This article is contributed. See the original author and article here.
Hopefully, you have read my previous blog posts about Azure Purview access management Part 1 and Part 2 to find about Azure Purview control plane and data plane roles and tasks. In this post, I will cover the following topic:
- Overview of dashboards and roles required to extend your M365 Sensitivity Labels to Azure Purview.
By extending M365 Sensitivity Labels to Azure Purview you can automatically assign labels to files and database columns in Azure Purview.
In order to bring Sensitivity Labels from M365 to Azure Purview, you may need to work with other teams in your organization. The following table summarizes tasks, required to extend the labels to Azure Purview including dashboards and roles required to perform each step:
Task | What portal to use | Who can perform this task |
Verify if you have at least one M365 E5 License in your Azure AD tenant | Azure Portal (https://portal.azure.com/) OR M365 Admin Center (https://admin.microsoft.com/AdminPortal/) | Any Azure AD role (e.g. Global Reader) |
Consent “Extend labeling to assets in Azure Purview” | Microsoft 365 Security and Compliance Center (http://compliance.microsoft.com/) | Azure AD Roles: Compliance Administrator OR Global Administrator |
Create and update Sensitivity Labels in M365 | Microsoft 365 Security and Compliance Center | Azure AD Roles: Azure Information Protection Administrator OR Global Administrator |
Register Data Sources in Azure Purview | Azure Purview Studio (https://web.purview.azure.com/) | Azure Purview Roles (data plane:( Purview Data Source Administrator + Purview Data Curator AND Azure Roles (control plane) Reader (on data sources) |
Scan Data Sources in Azure Purview | Azure Purview Studio | Azure Purview Roles (data plane): Purview Data Source Administrator + Purview Data Curator OR Purview Data Source Administrator + Purview Data Reader |
Search Catalog and filter assets based on Sensitivity Labels | Azure Purview Studio | Azure Purview Roles (data plane): Purview Data Reader OR Purview Data Curator |
View Sensitivity Labels Insights reports | Azure Purview Studio | Purview Data Reader OR Purview Data Curator |
Verify if you have at least one M365 E5 License in your Azure AD tenant
Use your M365 Admin center to check if you already have M365 E5 Licenses in your tenant:
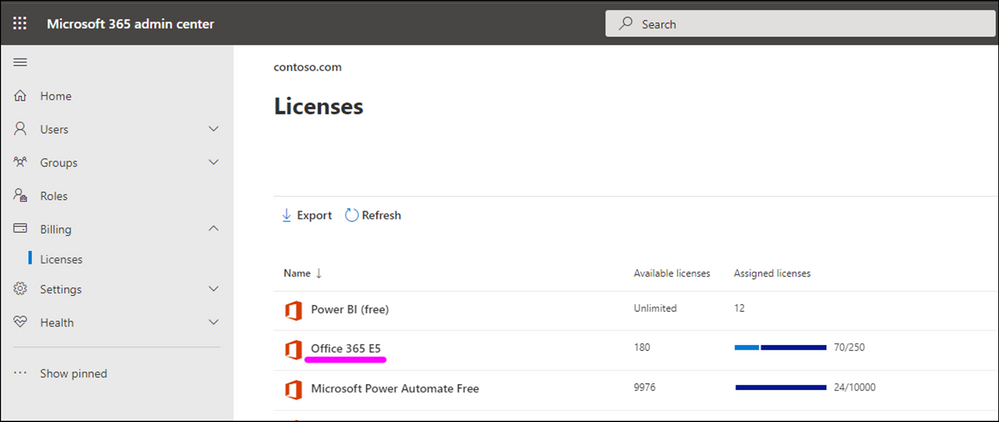
If you do not have this license in place, please work with your finance team to obtain the required licenses. Microsoft 365 E5 | Microsoft 365 Enterprise.
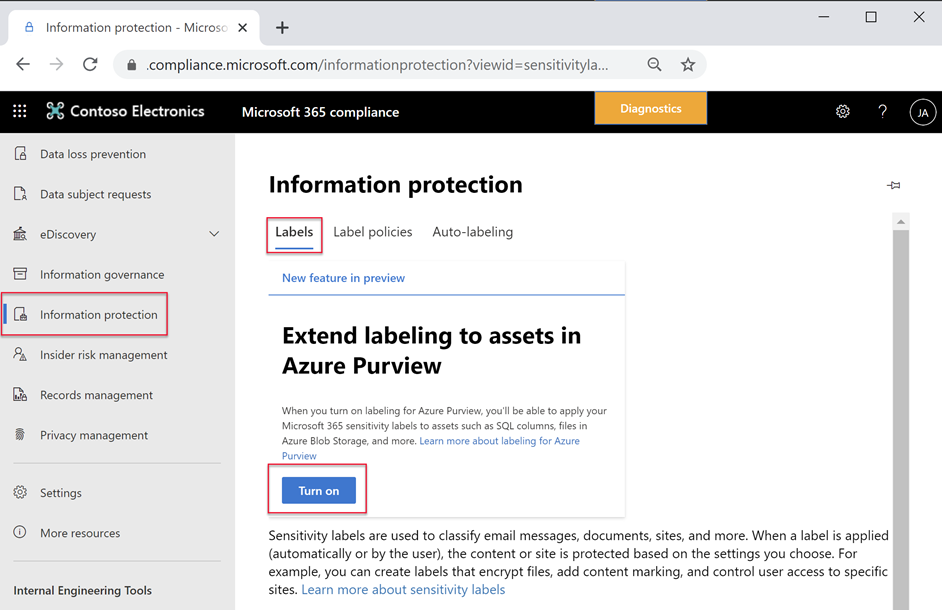
Consent “Extend labeling to assets in Azure Purview”.
By default, Sensitivity Labels are only available for assets in M365. With this one-time operation at your Azure AD tenant level, you will allow M365 Sensitivity Labels to be extended to assets in Azure Purview. Use Microsoft 365 Security and Compliance Center to consent.
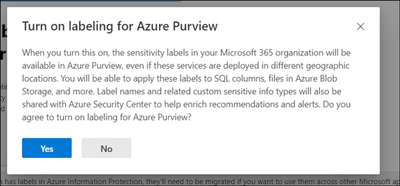
Create or update M365 Auto-labeling Rules
It is important to identify which team in your organization is responsible for defining Sensitivity Labels in Microsoft 365.
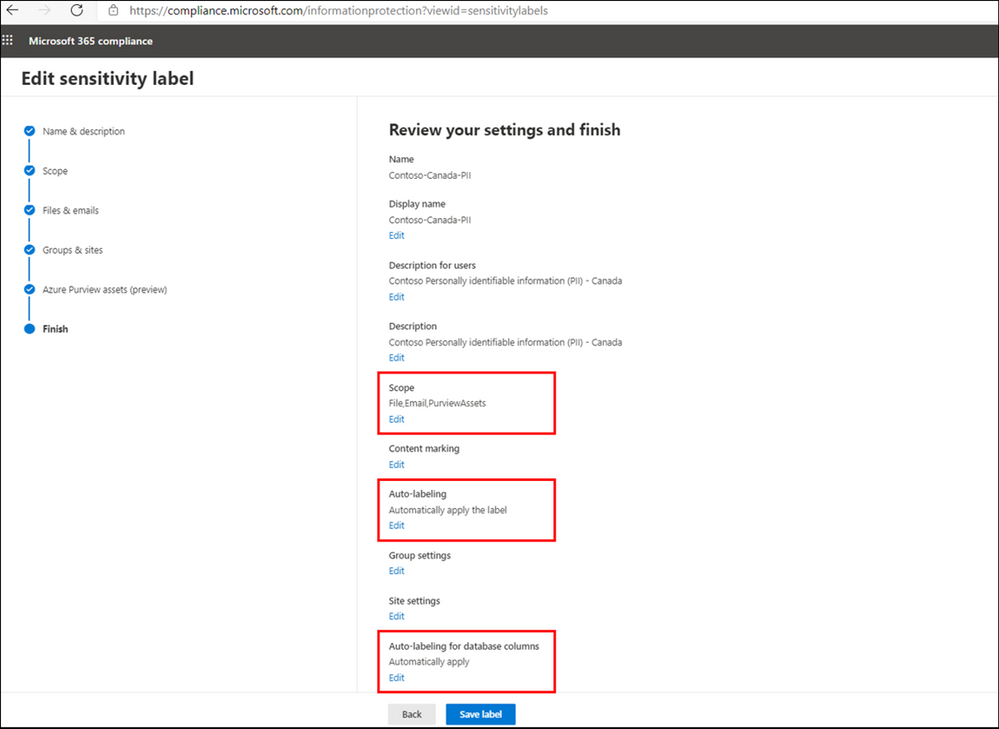
To extend a label to Azure Purview, you can create a new M365 Sensitivity Label or update an existing one in Microsoft 365 Security and Compliance Center, by configuring the following settings:
- From Define the scope for this label enable Azure Purview Assets.
- Add Auto-labeling rule
- From Auto-labeling for database columns enable Auto-labeling for database columns.
Information Protection Administrator or Global Administrator roles can be used to create or update Sensitivity Labels.
If you are looking to expand visibility of your M365 Sensitivity Labels to other teams, you can provide them with Read-only access to view of M365 Sensitivity Labels in your tenant, you can assign the user with Security Reader role in Azure AD or more specifically assign them with Sensitivity Label Reader in Microsoft 365 Security and Compliance Center.
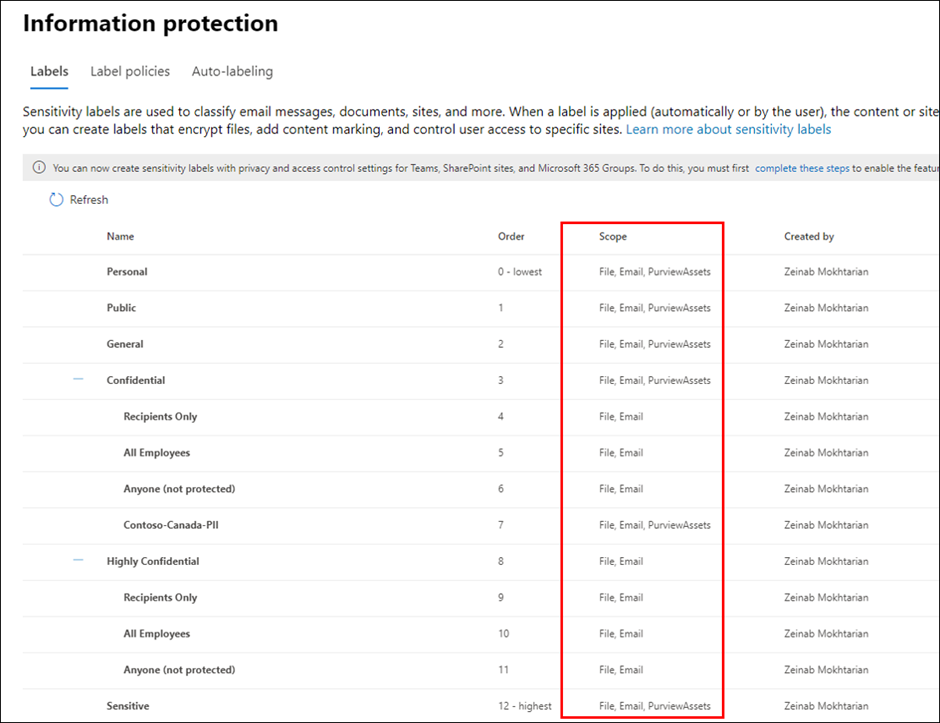
Register and Scan data sources in Azure Purview
Use Azure Purview Studio to register data sources such as Azure SQL Servers or Blob Storage. Once you scan your data sources, Sensitivity Labels are automatically assigned based on auto-labeling rules and then you will be search, browse and filter assets based on Sensitivity Labels or view Insights Reports. View my past blog post to read more about setting up and exploring assets by Sensitivity Labels in Azure Purview.
Purview Data Curator + Data Source Administrator or Purview Data Reader + Data Source Administrator roles can be used to scan data in Azure Purview. To search assets and view reports, you can use at least Purview Data Reader role.
Summary and Call to Action
Through close integration with Microsoft Information Protection offered in Microsoft 365 Azure Purview enables direct ways to extend visibility into your data estate, and classify and label your data.
We would love you hear your feedback and know how Azure Purview helped tracking your sensitive data estate using automatic labeling.
- Create an Azure Purview account now and extend your M365 Sensitivity Labels across your files and database columns in Azure Purview.
- Use Sensitivity Labels Insights to get a bird’s eye view of your data estate by the sensitivity labels.
- Learn more about Azure Purview Autolabeling and Sensitivity Label Insights.
- Provide your feedback.
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.


Recent Comments