This article is contributed. See the original author and article here.
Introduction
This is John Barbare and I am a Sr Customer Engineer at Microsoft focusing on all things in the Cybersecurity space. In this blog I will focus on a future release of Microsoft Defender Application Guard for Office available in limited preview for Windows 10 20H2. Windows 10 20H2 is now available for commercial customers to begin feature exploration and validation prior to being released for general availability. For the last several months I have tested and demoed multiple new features in Windows 10 20H1 as I was on Microsoft’s Elite Program before it became limited availability. One can access Windows 10 20H2 through normal channels, including Windows Update, Windows Server Update Services (WSUS), and Azure Marketplace. If you want to test out in a lab environment or proof of concept, you can also download the .iso file located here.
My interest in Microsoft Defender Application Guard came from demoing and then deploying to several large clients last year due to a high interest of attackers developing new techniques to breach large scale networks and compromising workstations. With phishing schemes remaining one of the top ways to dupe users into social engineering attacks, Microsoft Defender Application Guard is engineered and designed to proactively prevent multiple types of attacks. When Microsoft extended Microsoft Defender Application Guard for Office, it further decreased the overall attack surface reduction while also increasing employee’s productivity. Before we go into the features of Microsoft Defender Application Guard for Office, I will go over a brief introduction to Microsoft Defender Application Guard if one is not familiar.
Prerequisites for Microsoft Defender Application Guard
Hardware Requirements
- A 64-bit computer with a minimum of 4 cores (logical processors) is required for hypervisor and virtualization-based security (VBS). For more info about Hyper-V, see Hyper-V on Windows Server 2016 or Introduction to Hyper-V on Windows 10. For more info about hypervisors, see Hypervisor Specifications
- CPU virtualization extensions – Extended page tables, also called Second Level Address Translation (SLAT) and one of the following virtualization extensions for VBS: VT-x (Intel) or AMD-V
- Minimum 8GB RAM
- 5 GB free space, solid state disk (SSD) recommended for hard disk space
Software requirements
- Operating system – Windows 10 Enterprise edition, version 1709 or higher
Windows 10 Professional edition, version 1803 or higher
Windows 10 Professional for Workstations edition, version 1803 or higher
Windows 10 Professional Education edition version 1803 or higher
Windows 10 Education edition, version 1903 or higher - Browser – Any variant of Microsoft Edge and Internet Explorer
Microsoft Defender Application Guard Brief Overview
Microsoft Defender Microsoft Defender Application Guard is a hardware Isolation leveraging a Hyper-V enabled container. The container uses a lightweight Virtual Machine (VM) that is resistant to kernel attacks and runs on a separate kernel from the host. There are two types of modes – Enterprise Management Mode and Standalone Mode. In Enterprise Management Mode, the administrator defines trusted sites through GPOs, Microsoft Intune, Microsoft Endpoint Configuration Manager, or your current mobile device management solution. Untrusted sites launch in the isolated Hyper-V container giving the user a malicious free browsing session.
Microsoft Defender Application Guard was created to target the following types of systems:
- Enterprise Desktops and Laptops -Domain-joined and managed by your organization.
- Bring your own device – Personally-owned laptops are not domain-joined, but are managed by your organization through tools, such as Microsoft Intune.
- Personal devices – Personally-owned desktops or mobile laptops are not domain-joined or managed by an organization. The user is an admin on the device and uses a high-bandwidth wireless personal network while at home or a comparable public network while outside.
In Standalone Mode, users can use hardware-isolated browsing sessions without any administrator or management policy configuration. In this mode, you must install Microsoft Defender Application Guard and then the user must manually start Microsoft Defender Application Guard while browsing trusted/untrusted sites. I normally do not recommend Standalone Mode to clients as it lets the user decide if they want to use a Microsoft Defender Application Guard session or to not use. Then the user can allow any action (good or bad) which might result in malicious behavior.
The following is a diagram of controls that are configurable for Microsoft Defender Application Guard sessions:
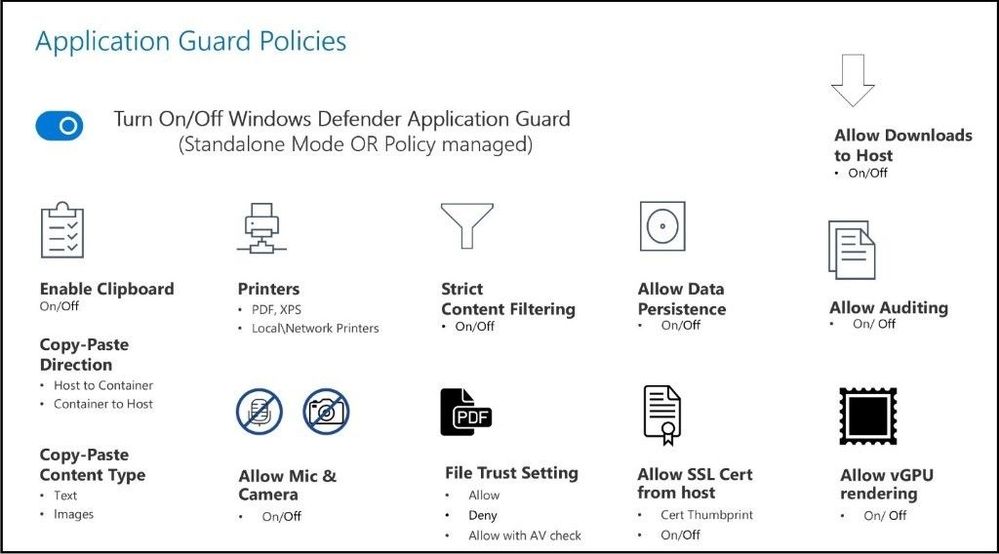
If an employee goes to an untrusted site, Microsoft Edge opens the site in an isolated Hyper-V-enabled container, which is separate from the host operating system. This container isolation means that if the untrusted site turns out to be malicious, the host PC is protected and the attacker cannot break out of the container or gain access to the local machine. The container is left running and until sign off or reboots the container is running in the background. For example, this approach makes the isolated container anonymous, so an attacker cannot get to your employee’s enterprise credentials or other sensitive information. Capabilities have also been extended for Application Guard for Google Chrome and Mozilla Firefox with browser side extensions as of this publication for users that chose other browsers.
Microsoft Defender Application Guard for Office
As stated previously, multiple files, phishing attacks, and malicious content from the internet pose a threat to users. Various other attack vectors, which include potentially unsafe locations, can contain viruses, worms, or other kinds of malware that can harm your computer and/or sensitive data. Microsoft Defender Application Guard steps in and gives you a second barrier to help protect you against these attacks. Microsoft Office will open files from potentially unsafe locations in Microsoft Defender Application Guard, a secure container, that is isolated from the device through hardware-based virtualization. When Microsoft Office opens files in Microsoft Defender Application Guard, a user can then securely read, edit, print, and save the files without having to re-open files outside of the container.
The settings for Microsoft Defender Application Guard for Office have additional controls you can set as depicted below. Office files supported include Excel for Microsoft 365, Word for Microsoft 365, and PowerPoint for Microsoft 365.
AppGuard Policies for Office
Depending on if you set your configurations for the user to change the settings after opening the file or if you block the user with no privileges, one can see the difference in each Office file as seen in the image below.
Different views per setting
If your administrator has enabled Safe Documents, the file will be verified against the Microsoft Defender Advanced Threat Protection service to determine if it is malicious before it is opened outside Microsoft Defender Application Guard.
Office will automatically use Microsoft Defender Application Guard to isolate untrusted documents under the following conditions:
- Microsoft Defender Application Guard is enabled in Windows. This can be enabled by either an administrator deploying policy or the user.
- The user is using Microsoft 365 Apps for enterprise client.
- The user signed into Office is licensed for Microsoft Defender Application Guard. Microsoft Defender Application Guard for Office will require either a Microsoft 365 E5 or Microsoft 365 E5 Security license.
If any of these conditions are not met, Office will use Protected View to isolate untrusted documents.
Files that are currently open in Protected View will open in Microsoft Defender Application Guard. These include:
- Files originating from the internet: This refers to files that are downloaded from domains that are not part of either the local intranet or a Trusted Sites domain on your device.
- Files that are located in potentially unsafe locations: This refers to folders on your computer or network that are considered unsafe, such as the Temporary Internet folder or other folders assigned by your administrator.
- Outlook attachments: Attachments in email can come from unreliable or unknown sources, such as someone outside your organization. Sometimes malicious attachments can appear to come from trusted senders or compromised accounts of trusted senders. Always confirm with the sender if you receive an unexpected or suspicious attachment via email.
Walkthrough of Opening an Office File in Microsoft Defender Application Guard
Ill demo using Microsoft Edge Chromium in User Mode on my test machine to show how Microsoft Defender Application Guard for Office will open an Office file. The settings will be slightly different as it will give me more options to choose from, which might be risky in some environments compared to Enterprise Mode.
I will first do a quick search for “Clemson Tigers Football Resume Template” on Bing.com and locate the website that contains the Office file I need. I find the site that contains the file, but as a regular user, I am not sure if the site (or file) has been spoofed, contains malicious content, or an active Ransomware campaign is in the Office file that will lock all the files on my computer. I go ahead and click the URL to open the Office file knowing I will be protected with Microsoft Defender Application Guard for Office.
Searching for an untrusted Office document to open
When the file opens, it automatically goes into a container in Microsoft Defender Application Guard for Office as you can see from the window below.
Untrusted Office document opening in AppGuard for Office
Once the file is open on my machine, I can view the document and the icon for Word on the taskbar has the shield inside to show that I am protected by using Microsoft Defender Application Guard for Office.
Word document in the container
In addition to being able to read the document within the secure container, one can now use features like printing, commenting and review, light editing, and saving, while keeping the untrusted document within the Microsoft Defender Application Guard container.
When you encounter documents from untrusted sources that are not malicious, you can continue to be productive without worrying about putting your device at risk. If you do encounter a document that is malicious, it is safely isolated within Microsoft Defender Application Guard, keeping the rest of your systems safe.
After finishing the template, I will go ahead and save on my machine and the Office file will still be saved in an isolated container in my OneDrive folder. I have my settings configured so I can take it out of the container if I trust the source. For testing purposes, I have it configured like this to show you the different options. Always test all Microsoft Defender Application Guard Office settings in a test environment before implementing in production.
AppGuard save as options
Next, I will go into my OneDrive and click on the same Office file. Notice it will open again in Microsoft Defender Application Guard for Office.
Opening back up the Office file
Once the file opens, you can see the Word document opens back up in Microsoft Defender Application Guard for Office as seen in the called-out boxes.
Office document opening back up in container
If I want to save the file outside the container, I can do so in this mode also. Once I click on the “Remove Protection”, the file is automatically scanned for any types of malicious threats or embedded scripts in Microsoft Defender ATP.
Removing protection
The file being scanned by Microsoft Defender ATP to be deemed safe before being saved locally.
Office file being scanned for threats
As one can see, the file has been deemed safe and the file will be saved in the folder of your choice with the necessary permissions.
Testing a Malicious (test) Word Document
To see what a malicious word document will do when trying to take it out of the container, we will download a test Word document that will create malicious executable content though an embedded macro. If your enterprise allows unsigned macros and they happen to be malicious, you will see what happens next. You can download the safe test file from Microsoft’s Attack Surface Reduction Rules test site located here. Once we click on the link and open the file, it automatically opens in Microsoft Defender Application Guard for Office.
Opening a malicious Office file
When we go to save the file and attempt to take it out of the container (removing the protection), we are prompted with the following screen. I will go ahead and click on remove protection to see the actions that are taken.
Removing protection
The file is confirmed to remove the protection and then scanned.
Removing protection confirmation
Office file being scanned for threats
The file is opened outside the container with a “security warning: macros have been disabled” as it has been determined to have a malicious macro(s) inside the Office document. Once I click on enable content to enable the macro(s), I am further prevented from working or editing the file.
Security warning that macros have been disabled due to a threat
The file shows me the warning with information about the macro(s) and the Office file will be automatically closed and be prevented from running the malicious content.
Confirmation of the threat and Office file closing
Conclusion
Thanks for taking the time to read this blog and I hope you had fun reading about the new Microsoft Defender Application Guard for Office. Since Office documents are immensely popular vectors for attacks, this new security feature will assist your enterprise in stopping Office file attacks by keeping them contained. By having this enhanced security feature, it will increase user productivity across your enterprise. Always test and refine these settings with a pilot group of users and devices first, before widely distributing to your organization! This new feature brings together Office, Windows, and Microsoft Defender ATP for an integrated value.
Hope to see you in my next blog and always protect your endpoints!
Thanks for reading and have a great Cybersecurity day!
Follow my Microsoft Security Blogs: http://aka.ms/JohnBarbare
References
Application Guard for Office for Admins
Microsoft Defender Application Guard Overview
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.


Recent Comments