by Contributed | Dec 4, 2020 | Azure, Microsoft, Technology
This article is contributed. See the original author and article here.
Sarah Lean
Sarah is a Cloud Advocate for Microsoft. In this Discover STEM video Sarah talks about cloud computing, including explaining the basic principles behind the technology, using terms like servers, data centres and computing power. She provides some advantages and disadvantages of using the technology and also provide examples for how industry might use cloud technology in the future.
A Gentle Introduction to Using a Docker Container as a Dev Environment | CSS-Tricks
Burke Holland
Sarcasm disclaimer: This article is mostly sarcasm. I do not think that I actually speak for Dylan Thomas and I would never encourage you to foist a light
Green Energy Efficient Progressive Web Apps | Sustainable Software
Asim Hussain
As a web developer, can we adjust our code to participate in the global effort to reduce the carbon footprint? PWAs offer some solutions
How to Monitor an Azure virtual machine with Azure Monitor
Thomas Maurer
Here is how to use Azure Monitor to collect and analyze monitoring data from Azure virtual machines to maintain their health. Virtual machines can be monitor…
Working with Git Branches!
Sarah Lean
Let’s get to grips with Git Branches
5 things you should know about Real-Time Analytics | A Cloud Guru
Adi Polak
Running analytics on real-time data is a challenge many data engineers are facing today. But not all analytics can be done in real time! Many are dependent on the volume of the data and the processing requirements. Even logic conditions are becoming a bottleneck. For example, think about join operations on huge tables with more […]
AzUpdate: Azure portal updates, ARM Template support for file share backup and more
Anthony Bartolo
It might be snowing in parts of the Northern Hemisphere, but we won’t let that stop us from sharing Azure news with you. News covered this week includes: New Azure Portal updates for November 2020, Azure Resource Manager template support for Azure file share backup, How to use Windows Admin Center on-premises to manage Azure Windows Server VMs, Multiple new features for Azure VPN Gateway now Generally Available, and our Microsoft Learn Module of the Week.
Hybrid management. Where do I start?
Pierre Roman
Managing & maintaining servers on-premises or in multiple clouds, as well as Azure? Learn about management tools for your servers wherever they are.
#VisualizeIT: A free online series of workshops to build your visual storytelling skills!
Nitya Narasimhan
#VisualizeIT is a free online series of workshops for creative technologists, from @MSFTReactor, @azureadvocates and members of the @letssketchtech community.
Handle app button events in Microsoft Teams tabs
Waldek Mastykarz
Did you know that you can respond to user clicking on the app button of your Microsoft Teams personal app?
Weekly Update #67 – Rebuilding laptops, filming videos and news!
Sarah Lean
In this week’s update I talk about rebuilding my laptop, talking at a user group, filming videos and the Azure news of the week. :red_circle: Azure Cloud Shell Update -…
Picking the Right Distributed Database [Create: Data]
Abhishek Gupta
“In God we trust, all others must bring data” William Edwards Deming Well…
Securing a Windows Server VM in Azure
Sonia Cuff
If you’ve built and managed Windows Servers in an on-premises environment, you may have a set of configuration steps as well as regular process and monitoring alerts, to ensure that server is as secure as possible. But if you run a Windows Server VM in Azure, apart from not having to manage the physical security of the underlying compute hardware, what on-premises concepts still apply, what may you need to alter and what capabilities of Azure should you include?
CLI for Microsoft 365 v3.3 – Microsoft 365 Developer Blog
Waldek Mastykarz
Connect to the latest conferences, trainings, and blog posts for Microsoft 365, Office client, and SharePoint developers. Join the Microsoft 365 Developer Program.
Microsoft 365 PnP Weekly – Episode 107 – Microsoft 365 Developer Blog
Waldek Mastykarz
Connect to the latest conferences, trainings, and blog posts for Microsoft 365, Office client, and SharePoint developers. Join the Microsoft 365 Developer Program.
What is Serverless SQL? And how to use it for Data Exploration | by Adi Polak | Dec, 2020 | Towards Data Science
Adi Polak
So, you are a data scientist, you work with data and need to explore it and run some analytics on the data before jumping into running extensive machine learning algorithms. According to Wikipedia…
Terraform for Java developers, part 1 of 4
Julien Dubois
An introduction to Terraform focusing on Java developers. In this first video (out of 4), we describe what Terraform is, and we fork the Spring Petclinic pro…

by Contributed | Dec 4, 2020 | Azure, Microsoft, Technology
This article is contributed. See the original author and article here.

The UP Podcast with Lisa Crosbie & Megan V. Walker
Lisa Crosbie and Megan V. Walker are Business Application MVPs. With Lisa in Australia and Megan in the United Kingdom, the pair thought it was a great idea to start a podcast together about Microsoft Business Applications, the Power Platform, Dynamics 365, and Microsoft technologies. The UP Podcast shares what is new and exciting, highlights community content, and seeks to share and learn with the audience. Follow on Twitter @LisaMCrosbie, @MeganVWalker, @the_UP_podcast.

How to automatically re-enable flow using Power Automate
Hiroaki Nagao is a Business Applications MVP from Japan. Currently working as a system administrator in an operating company, Hiroaki is a core member of the local Power Apps / Power Automate community. A regular blogger with more than 100 posts this year, find more on his blog or Twitter @mofumofu_dance

Engage Your Audience with Forms Polls in Microsoft Teams Meetings
Matti Paukkonen is an Office Apps & Services MVP and Modern Work Architect from Finland. He has more than 10 years’ experience of Microsoft collaboration solutions, like SharePoint, Microsoft Teams and Microsoft 365. He writes technical blog articles, organizes a local Teams User Group, and participates on several communities and speaks on events. Follow him on Twitter @mpaukkon.

Azure Sentinel: Connecting the Enterprise Firewalls
John Joyner is an inventor, author, speaker, and professor on datacenter and enterprise cloud computing topics. John, who has been named as an MVP for the past twelve years, teaches a cloud computing management course at the University of Arkansas. For more, check out his Twitter @john_joyner

ML.NET Model Builder: Getting Started (using ASP.NET Core)
Syed Shanu is a Microsoft MVP, a two-time C# MVP and two-time Code project MVP. Syed is also an author, blogger and speaker. He’s from Madurai, India, and works as Technical Lead in South Korea. With more than 10 Years of experience with Microsoft technologies, Syed is an active person in the community and always happy to share his knowledge on topics related to ASP.NET , MVC, ASP.NET Core, Web API, SQL Server, UWP, Azure, among others. You can see his contributions to MSDN and TechNet Wiki here. Follow him on Twitter @syedshanu3.

by Contributed | Dec 4, 2020 | Azure, Microsoft, Technology
This article is contributed. See the original author and article here.
Big announcement surrounding the general availability of Azure Synapse Analytics and the public preview release of Azure Purview data catalog is covered this week on AzUpdate. Other news items covered include: Azure AD Application Proxy now natively supports apps that use header-based authentication, and the Microsoft Learn Module of the week.
Azure Synapse now Generally Available
Solutions like data lakes and data warehouses have helped organizations collect and analyze several types of data. The process however, created niches of expertise and specialized technology. Azure Synapse rearchitects operational and analytics data stores to take full advantage of a new, cloud-native architecture. The solution enables organizations to query data using either serverless or dedicated resources at scale while maintaining consistent tools and languages. Think of it as your organization’s one pane of glass to analyze all its captured data. Azure Synapse combines capabilities spanning the needs of data engineering, machine learning, and BI without creating silos in processes and tools.
Further details can be found here: Harnessing the power of Azure Synapse for improved data and analytics
Details have also been shared on how Microsoft’s Modern Workplace team in partnership with CMS Medicare developed an end-to-end Azure Synapse and Power BI tutorial including over 120 million rows of real CMS Medicare Part D Data to help other organizations learn how to harness it.
The entire step-by-step tutorial including the demo public domain Part D data can be viewed here: How to Deploy an End-to-End Azure Synapse Analytics and Power BI Solution
Public Preview of Azure Purview data catalog
Announced alongside Azure Synapse, Azure Purview enters public preview and provides a comprehensive data governance solution enabling organizations to know where all thier data resides. The solution can easily create an up-to-date map of an organization’s data landscape with automated data discovery, sensitive data classification, and end-to-end data lineage wherever it is stored including on-premises, across multi-clouds and multi-edge, in SaaS apps, and in Microsoft Power BI. Azure Purview is integrated with Microsoft Information Protection thus enabling the ability to apply the same sensitivity labels defined in Microsoft 365 Compliance Center.
Further details can be found here: Azure Purview
Azure AD Application Proxy now natively supports apps that use header-based authentication
Public preview of Application Proxy support for applications that use header-based authentication on standard claims that are issued by Azure AD is now available. Some examples of said applications include NetWeaver Portal, Peoplesoft, and WebCenter of which can benefit from all the capabilities of Application Proxy, including single sign-on as well as enforcing pre-authentication and Conditional Access policies like requiring Multi-Factor Authentication (MFA) or using a compliant device before users can access these apps. What’s more, no added software is required as existing Application Proxy connectors can be used.
Steps on how to harness this can be found here: How to enable Azure AD Application Proxy to support apps using header-based authentication
Community Events
- Create: Data – A half day of conversations with experts and community to learn and discuss everything data – from the upcoming trends, to best practices and data for good.
- All Around Azure – A Beginners Guide to IoT – Focus on topics ranging from IoT device connectivity, IoT data communication strategies, use of artificial intelligence at the edge, data processing considerations for IoT data, and IoT solutioning based on the Azure IoT reference architecture
- Festive Tech Calendar – Continuing this month’s content from different Azure communities and people around the globe for the month of December
- Introduction to Cloud Adoption Framework – Sarah Lean investigates Microsoft’s Cloud Adoption Framework offering and what is available for organizations to take advantage of
MS Learn Module of the Week

Realize Integrated Analytical Solutions with Azure Synapse Analytics
This learning path provides details on how Azure Synapse Analytics enables you to perform different types of analytics through its’ components that can be used to build Modern Data Warehouses through to Advanced Analytical solutions.
This learning path can be completed here: Integrated Analytical Solutions via Azure Synapse Analytics
Let us know in the comments below if there are any news items you would like to see covered in next week show. Az Update streams live every Friday so be sure to catch the next episode and join us in the live chat.
by Contributed | Dec 3, 2020 | Azure, Microsoft, Technology
This article is contributed. See the original author and article here.
As part of our recent Azure Security Center (ASC) Blog Series, we are diving into the different controls within ASC’s Secure Score. In this post we will be discussing the control of “Apply Adaptive Application control”.
This security control contains up to 7 recommendations, depending on the resources you have deployed within your environment, and it is worth maximum of 1 point (2%) that counts towards your overall Secure Score. To understand about Azure Security Center’s secure score make sure you read this article. These recommendations are meant to keep your resources safe and improve your security hygiene.
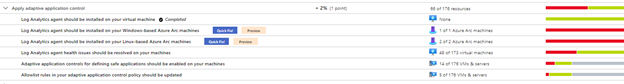
Apply adaptive application control contains the following 7 recommendations, depending on your environment:
- Log Analytics agent should be installed on your virtual machine
- Monitoring agent should be installed on your machines
- Log Analytics agent should be installed on your Windows-based Azure Arc machines
- Log Analytics agent should be installed on your Linux-based Azure Arc machines
- Log Analytics agent health issues should be resolved on your machines
- Adaptive application controls for defining safe applications should be enabled on your machines
- Allowlist rules in your adaptive application control policy should be updated
The example screenshot below shows an environment in which only 6 of those 7 recommendations are within the scope of Apply adaptive application control security control, because the recommendations which do not apply to any resource within your environment do not appear.
 Image 1 – Recommendations within the Apply adaptive application control
Image 1 – Recommendations within the Apply adaptive application control
Like the rest of the Secure Score controls, all these recommendations must be considered in order to get the full points and drive up your Secure Score (you can review all of the recommendations here). Also, some might have a “Quick Fix!” button as well! No excuses not to enable those, it simplifies remediation and enables you to quickly increase your secure score, improving your environment’s security. To understand how Quick Fix works, please make sure to visit here
Category #1: Log Analytics agent should be installed on your virtual machine
To monitor for security vulnerabilities and threats, Azure Security Center depends on the Log Analytics Agent. The agent collects various security-related configuration details and event logs from connected machines, and then copies the data to your Log Analytics workspace for further analysis. Without the agent, Security Center will not be able to collect security data from the VM and some security
recommendations and alerts will be unavailable and within 24hrs, Security Center will determine that the VM is missing the extension and recommends you to install it via this security control. You could manually install the agent with the help of this recommendation or If you have auto-provisioning turned on, when Security Center identifies missing agent, it installs the extension automatically which in-turn reduces management overhead. Refer to this article to understand deployment options. Several questions arise at this point for scenarios like, how auto provisioning works in cases where there is already an agent installed and to understand that please read this information.
The following recommendations belong to this category:
- Monitoring agent should be installed on your machines.
- Log Analytics agent should be installed on your Windows-based Azure Arc machines. This recommendation applies to Windows-based Azure Arc machines
- Log Analytics agent should be installed on your Linux-based Azure Arc machines. This recommendation applies to Linux-based Azure Arc machines
Alternatively, to fix this recommendation, you can visit our Github Repository and leverage the automations we have published there.
Category #2: Log Analytics agent health issues should be resolved on your machines
You’ll notice this recommendation when Azure Security Center finds Log Analytics agent unhealthy which means, a VM is unmonitored by Security Center since the VM does not have healthy Log Analytics agent extension. This could be due to several reasons, one of it could be the agents are not able to connect to and register with Security Center due to no access to the network resources. Read more about this scenario here. To fully benefit from all of Security Center’s capabilities, the Log Analytics agent extension is required.
For more information about the reasons Security Center is unable to successfully monitor VMs and computers initialized for automatic provisioning, see Monitoring agent health issues.
NOTE: The above recommendations (Category #1 and #2) to install the agent and recommendation about agent health issues are pre-requisites. You might observe these recommendations also show up in a different security control, and if they were remediated there, it will not appear here in this Security control.
Category #3: Adaptive application controls for defining safe applications should be enabled on your machines
Application allowlist is not necessarily a new concept. One of the biggest challenges of dealing with the application allowlist is how to maintain that list. The traditional approach of using AppLocker in Windows is a good solution, but still has the overhead of keeping up with the applications and making the initial baseline work properly for our needs.
Adaptive application controls is one of the advanced protection features you can benefit from, when you upgrade to Azure Defender ON, this falls under the cloud Workload Platform Protection (CWPP).
Adaptive application controls help to harden your VMs against malware by making it easier to control which applications can run on your Azure VMs. Azure Defender has built-in intelligence that allows you to apply allowlist rules based on machine learning. This intelligence analyzes the processes that are running in your VMs, creates a baseline of applications, and groups the virtual machines. From here, recommendations are provided that allow you to automatically apply the appropriate allowlist rules. The use of machine learning intelligence makes it super simple to configure and maintain application the allowlist.
With this feature, you’re able to alert on or audit . These can even be malicious applications that might otherwise be missed by endpoint protection solutions, or applications with known vulnerabilities. By default, Azure Defender enables application control in Audit mode. No enforcement options are available at this time of writing.
Adaptive Application Control do not support Windows machines for which AppLocker policy is already enabled by either group policy objects (GPOs) or Local Security policy.
Hope this helps you understand why it is super important for you to enable them. Learning about Adaptive Application Control is essential for anyone looking to gain more granular control and security within their environment, so make sure to read our documentation.
Category #4: Allowlist rules in your adaptive application control policy should be updated
This recommendation will be displayed when Azure Defender’s machine learning identifies potentially legitimate behavior that hasn’t previously been allowed. This recommendation suggests you to add new rules to the existing policy to reduce the number of false positives in adaptive application controls violation alerts. To edit the application control policy please refer to this for more information.
Next Steps
As with all security controls, you need to make sure to remediate all recommendations within the control that apply to a particular resource in order to gain credit towards your secure score.
I hope you enjoyed reading this blog post as much as I enjoyed writing it and learned how this specific control can assist you to strengthen your Azure security posture.
- The main blog post to this series (found here)
- The DOCs article about Secure Score (this one)
Reviewer
Special Thanks to @Yuri Diogenes, Principal Program Manager in the CxE ASC Team for reviewing this article.
by Contributed | Dec 3, 2020 | Azure, Microsoft, Technology
This article is contributed. See the original author and article here.
“Databases-as-Code” is an important principle in improving predictability in developing, delivering, and operating Azure SQL databases. In the first part of this two-part series with Arvind Shyamsundar, we quickly survey the different tools and methodologies available and then show you how to get started with GitHub Actions for a simple CI/CD pipeline deploying changes to an Azure SQL DB.



Recent Comments