by Scott Muniz | Jul 22, 2020 | Alerts, Microsoft, Technology, Uncategorized
This article is contributed. See the original author and article here.
Here are the updates to the Azure portal this month:
Compute>Linux
Storage>Storage Account
All categories
Intune
Let’s look at each of these updates in greater detail.
Compute>Linux
Simplification of the Linux + SSH Experience
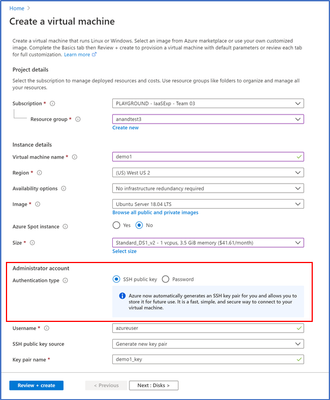
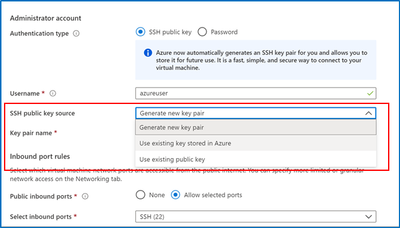
In the VM create experience, SSH key is now the default authentication method instead of passwords for Linux images. Azure will now automatically generate a new SSH key pair for you instead of you having to use a third-party tool to create a key pair.
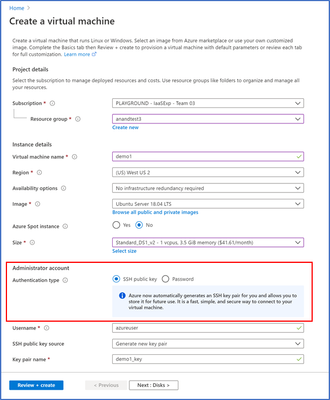
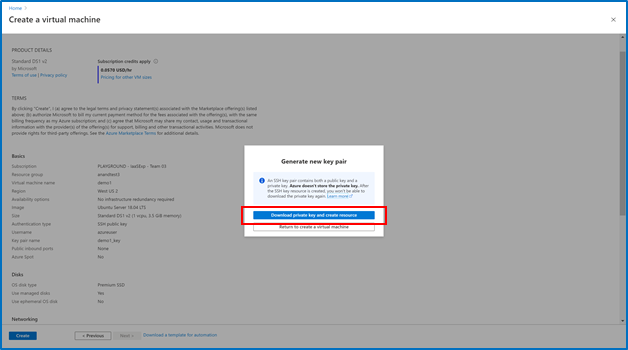
- Enter information to create your virtual machine, and after you click “create”, you will be prompted to download the private key pair, which you will need to connect to their VM via SSH
2. Go to the VM you created and select “SSH”, then open the SSH (terminal, PuTTy, etc.) client of your choice, making sure that you have read-only access to your private key.
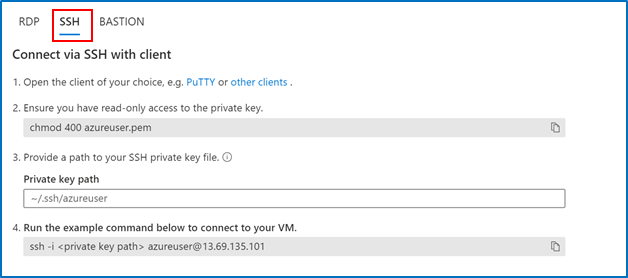
3. Copy the file path where your private key is stored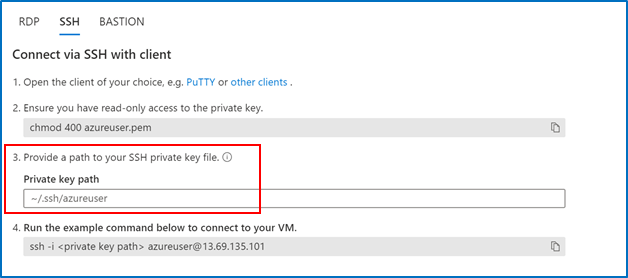 4. Paste the command in your SSH client
4. Paste the command in your SSH client
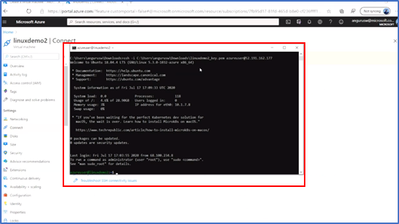
When creating additional Linux VMs, you can reuse SSH key pairs as well instead of creating a new key each time.
Storage>Storage Account
Network Routing Preferences for Storage Accounts now in Public Preview
You can now configure a routing preference to direct network traffic for the default public endpoint of your Storage account using either the Microsoft global network or using the public internet.
- Optimize for premium network performance by using the Microsoft global network, which delivers low-latency path selection with high reliability and routes traffic through the point-of-presence closest to the client.
- Alternatively, route traffic through the point-of-presence closest to your storage account to lower network costs and minimize traversal over the Microsoft global network.
Routing configuration options for your Storage account also enable you to publish additional route-specific endpoints. Use these new public endpoints to override the routing preference specified for the default public endpoint by explicitly directing traffic over a desired path.
Routing preferences for Azure Storage is now available for preview in France South, North Central US, and the West Central US regions.
You can specify your routing preference for a storage account at Create time in the Networking tab.
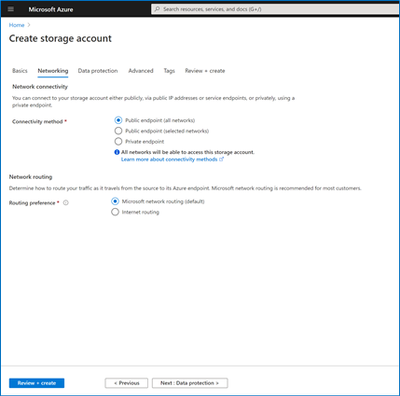
You can also specify a routing preference for your storage account after creation in the Firewalls and Virtual Networks tab in Storage Account Manage.
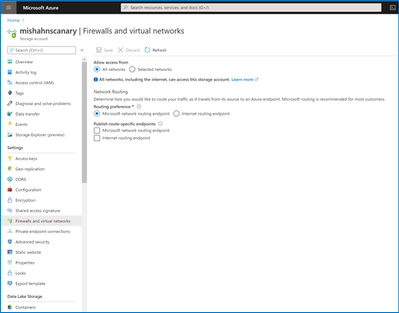
Should you elect to public the individual route-specific endpoints, you can generate an SAS token that directs traffic along the network route you specify.
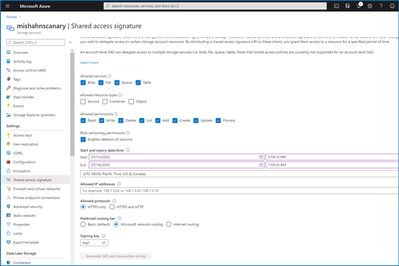
All Categories
New Dashboard Pinning Experience
Previously, users did not have the option to select a dashboard when pinning content. With the new pinning experience, users can now choose an existing dashboard or even create a new dashboard to pin their content to. This pinning experience can be invoked from any service that offers the pinning feature, as indicated by a pin icon.
- Go to any service that enables pinning. Take “All resources” for example.
- Click on the “pin” icon which opens the new pinning experience
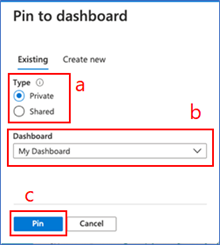
3. From here you can pin to an existing dashboard (default) or create a new dashboard.
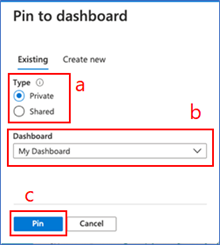
If you pin to an existing dashboard:
a. Select whether you want to pin to an existing private or shared dashboard in the “Type” section
b. Find the dashboard in dashboard dropdown – the default selection in the dropdown is your most recently accessed dashboard
c. Once you select the dashboard from the dropdown, click “Pin”
d, You will get a notification once the pinning has been completed. You can access the dashboard by clicking on the notification.
If you pin to a new dashboard:
a. Select “Create new”
b. Select whether you want to create a new private or shared dashboard
c. Fill in the required information
d. Once you’re done, click “Create and pin”. You will get a notification when the dashboard is successfully created and pinned to. You can access the dashboard by clicking on the notification. You can also access the pinned content by going to Dashboard in the left nav and finding the dashboard you’ve pinned the content to.
INTUNE
Updates to Microsoft Intune
The Microsoft Intune team has been hard at work on updates as well. You can find the full list of updates to Intune on the What’s new in Microsoft Intune page, including changes that affect your experience using Intune.
Azure portal “how to” video series
Have you checked out our Azure portal “how to” video series yet? The videos highlight specific aspects of the portal so you can be more efficient and productive while deploying your cloud workloads from the portal. Check out our most recently published video:
Next steps
The Azure portal has a large team of engineers that wants to hear from you, so please keep providing us your feedback in the comments section below or on Twitter @AzurePortal.
Sign in to the Azure portal now and see for yourself everything that’s new. Download the Azure mobile app to stay connected to your Azure resources anytime, anywhere.
See you next month!
by Scott Muniz | Jul 22, 2020 | Alerts, Microsoft, Technology, Uncategorized
This article is contributed. See the original author and article here.
The Azure Sphere Security Service is an integral part of Azure Sphere and brokers trust for device-to-cloud communication. When a customer creates a new tenant, the Azure Sphere Security Service issues a tenant certificate authority (CA) certificate to the customer. The tenant CA certificate, in turn, issues device certificates that the device uses to get OS updates and to upload telemetry. Tenant CA certificates have a lifetime of two years, which starts from tenant creation. The Azure Sphere Security Service will automatically renew tenant CAs approximately 60 days prior to expiry. If you use Azure Sphere tenant CA certificates to register in Azure IoT hub, Azure IoT Central, and any other relying party, you must register the new certificate so they recognize and authenticate your devices.
Renewal process
Tenant CA certificates will be automatically renewed. Automated renewal process begins approximately 60 days before the current certificate expires.
- A new tenant CA certificate is generated within 60 days prior to the expiration of the current active certificate.
- Approximately 30 days after the creation date of the newly generated CA certificate, it becomes the new active CA certificate and the current active CA certificate becomes inactive and retired. Once a tenant CA certificate has been retired, Azure Sphere device certificates will be issued from the new active CA certificate.
- Once the new tenant CA certificate is issued, it is ready for download. Using new commands available in the Azure Sphere Developer Command prompt, you can:
- Download certificates and certificate chains for the current and new certificates
- Download proof of possession certificates to verify the tenant CA certificate in Azure IoT Central and/or IoT Hub
- Get a list of available certificates and their details for an Azure Sphere tenant.
- A tenant CA certificate status will be one of three possible values, listed below along with a brief explanation of what each status means for you:
| Certificate status |
Description |
What does this mean for you? |
| Revoked |
An untrusted certificate |
This will not be used by the Azure Sphere Security Service |
| Active |
Current active certificate for the tenant |
This tenant CA certificate will issue device certificates |
| Inactive |
This state could mean one of the following. The certificate could be:
- Newly created certificate if “End Date” displayed by the command or “notAfter” in the certificate is approximately two years in the future
- Retired certificate if “End Date” displayed by the command or “notAfter” in the certificate is one to 60 days in the future
- Expired certificate if the “End Date” displayed by the command or “notAfter” in the certificate is in the past
|
The newly created certificate will become active approximately 30 days after it is created. Register this tenant CA certificate in Azure IoT Hub or IoT Central or any other third-party resources |
What do you need to do?
The newly generated certificate is not automatically re-registered in IoT Hub, IoT Central, or any other third-party resource. First, this new certificate must be downloaded. When downloading the certificate, ensure that the newly generated certificate is downloaded and not the currently active certificate. You can use the thumbprint to verify if you are using the correct certificate.
In Azure IoT hub and Azure IoT Central, registering the certificate involves a few simple steps:
- Tenant CA certificate must be first uploaded in the certificates section of IoT Hub or IoT Central.
- In the enrollments section of IoT Hub or IoT Central, the uploaded certificate can be configured as either the primary or secondary certificate. Do not remove any certificates that have not expired.
- The proof of possession certificate can be downloaded using the verification code generated by IoT Hub or IoT Central. Proof of possession certificate must then be uploaded in IoT Hub or IoT Central to complete the certificate registration process.
To avoid any interruption in service, you will have 30 days to register the new certificate in Azure IoT Hub, IoT Central, or any other third-party resource before the newly generated certificate becomes the active certificate.
NOTE: These steps require the 20.07 SDK, which is currently scheduled for release on the afternoon of July 29, 2020 (PST). We will update this post with links to documentation once the 20.07 SDK has been released.
Questions:
Q: Will my devices be updated even after the certificate auto renewal?
A: Your tenant CA certificates are auto renewed to ensure that your devices will continue to receive updates and uploading telemetry.
Q: Help! Rollover has happened to new cert, and my devices are now failing to connect to my services, how do I resolve?
A: You can still register the new certificate. The Azure Sphere Security Services may already be using the new certificate. Relying partners such as IoT central or IoT hub will fail to authenticate your device till the new tenant CA certificate is registered with them.
Q: Oh no! My tenant CA certificate has expired, and I didn’t realize I had to register the new certificate? What do I do?
A: Register your new certificate ASAP. The Azure Sphere Security Service will already be using the new certificate. Relying partners such as IoT central or IoT hub will fail to authenticate your device till the new tenant CA certificate is registered with them.
Documentation Resources:
by Scott Muniz | Jul 22, 2020 | Alerts, Microsoft, Technology, Uncategorized
This article is contributed. See the original author and article here.
This tutorial walks you through the process on how to load data from Always Encrypted enabled Azure SQL database using SQL Server Integration Services (SSIS) in Azure Data Factory.
Azure-SSIS integration runtime has built-in Microsoft ODBC Driver 13 for SQL Server. In this tutorial, we use SSIS ODBC source with Microsoft ODBC Driver 13 to load data from Azure SQL database. Details about ODBC driver setup, refer to using Always Encrypted with the ODBC Driver for SQL Server via Azure Key Vault built-in keystore provider.
- Follow the steps to configure Always Encrypted by using Azure Key Vault , Column Master Key (CMK) is now stored in Azure Key Vault.
- Enable client application access to get the Application (client) ID and client secrete.
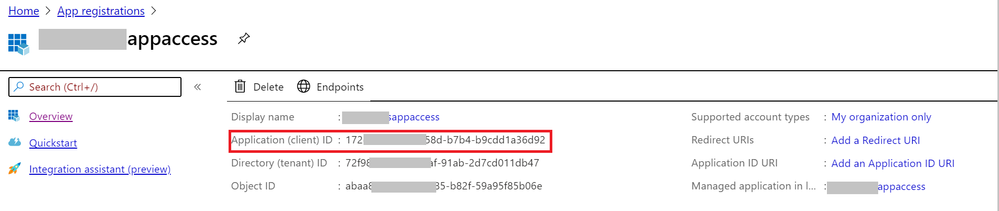
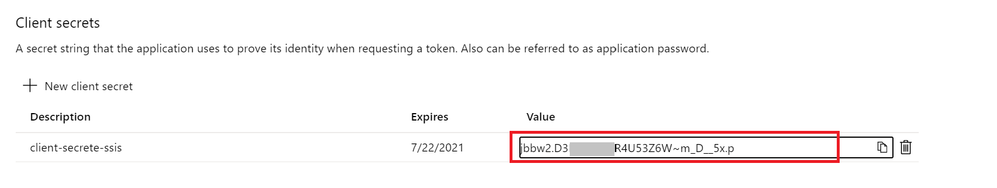
3. Grant the client application proper permissions (get, unwrapKey, and verify) in the Azure Key Vault.
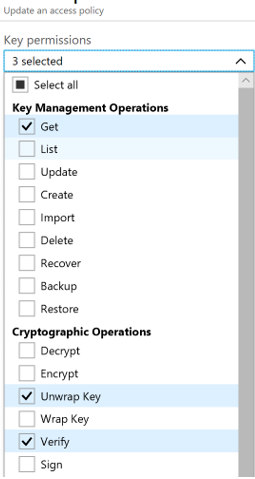
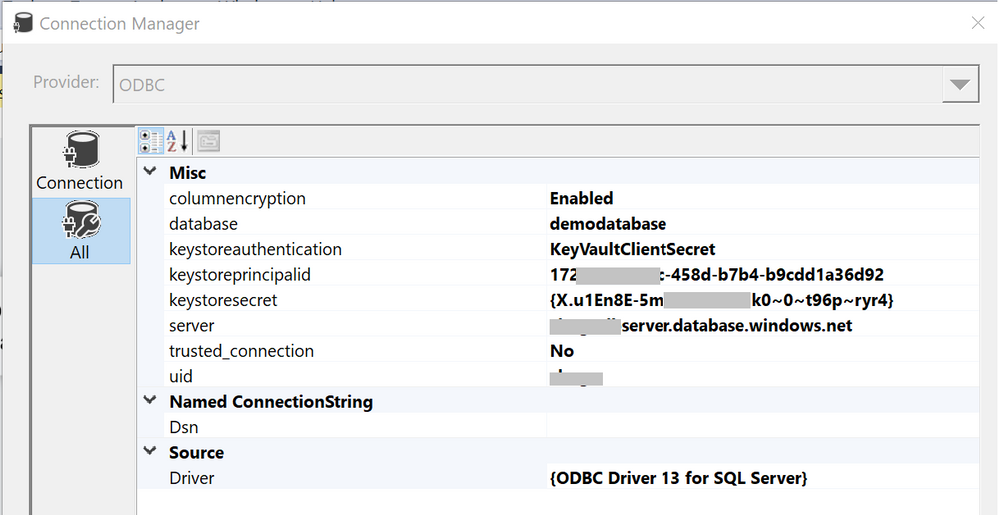
- Create simple SSIS package in Visual Studio 2017 that uses an ODBC source and a flexible file destination. Configure connection string like below:
DRIVER={ODBC Driver 13 for SQL Server};SERVER= <EnterYourServer.database.windows.net>;uid=<myuser>; DATABASE=<mydatabase>;ColumnEncryption=Enabled;KeyStoreAuthentication=KeyVaultClientSecret; KeyStorePrincipalId=<Application (client) ID>;KeyStoreSecret=<client secrete>
Note:
Surround the value with { } when there are [ ] { ( ) , ; ? * = ! @ characters in the client secrete, and manually escape the interior } with a second }.
Example:
keystoresecret={)#|;_=&*{+>*-.&)$8?%}}|S|_^?|*=?.;o==_#-QA=&%};
- Execute package successfully in Visual Studio.
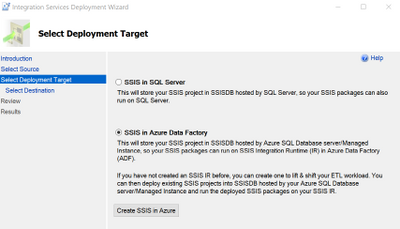
- Deploy project to SSIS in Azure Data Factory.
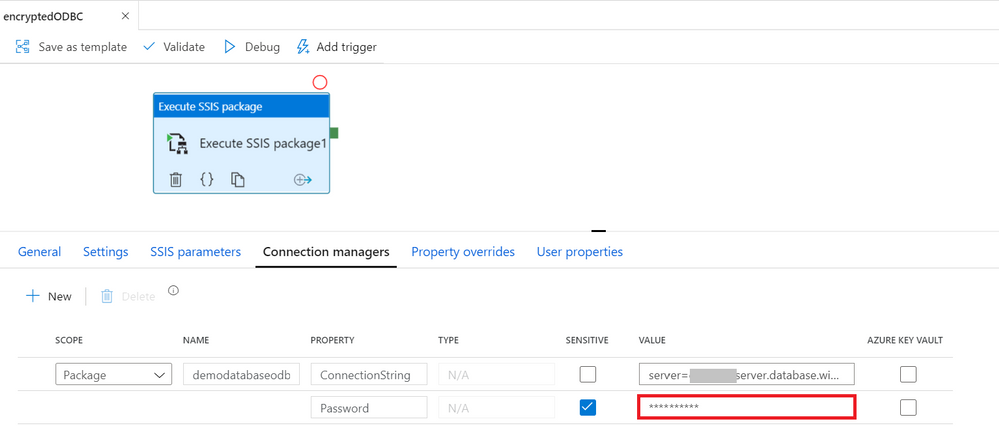
7. Author data factory pipeline with execute SSIS package activity, input password in connection manager parameter.
8. Execute data factory pipeline.
by Scott Muniz | Jul 21, 2020 | Alerts, Microsoft, Technology, Uncategorized
This article is contributed. See the original author and article here.
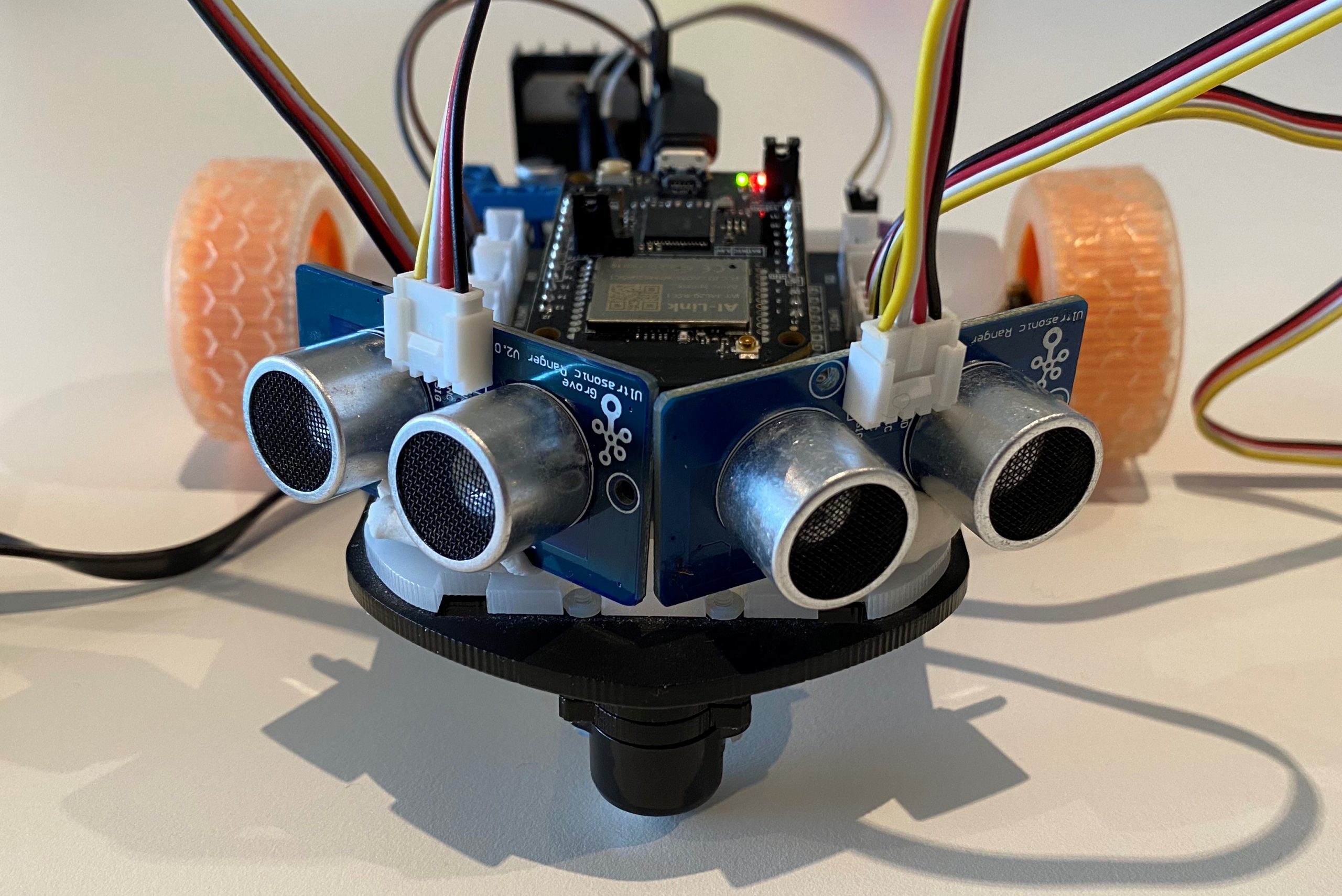
Build a Rover combining the best of Azure Sphere security with FreeRTOS
What you will learn
You will learn how to integrate a Real-time FreeRTOS application responsible for running a timing-sensitive ultrasonic distance sensor with the security and cloud connectivity of Azure Sphere.
#JulyOT
This is part of the #JulyOT IoT Tech Community series, a collection of blog posts, hands-on-labs, and videos designed to demonstrate and teach developers how to build projects with Azure Internet of Things (IoT) services. Please also follow #JulyOT on Twitter.
Source code and learning resources
Source code: Azure Sphere seeing eyed rover Real-time FreeRTOS sensors and Azure IoT.
Learning resources: Azure Sphere Developer Learning Path.
Learn more about Azure Sphere
Azure Sphere is a comprehensive IoT security solution – including hardware, OS, and cloud components – to actively protect your devices, your business, and your customers.
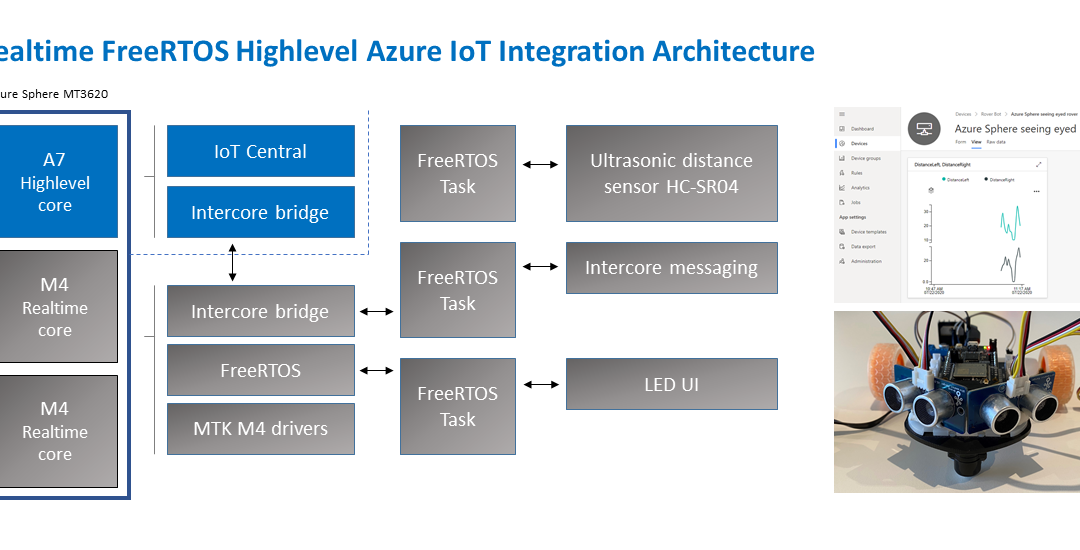
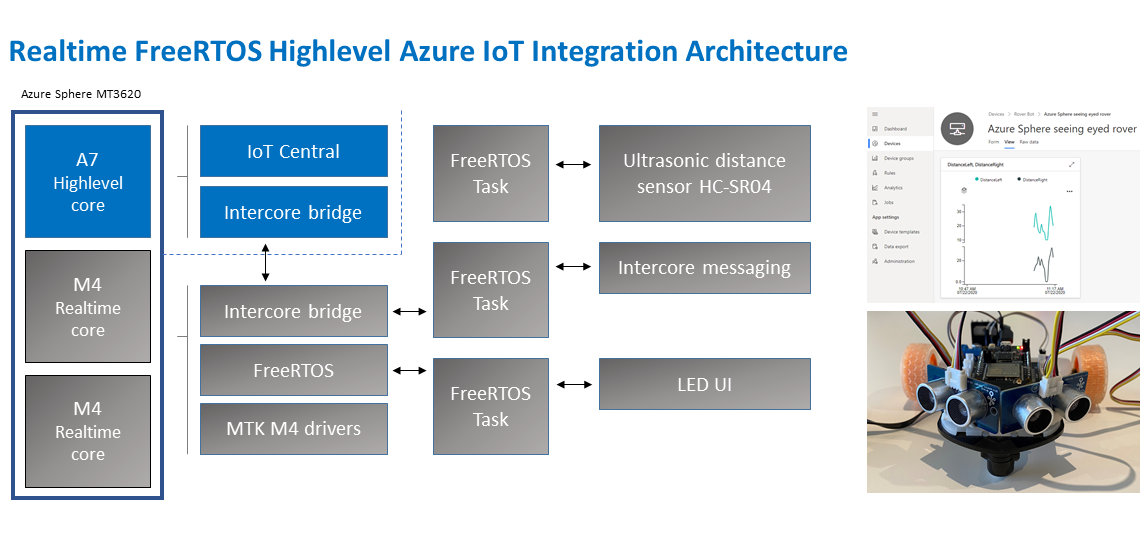
Application architecture
The application running on the Azure Sphere consists of two parts.
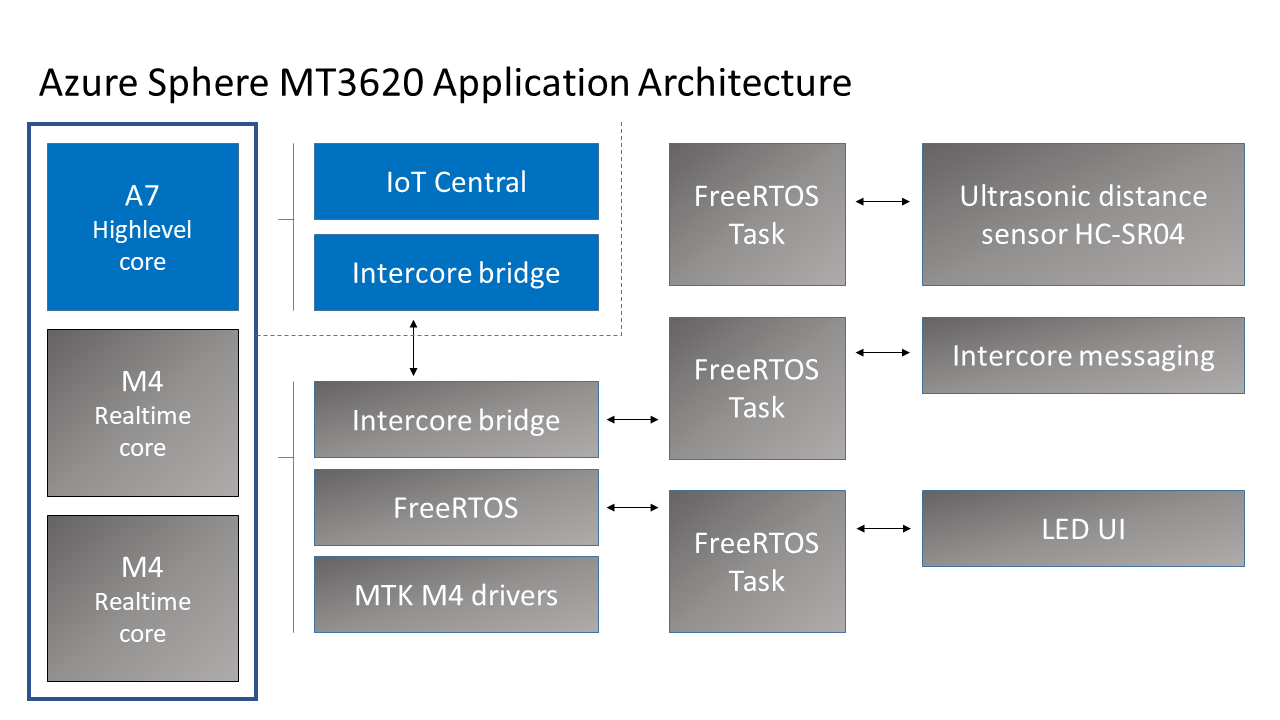
Real-time FreeRTOS Application
- The Real-time FreeRTOS application running on one of the M4 cores that is responsible for running the timing-sensitive HC-SR04 ultrasonic distance sensor.
- Distance is measured every 100 milliseconds so the rover can decide the best route.
- The sensor requires precise microsecond timing to trigger the distance measurement process, so it is a perfect candidate for running on the Real-time core as a FreeRTOS Task.
- Every 5 seconds a FreeRTOS Task sends distance telemetry to the Azure Sphere A7 High-level application.
Azure IoT High-level Application
- The application running on the Azure Sphere A7 High-level application core is responsible for less timing-sensitive tasks such as establishing WiFi/Network connectivity, negotiating security and connecting with Azure IoT Central, updating the device twin and send telemetry messages.
Extending
- I am thinking about extending this solution with a local TinyML module for smarter navigation.
Parts list
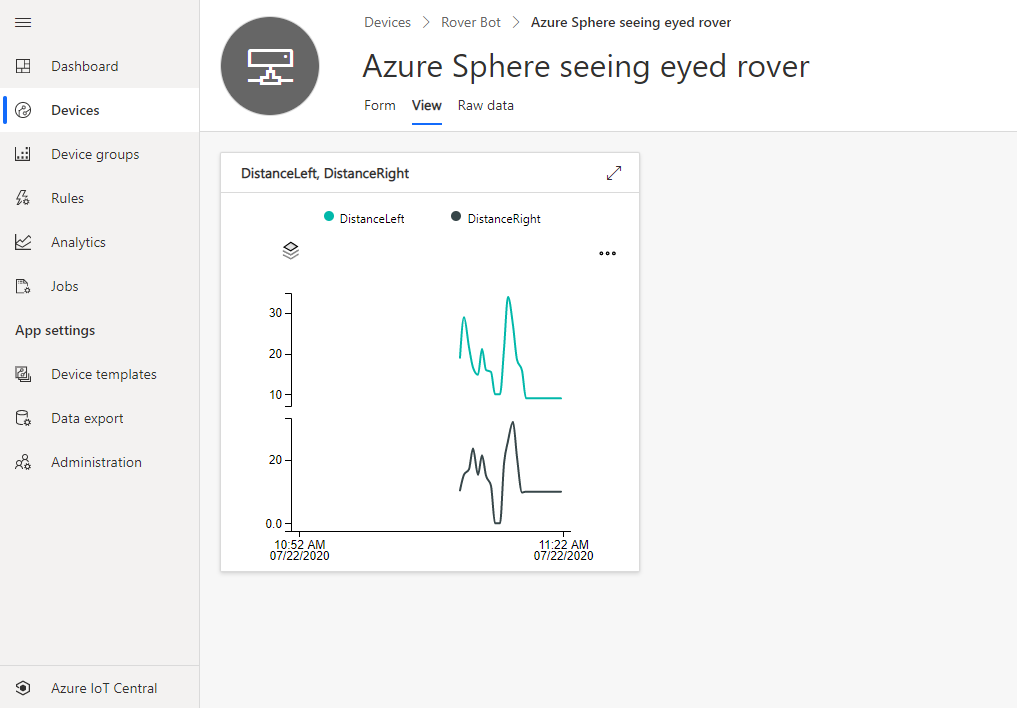
Azure IoT Central
Azure IoT Central provides an easy way to connect, monitor, and manage your Internet of Things (IoT) assets at scale.
I created a free trial of Azure IoT Central and in no time I had the rover distance sensor charted and available for deeper analysis. By the way, you can continue to connect two devices for free to IoT Central after the trial period expires.
Extend and integrate Azure IoT Central applications with other cloud services
Azure IoT Central is also extensible using rules and workflows. For more information, review Use workflows to integrate your Azure IoT Central application with other cloud services
How to build the solution
- Set up your Azure Sphere development environment.
- Review Integrate FreeRTOS Real-time room sensors with Azure IoT.
- Learn how to connect and Azure Sphere to Azure IoT Central or Azure IoT Hub.
- The IoT Central Device Template Capabilities Model JSON file for this solution is included in the iot_central directory of this repo.
Have fun and stay safe and be sure to follow us on #JulyOT.
by Scott Muniz | Jul 21, 2020 | Alerts, Microsoft, Technology, Uncategorized
This article is contributed. See the original author and article here.
As companies continue their cloud journey, they are more and more adopting a microservice architecture as part of their application modernization. In this blog post, we have Walter Oliver (@walterov) who is a Program Manager in the Azure Stack Hub team to explore how Azure API Management Gateway on Azure Stack Hub can help in the hybrid strategy for these services.
While some of the applications are being deployed on Azure, companies face challenges with operational consistency when it comes to those apps that must remain on premises. That is one of the scenarios where Azure Stack Hub (ASH) can provide the platform where to host their on-premises applications, while keeping operational consistency. Enterprises are increasingly using Kubernetes on Azure Stack Hub as their choice for their microservices, as they seek increased autonomy for their development teams, flexibility, and modularity. But the process of decoupling single tier monolithic applications into smaller API services brings new problems: how do you know what are these services? Do they meet the security requirements? How are they accessed and monitored?
Azure API Management (APIM) helps address these issues. APIM is part of the Microsoft hybrid strategy, it will help you in:
- Publishing a catalog of APIs available and control access to them
- Preventing DOS attacks for externally available APIs
- Implementing security policies
- Onboarding the ISV partner ecosystem
- Supporting your microservices program with a robust internal API program
Challenges to API Management on Premises
However, since the Azure API Management service is on the cloud, utilizing it implies a round trip to the cloud and then to the on-premises service to service every call. In some cases, this is acceptable, but in many it is not (figure 1).
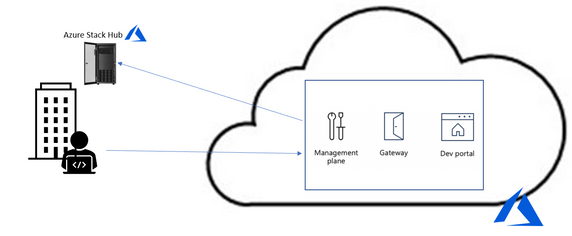
Figure 1. API Management without self-hosted gateway
To solve it the Azure APIM team created the API Management self-hosted gateway. The self-hosted gateway, as the name implied, can be hosted locally in your data center (figure 2).
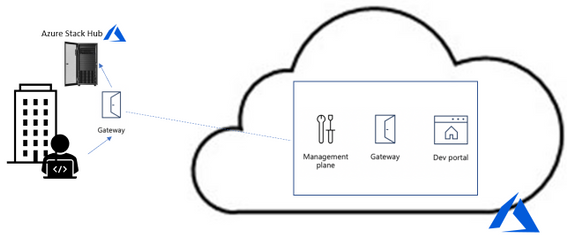
Figure 2. API Management with self-hosted gateway
Running the Self-hosted Gateway in Azure Stack
The APIM’s self-hosted gateway feature enables Azure Stack Hub customers (and customers in general) to manage their on-premises microservices APIs on a central portal in Azure. The self-hosted gateway is a containerized, functionally equivalent version of the managed gateway deployed to Azure as part of every API Management service.
Now you can deploy it inside Azure Stack Hub as a Linux -based Docker container from the Microsoft Container Registry. This means that you can hosted inside the AKS-engine-deployed Kubernetes cluster inside ASH. In cases where you have microservices APIs exposed to applications inside the Kubernetes cluster all the calls happen locally with minimal latency and no extra data transfer costs. More importantly, it also ensures that compliance is maintained since there are not round trips to Azure. Yet, all the benefits of utilizing APIM from Azure remain: single point of management, observability, and discovery of all APIs within the organization.
For complete documentation on AIPM self-hosted gateway see the overview here. To provision the gateway in APIM in Azure follow the instructions here. To deploy the gateway containers in Kubernetes follow the instructions here.
Considerations when running the gateway in Azure Stack Hub
- A common question is whether there is a need for opening ports for inbound connectivity, the answer is no. Self-hosted gateway only requires outbound TCP/IP connectivity to Azure on port 443, it follows a pull model, not a push model for communication. Connectivity is required so that information such as health reporting, updates, events, logs, and metrics can be transferred. This also implies that when there is no communication with Azure, the data does not flow, yet the gateway continues to operate as expected.
- When running the gateway container in your Kubernetes cluster with the configuration backup option, you will notice an extra managed disk being created in the cluster, this is the disk where the configuration backup is stored. This is particularly useful in case that connection to Azure can become unavailable. Notice that the gateway container is not meant to be run on an ASH stamp that will be disconnected from the internet or is planned to be disconnected most of the time. In fact, if the stamp is disconnected temporarily and for some reason the gateway container is stopped, Kubernetes will try to restart it but if the option of running with backup configuration was off, it will fail. In those cases, you need to ensure that connectivity to Azure is restored.
- Another question is whether that Gateway container automatically discovers the available APIs. The answer is that they are not, you must explicitly go to the Azure APIM portal and register the APIs you need to manage.
- In the case that you have APIs in another Kubernetes cluster (or anywhere in your data center) that you would like to manage you can publish them via the same gateway container or provision and deploy another gateway instance
- Deploying a new microservice and publishing its API or applying changes to an existing one is something that is better formalized in a CI/CD Pipeline. Getting familiarized with the available operations will be useful, see the reference here. For a guide on how to architect a CI/CD pipeline with corresponding repo see this blog.
Summary
Azure’s API Management service is very helpful for managing large microservices deployments, now the self-hosted APIM Gateway makes it very appealing for including APIs deployed on premises. The documentation provided online in Azure covers the basic concepts, provisioning, and deploying of self-hosted gateways, the summary provided above is an introduction to the subject tailored to Azure Stack Hub customers. Subsequent posts will include a sample deployment of an API and its publishing through APIM on Azure.
4. Paste the command in your SSH client











Recent Comments