This article is contributed. See the original author and article here.
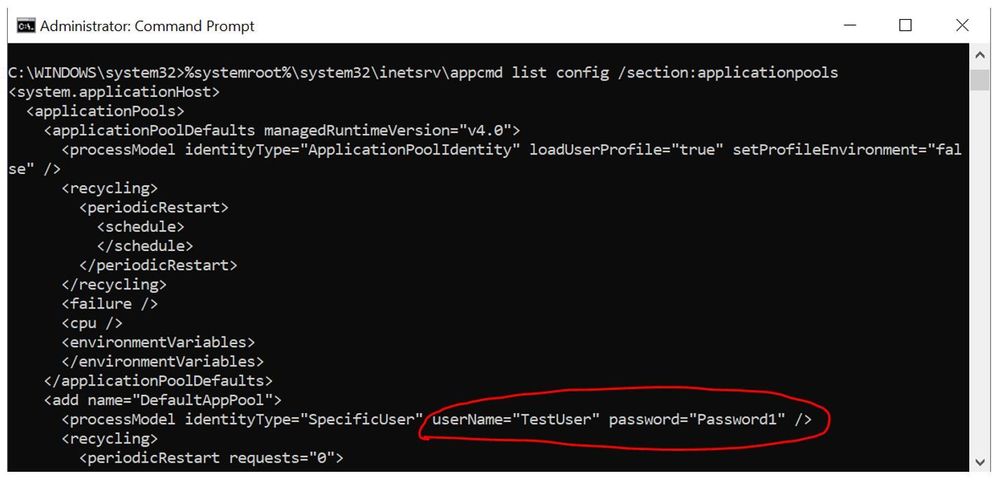
In IIS Manager, the application pool identity set to a custom service account will always display it’s password in encrypted (masked) format. In applicationHost.config file also the password will show as encrypted.
But when you run the below command in a command line tool then the password is visible.
%systemroot%system32inetsrvappcmd list config /section:applicationpools
 Is there a way to encrypt the password in the command line?
Is there a way to encrypt the password in the command line?
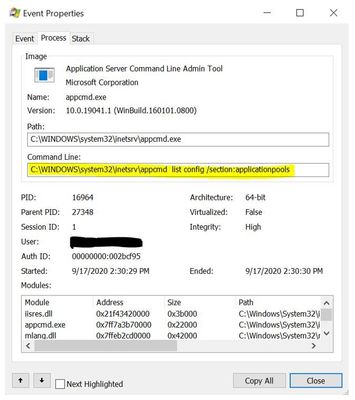
The AppCmd tool uses the same interfaces to read the configuration data that the Windows Process Activation Service uses to read the same configuration data.
Sample dll stack: (Collected using Procmon)
| AppCmd tool |
Windows Process Activation Service |
|
0 ntoskrnl.exe SeOpenObjectAuditAlarmWithTransaction + 0x4ad8 0xfffff8064bed03c8 C:WINDOWSsystem32ntoskrnl.exe
1 ntoskrnl.exe SeOpenObjectAuditAlarmWithTransaction + 0x16ac 0xfffff8064beccf9c C:WINDOWSsystem32ntoskrnl.exe
2 ntoskrnl.exe SeOpenObjectAuditAlarmWithTransaction + 0x57ee 0xfffff8064bed10de C:WINDOWSsystem32ntoskrnl.exe
3 ntoskrnl.exe ObOpenObjectByNameEx + 0x1fa 0xfffff8064beda39a C:WINDOWSsystem32ntoskrnl.exe
4 ntoskrnl.exe ObOpenObjectByName + 0x5c 0xfffff8064beda17c C:WINDOWSsystem32ntoskrnl.exe
5 ntoskrnl.exe SeQueryInformationToken + 0xcf1 0xfffff8064bed9ca1 C:WINDOWSsystem32ntoskrnl.exe
6 ntoskrnl.exe NtFsControlFile + 0x582 0xfffff8064be4f2a2 C:WINDOWSsystem32ntoskrnl.exe
7 ntoskrnl.exe setjmpex + 0x7cc5 0xfffff8064bc058b5 C:WINDOWSsystem32ntoskrnl.exe
8 ntdll.dll ZwOpenKey + 0x14 0x7ffed2cac004 C:WindowsSystem32ntdll.dll
9 bcryptprimitives.dll ProcessPrng + 0x3b5c 0x7ffed08285ec C:WindowsSystem32bcryptprimitives.dll
10 bcryptprimitives.dll ProcessPrng + 0x39dd 0x7ffed082846d C:WindowsSystem32bcryptprimitives.dll
11 bcryptprimitives.dll ProcessPrng + 0x3934 0x7ffed08283c4 C:WindowsSystem32bcryptprimitives.dll
12 bcryptprimitives.dll GetKeyDerivationInterface + 0x13b3e 0x7ffed08474de C:WindowsSystem32bcryptprimitives.dll
13 ntdll.dll RtlActivateActivationContextUnsafeFast + 0x11d 0x7ffed2c47b3d C:WindowsSystem32ntdll.dll
14 ntdll.dll RtlGetThreadErrorMode + 0x313 0x7ffed2c73403 C:WindowsSystem32ntdll.dll
15 ntdll.dll RtlGetThreadErrorMode + 0xa6 0x7ffed2c73196 C:WindowsSystem32ntdll.dll
16 ntdll.dll TpAllocTimer + 0x1c3 0x7ffed2c50d13 C:WindowsSystem32ntdll.dll
17 ntdll.dll LdrGetDllHandleEx + 0x4f6 0x7ffed2c44ca6 C:WindowsSystem32ntdll.dll
18 ntdll.dll ApiSetQueryApiSetPresenceEx + 0x5a4 0x7ffed2c4c414 C:WindowsSystem32ntdll.dll
19 ntdll.dll RtlDosPathNameToRelativeNtPathName_U + 0xd2 0x7ffed2c4c612 C:WindowsSystem32ntdll.dll
20 ntdll.dll RtlVirtualUnwind + 0xae7 0x7ffed2c32b97 C:WindowsSystem32ntdll.dll
21 ntdll.dll LdrResolveDelayLoadedAPI + 0xc6 0x7ffed2c44196 C:WindowsSystem32ntdll.dll
22 rpcrt4.dll RpcErrorGetNextRecord + 0x242 0x7ffed2b04572 C:WindowsSystem32rpcrt4.dll
23 rpcrt4.dll I_RpcServerSetAddressChangeFn + 0xc71 0x7ffed2b11c81 C:WindowsSystem32rpcrt4.dll
24 rpcrt4.dll UuidCreate + 0x15 0x7ffed2af6945 C:WindowsSystem32rpcrt4.dll
25 combase.dll CoInitializeEx + 0x1688 0x7ffed2132588 C:WindowsSystem32combase.dll
26 combase.dll CoInitializeEx + 0xdf3 0x7ffed2131cf3 C:WindowsSystem32combase.dll
27 combase.dll CoInitializeEx + 0xd95 0x7ffed2131c95 C:WindowsSystem32combase.dll
28 combase.dll CoInitializeEx + 0x750 0x7ffed2131650 C:WindowsSystem32combase.dll
29 combase.dll RoGetActivatableClassRegistration + 0x45ca 0x7ffed213080a C:WindowsSystem32combase.dll
30 combase.dll CoInitializeEx + 0x268 0x7ffed2131168 C:WindowsSystem32combase.dll
31 combase.dll CoInitializeEx + 0x58 0x7ffed2130f58 C:WindowsSystem32combase.dll
32 appcmd.exe CLockBase<4,1,1,2,3,3>::LockType + 0x1898 0x7ff7a3b75758 C:WindowsSystem32inetsrvappcmd.exe
33 appcmd.exe STRAU::SafeCopy + 0x58d 0x7ff7a3b81f4d C:WindowsSystem32inetsrvappcmd.exe
34 kernel32.dll BaseThreadInitThunk + 0x14 0x7ffed14b6fd4 C:WindowsSystem32kernel32.dll
35 ntdll.dll RtlUserThreadStart + 0x21 0x7ffed2c5cec1 C:WindowsSystem32ntdll.dll
|
0 ntoskrnl.exe SeOpenObjectAuditAlarmWithTransaction + 0x4ad8 0xfffff8064bed03c8 C:WINDOWSsystem32ntoskrnl.exe
1 ntoskrnl.exe SeOpenObjectAuditAlarmWithTransaction + 0x16ac 0xfffff8064beccf9c C:WINDOWSsystem32ntoskrnl.exe
2 ntoskrnl.exe SeOpenObjectAuditAlarmWithTransaction + 0x57ee 0xfffff8064bed10de C:WINDOWSsystem32ntoskrnl.exe
3 ntoskrnl.exe ObOpenObjectByNameEx + 0x1fa 0xfffff8064beda39a C:WINDOWSsystem32ntoskrnl.exe
4 ntoskrnl.exe ObOpenObjectByName + 0x5c 0xfffff8064beda17c C:WINDOWSsystem32ntoskrnl.exe
5 ntoskrnl.exe SeQueryInformationToken + 0xcf1 0xfffff8064bed9ca1 C:WINDOWSsystem32ntoskrnl.exe
6 ntoskrnl.exe NtFsControlFile + 0x582 0xfffff8064be4f2a2 C:WINDOWSsystem32ntoskrnl.exe
7 ntoskrnl.exe setjmpex + 0x7cc5 0xfffff8064bc058b5 C:WINDOWSsystem32ntoskrnl.exe
8 ntdll.dll ZwOpenKey + 0x14 0x7ffed2cac004 C:WindowsSystem32ntdll.dll
9 bcryptprimitives.dll ProcessPrng + 0x3b5c 0x7ffed08285ec C:WindowsSystem32bcryptprimitives.dll
10 bcryptprimitives.dll ProcessPrng + 0x39dd 0x7ffed082846d C:WindowsSystem32bcryptprimitives.dll
11 bcryptprimitives.dll ProcessPrng + 0x3934 0x7ffed08283c4 C:WindowsSystem32bcryptprimitives.dll
12 bcryptprimitives.dll GetKeyDerivationInterface + 0x13b3e 0x7ffed08474de C:WindowsSystem32bcryptprimitives.dll
13 ntdll.dll RtlActivateActivationContextUnsafeFast + 0x11d 0x7ffed2c47b3d C:WindowsSystem32ntdll.dll
14 ntdll.dll RtlGetThreadErrorMode + 0x313 0x7ffed2c73403 C:WindowsSystem32ntdll.dll
15 ntdll.dll RtlGetThreadErrorMode + 0xa6 0x7ffed2c73196 C:WindowsSystem32ntdll.dll
16 ntdll.dll TpAllocTimer + 0x1c3 0x7ffed2c50d13 C:WindowsSystem32ntdll.dll
17 ntdll.dll LdrGetDllHandleEx + 0x4f6 0x7ffed2c44ca6 C:WindowsSystem32ntdll.dll
18 ntdll.dll ApiSetQueryApiSetPresenceEx + 0x5a4 0x7ffed2c4c414 C:WindowsSystem32ntdll.dll
19 ntdll.dll RtlDosPathNameToRelativeNtPathName_U + 0xd2 0x7ffed2c4c612 C:WindowsSystem32ntdll.dll
20 ntdll.dll RtlVirtualUnwind + 0xae7 0x7ffed2c32b97 C:WindowsSystem32ntdll.dll
21 ntdll.dll LdrResolveDelayLoadedAPI + 0xc6 0x7ffed2c44196 C:WindowsSystem32ntdll.dll
22 rpcrt4.dll RpcErrorGetNextRecord + 0x242 0x7ffed2b04572 C:WindowsSystem32rpcrt4.dll
23 rpcrt4.dll I_RpcServerSetAddressChangeFn + 0xc71 0x7ffed2b11c81 C:WindowsSystem32rpcrt4.dll
24 rpcrt4.dll UuidCreate + 0x15 0x7ffed2af6945 C:WindowsSystem32rpcrt4.dll
25 combase.dll CoInitializeEx + 0x1688 0x7ffed2132588 C:WindowsSystem32combase.dll
26 combase.dll CoInitializeEx + 0xdf3 0x7ffed2131cf3 C:WindowsSystem32combase.dll
27 combase.dll CoInitializeEx + 0xd95 0x7ffed2131c95 C:WindowsSystem32combase.dll
28 combase.dll CoInitializeEx + 0x750 0x7ffed2131650 C:WindowsSystem32combase.dll
29 combase.dll RoGetActivatableClassRegistration + 0x45ca 0x7ffed213080a C:WindowsSystem32combase.dll
30 combase.dll CoInitializeEx + 0x268 0x7ffed2131168 C:WindowsSystem32combase.dll
31 combase.dll CoInitializeEx + 0x58 0x7ffed2130f58 C:WindowsSystem32combase.dll
32 w3wp.exe w3wp.exe + 0x12dd 0x7ff6b36012dd C:WindowsSystem32inetsrvw3wp.exe
33 w3wp.exe w3wp.exe + 0x363d 0x7ff6b360363d C:WindowsSystem32inetsrvw3wp.exe
34 kernel32.dll BaseThreadInitThunk + 0x14 0x7ffed14b6fd4 C:WindowsSystem32kernel32.dll
35 ntdll.dll RtlUserThreadStart + 0x21 0x7ffed2c5cec1 C:WindowsSystem32ntdll.dll
|
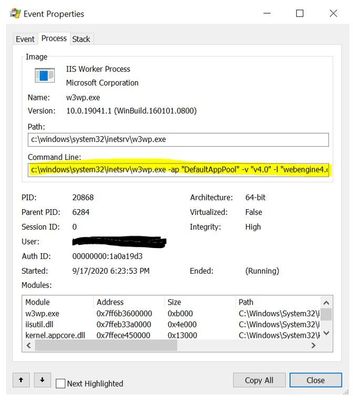
At some point we have to decrypt the password to hand it off to LSA to log in the account and both WAS and AppCmd can do this, but it is dependent on running as either Local System or a local administrator.
If we run the same command using an account that is not a local administrator, it will fail.
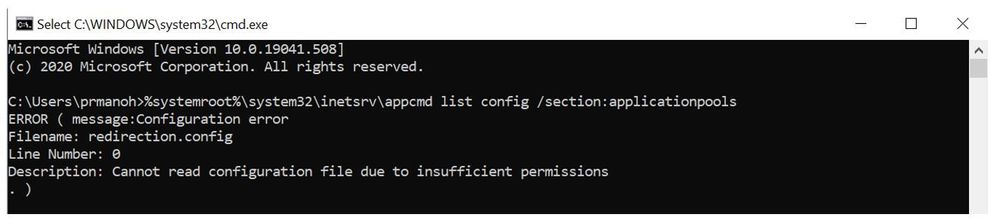 By design, it is architecturally infeasible to prevent an administrator from being able to read the password in this manner.
By design, it is architecturally infeasible to prevent an administrator from being able to read the password in this manner.
AppCmd is an IIS admin tool that requires admin privilege to run. Therefore, showing the password doesn’t break the security boundary. On the other hand, if the goal is to prevent “peeking over the shoulder” or “leaking password from the admin script logs”, it might be helpful to have a switch for the command line to mask the passwords. Unfortunately, such an option was never added.
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.

By design, it is architecturally infeasible to prevent an administrator from being able to read the password in this manner.


Recent Comments