This article is contributed. See the original author and article here.
A few weeks ago, I was asked to talk about Azure Security Center in a virtual full-day security workshop. After my session, I got some great feedback from attendees, and from this feedback, I realized that I had touched a topic during my talk which made attendees think and which seems to be more or less unknown or unclear to many of our customers. This is why I decided to write this article to shine some light on Azure Secure Score and Azure governance.
Azure Security Center is a Cloud Security Posture Management (CSPM) and Cloud Workload Protection Platform (CWPP) solution, with Secure Score being one of the main features in the CSPM stack. The idea behind Secure Score is to give customers a comprehensive and unified overview of their cloud environments’ current security postures.
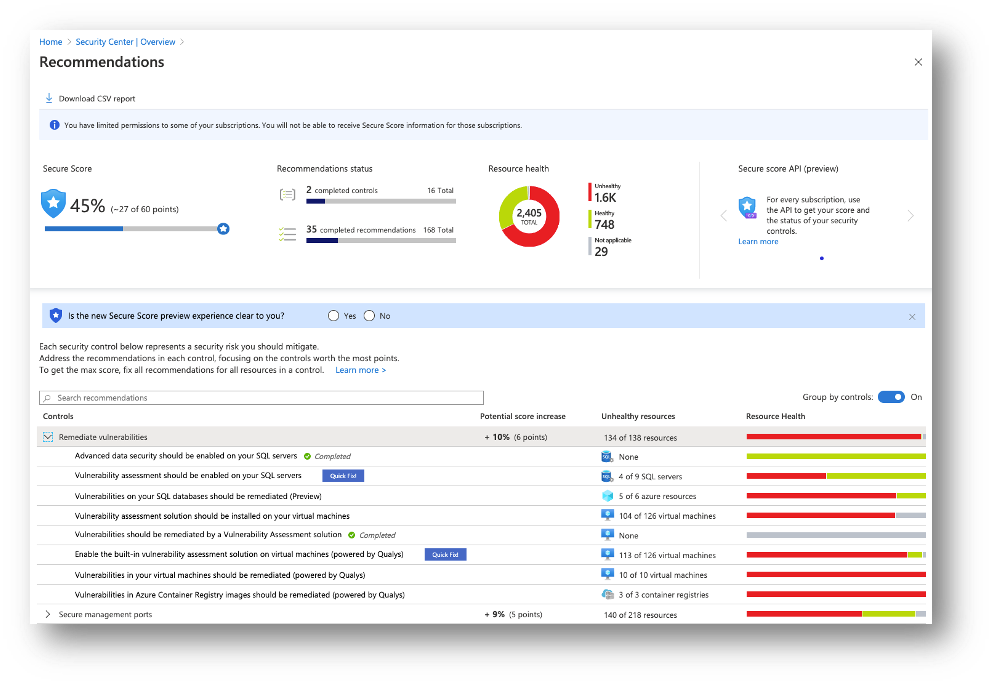
Secure Score is based on recommendations which reflect industry standard and Microsoft security best-practices, such as the recommendations to enable MFA or to secure management ports. Recommendations are logically grouped in security controls. For more information about how Secure Score works, read Enhanced secure score in Azure Security Center.
The overall Secure Score in the example shown in Figure 1 is 45%. The first security control Remediate vulnerabilities contains several recommendations, some of which already have been completed for all resources in the given scope. In order to increase the Secure Score, not one recommendation needs to be completed for all resources, but all recommendations need to be completed for all flagged resources.. If all recommendations under the security control are remediated, your Secure Score increases by the value that is shown in the respective security control. This is because we want Secure Score to give customers valid and useful information without claiming security improvements which are not really secure. For example, if you would complete our recommendation to install an endpoint protection solution on a VM but then would not resolve health issues with this solution (which is a second recommendation), increasing the Secure Score would lead to a misassumption regarding the actual security posture of that workload.
How does secure score influence your governance?
Now that you understand Secure Score calculations from a high-level perspective, let’s take a look at what can influence Secure Scores over time. Of course, the goal is to increase your Secure Score because that means that your security posture has enhanced alongside. At the same time, the higher the Secure Score gets, the fewer recommendations will be left, making it easier to plan for remediation. The diagram shown in Figure 2 has an example of a secure score that is improving over time.
Figure 2 – Secure Score improvement over time
There are many strategies to continue driving the secure score up, I recommend you to read the Secure Score Survival Guide in order to understand some of these strategies.
Once you have invested time and effort in increasing your Secure Score, you want to make sure that it will not decrease by a serious percentage, again. The problem is that the remediation is always done for existing resources, not for new ones. For example, if you grant an Azure AD account write access to an Azure subscription without enabling it for MFA, or if you create new Azure VMs without making sure that their management ports are protected, or if you create new storage accounts without enabling secure transfer; your Secure Score will drop once you provision new resources which are not secure by default.
Figure 3 – Secure Score drops after resource creation
This is when Azure Governance comes into play. With Azure Policy you can make sure that only resources that adhere to your security principles and recommendations can be deployed, and with Azure Blueprints, you have a great tool to enable quick and repeatable creation of fully governed Azure environments. Furthermore, Blueprints enable you to ensure compliance and empower DevOps.
That said, every time you remediate a particular security recommendation or the entire security control, you need to make sure that this remediation also reflects in your deployment scenarios. Whatever recommendation you remediate, make sure to change your ARM templates and PowerShell deployment scripts accordingly. This way, you make sure that you will only deploy resources which are secure by default.
In large environments, remediation at scale is one of the most important aspects when it comes to leveraging Azure Security Center. No one wants to manually take care of 20,000 storage accounts and 2,300 VMs across 1,500 subscriptions. Azure Policy definitions, Logic App Playbooks, and PowerShell scripts are some immensely powerful tools within this context. With DINE (deploy-if-not-exist) policies, you can make sure that all resources in the affected scope will automatically be remediated (depending on the recommendation). When new resources are deployed, the respective policy will automatically make sure that the security recommendations will be met just after deployment. With PowerShell scripts, you can remediate existing resources, and with Logic App Playbooks, you can react on triggers, such as recurrence, or events, or you can directly run them from the recommendation in Azure Security Center. In our GitHub community, we have published a number of remediation scripts and templates which you can leverage for your environments.
Secure Score over time
Today, Secure Score reflects your current security posture at a given point in time. We have recently released the Secure Score API in public preview, which enables you to export and store your Secure Score at any time. As an example, we have published a LogicApp playbook on our Azure Security Center GitHub community, which will pull your Secure Score, controls, and assessments into an EventHub every 24 hours. This information can then be used for example to create custom PowerBI dashboards or be integrated into your own dashboards to show a Secure Score trend over time. You can also read this great post that shows how to operationalize the Secure Score API to send weekly briefings via email.
Takeaways
As you see, Azure Governance is an important part of security and should always be part of your strategy to enhance your security posture. We recommend our customers to leverage Secure Score as a great tool to determine their current security state and to use the Secure Score API to build a trending view that helps them understand where they came from and what they have already achieved on their journey to security. We also encourage you to join our GitHub community, and use the tools and scripts we have published. If you miss something, let us know, or create some artifacts by yourself which then can be added to the repository.
Thanks for reading and best regards,
Tom Janetscheck,
Senior Program Manager – CxE ASC Team
This post was reviewed by @Yuri Diogenes, Senior Program Manager – CxE ASC Team
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.


Recent Comments