This article is contributed. See the original author and article here.
Scenario:
User has access control configuration enabled on the Logic app with Trigger access restricted to specific IP ranges and using Send Approval email action in the workflow. So when recipient receives an approval email, user isn’t able to record the response (like approval/reject).
Cause:
When we enable the access control for IP ranges by default it inspects all inbound traffic to Logic App. If source IP isn’t part of the restricted Ips ranges then it blocks the traffic. In our case, Connector outgoing IP addresses are not enabled on the restricted IPs.
Resolution:
User can either update the IP ranges on the access control configuration in designer or using ARM template to update the same.
You can find the Logic App outbound /Connectors outbound IP addresses here Logic App outbound-ip-addresses . We need to open the specific outbound Ips with respect to Connector.
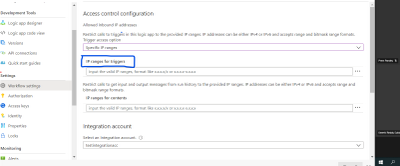
Logic App Designer:
At present designer has two settings for restricting IP ranges for triggers (Its for both access endpoint and actions call back request) and contents. So, you can enable both the trigger restricted and respective action connector outbound IP addresses in the IP ranges for triggers param.
Using ARM template:
You can also use the ARM template allows to provide the access control configurations for Trigger and Actions separately. You can use IP as IP range (x.x.x.x-x.x.x.x) or CIDR notation (x.x.x.x/x)separated by ‘,’ as an array.
{
“$schema”: “https://schema.management.azure.com/schemas/2015-01-01/deploymentTemplate.json#“,
“contentVersion”: “1.0.0.0”,
“parameters”: {},
“variables”: {},
“resources”: [
{
“name”: “[parameters(‘LogicAppName’)]”,
“type”: “Microsoft.Logic/workflows”,
“location”: “[parameters(‘LogicAppLocation’)]”,
“tags”: {
“displayName”: “LogicApp”
},
“apiVersion”: “2016-06-01”,
“properties”: {
“definition”: {
“<workflow-definition>”
},
“parameters”: {
},
“accessControl“: {
“triggers“: {
“allowedCallerIpAddresses“: []
},
“actions“: {
“allowedCallerIpAddresses“: []
},
// Optional
“contents”: {
“allowedCallerIpAddresses”: []
}
},
“endpointsConfiguration”: {}
}
}
],
“outputs”: {}
}
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.


Recent Comments