This article is contributed. See the original author and article here.
By Masaki Iwamaru – Service Engineer | Microsoft Endpoint Manager – Intune
Box for EMM is an app for the iOS platform developed by Box Inc. The Box for EMM app is intended for enterprise customers with mobile device management (MDM) solutions such as Microsoft Endpoint Manager – Microsoft Intune. The app provides secure access to data in Box cloud storage workspace with iOS devices.
When you integrate Box for EMM app with Intune, you can apply app protection policies (APP). This will enable the data protection features of the app built with the Intune App SDK. You can control data transfer between apps, restrict copy-paste between apps, set access requirements, and force conditional launch settings.
This blog post provides you a step-by-step guide on integrating Box for EMM app with Intune.
Note
There is a separate Box app that can be used for both personal and enterprise use. This article focuses on the Box for EMM app, which has supported Intune since 2015. Both the Box for EMM and Box app can access the same cloud storage space provided by the Box EMM Enterprise workspace.
Steps to integrate Box for EMM with Intune
Step 1. Add and deploy Box for EMM app to your employees.
Deploy the app using Intune. If end users install Box for EMM from the App Store and you haven’t deployed it to users or devices, they will not be able to sign-in to the app because the required app configuration policy is not applicable (see step 2).
To add Box for EMM to Intune:
- Sign into the Microsoft Endpoint Manager admin center.
- Go to Apps > iOS/iPadOS.
- Select + Add, choose iOS store app from the dropdown list, and then Select.
- Select Search the App Store and enter Box for EMM.
- Select to add the app to Intune.
After you add the app to Intune, deploy it by assigning the app to users and devices. Learn more about deploying apps in this article.
Tip
You can also deploy the Box for EMM app that’s purchased through the Apple Volume Purchasing Program (VPP).
Step 2. Create and deploy an app configuration policy.
This is a required configuration for the Box for EMM app. Otherwise end users won’t be able to sign into the app.
- Go to Apps > App configuration policies to create an app configuration policy.
- Select + Add and choose Managed devices from the list.
Note
Be aware you need to create and deploy an app configuration policy using a managed device. Managed apps won’t work for the Box for EMM app. - Enter a policy name in Name and choose iOS/iPadOS from the Platform list.
- For Targeted app, Select app, and then choose Box for EMM from the list.
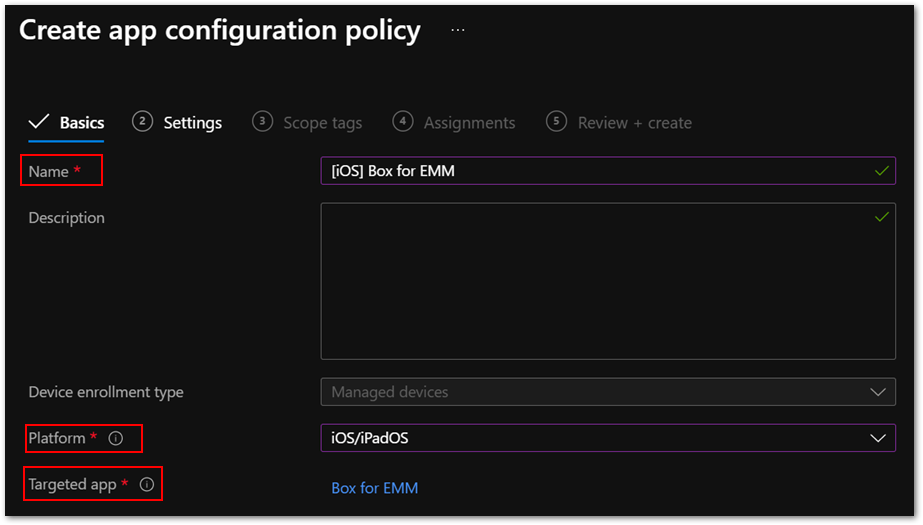 Figure 1. Box for EMM policy in the Microsoft Endpoint Manager admin center
Figure 1. Box for EMM policy in the Microsoft Endpoint Manager admin center
Go to the Settings tab.
Choose Use configuration designer from the Configuration settings format list and specify the following values from the XML property list.
Configuration key
Value type
Configuration value
Public ID
String
<The value provided by Box.com>
Management ID
String
AnyString
Intune Enterprise
String
1
com.box.mdm.oneTimeToken
String
AnyString
userprincipalname
String
{{userprincipalname}}
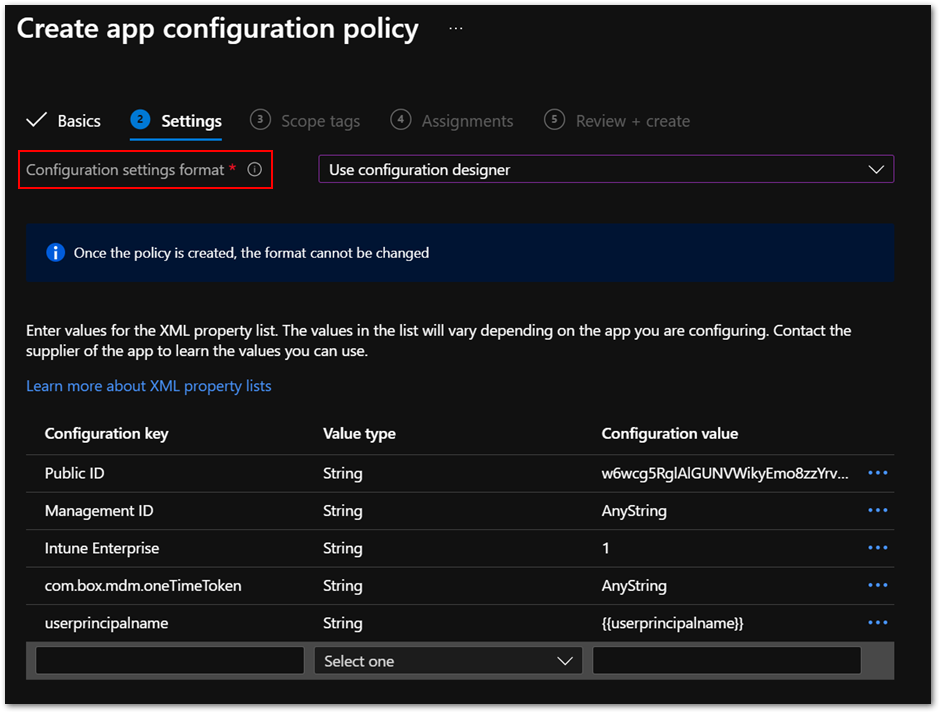 Figure 2. App configuration policy settings
Figure 2. App configuration policy settings
- Then deploy the policy to users and devices. These assignments are usually identical to the ones for the Box for EMM app.
Step 3. Create and deploy an app protection policy (APP) for the Box for EMM app.
You can create a new app protection policy for iOS and iPad operating systems (OS) or use an existing one. Here are a few best practices:
- Make sure that the Box for EMM app is included in the Targeted apps list of the policy.
- Set Target to apps on all device types to Yes in app protection policies to avoid misconfigurations. If you set it to No, you might need to deploy the IntuneMAMUPN key. This often overlooked by administrators, so I recommend setting it to Yes.
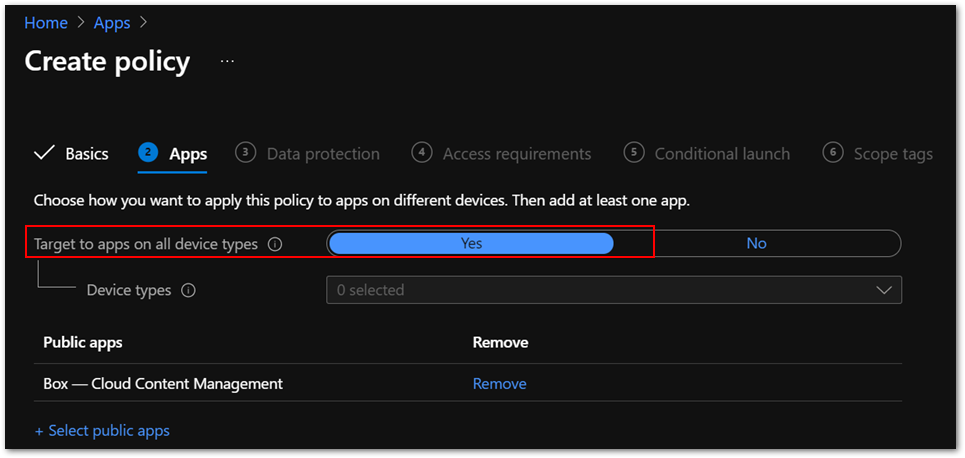 Figure 3. App configuration policy settings
Figure 3. App configuration policy settings - Make sure the policy is assigned to the correct users. App protection policies should be assigned to users instead of devices.
Step 4. install the Box for EMM app to iOS/iPadOS using Intune.
Make sure both the app and the app configuration policy are deployed. You can check deployment status in the Microsoft Endpoint Manager admin center.
Step 5. Launch the Box for EMM app.
You will see the Microsoft Azure Active Directory (Azure AD) sign-in screen. The user name is automatically populated. It should be the same as the user who enrolled the device. Enter the password for the user and app protection policy will be applied. Then you will see an app restart request.
Step 6. Relaunch the app.
When you relaunch the app, it might ask you to set an app PIN. Then you will see a login screen for the Box for EMM app. Sign in with your Box account. Now you can use the app with Intune app protection.
Frequently asked questions (FAQs)
In summary, here are common issues to be aware of when you’re integrating Box for EMM app with Intune:
The Box for EMM app is not installed on iOS devices.
Make sure you assigned the app to the correct groups. You can check app installation status in Device install status in each app or Managed Apps in each device.
If you use VPP for app deployment, make sure the VPP token is valid, and you have enough app licenses.
App configuration policy for Box for EMM app shows Not applicable.
Ensure that the Box for EMM app is installed using Intune instead of the App Store.
Check that the app configuration policy targets the Box for EMM app that you are deploying. Sometimes it targets the incorrect applicationID of the same app name because you have multiple Box for EMM apps in the Microsoft Endpoint Manager admin center or you have deleted and re-added the app.
Note
The app configuration policy type should be Managed devices instead of Managed apps.
App protection policy is not applied after sign-in.
Make sure the policy is assigned to correct users. App protection policy should be assigned to users instead of devices.
Be sure that Target to apps on all device types is set to Yes.
It can take time for the policy to be applied if end users are signed-in to the app before the policy assignment. This article provides more information about expected policy delivery timing.
How can I get Public ID for my Box tenant?
Public ID is provided by Box, Inc. for your tenant. Contact Box support for this information
- Should I set up single sign-on (SSO) between Azure AD and Box service?
You can use Box for EMM features without SSO integration. While it is optional, SSO provides a simplified and excellent user experience. Check out this article to learn about SSO integration guidance.
I want to allow access with Box for EMM app only while blocking personal Box app.
You can use the iOS device restriction profile to hide and disable the Box for EMM app. The Show or hide apps setting is applicable only to supervised iOS devices.
There is also a setting for enabling and disabling Official Box Apps in Box Admin Console – Apps.
I want to disable Files app functionality on iOS devices to prevent unintended file sharing.
Intune doesn’t have this setting. There is a setting for disabling Files app functionality in Box Admin Console – Enterprise Settings – Mobile.
Are there recommended settings for the Box for EMM app?
The following recommended settings allow end users to open, modify, and save files directly in Box storage with Microsoft Office applications.
Setting name
Value
Send Org data to other apps
Policy managed apps with OS sharing
Receive data from other apps
All Apps with incoming Org Data
Save copies of Org data
Block
Allow user to save copies to selected services
Select locations you want to save org data into
We also recommend adding the following key/value pair in the app configuration policy.
Key
Value (is you’re using Intune as the MDM)
IntuneMAMUPN
{{UserPrincipalName}}
The actual value specified for the IntuneMAMUPN key depends on the MDM provider you are using. You can find examples of the value you should enter for a third-party MDM provider in this article.
More info and feedback
For further resources on this subject, please see the links below.
iOS/iPadOS app protection policy settings
Validate your app protection policy setup
Create and deploy app protection policies
Set up app protection policies for iOS devices
Let us know if you have any questions by replying to this post or reaching out to @IntuneSuppTeam on Twitter.
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.


Recent Comments