibility in the process. This is why a composable approach makes the rapid deployment of a supply chain control tower possible.
Our vision
Gartner predicts that by 2026, 80 percent of companies will suffer significant value loss due to failure to merge their digital supply twin and control tower initiatives.3 We agree. And, our solutions help companies avoid this outcome by providing a composable approach that makes merging these initiatives possible.
At Microsoft, we see supply chain control towers as a shared service process that can be composed from a mix of supply chain workloads. For example, a supply chain control tower and digital twin can be built using Dynamics 365 Supply Chain Management, Dynamics 365 Intelligent Order Management, Dynamics 365 Supply Chain Insightspreview together with Microsoft Power Platform, and our growing digital supply chain applications ecosystem.

Dynamics 365 Intelligent Order Management is often a great place to start when building a supply chain control tower in a retail, distribution, or direct-to-consumer (DTC) manufacturing business. This is because Dynamics 365 Intelligent Order Management is built on a microservice architecture that includes rules-based order orchestration and fulfillment, real-time inventory, and AI. As such, it is step-forward to the composable approach that allows companies to achieve the real-time end-to-end visibility of a supply chain control tower. The composability of the solution also means that organizations can get up running quickly and maximize the benefit of existing investments through easy integration with existing legacy ERP systems.
What’s next
Supply chain control towers that include Dynamics 365 Intelligent Order Management positions organizations to respond faster and more intelligently to disruptions and opportunities. Dynamics 365 Intelligent Order Management works seamlessly with any ERP and CRM system. It is also a stand-alone application that allows customers to start their control tower initiative without dependencies on other Dynamics 365 solutions. It integrates seamlessly with many market-leading API-enabled applications, using our out-of-the-box pre-built connectors to order intake sources, tax calculation, and third-party logistics partners ecosystem. Moreover, it automates and optimizes fulfillment using AI and real-time omnichannel inventory data. Supply chain and commerce professionals can proactively overcome disruptions through quickly order flows reconfigurations with drag and drop actions in a low-code/no-code interface. And by enabling them with all these capabilities, help them accelerate their order management digital transformation and turn order fulfillment into a competitive advantage.
Learn more in the on-demand webinar: How to rapidly deploy a supply chain control Tower with a Composable Approach.
Sources:
- Gartner, Hype Cycle for Supply Chain Strategy 2021, September 14, 2021.
- Gartner, Composable Commerce Must Be Adopted for the Future of Applications, June 18, 2020.
- Gartner, Predicts 2022: Supply Chain Technology, November 17, 2021.
GARTNER is the registered trademark and service mark of Gartner Inc., and/or its affiliates in the U.S. and internationally and has been used herein with permission. All rights reserved.
The post Dynamics 365 composable approach enables rapid deployment of a supply chain control tower appeared first on Microsoft Dynamics 365 Blog.
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.




 Today we’re kicking off Identity Theft Awareness Week 2022. Identity thieves have been busier than ever during the pandemic, with scammers and identity thieves after people’s information to apply for credit, unemployment benefits, file taxes, buy things, or get medical services. But there are some things you can do to protect yourself, and this week, you’ll learn how.
Today we’re kicking off Identity Theft Awareness Week 2022. Identity thieves have been busier than ever during the pandemic, with scammers and identity thieves after people’s information to apply for credit, unemployment benefits, file taxes, buy things, or get medical services. But there are some things you can do to protect yourself, and this week, you’ll learn how.

Recent Comments